
How To: Properly cite a website in MLA format
Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.


Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

Open Jungle Magic and then open up Cheat Engine, click Browse and find the process that is running Jungle Magic (ex. firefox.exe). Click Open and in Value Type change to Array of Bytes, copy the cheat code in Hex box and press First Scan. Select the value from the left area, now in the bottom area change the value to the cheat value. Go to the game and start to play, you will see that now you have unlimited time. Go back to Cheat Engine and click New Scan, change the value type to 4 bytes, un...
The future is now, which means you can do crazy things like connect to the world wide web through your Xbox 360 and PS3. Cool, right? Definitely. But before you start surfing the Internet you'll need to adjust the settings on both your computer and gaming console. This instructional video tutorial demonstrates the process and offers helpful user tips in setting up an Internet connection on your video game system using Microsoft Windows XP.

This video explains how to send the Text message to any where specifically to mobile using Yahoo mail. To do that first type the "www.yahoo.com" or "www.yahoomail.com" in the browser. And then choose the Mail option from the front page of the yahoo website. From that click the sign in option, and give your Mail id and password in the yahoo sign in page now you will logged into your yahoo account. Into your account you will have the "New" menu option on left to corner. From that you have to ch...

Ceramic cups can have different types of handles, depending on their function or style. Learn about cup making and three pottery handle types in this free ceramics video series.

There's no default keyboard on the Apple Watch, but watchOS has another way to let you type text out for emails, messages, music searches, and more on the small display, and that's Scribble. With it, you simply draw letters and other characters on the screen with your finger, then your watch converts that into plain text. However, it's not perfect, and getting the nuances of regular typing can be tough.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

There are tons of apps to help you create unique and compelling posts and stories on Instagram, but you already have the tools you need to make something eye-catching. You can insert line breaks in captions, create translucent overlays for photos, rainbow-up your story font, and even add a 3D text effect to your stories.
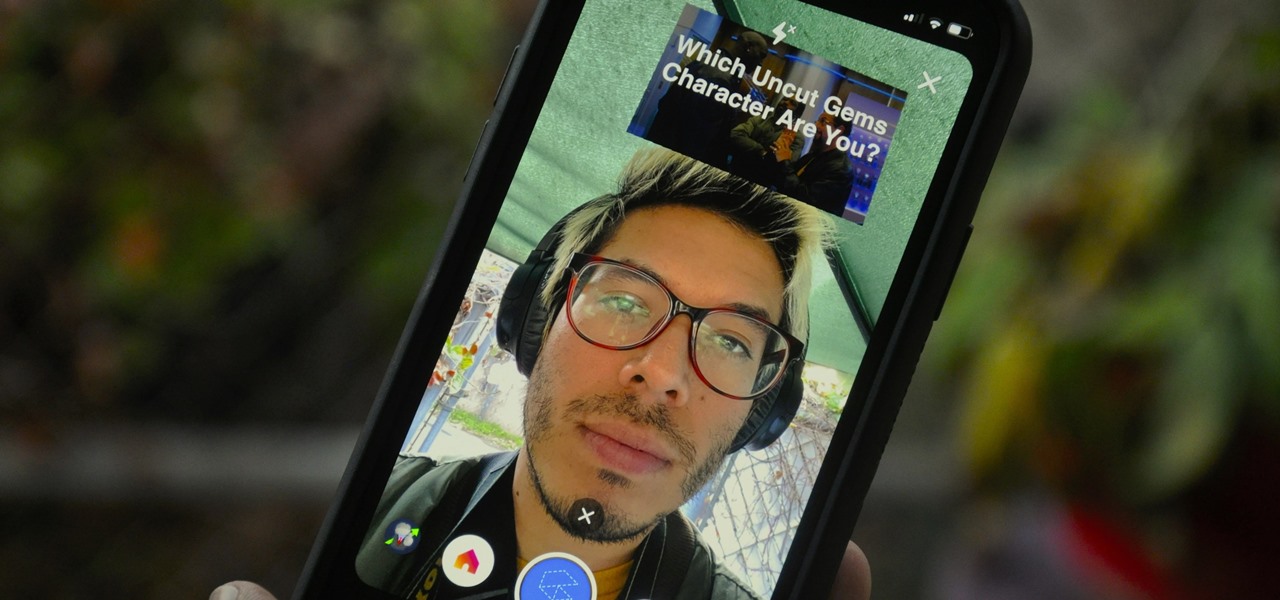
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

Your computer has a lot of physical keys. Your iPhone has, at most, four hardware buttons, none of which are used for typing. That means the software has to power the same typing tools you'd find on your Mac or PC, only on a touchscreen. As such, some features, such as the indent tools, are buried so deep you may not even know it's possible to "tab" forward and backward.

Niantic's Harry Potter: Wizards Unite offers players an augmented reality look into the world of witchcraft and wizardry. The Wizarding World and Harry Potter novel series is full of unique and interesting characters, which is why it makes sense that Wizards Unite offers you to take the role of one of three "Professions" — Auror, Magizoologist, and Professor. The question is, which one do you pick?

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.
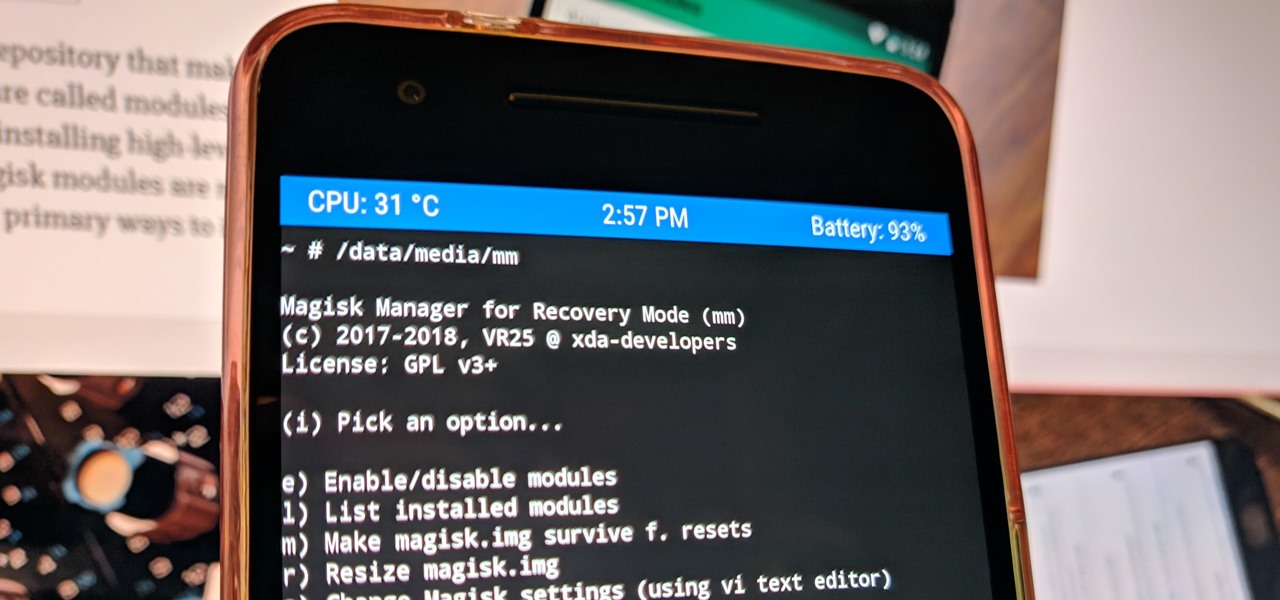
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.
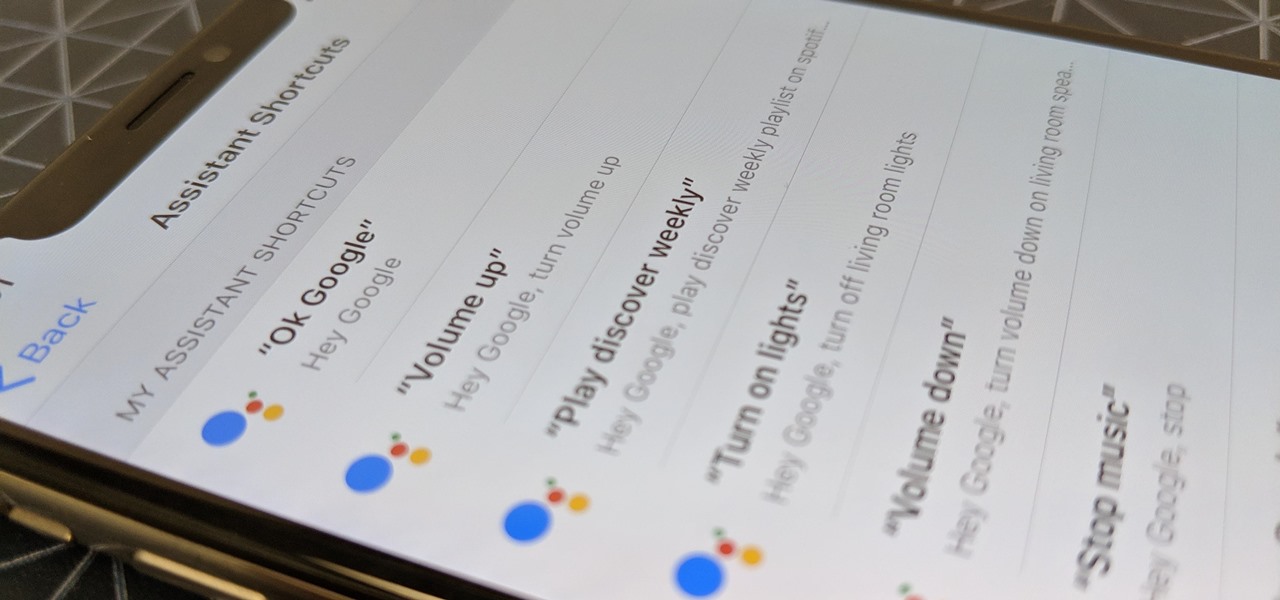
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

If you ask Siri to check the weather on your iPhone right now, you'll get information from the stock Weather app in iOS — even if you have and prefer other weather apps installed. But that doesn't have to be the case. Thanks to Siri Shortcuts in iOS 12 and later, you can set specific phrases that Siri will respond to for any compatible weather app you want.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

If you're looking for an alternative iOS keyboard for your iPhone, look no further than Gboard. The Google-made keyboard is bursting with features like web search, Google Maps, GIFs, and more. Now, Gboard is adding a new feature that'll make it easier to find the perfect emoji.
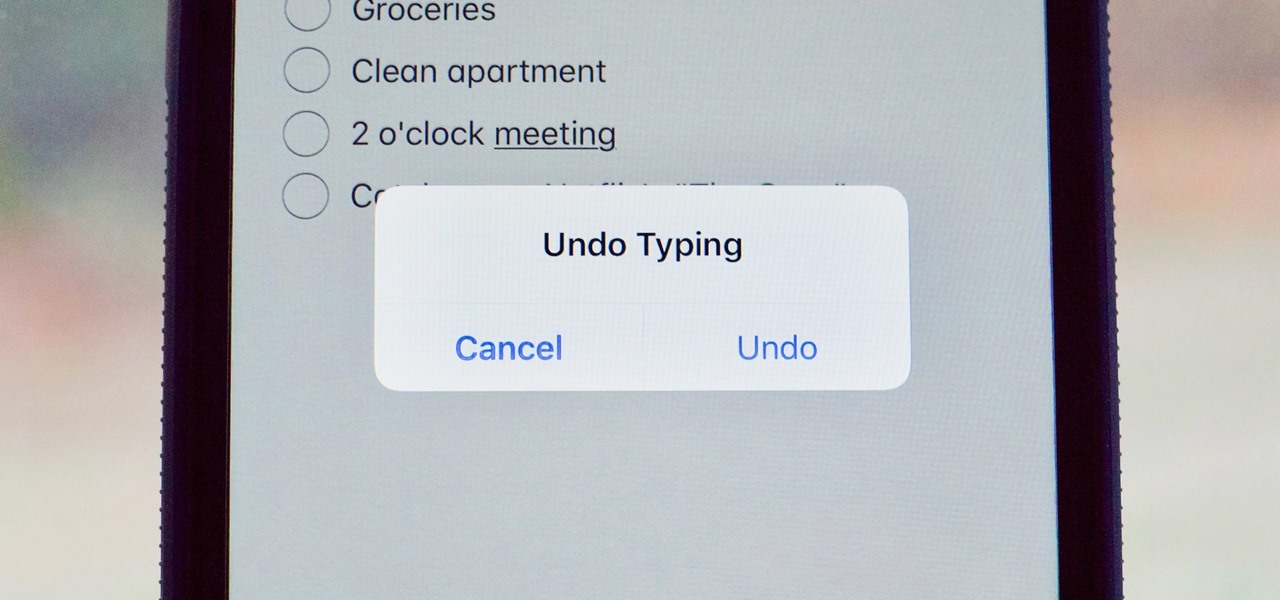
Many of us use the Notes app to jot things down in a hurry. Most of the time, that's no big deal. However, the faster the typing, the higher the chance of error. If you happen to make a typo, or if you accidentally delete that chart you worked so hard on, there's an easy way to undo the changes.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

People love emojis, it's a scientific fact. So an app that places poops, smileys, and ghosts into social media videos should, in theory, be the most popular app ever. That's likely the reasoning behind the new Holocam app, which is available for $0.99 in the iOS App Store. Sure, Snapchat and Instagram offer users editing tools to stick static text, emojis, and drawings on top of photos and videos. However, Holocam ups the ante by placing fully three-dimensional emoji, text, and drawings, as w...

Siri can definitely be helpful when you need it, but you may not want the entire world hearing Siri's responses in certain situations. If you're in a library, meeting, class, or another scenario where your iPhone's voice assistant would do more harm than good, there's a way to keep Siri silent ... but it's tricky.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Whether you're hard of hearing, watching a foreign movie, or just like reading along when you're watching a TV show or film on your smartphone, Netflix includes captions and subtitles that you can use. Best of all, if you don't like the way the default captions and subtitles look (color, background, font, or size), Netflix has your back.

If you are a small account looking to get more followers and likes, then getting past Instagram's 30 hashtag limit may be what you need to increase engagement. While I don't recommend posting so many hashtags in your caption (it looks terrible), there are certain ways to add tags and still make your posts look super clean.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Most of us equate feeling cold with catching a virus—but we've also heard plenty of debunkers proselytizing that being cold isn't what gives you the flu.

Joyce Kuo of Nijie Technology released a video showing a group fighting it out Dragon Ball Z-style in a restaurant, but instead of Goku, Piccolo or Vegeta, we have two horse-headed young ladies shooting fire and other elements at each other.
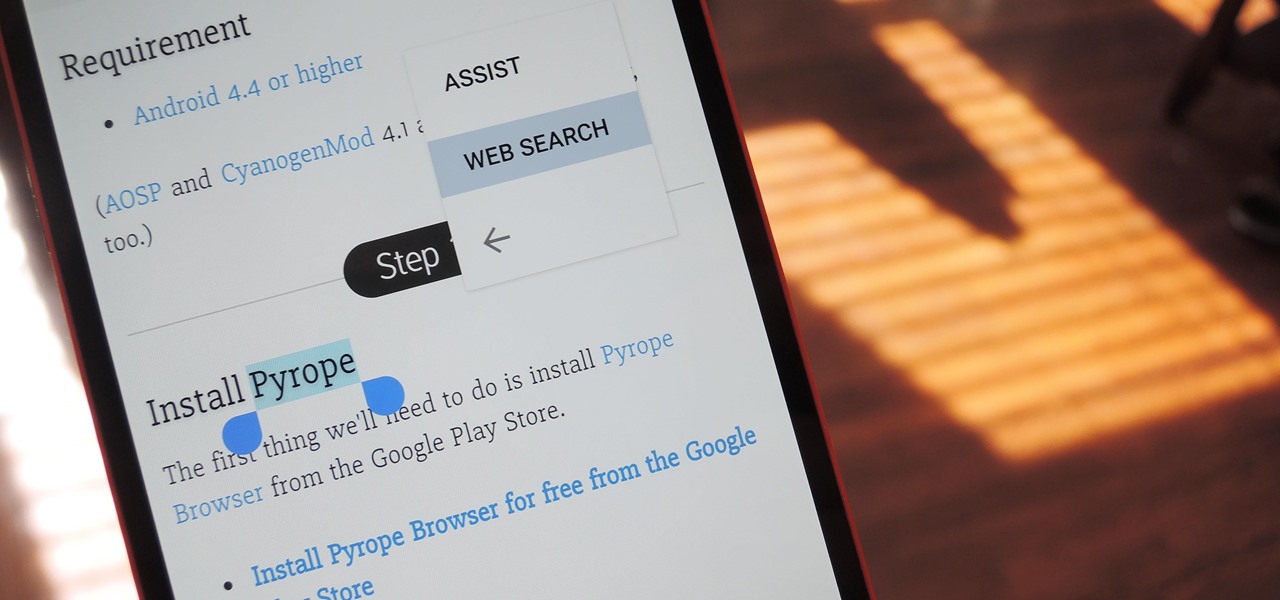
Chrome's text selection interface is pretty nice, but it could definitely use some improvements. For instance, when you're in Incognito Mode, you can't perform a web search for words you've highlighted. And when you're typing out a forum post or using any text input field, for that matter, there's no option to search or share any of the text you've written.