
How To: Create a shiny interface button in Photoshop
Perfect for your web 2.0 designs or site, or even another type of interface, this shiny button will add some depth and style to your design. See how to make one in Photoshop in this tutorial.


Perfect for your web 2.0 designs or site, or even another type of interface, this shiny button will add some depth and style to your design. See how to make one in Photoshop in this tutorial.

Watch this video an make a delicious melontini infused with three different types of melons. Use watermelon, honeydew and cantaloupe with premium vodka to make a delicious melontini.

This trick shows you how to remove the search assistant dog in Windows XP. You want to go to: Start, run, type regedit, go to HKEY_CURRENT_USER SoftwareMicrosoft Windows CurrentVersion Explorer CabinetState, create a new string and call it "Use Search Asst" (remember the Caps), give it the value "no".

Learn how to make two different types of vegan donuts: jam-filled donuts and chocolate long john donuts.

You won't believe its vegan, a creamy rich sponge cake that everyone will love. Serves: 12 approx

Learn how to use 17 warm up stretching drills for your feet, legs and knees. These types of exercises are important for atheletes and high impact, explosive activities.

Learn some terminology and topics that will help you be better prepared for your next trip to the lumber yard. Just a few of the topics covered include identifying different types of cuts, estimating board feet, and finding a good hardwood supplier.

Add storage space to your computer by either adding an additional drive or swapping out your old one. Note: This is for Parallel ATA type drives only.

For beginning DJs. Learn how to use and fine tune the pitch control. This method applies to all types of turntables, not just the Technics sl1200!

Dave shows us some unusual types of clematis with striking flower colors and shapes and resistance to disease. Any plants that are resistance to disease are a good choice.

In this video Chef Sanjay shows you how to make three different types of Indian fish pakoda. Sanjay is using mahi but you can substitute for your favorite fish or market availability.

This video is all about creating dolly shots. If you have ever wondered about how to use and control this type of shot, then let Israel Hyman show you. This is a great alternative to zooming in and out which is unnatural for our eyes.
Learn how to change the default action that the Firefox web browser takes when opening a type of file including .mp3, .midi, and others.

Learn the steps for making an easy shrimp fried rice, including a trick for frying the egg in the middle of the ingredients. You will need cooked rice, frozen cooked shrimp, frozen baby peas, green onion, olive oil eggs and low sodium soy sauce. Fried rice can be made with any type of protein - enjoy making this Asian dish for your family!

Your video footage does not need to come from a camcorder or iMovie HD. In this tutorial you will learn how to import other types of video into iMovie '08.

In this episode, The Shirtless Apprentice gives us some tips and information on how to use one of the most versatile and under appreciated tools in a videographer"s arsenal, the sungun! Matt compares two types of sunguns, incandescent and L.E.D., and weighs the benefits of each.

Jeff Schell shows you how to create a spinning headline or front page of a newspaper. You'll see how easy it is to build this special effect for any type of image or clip using a pair of rotation keyframes and scale keyframes, and by specifying your keyframes in reverse order.

Sample different types of threads and sewing machine settings to learn the best combinations for varying sewing projects and effects.

Unfortunately not everyone goes through the effort of making form fields on their forms. So rather than print the form out and fill it out by hand, use the Acrobat Typewriter Tool to click right onto the form and type right onto it without the need for form fields. In this video you’ll learn how.

Been trying for those 6-pack abs without much success? According to oodelboxTV fitness guru Wes Cole, odds are you aren’t working out the correct type of muscle fibers. What? Watch and learn what that means AND how to get a brick belly.

This video demonstrates how to work out your quadricep muscles using a leg extension machine. The video walks you through adjusting the machine to your body type and explains how to perform the exercises correctly.

This video demonstrates how to use a leg press to work out your quads and glutes. The video walks you through setting up the machine to your body type and performing the exercises correctly to avoid injuries.

Ironing can be a bit tricky, with so many different designers and clothing materials to choose from. This video shows you how to iron a blouse and skirt so each looks perfect every time.

Chef Chris Smith makes two different types of smoothies including a chocolate peanut butter and a berry smoothie usng berries, soy milk, tofu, banana extract and fiber fruit smoothie. Both demonstrations are low carb smoothies.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).

Between sending iMessages, jotting down notes, and crafting emails, you do a lot of typing on your iPhone. No doubt, you've been in the middle of an important task when everything comes to a screeching, obtrusive halt, where a rogue "Undo Typing" pop-up forces you to close it before continuing with your typing. Don't put up with the BS anymore — here's how to stop it.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.
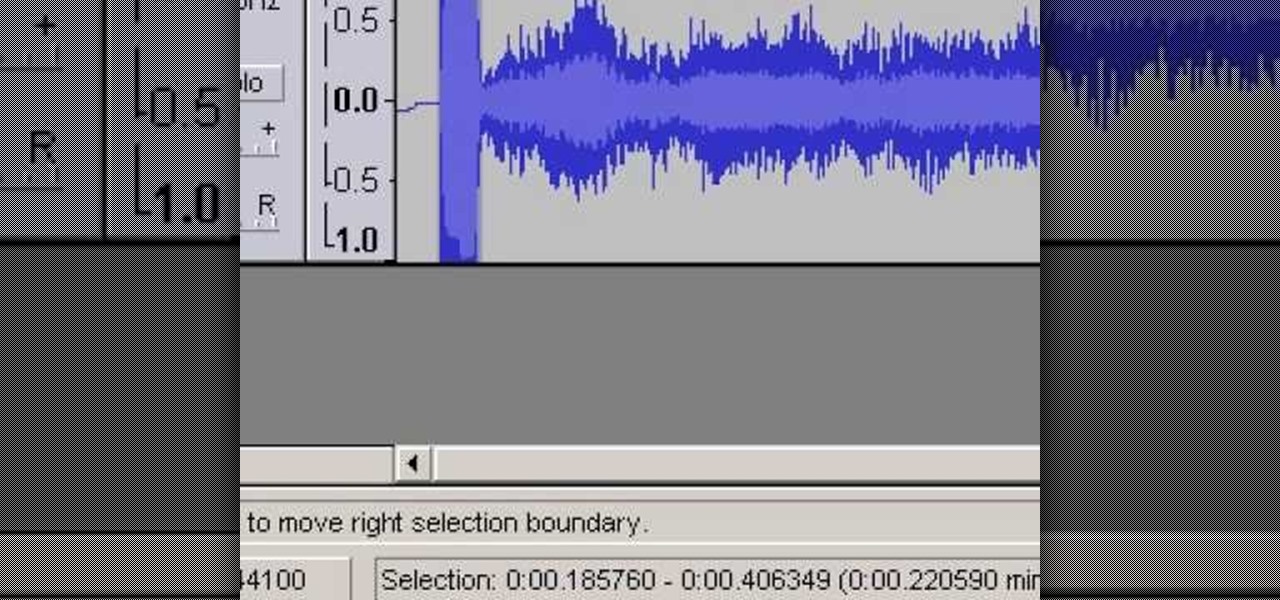
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.
Shake to undo is now the worst way to take back what you just typed on your iPhone. Among the many changes in iOS 13, Apple has updated text gestures, including how you select a word, sentence, and paragraph, copy and paste text, and undo and redo what you type.
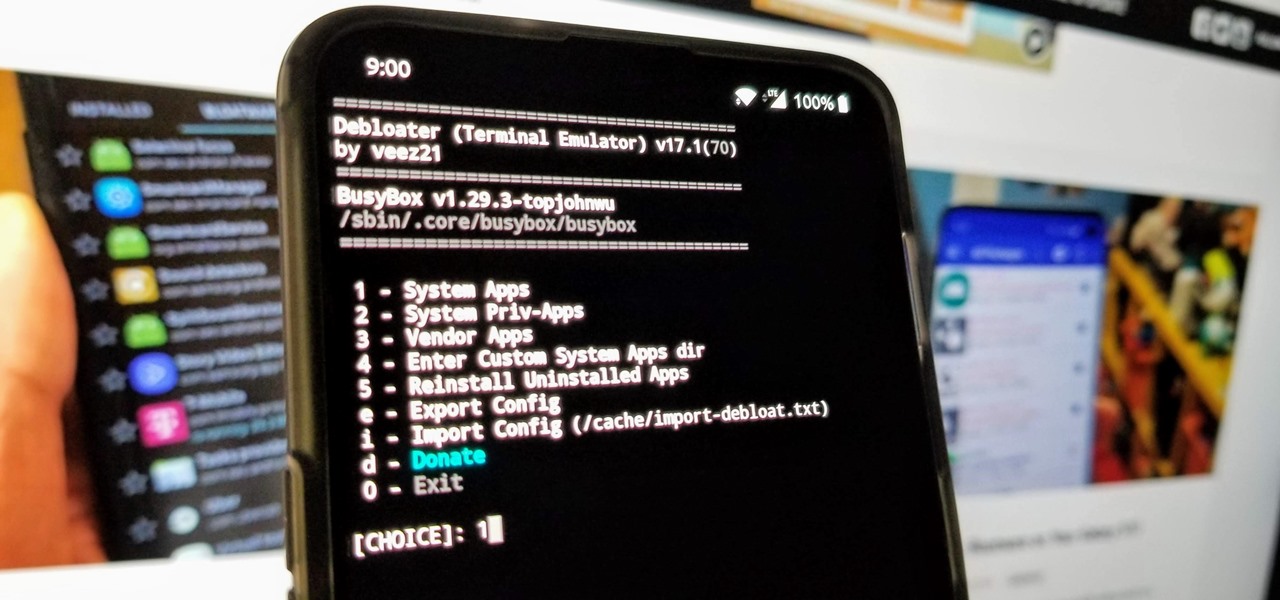
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.