The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

The theme running throughout most of this year's WinHEC keynote in Shenzhen, China was mixed reality. Microsoft's Alex Kipman continues to be a great spokesperson and evangelist for the new medium, and it is apparent that Microsoft is going in deep, if not all in, on this version of the future. I, for one, as a mixed reality or bust developer, am very glad to see it.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

As first reported by Korean media outlet Yonhap News Agency, Samsung has issued a global recall for all of its Galaxy Note7 models (except China, it seems). This unprecedented move will surely do serious damage to the Note brand, and even Samsung itself.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

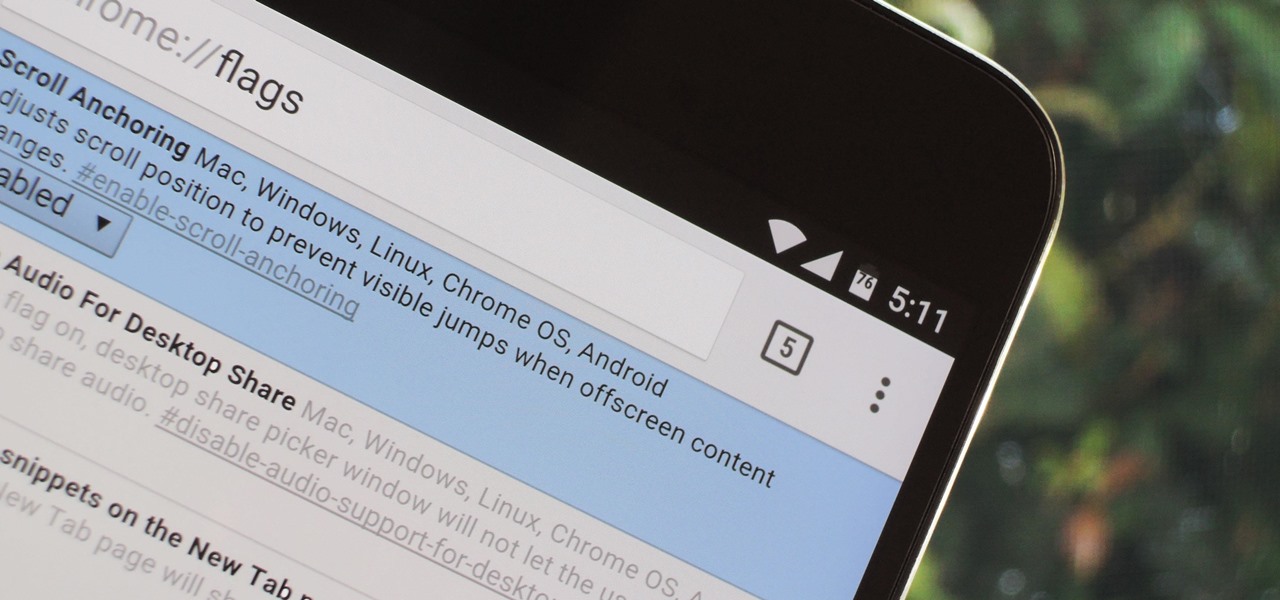
Google's Chrome browser comes pre-loaded on the vast majority of today's Android devices, and it's one of the fastest, most stable, and useful browsers out there. But it does have one major annoyance—while a page is loading, you'll see a link, then reach to tap it, but an element further up the page will load, and the link will jump out from underneath your fingertip.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

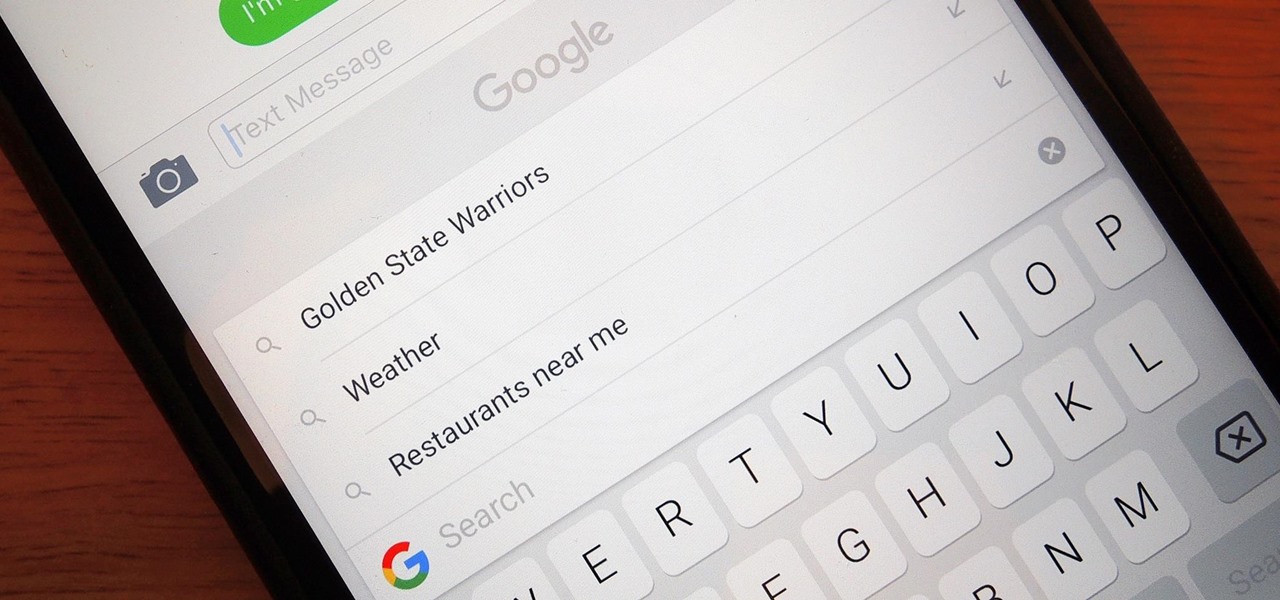
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

One of the more annoying parts about cooking or baking at home is dealing with sticky ingredients. You scrape the peanut butter out of the jar and into a measuring cup to make sure you have the right amount for your recipe, then scrape the correct amount into the bowl you're cooking with.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

Google's design chief Matias Duarte has gained fame and acclaim for his recent visual revamp of the Android operating system, and now, Google's starting to incorporate this Material Design styling into more of its products.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, and more so if you plan on cooking meals over the flames.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

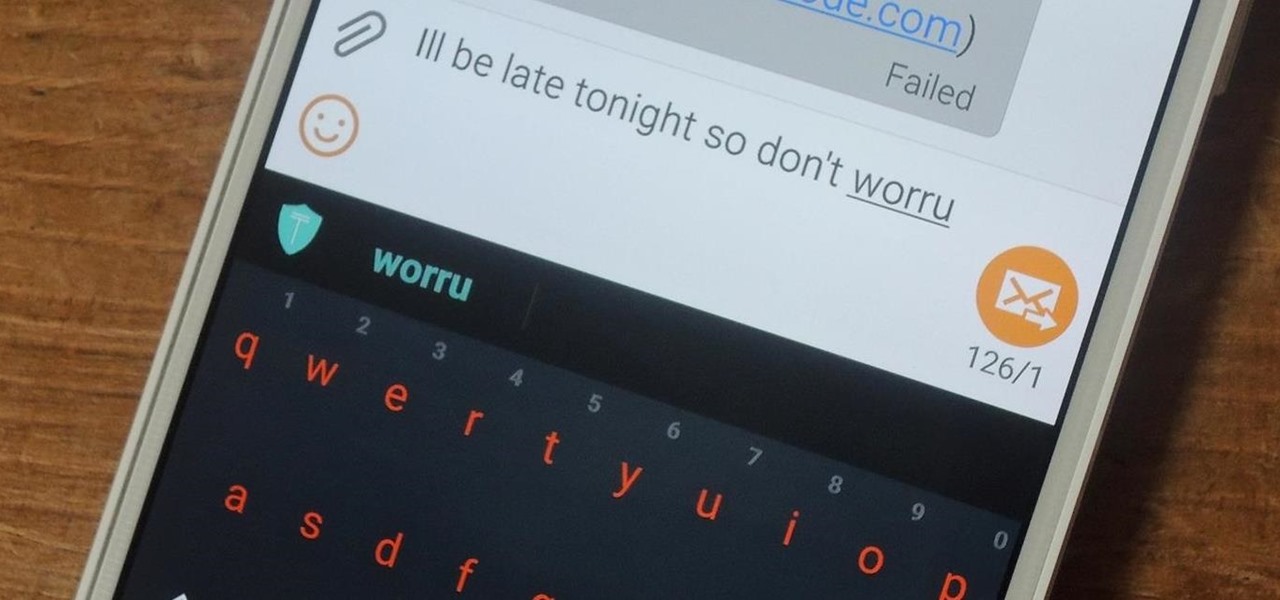
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Before heading out on a hike, or any excursion for that matter, it would be wise to take a map with you just in case you get lost while on your quest.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

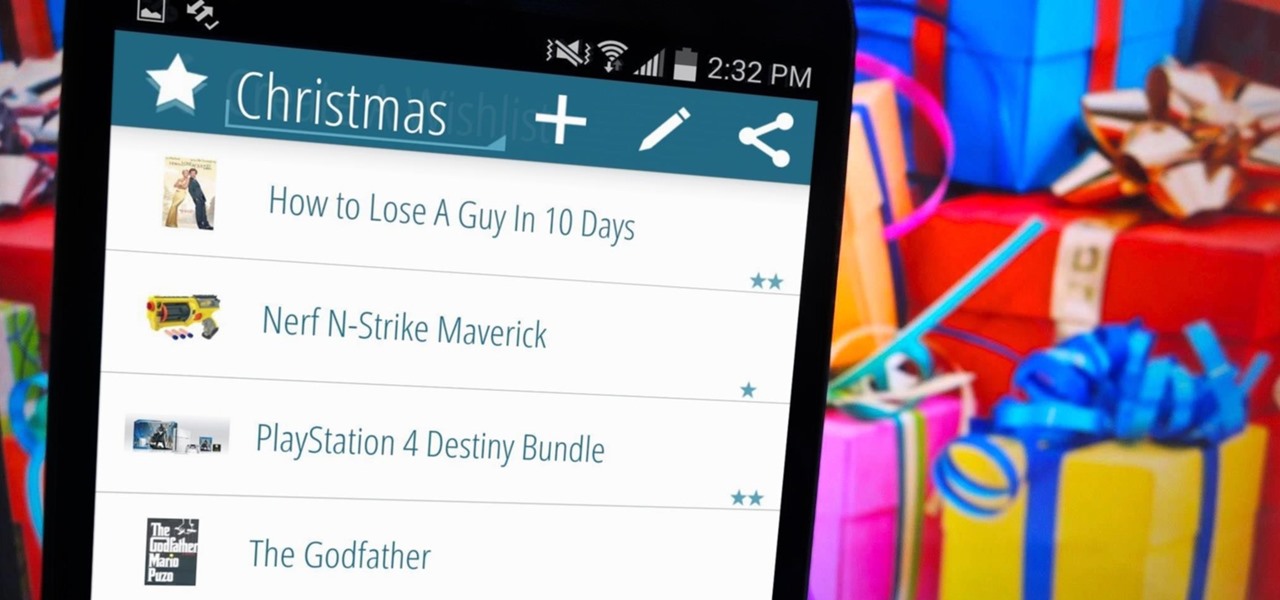
I love the holidays, but man am I sick of receiving oversized sweaters as Christmas presents. As well as people think they know us, their gifts often say otherwise. Instead of stocking up on useless items and articles of clothing you'll never wear, it's high time to create a wish list that's easily sharable amongst family and friends, and it's incredibly easy to do on Android.

I'm the type of person that rarely has an audible ringer enabled on my phone. Haptic feedback (vibration) is enough for me... most of the time. When my phone isn't in my pocket, I become the type of person who frequently misses calls and texts—and no one likes that person.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

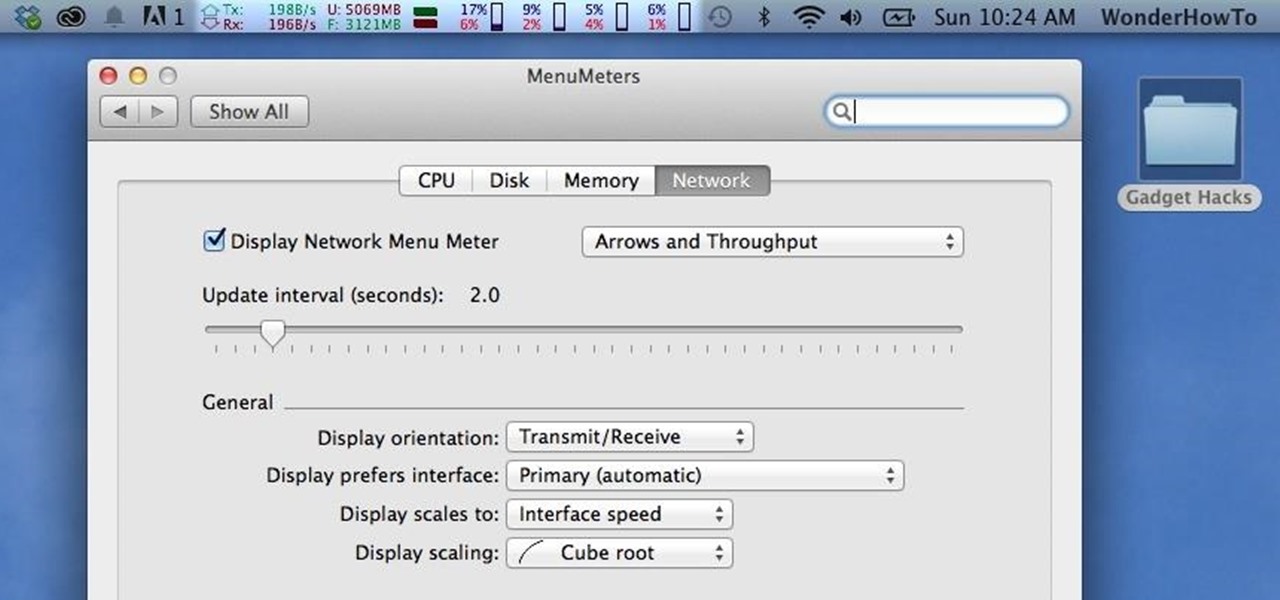
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.