In this series of gardening videos, our perennial plant expert Martha Cycz tells you how to design a great looking garden that is healthy and inexpensive. She discusses how to tell if your plants are getting enough sun and how to determine if you have left enough space for them to expand. She even offers tips for controlling pests. The key to a great looking garden is planning: after watching these videos, you will know exactly how to map out your backyard work of art.

Chef Don from HouseCallChef demonstrates how to grill mushrooms, asparagus, zucchini and yellow squash. You can also grill other vegetables such as parsnip, rutabaga, potatoes, tomatoes or peppers, and even some fruits like pineapple, watermelon, apples and oranges. You can use any type of grill that you want.
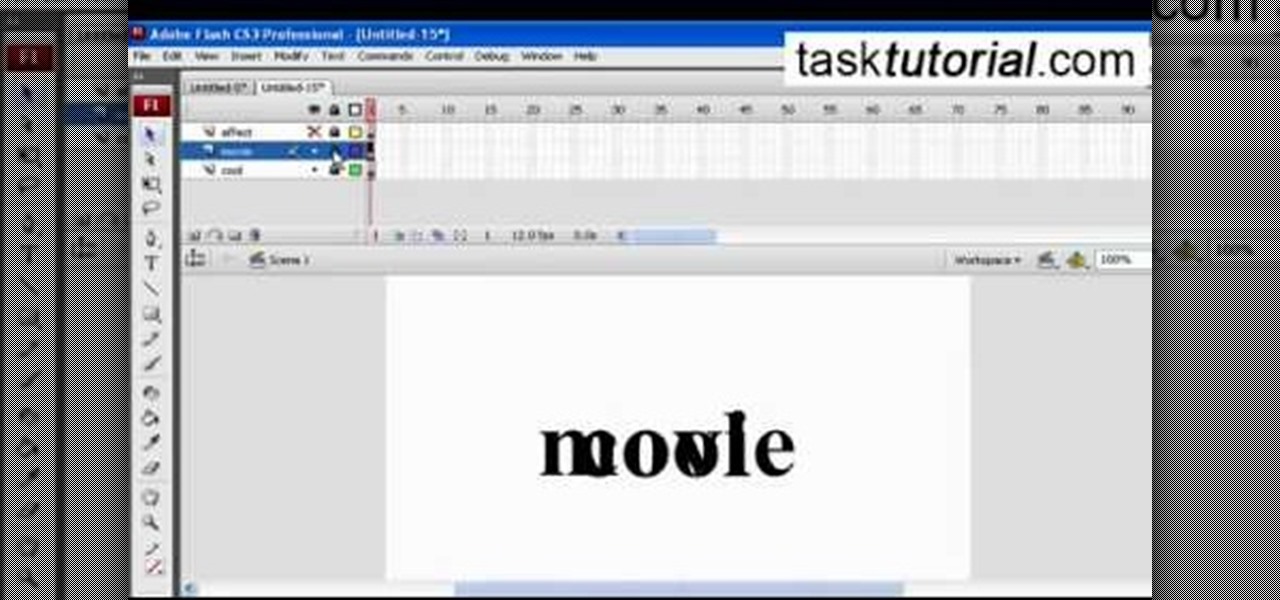
A great free video training from tasktutorial on how to create a cool movie text effect in Flash. Start by creating the text; type in "cool", rename the layer and lock it. Now type "movie" and rename the layer. Type in "effect" and rename this layer as well. Now focus on the first layer. Convert it to movie clip. Now convert the other two layers to movie clips as well. Stack the three layers on top of each other. Next add a key frame starting from frame 10. Select the "cool" layer. Re-size it...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to transform a photo into a flashy poster in Photoshop.
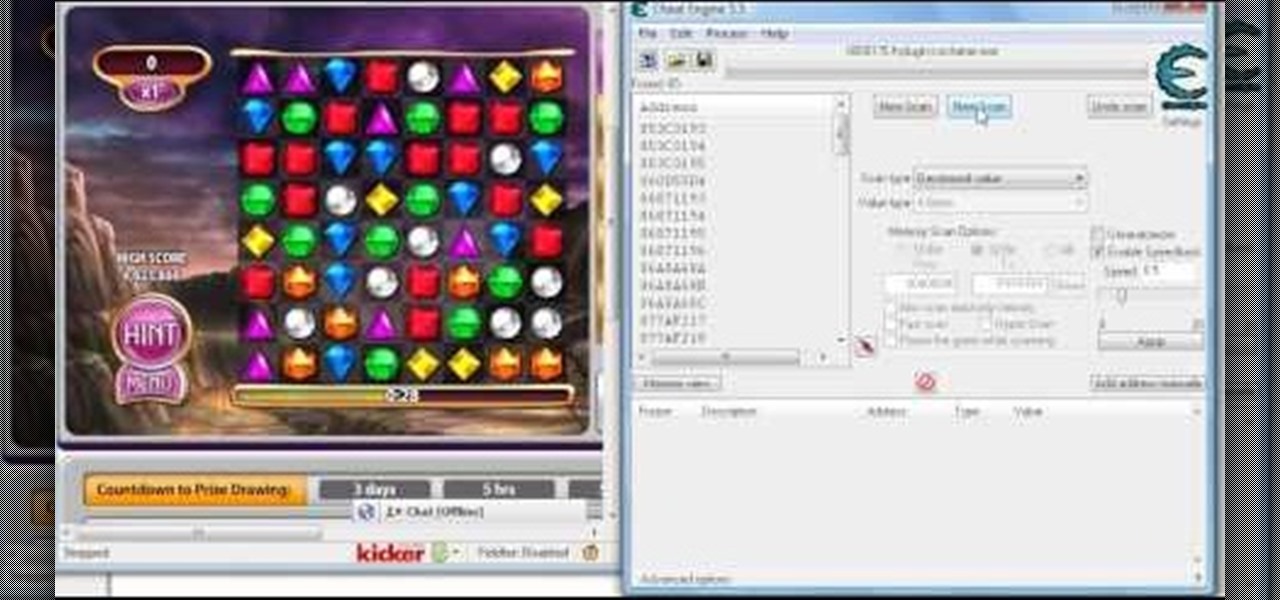
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).
This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Hamsters are great pets. They are sociable, and they do not demand a great deal of attention. However, before you go to the pet store to buy a hamster, you should know what to look for in selecting a healthy hamster. In this free video series, our expert tells you some tips for finding the right hamster for you.

In this series of videos you'll learn how to draw with charcoal from a professional artist. Expert William Cotterell shows you what types of art supplies you'll need to get started, including various types of charcoal, compressed and pencil varieties, types of erasers that work best with charcoal, and the best types of paper for making charcoal drawings. He also shares tips for choosing a subject, understanding light, blending techniques, adding highlights, and using Fixatif to protect your w...

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

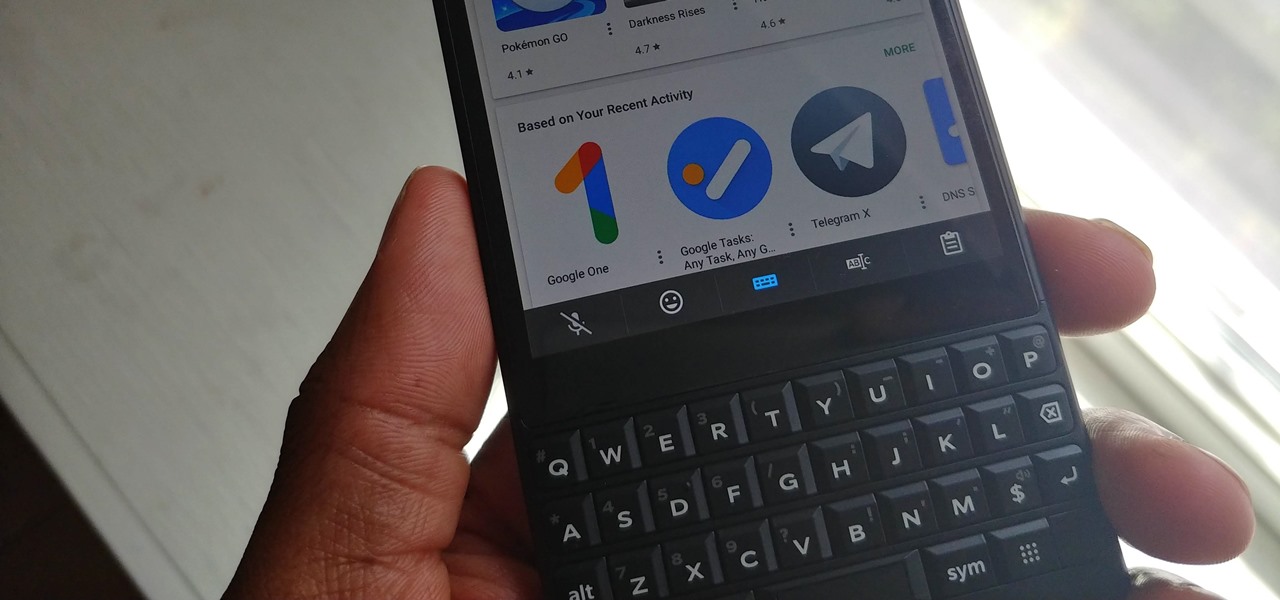
One of the best parts of the BlackBerry KEYone and KEY2 is the iconic physical keyboard. There is one major downside, though: By default, the virtual keyboard appears on these devices even when typing on the physical keyboard. Luckily, there's a way to change that.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

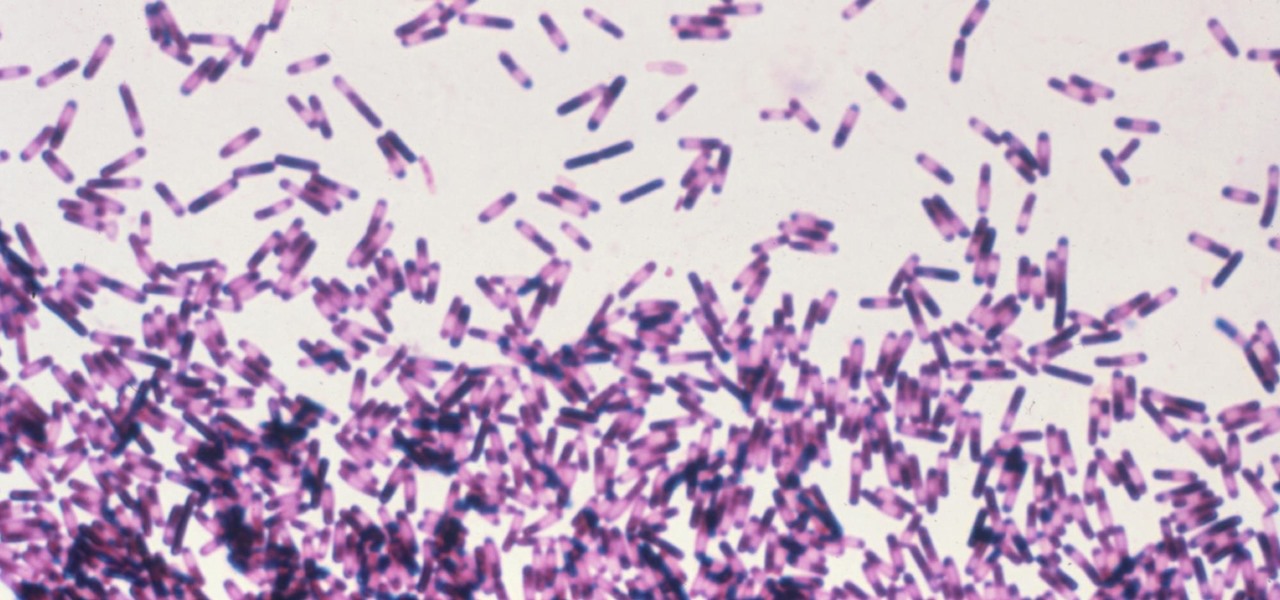
Whether or not a microbe is successful at establishing an infection depends both on the microbe and the host. Scientists from Duke found that a single DNA change can allow Salmonella typhi, the bacteria that causes typhoid fever, to invade cells. That single genetic variation increased the amount of cholesterol on cell membranes that Salmonella and other bacteria use as a docking station to attach to a cell to invade it. They also found that common cholesterol-lowering drugs protected zebrafi...

When Chan Mei Zhi Alcine chose her senior project, she thought outside the box by thinking inside the bottle. Along with a research team at her university, she found a way to combine health and enjoyment, while meeting a challenge not so definitively met before in alcoholic beverages. She and a research team at her university claim they've created the world's first probiotic sour beer.

Multistate outbreaks of Salmonella infection in humans have led the Centers for Disease Control to advise caution when interacting with poultry. A press release on June 1st mentioned eight multistate outbreaks connected to backyard flocks. As of May 25, 372 people in 47 states were reported infected with the outbreaks' Salmonella strains. That means this year could be as bad as 2016, a record year, for salmonella outbreaks with 895 people infected.

Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

No crème brûlée is worth its custard without the crackled, caramelized crust it's famous for. For this reason alone, many cooks have a brûlée torch sitting somewhere in their cabinets.

Hello there Nullbyte users! This will be my first article here.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

Indoor electric grills are nothing new; George Foreman grills have been around for over 20 years now, providing healthy, smokeless grilling options for indoor use. Yet as nifty and fun as George Foreman grills are, indoor grills have never been considered a hot item for passionate and avid home cooks.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Cookies for breakfast seem like a clear dietary no-no, but these three-ingredient breakfast cookies are easy, healthy, portable, and can be made in advance. They're also dairy-free, egg-free, and have no added processed sugar, so they can also be called allergy-friendly cookies. If you use gluten-free quick oats in this recipe, they are also gluten-free breakfast cookies! Besides all of those reasons, these cookies are only about 50 calories each when they're made with just the original three...

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

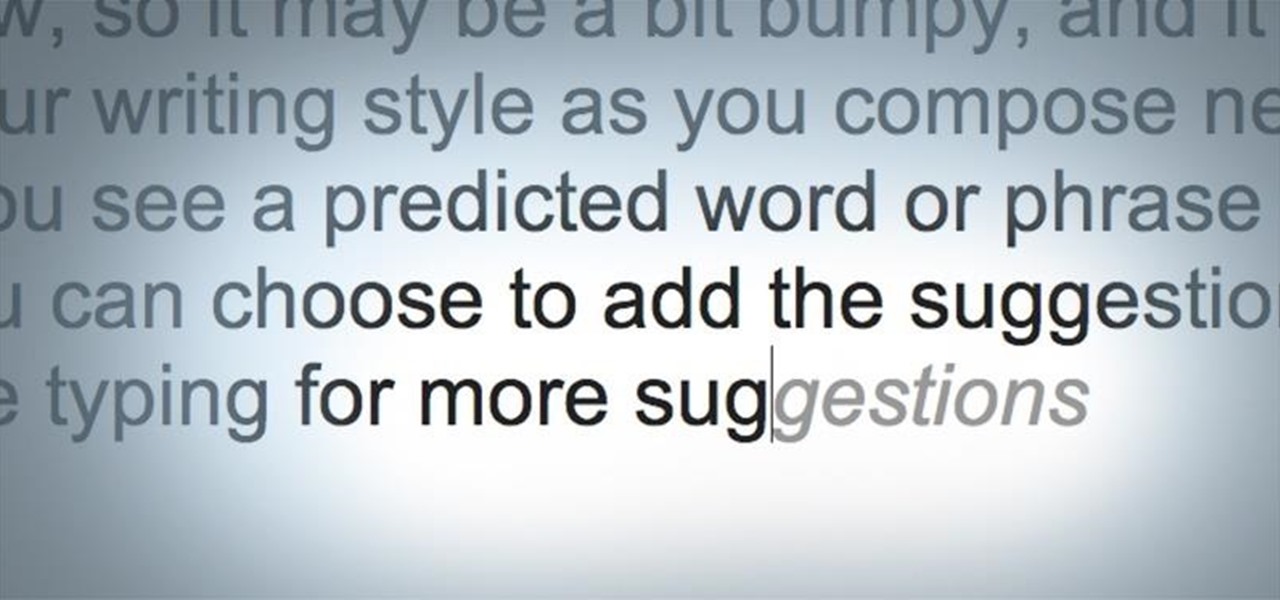
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Some food jars seem like they're actually designed to prevent you from enjoying every last bit inside. The remnants of sticky foods like Nutella and peanut butter are almost impossible to scrape out with a knife or spoon, and it's a shame to throw out something that tastes so good—especially when it's the best part. A spatula could help you get that last drop out from the walls or bottom easier, but that's just ruining your chance at maximizing the full potential of those remains into somethi...