Amid a troubling resurgence in coronavirus cases, led by the new Delta variant, augmented reality is once again moving back into the spotlight as a solution, especially now that the move to return to offices has been stalled.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

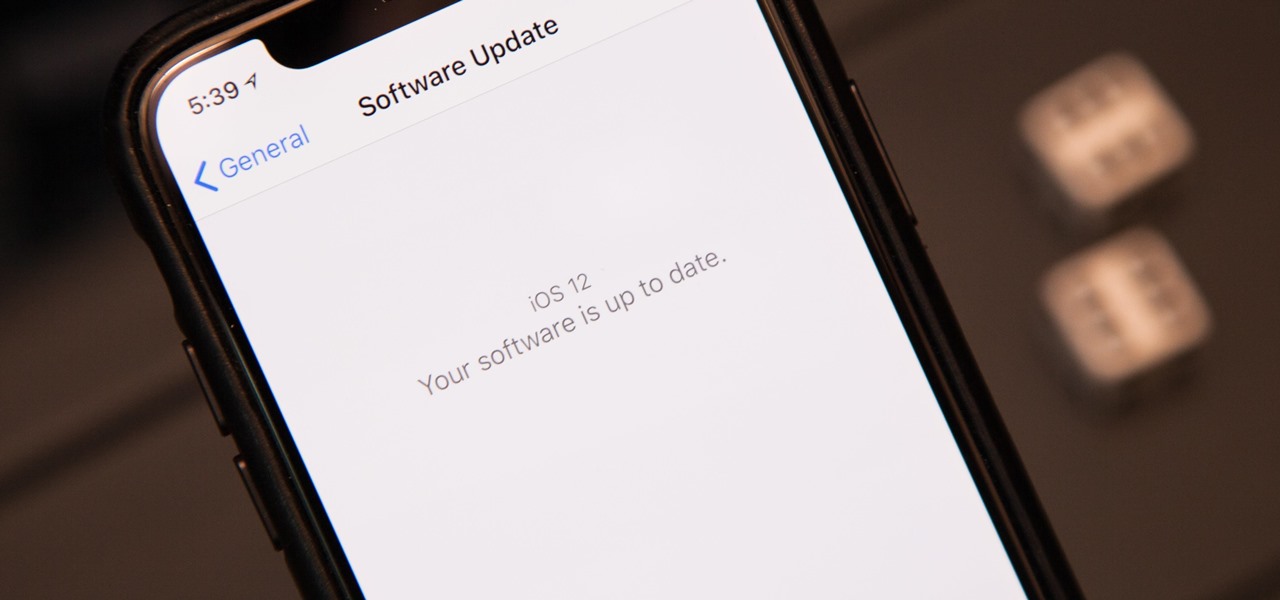
Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

With iOS 18, you get better note-taking capabilities in the revamped Notes app, advanced features like conversions and results history in the more powerful Calculator, and interactive Math Notes, a feature in both apps that's a game changer for students and professionals dealing with complex equations. But Apple didn't forget about Reminders, which has become more than a simple to-do-list app.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

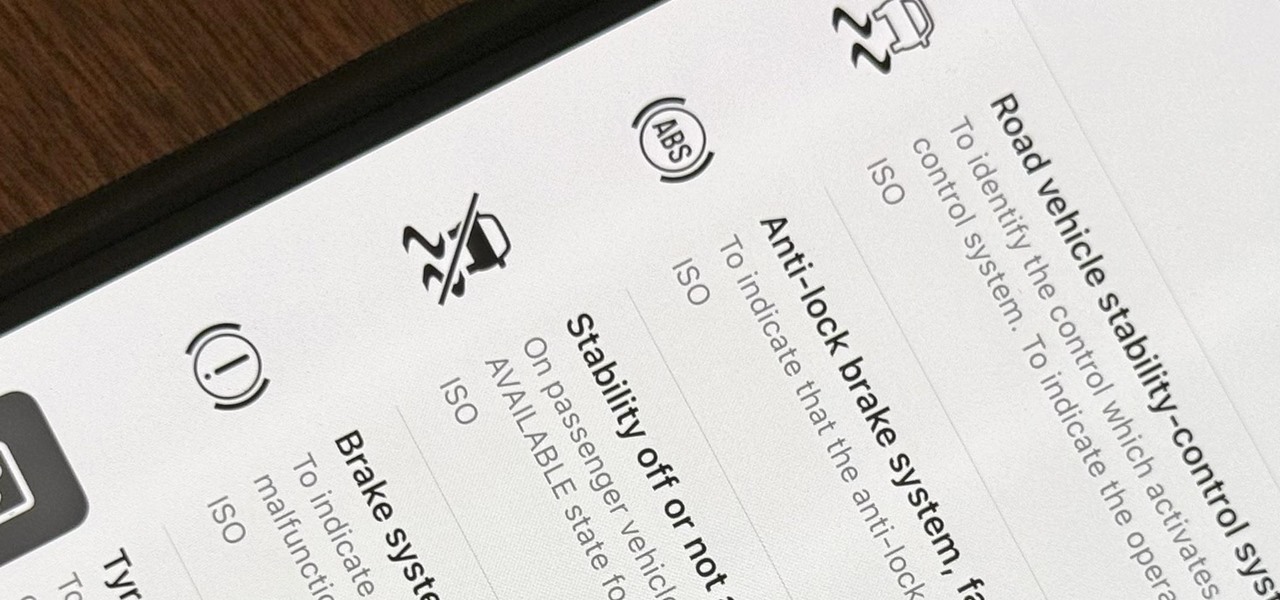
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.

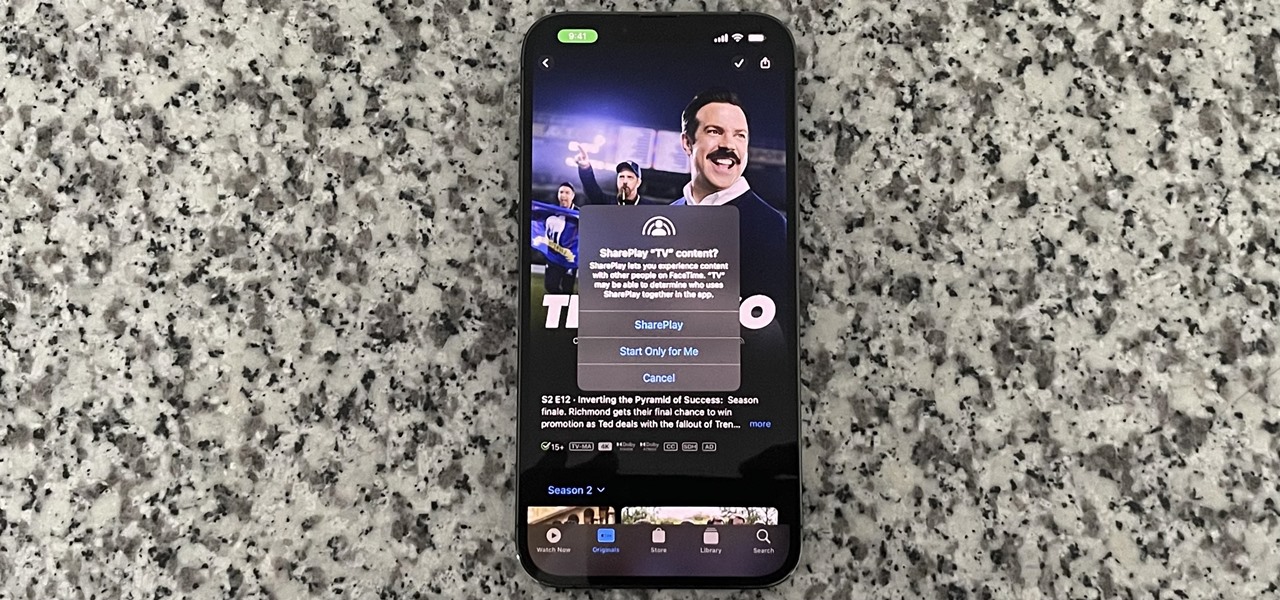
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

A surefire way to delight this holiday season is with the latest tech. Gadgets today aren't cheap, but we've got you covered with some useful gear that's perfect for practically everyone — at a price that won't break the bank. If you need a last-minute present, check out the best gadget gifts of 2020, on sale for less than $100.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

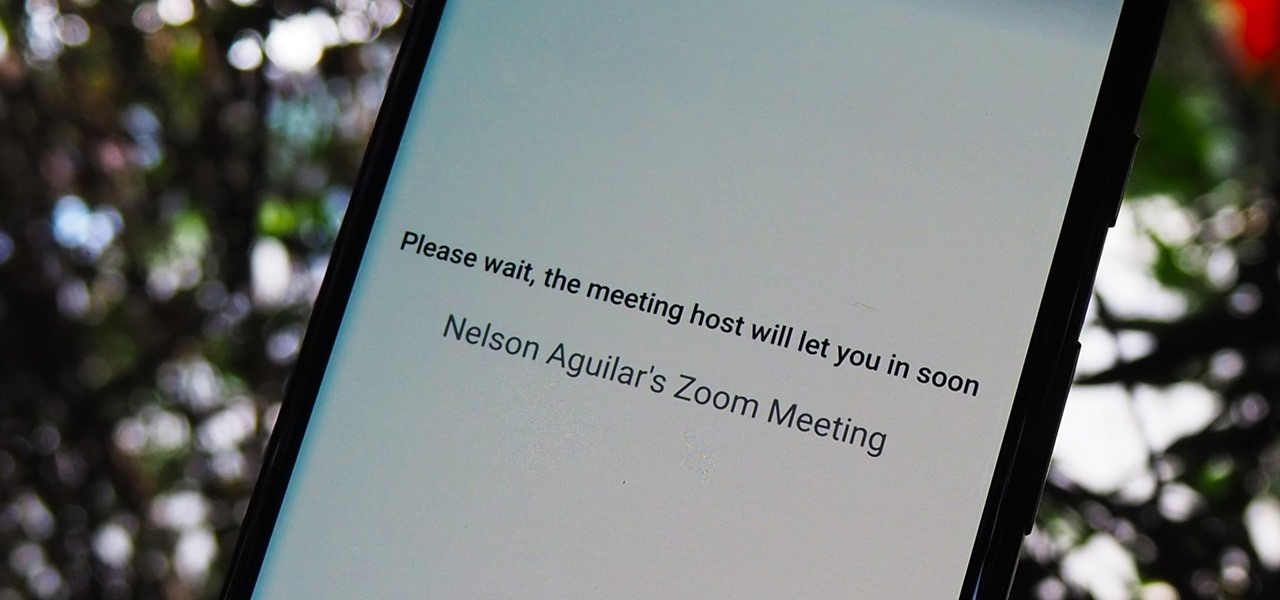
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Mikoto, from Karen Tsai (aka angelxwind), is a free jailbreak tweak unlike any other. With Mikoto, you can customize features in your favorite iOS apps to an extent that you would've never thought possible.

Being able to sleep deeply and fully is one of the foundations for real health. When you go without it, you feel subhuman and incapable of dealing with the world—just ask a student who's had to pull an all-nighter or the parents of a newborn. In fact, many studies have shown that lack of sleep or irregular sleep is linked to acne, weight gain, and depression.

In this video series, graduate student and teaching assistant Esther-Xiaohua Liu will show you how to write Chinese characters by using the radical for "water." If any Chinese character contains the "Three-Dot-Water" radical, it will have some association to shui or "water." Learn to speak and write the characters for juice, converge, the Milky Way, sweat, dirt, soup, pond, irrigate, float, and many more! Esther-Xiaohu will give you what you need to recognize these water words in print today!

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

Live Activities is Apple's hottest new feature for iPhone, but it's not always straightforward. Sometimes you'll trigger one without realizing it, but it may seem frustratingly impossible to start one when you really want it.

If you haven't noticed yet, there are a lot of new features hiding in your iPhone's Messages app, and some of them are things users have been requesting for a long time. While iMessage is getting a lot of attention by letting us edit and unsend messages, it's only just the start of a pretty big update.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Ivy League schools aren't just places for people to row and sip their drinks out of glasses normal people would never use (i.e. snifters). They also the place for trolling on a grand scale. Just take a look at these Trolls de la Resistance!

In this video tutorial series, you'll find instructions for using the UCSC Genome Browser. More specifically, this video addresses (1) getting DNA sequences, (2) using annotation tracks, (3) locating intron-exon boundaries, and (4) searching with BLAT. For further detail about any or all of the above topics, and to get started using the UCSC Genome Browser yourself, take a look! Use the UCSC Genome Browser - Part 1 of 4.

Science is most marvelous when it's creating an explosion, even at the tiniest of proportions. In the video below, Daniel Rosenberg from Harvard's Natural Science Lecture Demonstration Services reveals the secret to shooting a cork rocket over twenty meters using a little chemistry and an ultraviolet LED light. Rosenberg, who's a research assistant and lecturer for the Natural Science division at Harvard, demonstrates what happens when hydrogen and chlorine are explosively "burned" together t...

No more alkaline batteries. No more NiCad's. No NiMH's. No Lithium. Forget all of those hazardous chemical reactions in the batteries and think eco-friendly. Professor David Edwards did.

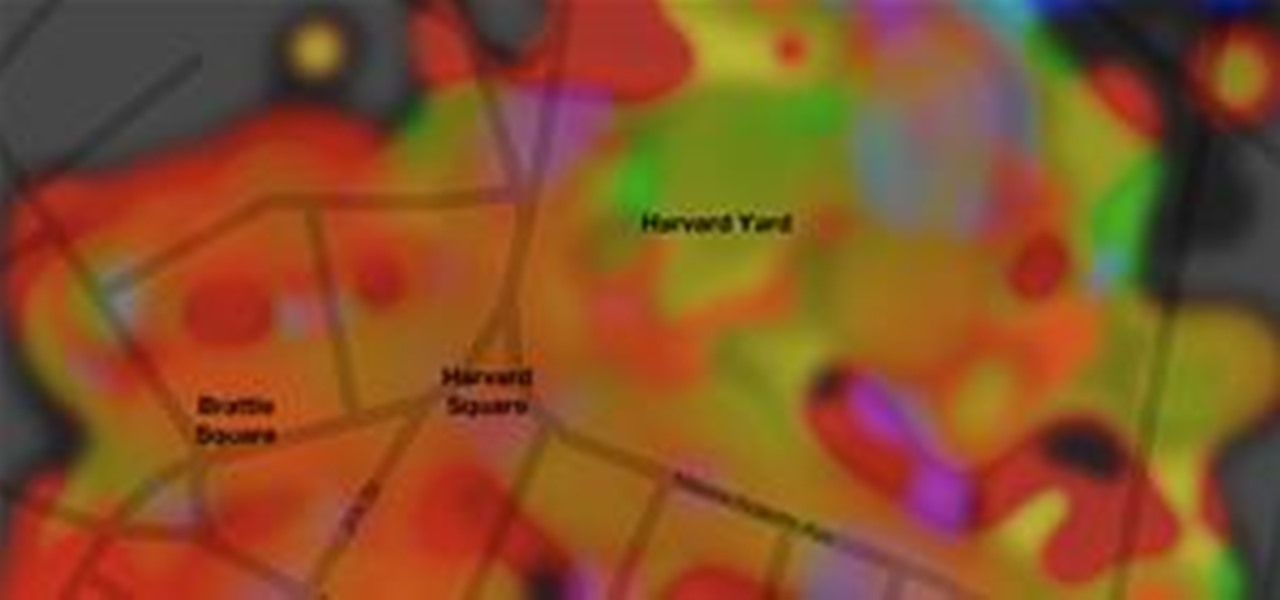
Cartograms are usually pretty mundane, but throw in Flickr, Photoshop, and a well-known public place and you have an artistic representation of popular colors. Much more eye-grabbing than your common map.

Have a few light bulbs and a blowtorch? Then join the folks over at Harvard in a cool science experiment on the conductivity of glass. As you well know, glass is an insulator with low conductivity and high resistivity. In the video below, they flip the switch, demonstrating how heating the glass fuse enclosure from an incandescent light bulb can create a conductive material that completes the series circuit and lights the second light bulb. In the video, the two light sockets are wired in ser...

When editors or teachers ask you to write in "APA style," they do not mean writing style. They are referring to the editorial style that many of the social and behavioral sciences have adopted to present written material in the field. This how to video teaches you how you can master the APA format writing style and when you should use it. Write in a APA format.

If you're into entomology, then you probably recognize the name E.L. Trouvelot. After all, he was the person responsible for the outbreak of invasive gypsy moths in North America, which are now one of the most destructive foliage-eating pests in the United States.