
How To: Stop the New Java 7 Exploit from Installing Malware on Your Mac or PC
UPDATE: A patch to fix the exploit has been released. Download it here.


UPDATE: A patch to fix the exploit has been released. Download it here.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.
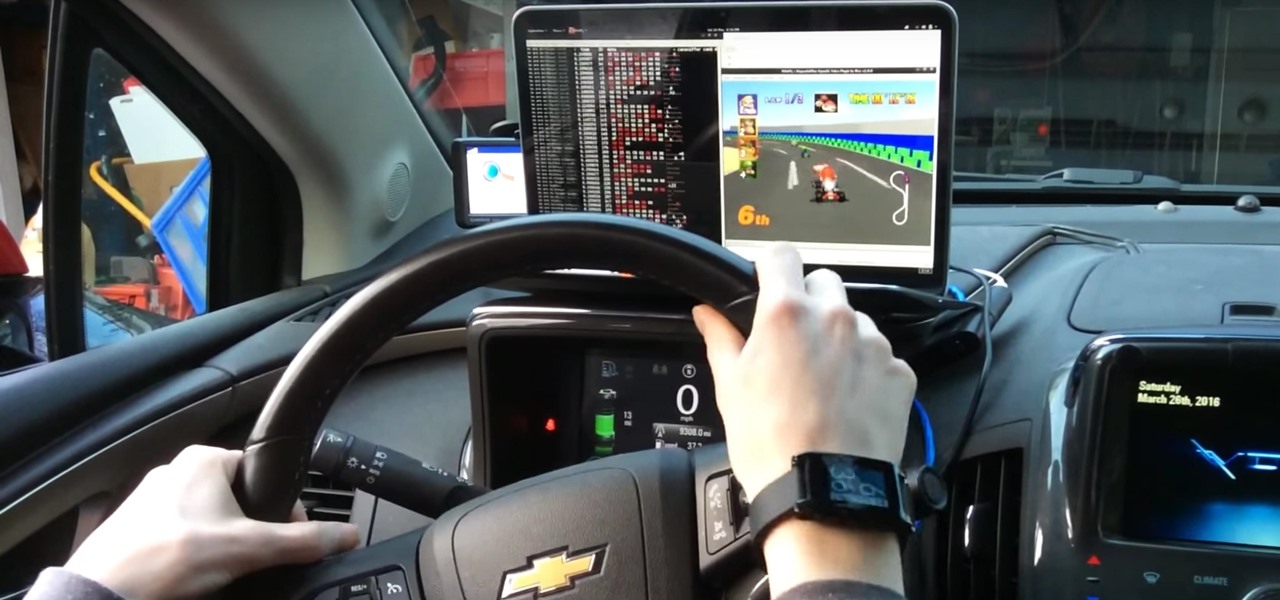
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department.

Tricking your eyes into seeing 3D images isn't all that hard in movies or even in virtual reality, but when you start projecting holograms into the physical world, you run into some difficult problems. Microsoft obviously figured them out with their HoloLens, but how? The process is pretty amazing.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.
Apple's line of iPhones, iPads, and iPods are of some of the most advanced devices available on the market. Usually, the biggest complaint is that they are not customizable, but they can be if you exploit a few bugs in the system.

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Sometimes the hardest part about getting your minecart rolling is the beginning takeoff. Have you ever started a minecart on a hill, and then tried to jump into it as it started moving, only to fail and watch it slowly dwindle into the distance?

We've already done a tutorial explaining why buttons are superior to levers, but now I want to show you a way to make them even more useful than they already are. You can't get this sort of functionality with levers!

One of the hardest parts of entering the IT and computer science field — other than the difficult material and intense competition — is the time and financial cost of learning everything you'll need. Learning to code isn't just learning one language; you have to learn a variety of languages used for different purposes, and then you have to get experience using them.

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Lyme is a growing threat as we move into warmer weather in the US. Researchers have said this year could be one of the worst for this tick-borne disease, as a skyrocketing mouse population and warmer temperatures increase the risk.

Pertussis, or whooping cough, is a highly contagious disease that can be life-threatening for young children. New research backs a recommendation that all pregnant women receive a pertussis booster with each pregnancy, as it can help their infants fight off the infection.
There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

I remember the first time I used coconut oil; the whole kitchen was filled with a fragrant aroma that reminded me of the tropics. After learning it was a healthier alternative to traditional cooking oil—not to mention a great source of the good-for-you saturated fat—I was hooked.

Whites are the hardest color to keep looking bright and new after just a few months' time. Your sweat and oils quickly become stains, and colors from other clothes will eventually bleed into the fabric, discoloring your bright whites into something merely whitish. But before you reach for the bleach, the ultimate chemical cleaner, try some a few of these safer, less-toxic DIY solutions out instead.

After you have registered to this site,sign in then to start missions. Basic Missions

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work
Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great deal, the biggest issue most users have with the service is the limited amount of available content. Anything?

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

Want to find out if your neighbors are talking about you? You could always hack their webcam or turn your iPhone into a secret spy camera, but unless you have a key to their house, that could be tricky to do without getting caught.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.
For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Summer's coming, and that means burger season. Okay, never mind... every season is burger season. Burgers are universally loved; they're the one meal you can find at numerous fast food shacks and haute cuisine spots.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

If you're a Steampunk (or costumer of any variety) and you don't know what Rub 'n Buff is, this tutorial will make your life so much easier. You have no idea.