Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

This video shows the two types of necklaces. First one is in Egyptian style and the second one is in Christmas colors :) You can use your own colors if you wish..

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.
This video will show you how to create a Twitter list for similar interest twits together. But if you want that twit from a special type of following or users will be bundled together then you have to create a list. You can isolate you favorite or useful twits from all twits coming by creating list in twitter. So please watch the video.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

This pattern may look complicated, but here I used only the Square knot :) Pattern looks like the stars or birds in the sky. You can use this pattern for different types of goals, for example: clothing accessories, Handbags, purses, cases, wallets etc..

This video will show you how to set finger print scanner for phone unlocking in Samsung galaxy S5. The finger scanner option allows you to register your finger print for unlocking your phone. This method of unlocking your phone saves your time over typing password. This way no one can open your phone except you. Watch the video and employ the tricks in your Smartphone.

This video will show you how to change downloading location from Google Chrome. If you download a special type of file often then you have to visit default downloading folder and move them to your preferred location. But you could set the downloading location to your preferred folder from chrome. Watch the video and follow all the steps carefully.

As the title says, you'll learn how to set up a prank that will end up with your victims having eggs on their faces.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

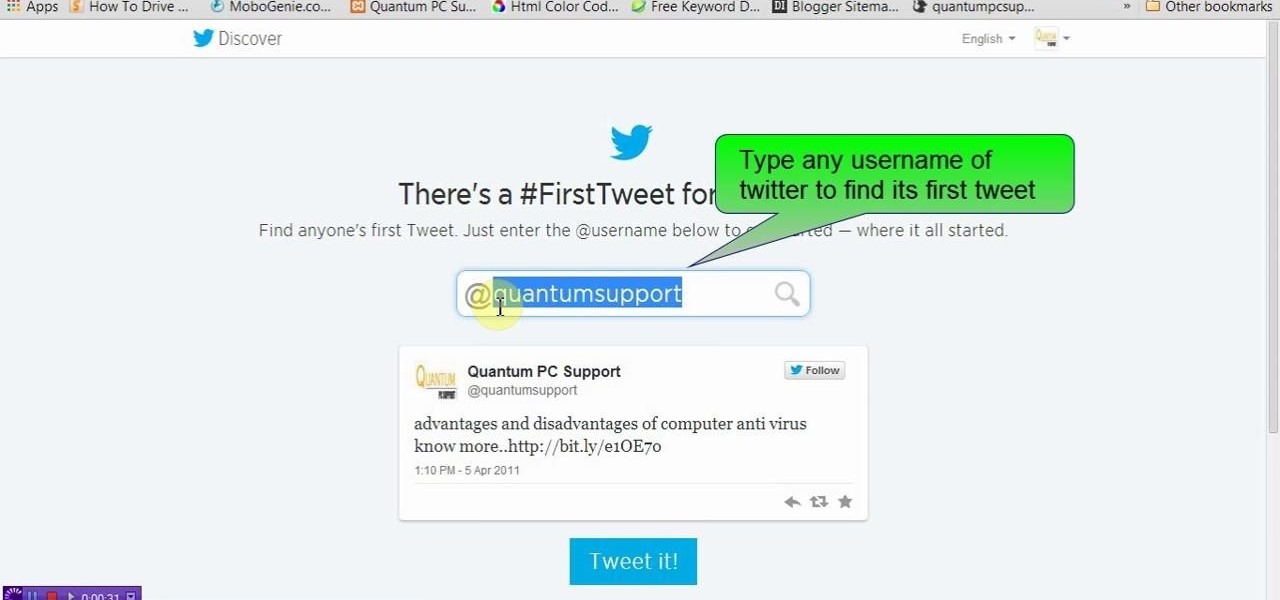
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

This is a video of how to use a can opener that's a safe can opener, which will not leave sharp edges. You can also reuse the lid to put back on top of the can if all of it's contents are not used.

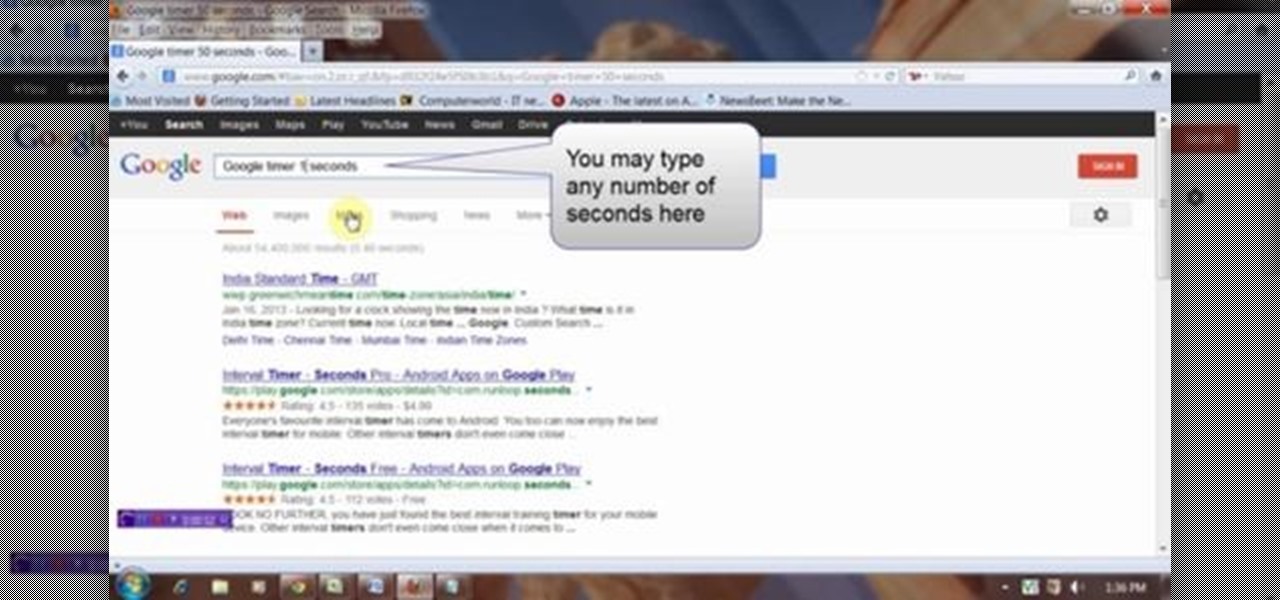
This video will describe you how to set Google online timer. Now you don't have to bother about the timer or stopwatch. You can bring a timer in your Google.com home page. You have to type a command "Google timer 50 seconds" and a timer will start automatically. You can stop and reset the timer whenever you want. Watch the video and employ it yourself.

Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face.

This video tutorial shows How to make a Macrame Lizard, Nice accessory for the summer season! You can use this Lizard for different types of goals, for example: keyring, keychain, pendant for necklace, earrings, decor and accessory..

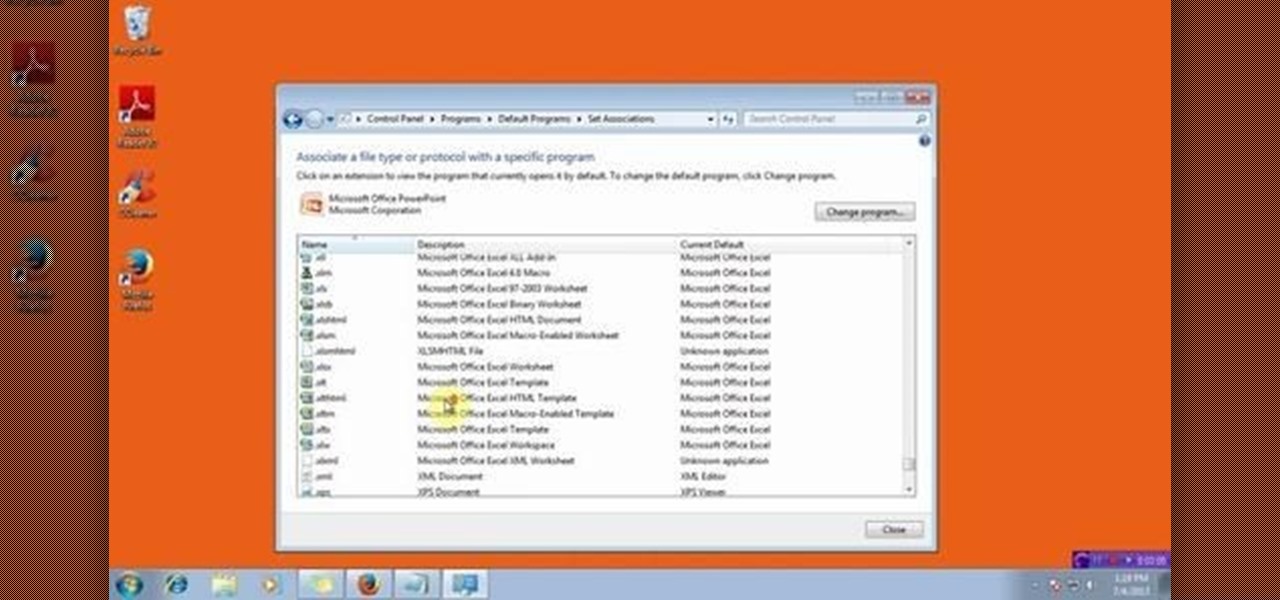
This video will show you how to change the default program for a Specific File Extension in Windows 7.

Welcome back, my greenhorn hackers!

You can use this beautiful macrame pattern for different types of goals, for example: Handbags, cosmetic bags, clothing accessories, purses, cases, wallets, bracelets, etc..

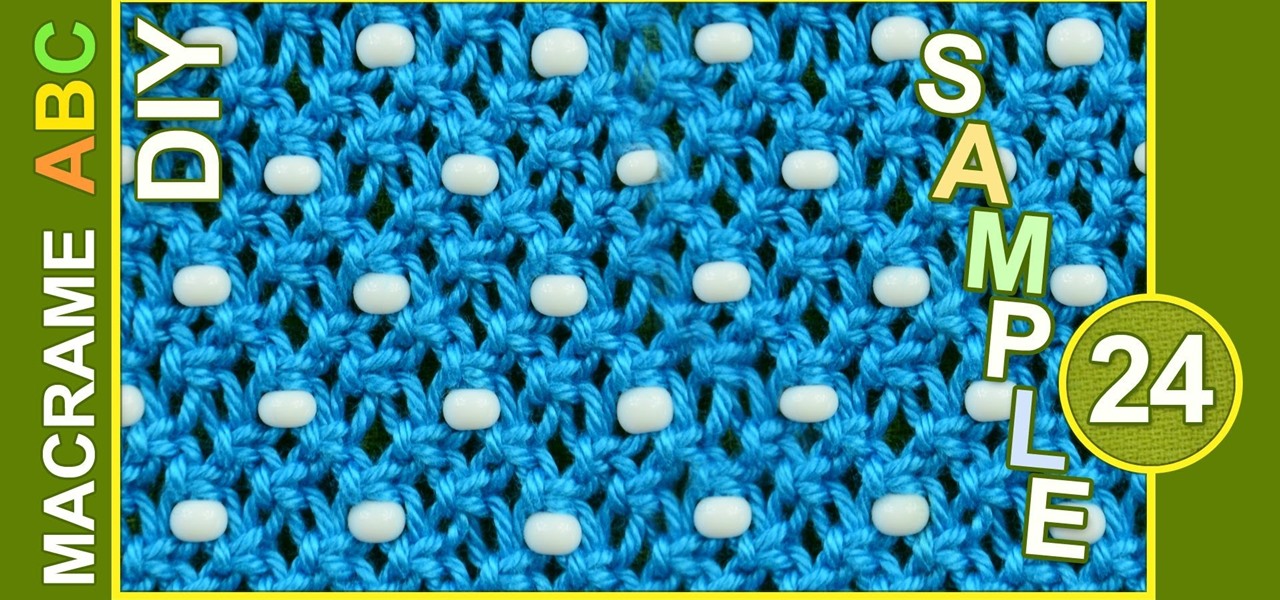
Easy Macrame pattern with beads. You only need to know Square knot and you can use this pattern for different types of goals, for example: clothing accessories, Handbags, purses, cases, wallets etc..

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

You can use this pattern for different types of goals, for example: Clothing, handbags, tablecloths, coasters etc ...

Today we show you how to make horns for a costume. We specifically made horns for Maleficent, but you can shape and paint yours to like any type of thing.

Friendship Bracelet Tutorial for Beginners - Rag Rug, Easy Pattern One type - different bracelets - 3 samples...

This pattern with flower motifs looks very good! Maybe this tutorial is not for beginners, but you can use it for different types of goals, for example: Bags and Handbags, purses, tablecloths, coasters, clothing, wallets, phone bags and phone cases etc..

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

This is a tutorial how to make an easy ZigZag Macrame bracelet. You can use it as a friendship bracelet. Before you start you should know the basic macrame knots. There are 2 types of knots, the double half hitch and the reverse double half hitch. These knots are very easy to make. Don't worry and let's go make these Zigzagging waves :)

This is for those people that want to create a fire in a camping situation, survival situation, flare type alert to other that you are lost, or simply for entertainment.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Henry shows you how to install a 3 tab asphalt shingle roof in this video. This video covers everything from the type of roofing felt to use, making the starter strips, layout with chalk lines right through to making and installing the ridge caps.

Depending on where you live, the type of skirting option you choose is important (Skirting is the base trim around the shed). Henry shows you three different ways to do this including the Drip Cap options for wetter climates.

Oysters are a bit of an acquired taste, you really need to try a few times to really begin appreciating them. Then once you get into it, you realise there are so many different types that you need to get to know them one by one.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

This web design Tutorial will walk you through process of linking to files on your computer. You can link file types including but not limited to Microsoft Word, PowerPoint, PDF, Videos and so on for download on your website.