Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

In this video, doctors can learn how to perform a full cardiac examination on a patient. The very first thing a doctor should do is visually inspect the patient, because there's a lot that can be gained by simply examining by eye. You'll want to carefully examine the respiratory pattern of the patient, the nature of their precordium, the anterior part of their chest over the heart. Feeling the pulse is also necessary when starting out this heart exam. To learn more, watch the full video.

Andy Field shows us a trick that has little set up and carries a high reaction. This trick is called the wrong prediction trick. You will need a deck of playing cards a wallet and a black magic marker. Take out the queen of hearts and write "9 of clubs" on the back of it. Stick the card in the wallet face side up this will be called the "force card". Find the 9 of clubs in the deck and slightly bend it to give a slight concave effect. Do the same to the queen of hearts. Fan out the deck face ...

First of all you need to a set up deck. You need to learn about two things. First you need to learn about calculating the numerical value of the card and also work out the suit the card. First take out a card and lay it face up. This is 4 of clubs. The rule here is that next card shall be 3 more in numerical value because this deck is a set up. So pick the next card that is 7(4+3) of hearts then 10 of spade (10+3) and then king of diamonds (10+3). Now remember the phrase "chsd", c for club, h...
Worried about a zombie apocalypse? Of course you are, we all are! This tongue in cheek video divulges the steps you'll need to take should zombies begin roaming the earth. Using clips from horror movies, this video shows you the right way to hide from zombies and even explains who you can trust. Learn what weapons work on zombies and how to cripple them and most importantly, destroy their brain! Nobody wants to get bitten by a zombie, learn how to escape, travel and even how to recognize if o...

The heart needs exercise just like any other muscle. Live longer and healthier by pumping it up! You Will Need

This nail art is a perfect look for Valentine's Day. Give the tips a pretty scalloped red tip, and then add a little white heart onto each nail tip. You can use pink instead of red and it'll still look the same.

We know it feels like you're surrounded by a wall of pink and red on Valentine's Day, especially when you enter any retailer, but you have to admit these two colors evoke quite the aura of romance.

How much do you love your amor? They say love can't be quanfied in sheer numbers or even words, but we think this wheelbarrow, filled to the brim with loads of hearts, will do the trick for the time being.

We know that you're probably still reeling from the winter holidays, but lo and behold Valentine's Day is just around the corner. While indulgent gifts like a massage or trip to see a musical are best, when it comes to Valentine's Day cards handmade cards are often the most appreciated.

Whisper sweet nothings to your Valentine this Valentine's Day by making him or her this adorable origami heart. You can tuck a message like "Happy Valentine's Day" or "I Love You" inside for a personalized and sentimental touch.

Looking for a new gift idea for Valentines Day, your anniversary, or just a gift for that special someone? Well, try this great fancy balloon heart! All you will need is one of those straight balloons and a little time and patience! In this video you will get a full tutorial on how to make your own!

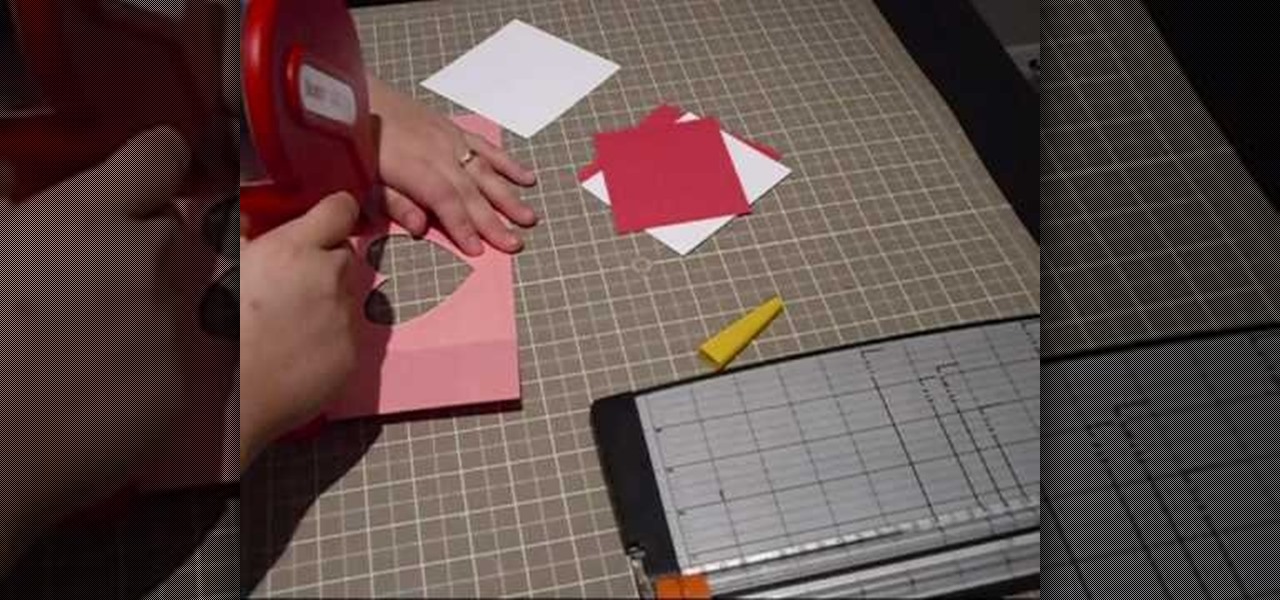
In this video, we learn how to make January thank you notes with Stampin' Up. First, you want to choose what you want your notes to say. You can use a small card stock that is 3" x 3". Then, use a border hole punch and apply it on in different colors you prefer. After this, you will want to stamp on a message that says thank you in black on the front of the card. Next, you can lay a heart punch out on top of the card to give it more personality. You can also place the heart on first and let t...

Want to know how to play Céline Dion's "My Heart Will Go On" on your piano or keyboard? Learn how with this free video piano lesson. While this tutorial is best suited for intermediate players, pianists of all skill levels can play along given a little sticktoitiveness. For more information, and to get started playing this great movie theme on your own keyboard instrument, watch this how-to!

In this clip, learn how to make one of the tastiest and easiest dishes you will ever cook - arepas! Arepas are basically mini sandwiches that come from Venezuela. All you really need is a bit of oil and PAN cornmeal, and then stuff it to your heart's desire.

This is the third mission in Battlefield Bad Company 2 called the Heart of Darkness, where you need to follow your unit through the ruined village. But first you have to survive the helicopter ride with the hippy pilot. You need to destroy the M-COM stations to succeed in this mission. Watch this video walkthrough to learn how to complete the Heart of Darkness mission in Bad Company 2 on the PS3.

Learn how to make a simple heart shape with twisting balloons, skill, and practice! Your Balloon Man, Mr. Fudge, is full of balloon tricks! Be sure to find other balloon videos on WonderHowTo from Mr. Fudge teaching everything from animals to planes! In a few twists and a few ties, you'll be an expert balloon artist in no time!

Real flowers are beautiful, but they don't last very long. In this tutorial, learn how to solve the problem of wilting daisies with these fabric flowers! In this video, you will see exactly how to create three different types of fabric flowers and accessorize to your heart's desire.

This video explains the method making heart shaped cupcakes or Valentine Day's cupcakes. At first take the mix here the moist deluxe cake mix is used. Using that mix make the cupcake mix, for a particular pack of mix 3 table spoon of oil is added then add egg white to the mix. Then to the mix pour some water of about half or quarter of a glass. The water poured mix is mixed with a mixer. Then pour the mix in the cup cake plate placing a cup cake paper in it. Then shape it in the form of heart...

This is a video how to fold a heart from drinking straws. It requires a pair of normal drinking straws(Try not to use hard straws,eg:fastfood restaurant straws are pretty hard!) You can purchase specially made straws from craft shops in many colors!

Craft a crazy three dimensional Slinky-esque heart shaped card. Perfect for Valentine's Day or Mother's Day.

How to find the "Heart of Liberty City," an easter egg inside of the Statue of Happiness in Grand Theft Auto IV (GTA 4).

Learn how to make a cool little heart shaped cup out of two pieces of paper and some folding and cutting. Similar to origami, the Japanese art of kirigami requires the use of scissors.

This guy teaches you how to twist a balloon into the shape of a heart. Very simple process, very fun shape, and it only requires one balloon.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.