Let’s try to thread the needle, as in give a choke hole. First get your opponent down on the mat facing upwards and sit in the mountain position. Hold your opponent's left hand with yours around his head to block him/her. Get your right hand through your opponent's left hand (needle in the hole) and push your chest towards the ground. This will put pressure on your opponent. It will help in your attack as well as defense techniques.

In this tutorial, viewers will learn how to use the synthesizer functions of the Yamaha PSS-780 keyboard. Starting with the basic piano voice, the presenter shows how this can be modified to create a new sound. He shows how the attack rate of the sound can be modified with one setting, how the modulation button affects the tones of the sound, and how sounds can be further modified with the frequency control. The presenter concludes by noting that with practice the user will learn to create ot...

Want tour-like spin on your swing? There are several keys to imparting tour-like spin on your wedge shots, including proper set up, a correct angle of attack, and quality contact. Tim Mahoney, Director of Education for Troon Golf, explains these keys and how you can make them part of your game.

This is a Cheat Engine guide on how to hack this flash game - P.O.D. Kongregate Acheatment shows you how to hack P.O.D. with Cheat Engine (09/23/09). This P.O.D. cheat will give you a level hack.

Cary Kolat demonstrates wrestling technique for collegiate defense. This covers defending single leg attack on the mat. Coach Kolat shows you how to practice funk roll same side as single leg move

Learn how to deal with a black bear or grizzly encounter with Shannon Davis and Ted the Bear. Black bears are distinguished from brown bears by lack of a prominent shoulder hump; a Roman profile or sloping nose and forehead instead of a dished forehead; and shorter, thicker claws for climbing versus longer, more slender claws for digging. Although brown bears are generally bigger, size is not a dependable indicator. Also, fetal position is often recommended as opposed to lying prone as shown.

You never know when you'll have to defend yourself against one of these bloodsuckers, so be prepared to bring a vampire to his knees. While you may not believe in vampires, there are those that do. In any case, prepare now for a hypothetical attack from the un-dead and you won't have to kick yourself later. You will need garlic, a cross, rice, grain, or seeds, holy water, a wooden stake, an axe, matches, and some water. Watch this video survival training tutorial and learn how to fight off a ...

Grandmaster Alexandra Kosteniuk teaches you how to... you guessed it, play a game of chess. This chess video tutorial will show you how to take the initiative in a chess game to win.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Mobile augmented reality company Snapchat now has a special option for romantic message exchanging this Valentine's Day, a day which, incidentally, happens to be the first one in 116 years where Sweethearts, the original heart-shaped candy, will be unavailable for purchase.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

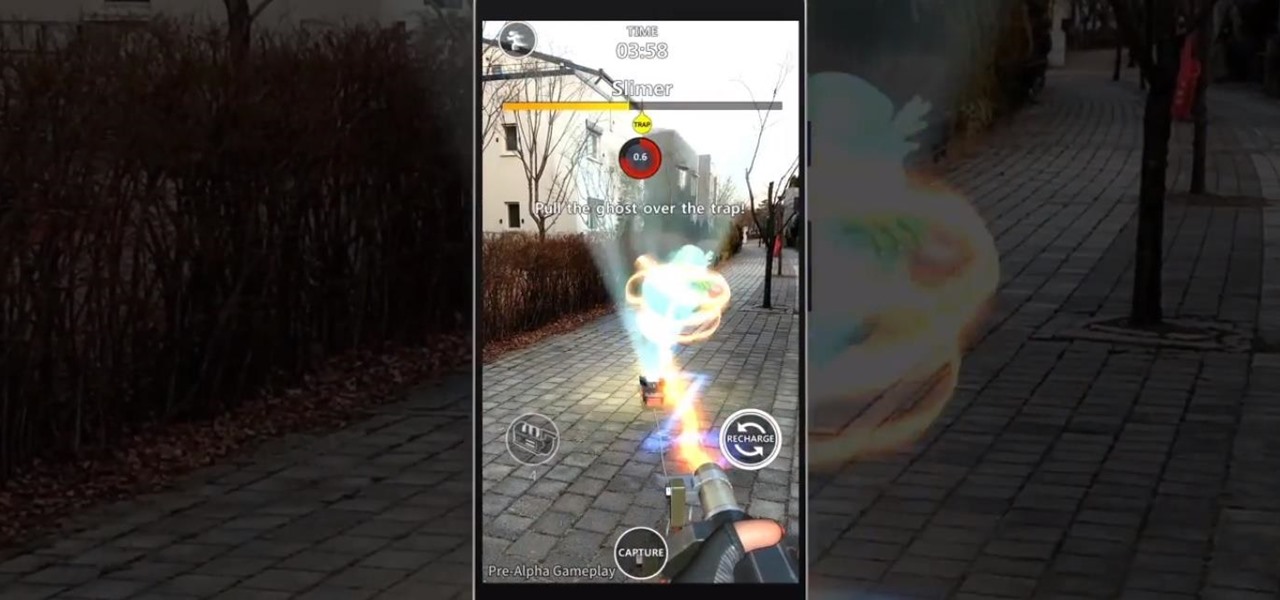
Sony's Ghost Corps, the caretaker of the Ghostbusters franchise, just released some pre-alpha gameplay footage from the upcoming Ghostbusters World location-based AR game to whet the appetites of would-be hunters of the paranormal.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

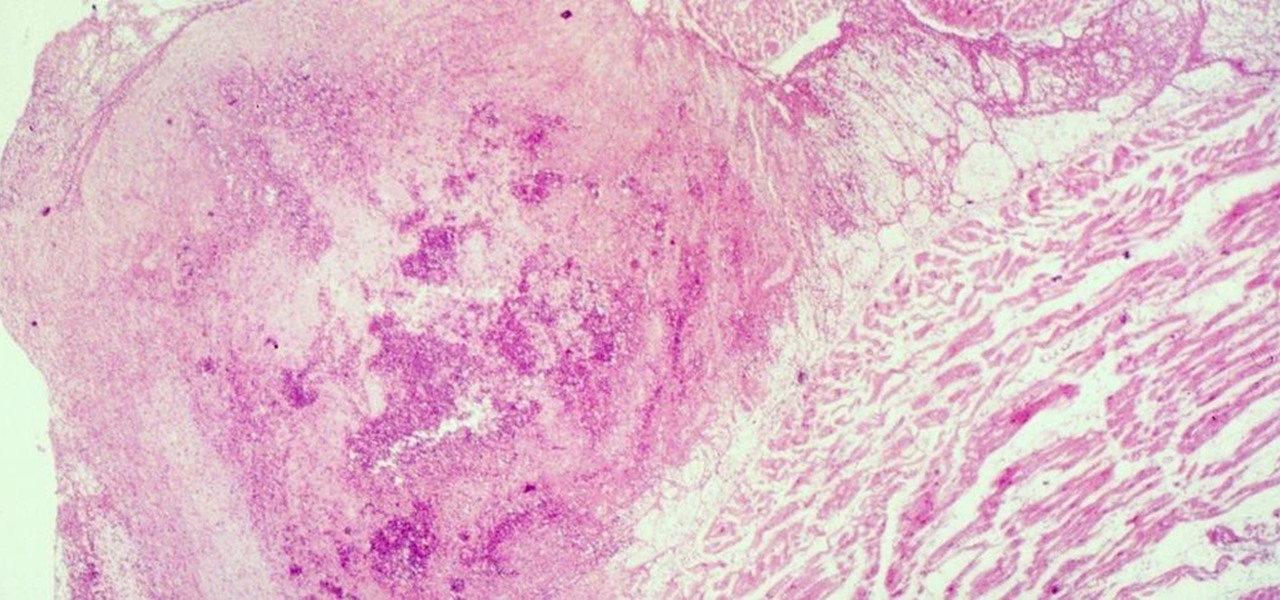
Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

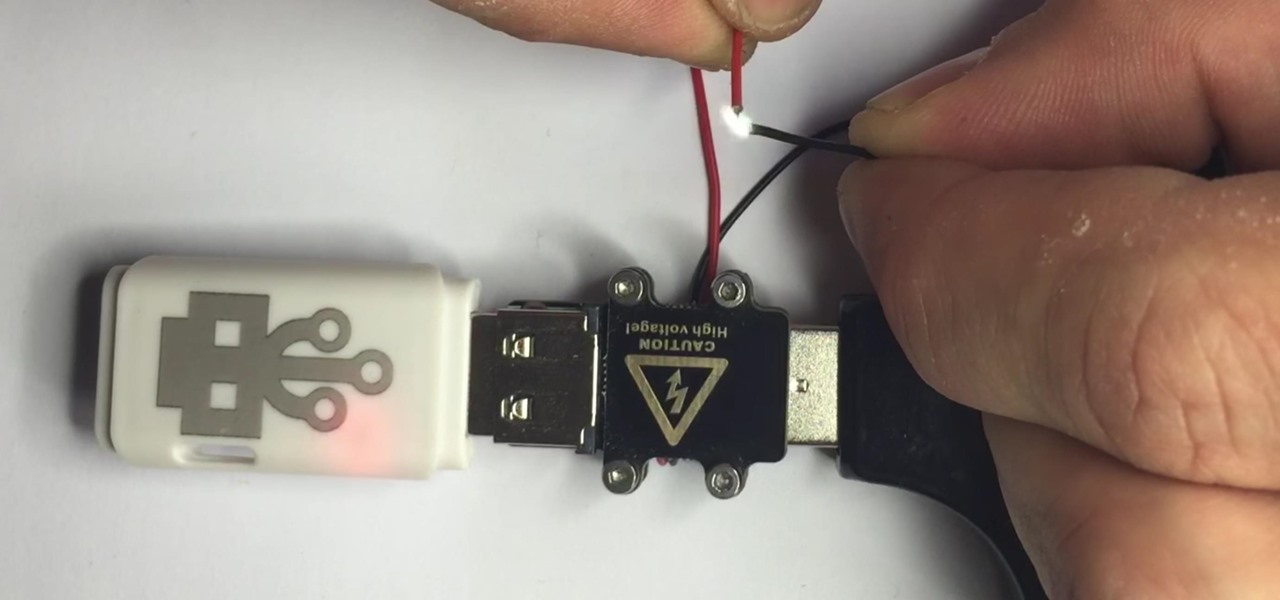
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

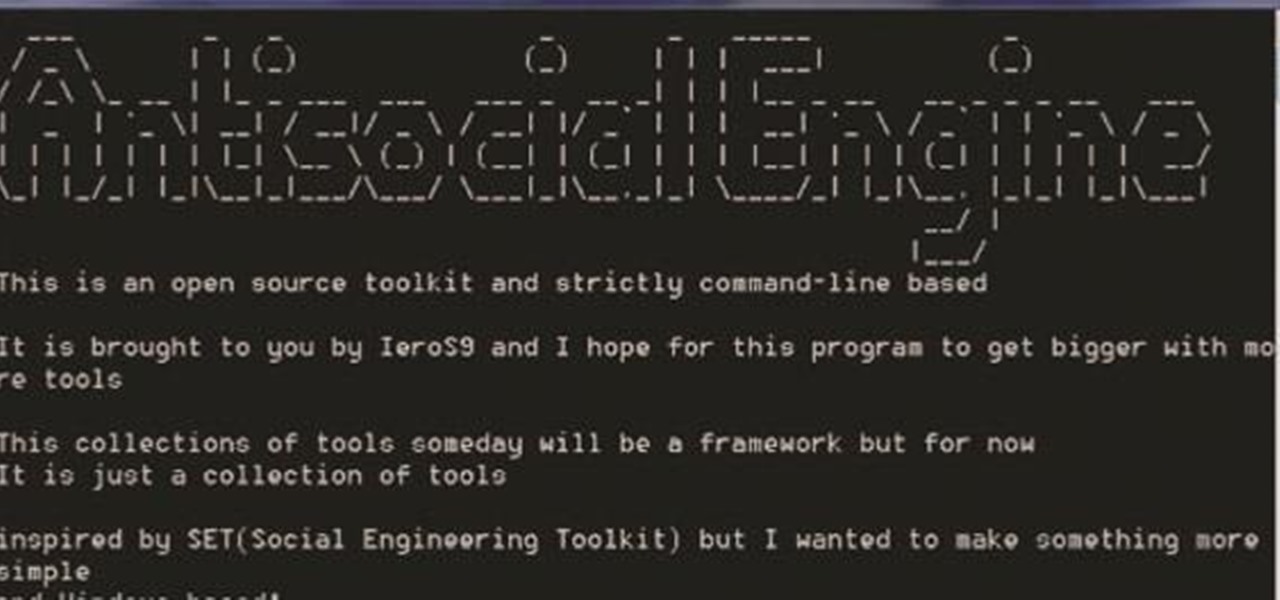
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...