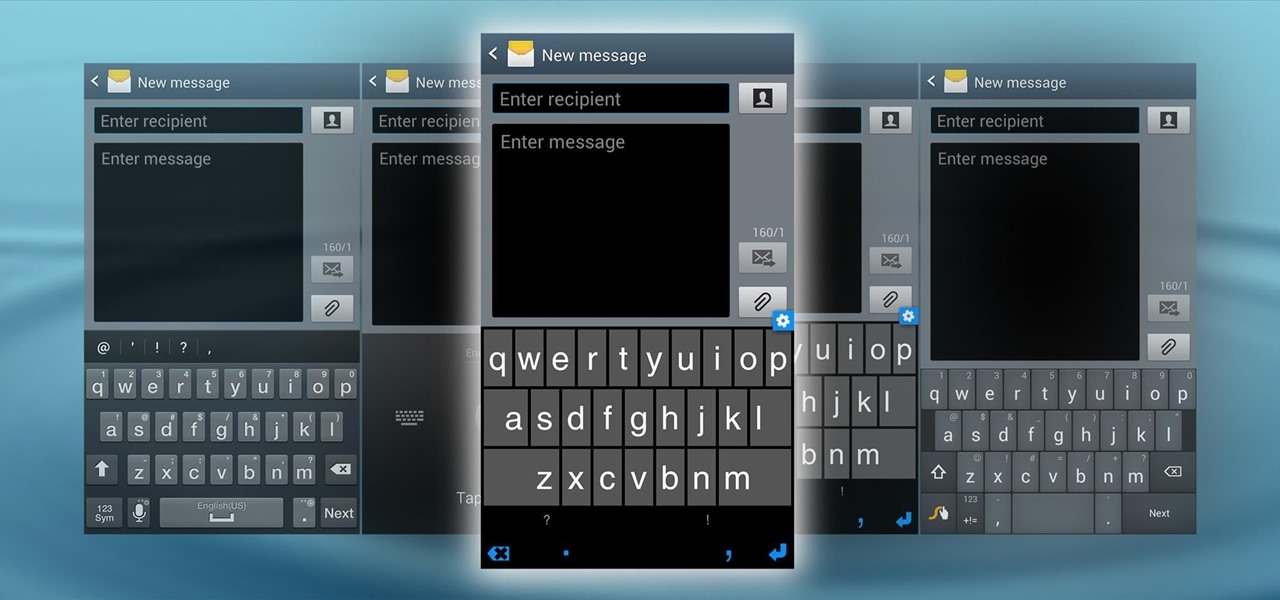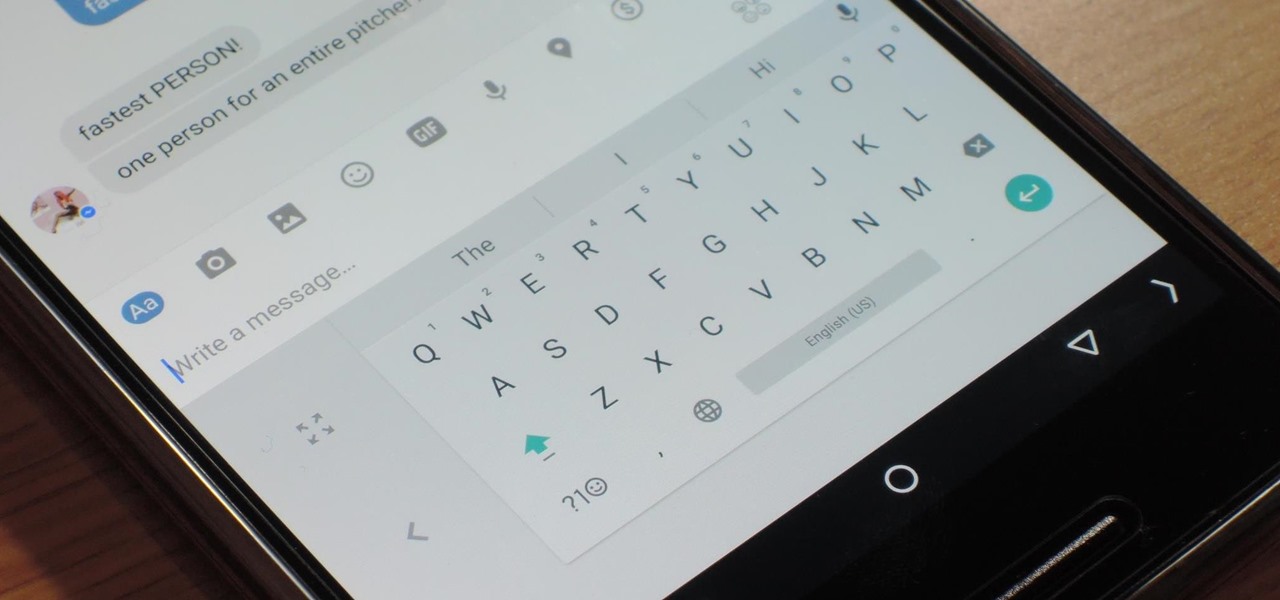
Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

Sautéed mushrooms and boiled green peas simmered in creamy, spicy onion-tomato gravy. Mushroom mutter gravy is typical a North Indian gravy. It is made from onion and tomato. it is spiced up with regular spices. Just like other vegetables, these mushrooms are also healthy and nutritious, good for our body.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

With the DOJ attempting to rip Apple a new one and an Apple attorney firing back, the President offered his opinion on the recent encryption debacle between the FBI and Apple at SXSW, amidst some talk about the direction of today's tech industry.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

According to the American Osteopathic Association, "1 in 5 teens has some form of hearing loss," and some experts believe it's because of an increase in headphones use. While I understand that music, movies, and video games help keep children preoccupied, there's no reason why they can't be entertained at a healthy hearing level.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

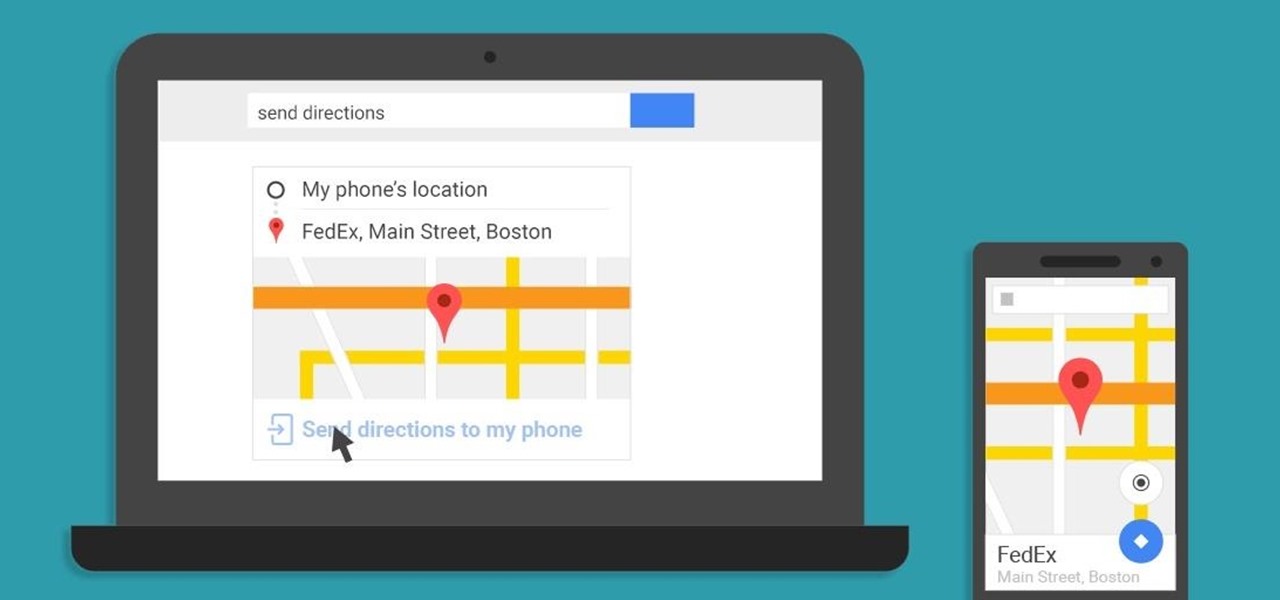
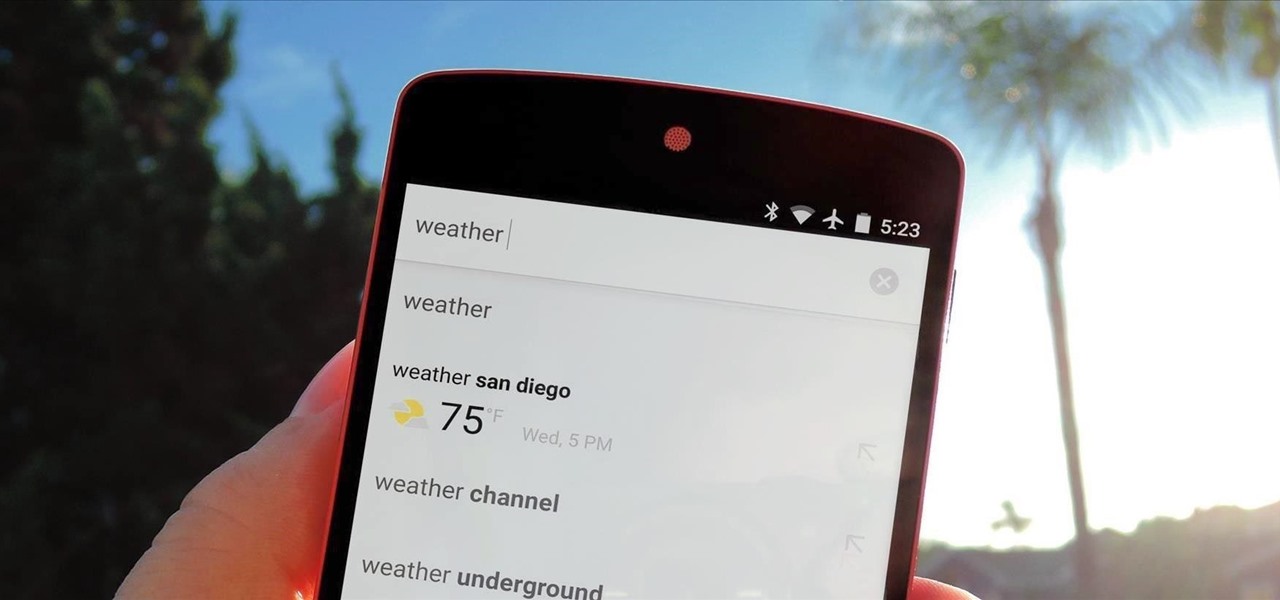
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Using spaghetti squash "noodles" for a healthy, low-carb meal seems like such a great idea, but as many of us know, turning this vegetable into a decent pasta facsimile usually has less-than-satisfying results. The usual method is to cut the squash lengthwise and roast, microwave, or steam it. Often, it comes out overcooked and underwhelming.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Diabetes is a well known metabolic disorder occurs due to disturbance of insulin level in the blood leading to high glucose level which has a very serious impacts on our body To Avoid Diabetes; You Have to Do Four Things

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

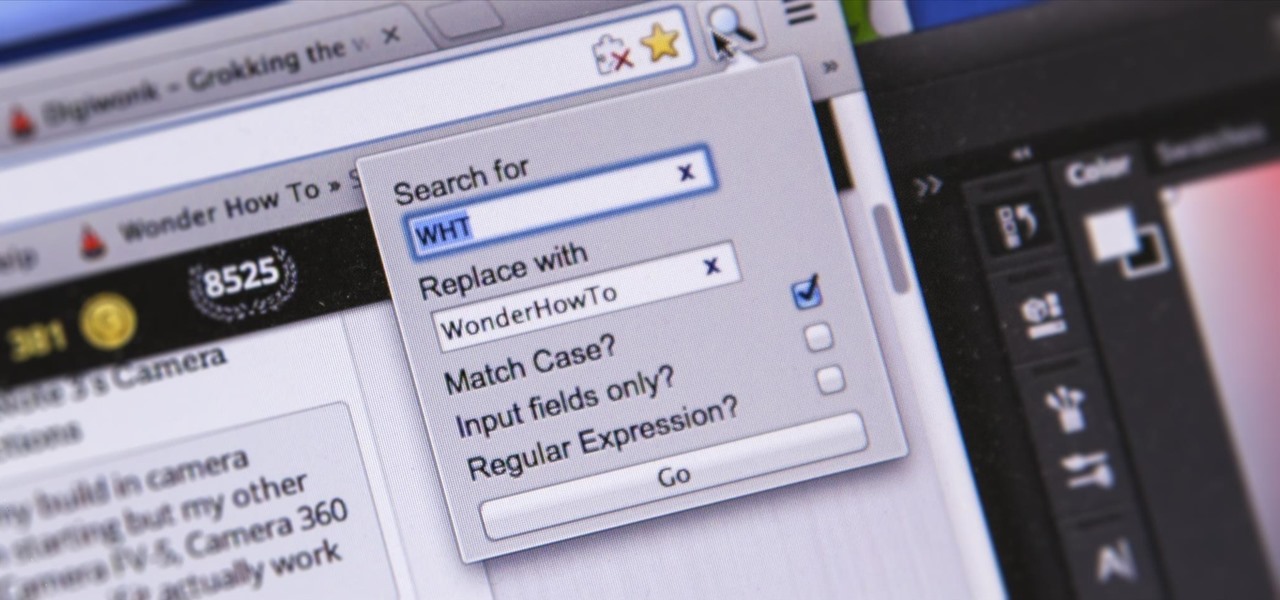
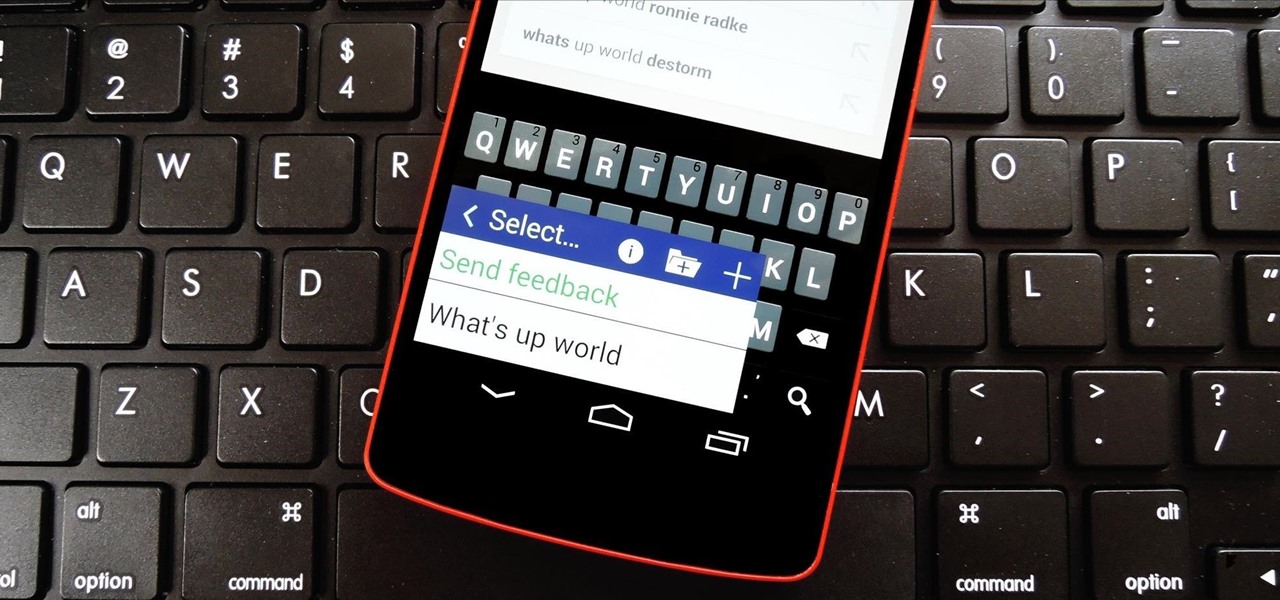
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

I don’t buy socks—I get a pack from my parents on Christmas Day, so I’ve got to make sure they last all year. Other than losing them mysteriously in the dryer, the biggest threat to my limited sock collection is a stretched out cuff. Nothing's more frustrating than a loose sock sliding down into your shoe.

With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

Love pizza but can't have the carbs? Well this recipe is not only delicious, it is a healthy alternative to pizza dough. Giving you a lot of versatility this cauliflower pizza crust recipe is a great to have in your go to recipes.

Look through the dessert recipes on any food blog and there's a pretty good chance you'll find something with chocolate and peanut butter. It's one of the most common combinations in candy bars and other sweets (not that I'm complaining).

What can't Sriracha do? You can use it to upgrade your ramen, spice up your candy, or even try one of various recipes to make your own. And if you want an easy way to add it to basically everything, you can make your own Sriracha salt, which is just as awesome as it sounds.
these techniques are little warm ups i love to use on a daily bases. it depends how my voice is feeling. singing is my passion. and if it yours, you found the right gal :)

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

I have been getting requests for this one since a really long time. So finally a few days back I decided to step up and create a video on nail care and help lots of girls out there who are facing nail issues on a daily basis.

THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Roughly five million years ago, humans split off from chimpanzees, who had in turn split off from gorillas five million years earlier.

As dedicated bicyclists are well aware, riding can be very dangerous. Now that daylights savings time has ended in the United States, darkness appears quicker, and the night is especially dangerous for cyclists because of the low visibility that drivers have. Not only is darkness a danger, but also fog, blizzards, and heavy rain—all wreaking havoc on the vision. To combat this, bikers attach reflectors: clear front reflectors, red rear reflectors, amber pedal reflectors, and clear side reflec...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Hello! This post will be about the special care your dwarf rabbit needs during hot weather. There are many ways to keep your pet happy. Step 1: Choose the Environment
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Having a healthy lifestyle is very important. In this video, learn how to do a forearm stand with Tara Stiles in her "Let's Get Physical" Challenge. First, lay your forearms on the ground. Make sure your elbows are directly below your shoulders. Have the rest of your body in plank pose (your feet on the ground and your body flat.) After a little bit, walk your feet back up so that your body now forms an arch with your butt in the air. Walk back to your plank pose and stay there. If you're loo...

This video will show you how to use MCedit to create flat land in your Minecraft world. Are you the type for wide open spaces? Land lots of land under starry skies above? Watch this video to learn how to make flatland in Minecraft with MCedit.

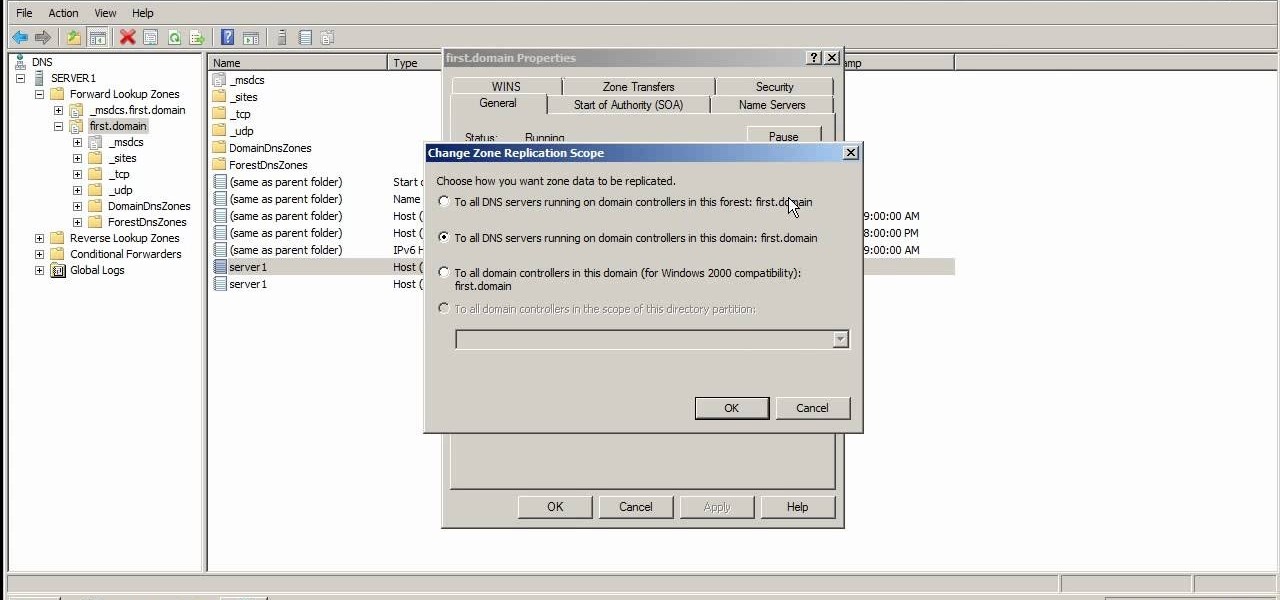
This video explains the different kinds of zones you will come across in Microsoft Windows Server 2008 DNS. The video has practical step by step instructions to managing these zones, as well as understanding their different functions and uses, and covers replication.

Fairy cakes are basically lovely little cupcakes adorned with pretty icing and "fairy dust" - AKA sprinkles - for a nice ethereal effect.