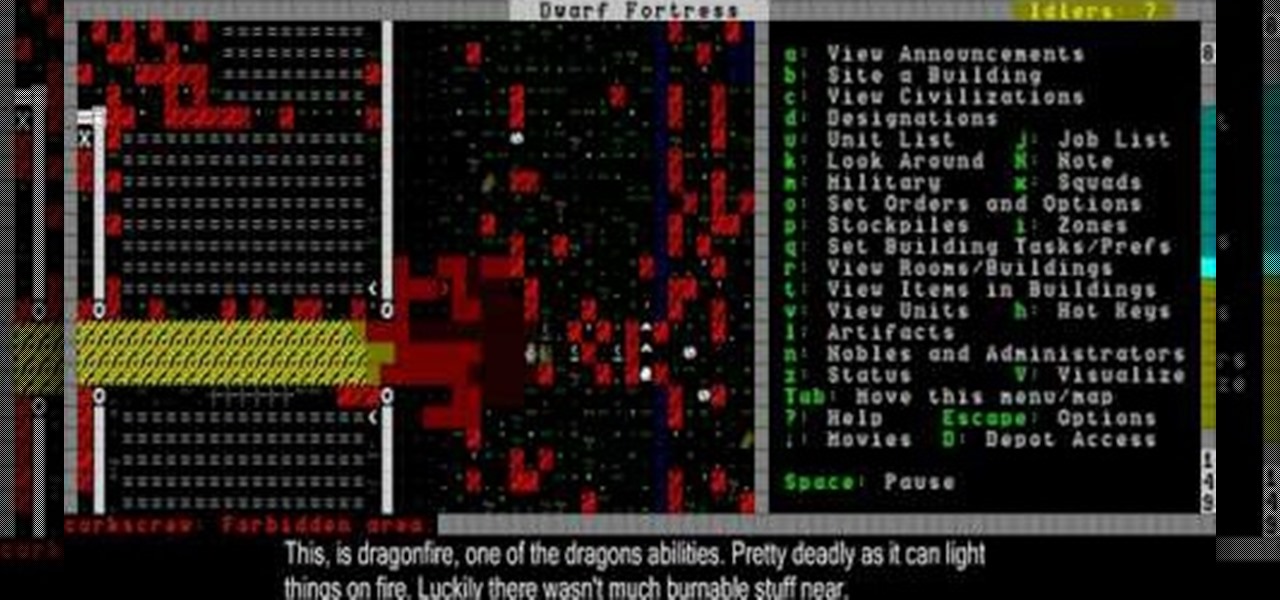
Dragons and goblins are two of the many enemies that may come attack your fort in Dwarf Fortress. This video will show you how to deal with attacks by both and preserve the sanctity of your fortress.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.

In this video tutorial, viewers learn how to receive the "Hunter Special" and "Alchemist Special" achievements in the video game, Prince of Persia. To receive the Hunter Special achievement, users will need to deflect the Hunter's attack 5 times in one battle. To deflect an attack, press the Right Trigger as the same time the Hunter attacks you. To receive the Alchemist Special achievement, users will need to defeat the Alchemist without using the acrobatic button. Only use the X button to fi...

In this tutorial, we learn how to stop a panic attack. Start by reminding yourself that you are having anxiety and do not get upset with the situation. Realize you are just having heightened sensations and that you are not in any danger at the moment. Don't close down, let your sensations run through your body and process the fear. Travel through the anxiety to become free of it. The act of welcoming will change your attitude, and let you flow with the experience. You can mentally feel the se...

The Shiva sisters fight in Final Fantasy XIII is more to prove yourself to the sisters so you may summon them than to actually fight them. To win the battle, you must fill up the gestalt meter which appears over the sisters' heads. No one will die, one sister will actually heal you throughout the battle, but you do have a timer over your head which will give you a game over if it runs out. To begin, use Libra on the sisters to determine their weaknesses, which will make you realize that physi...

Need some more chess tactics for your arsenal? Well, why not try out this "skewer" tactic from this video lecture. A skewer is an attack on two pieces on the same line. The opponent moves the more valuable piece exposing an attack on the second piece. The skewer is a reverse cousin to the "pin."

Learn Epee fencing techniques, attacks and advances, riposte, and counterattacks in these free Epee fencing tutorial videos.

Cid Raines has always been a formidable foe in the FInal Fantasy series. This video will show you exactly how to beat him in FInal Fantasy XIII.

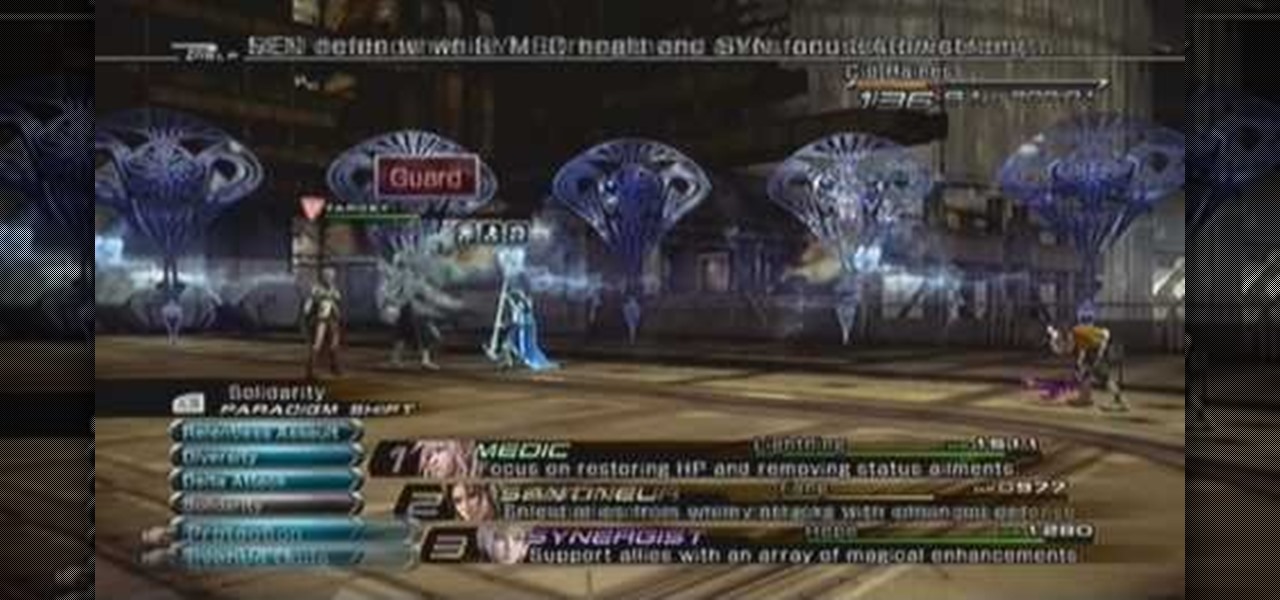
If you're trying to figure out how to play the Disgaea 4 combat modes effectively, take a look at this guide on positioning, attacking, defending, and more while fighting against opponents in the PS3 game. The combat can be a little confusing but there are many different options such as team attacks and combo attacks. This tutorial will give you some understanding of the early fights in the game.

This is why you're fat. Coincidentally, this is also why you're happy when you nom on artery clogging junk fare. We don't recommend you whip up this recipe on a regular basis unless you're hopin' and wishin' for a heart attack this Christmas, but this would make a sweet treat every once in a while.

We once read a Twitter profile that said, "Love food. Hate exercise. Will die of heart attack." While that's funny and all, we doubt any of you guys and gals would want to drop dead on your 40th birthday. While we're totally for the occasional splurge, it's definitely a good idea to begin eating healthy now.

A big part of pizza's allure is its perfectly crispy crust and oodles of heart attack-inducing oil sitting on the cheese. Personally, we can't even consume a pizza we get from Pizza Hut or Domino's without taking a napkin and blotting off the oil.

It's time to smash that iPhone, but wait… you don't really want to break your iPhone, do you? That's were a fake iPhone prop comes in, perfect for any homemade movie. Just make this, and switch it out with the real one during the anger attack. Watch this video tutorial to learn how to build a breakable iPhone movie prop. Also works with a fake smashable iPod.

Check out this piano tutorial video that shows you the effects of different key attack techniques. From high and low, learn the different sounds and senses of the various key attack techniques. Practice these exercises and improve your piano playing skills by watching this instructional piano video.

Watch this Brazilian Jiu-Jitsu tutorial video with Kurt Osiander and the Move of the Week as he illustrates the rear jump to the arm bar attack. It's all dependent on the force you apply to the back of your opponent's neck. Practice your rear jump to arm bar attack technique with this instructional video and improve your Brazilian Jiu-Jitsu skills!

What is the deadliest attack? Well, it's from a position from a game played by Duras and Spielmann. If you want to be a chess master, then you're going to have to learn the secrets of the game, the strategies, the chess maneuvers. Learn how to play the deadliest attack known in chess.

Trying to eat healthy and lose weight when you're a foodie is hard. Because when it comes down to it, most good food (we're thinking sweet, salty, fried, and crispy) is essentially a heart attack in a box. But every now and then you find a recipe that's both delicious and relatively healthy.

Get free self-defense techniques and tips for women's self-defense. Learn to escape an attacker's grasp using self-defense techniques in this free video on women's self-defense.

Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

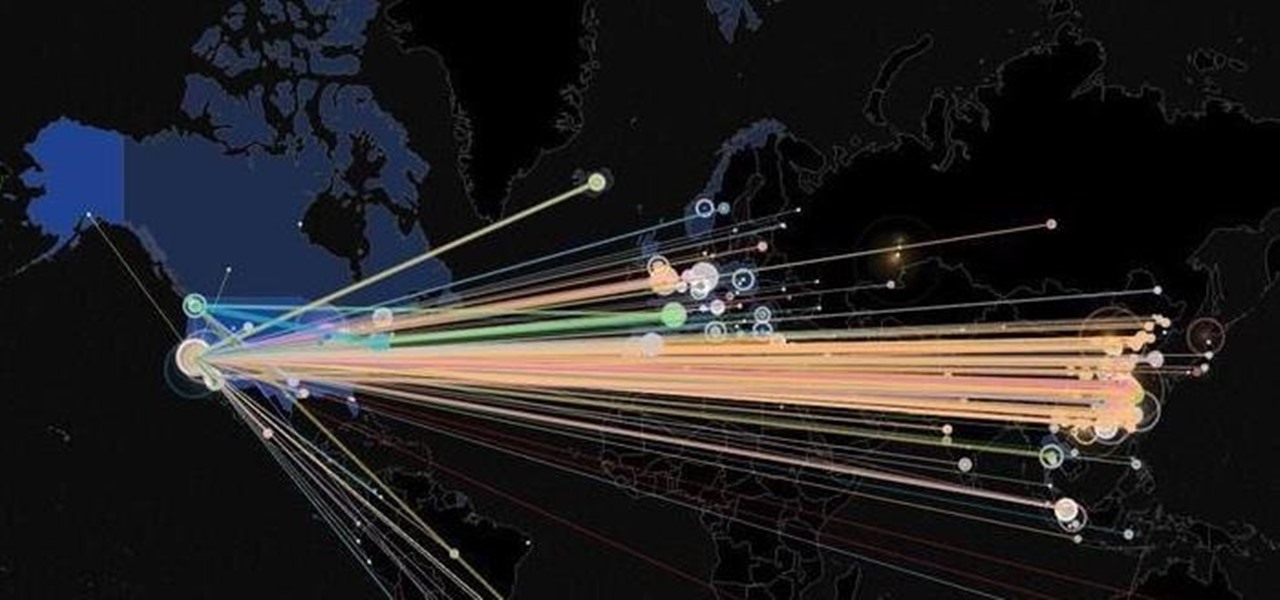
The mysterious, still unidentified missile that was seen yesterday off the coast of Southern California is stilling boggling Los Angeles residents. The projectile was seen on November 8th, shooting straight up into the sky, just north of Catalina Island.

In this video tutorial, you'll learn how to use Cheat Engine 5.5 to hack Penguins Attack TD 2! It's easy. So easy, in fact, that this clip can present a complete overview of the process in about five minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Big predators pose a big threat unless you know what to do under attack. HOW TO SURVIVE advises making lots of noise, freezing when confronted, and playing defense in order to survive. Watch this video outdoor safety tutorial and learn how to survive an attack from a large predator, like bears or cougars.

In this chess lesson, you'll learn how to do Greco's Attack in the Giuoco Piano, in an Italian Game. Everyone chess master should learn this, because you're middle game isn't getting any stronger.

Do you know what a "double attack" is in a chess game? Well, the "knight fork" is basically the same thing; a simultaneous attack of one piece against two opponent pieces. Don't let your opponent win! Use this.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

This tutorial shows you how to execute the first two sets of primary moves with the bo: group 1 (attacks) and group 2 (blocks). It also shows how to change grips.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

So you've mastered the basics of using a shield and going up against an opponent who also wields a sword and shield. This tutorial shows you how to both stage an effective side attack, and how to defend against an opponent making the same attack on you.

Geoff and Jack from Achievement Hunter, show you how to deny a sword lunge with a well-timed melee attack. The tip is to time your block just right because if you get hit with the sword, you're dead, so if you get the timing right it'll still cause you to lose your shield but you could get some shots in between blocking, especially if you're out of other weapons.

Battle in verses 1-12, killing Fairness and Angels, in the Xbox 360 game Bayonetta. In Chapter 3 - Burning Ground, you have to make sure you know what you're doing. In verse 4, the creature is called Fairness. A soon as it appears it will shoot a fireball at you, be sure to dodge it. Fairness has several attacks it uses. It can shoot fireballs, which move faster than other fireballs you've encountered. It has a charge attack that you can dodge or you can jump over it. It also has a sonic atta...

You can’t always get rid of panic attacks completely, but you can learn to live with them. Watch this video for helpful tips on controlling the situation.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.