Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.
If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

I chose to make this a Steampunk iPad case, but you can change the details and make it look as modern as you'd like. As I said earlier, Steampunks probably shouldn't buy iPhones or iPads, but if you're going to get one, you may as well make it look cool, right? The iPad pictured below was borrowed from a friend of mine, though I should add that this design will easily work with tablet computers of any variety, Apple, Android, or otherwise.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

In this video series, watch as professional guitarist and skilled craftsmen Frank Pope teaches how to build an electric guitar. Learn how to cut the body, install the truss rod, make the fingerboard, make fret inlay, install the bridge, set the wires and electronics, and stain and finish the wood. With this easy step by step tutorial, you can finally get an electric guitar that is exactly what you are looking for. Take the art of guitar playing to the next level with the help of the experts f...

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today.

You may be wondering what exactly makes the Pixel 4a's camera so great. Compared to its predecessor, it has the same Sony IMX363 sensor and no additional hardware. Well, beyond stellar image processing, it also has several great new features that Google has added since they released the Pixel 3a last year.
Welcome back Hackers\Newbies!

Does executing a perfectly timed, no-scoped headshot, followed by a well-choreographed teabagging ever get old? No, no it doesn't, and neither do custom emblems for Call of Duty: Black Ops 2. How else are we going to kill time until Black Ops 3 arrives?

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

In this video tutorial series, you'll find instructions for using the UCSC Genome Browser. More specifically, this video addresses (1) getting DNA sequences, (2) using annotation tracks, (3) locating intron-exon boundaries, and (4) searching with BLAT. For further detail about any or all of the above topics, and to get started using the UCSC Genome Browser yourself, take a look! Use the UCSC Genome Browser - Part 1 of 4.

Science is most marvelous when it's creating an explosion, even at the tiniest of proportions. In the video below, Daniel Rosenberg from Harvard's Natural Science Lecture Demonstration Services reveals the secret to shooting a cork rocket over twenty meters using a little chemistry and an ultraviolet LED light. Rosenberg, who's a research assistant and lecturer for the Natural Science division at Harvard, demonstrates what happens when hydrogen and chlorine are explosively "burned" together t...

No more alkaline batteries. No more NiCad's. No NiMH's. No Lithium. Forget all of those hazardous chemical reactions in the batteries and think eco-friendly. Professor David Edwards did.

Ivy League schools aren't just places for people to row and sip their drinks out of glasses normal people would never use (i.e. snifters). They also the place for trolling on a grand scale. Just take a look at these Trolls de la Resistance!

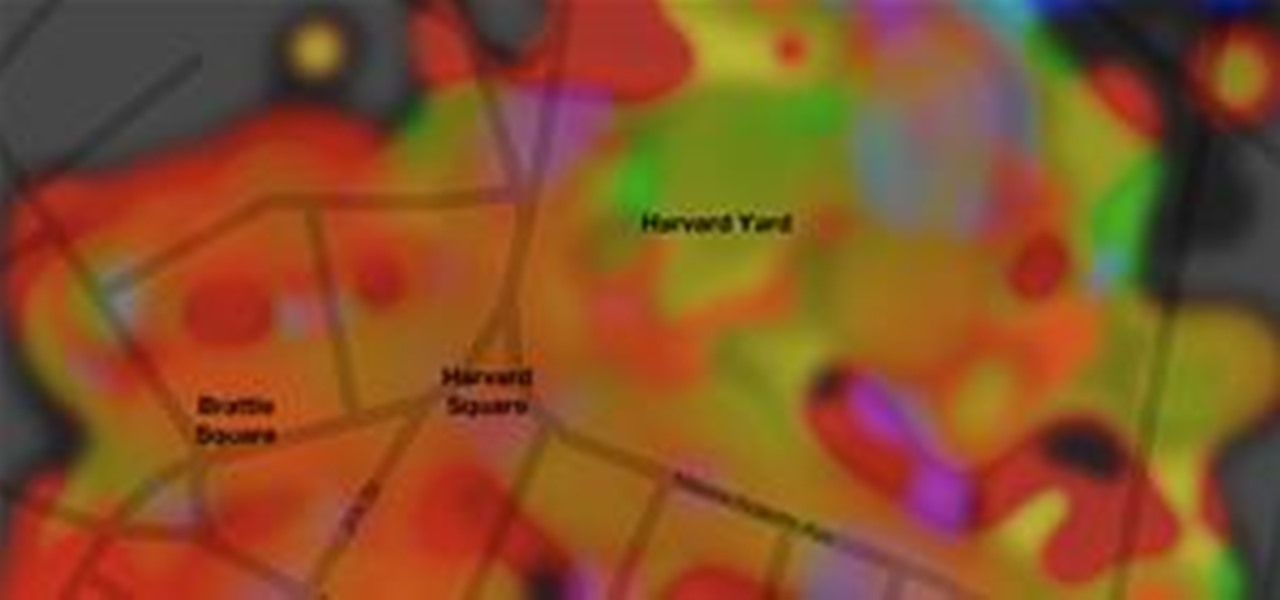
Cartograms are usually pretty mundane, but throw in Flickr, Photoshop, and a well-known public place and you have an artistic representation of popular colors. Much more eye-grabbing than your common map.

Have a few light bulbs and a blowtorch? Then join the folks over at Harvard in a cool science experiment on the conductivity of glass. As you well know, glass is an insulator with low conductivity and high resistivity. In the video below, they flip the switch, demonstrating how heating the glass fuse enclosure from an incandescent light bulb can create a conductive material that completes the series circuit and lights the second light bulb. In the video, the two light sockets are wired in ser...

When editors or teachers ask you to write in "APA style," they do not mean writing style. They are referring to the editorial style that many of the social and behavioral sciences have adopted to present written material in the field. This how to video teaches you how you can master the APA format writing style and when you should use it. Write in a APA format.

Amazing footage shot of some highly skilled wakeboarders, entitled "Winch Madness". According to Wikipedia, Wakeskate winching involves "an engine, spool, rope, handle, frame, and some sort of simple transmission. The person being towed walks (or swims) away from the winch and pulls out all of the rope." When the winch lets loose, the boarder can go 15-25 mph.

If you're into entomology, then you probably recognize the name E.L. Trouvelot. After all, he was the person responsible for the outbreak of invasive gypsy moths in North America, which are now one of the most destructive foliage-eating pests in the United States.

Soccer star David James is the goalkeeper for England and Portsmouth, so he's more than skilled with closing in on an attacker from the football field.

As F.C. Barcelona's star striker Zlatan Ibrahimovic explains, it's the defender's job to make your life as difficult as possible. So how do you get a defender to open up a spot for you to whisk away from him? Ibrahimovic shares a few tips in this video, including using speed, skilled footwork, and crazy steep swerves. This is a football training session that is vital for any soccer player looking to take his soccer team to victory. Get past defense as a soccer striker.

This link will take you to the executive branch or the President. The President is only in term for 4 years, but can be reelected once. The President does not work by himself; he has skilled people who help him make decisions. This website will allow you to learn about the people who help Obama. It also provides information on President Obama’s latest actions as president.

So you've added Google insiders, celebrities, and authors to your circles, but you want to know who you can reach out to for help when it comes to Google overall. Luckily for you, there seems to be a Community Manager for almost every Google product. If you've got an issue with your Google Account, just contact them via their Google+ profile!