Are you looking for a delicious yet healthy drink this Valentines? Alia shows us how to make a Moroccan Pomegranate Juice, the ultimate drink for your heart on this special day. Ingredients: 2 1/2 cups of pomegranate juice, 1/4 cup lemon juice, 1/2 tablespoon orange blossom water, 1 cup of sparkling water, 4 tablespoons of sugar. Preparing the juice: If using fresh pomegranate fruit: take the grains, blend and strain. If not, use 100% pomegranate juice available from the supermarket. Mix the ...

The first step to getting over a broken heart is to change the contact information of your ex to do not answer. Delete all texts when they come. Do not look at it! Throw away all moments from your relationships. Leave it in the garbage can! If your ex wishes to have an item back, just give it back. However, don't get it back yourself. Recruit a friend or family member to drop off your ex's stuff. Find a hobby that helps you get over your relationship. Go on a date. Hang out with friends and f...
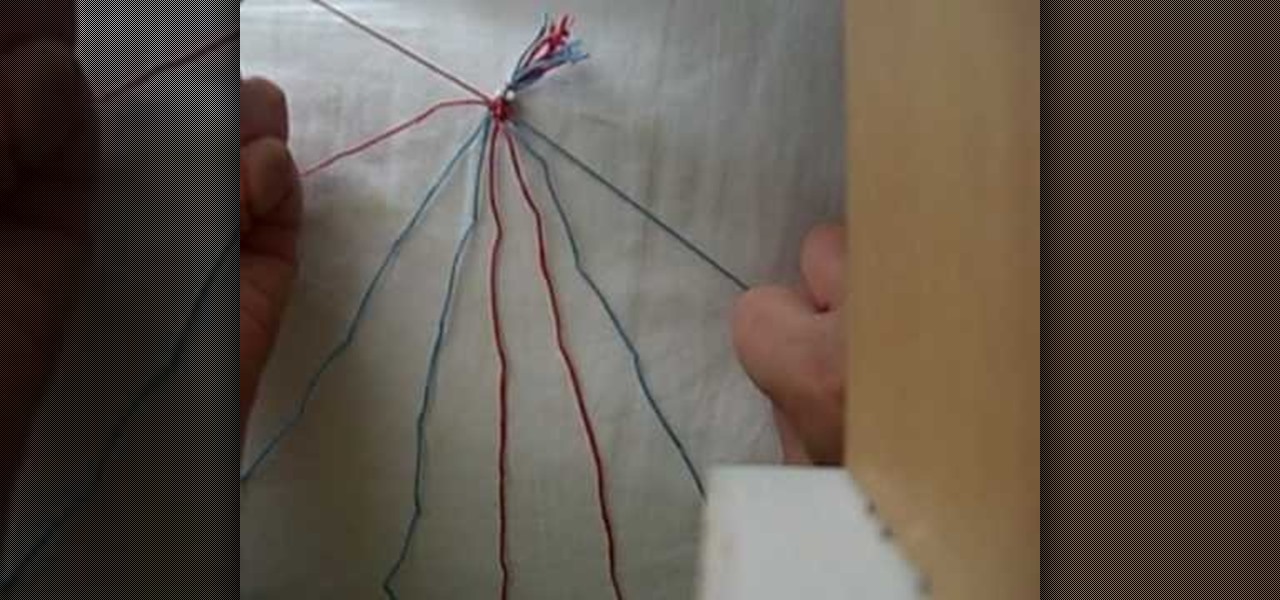
This video shows you how to make a friendship bracelet with a heart pattern in simple, easy to follow steps. All you need is two different colors of thread and you will be well on your way to making this friendship bracelet. The video takes you from the beginning to the end of the process. The finished product is a unique design which can then be given as gifts to family and friends, or you can immediately enjoy your craft by wearing it yourself.
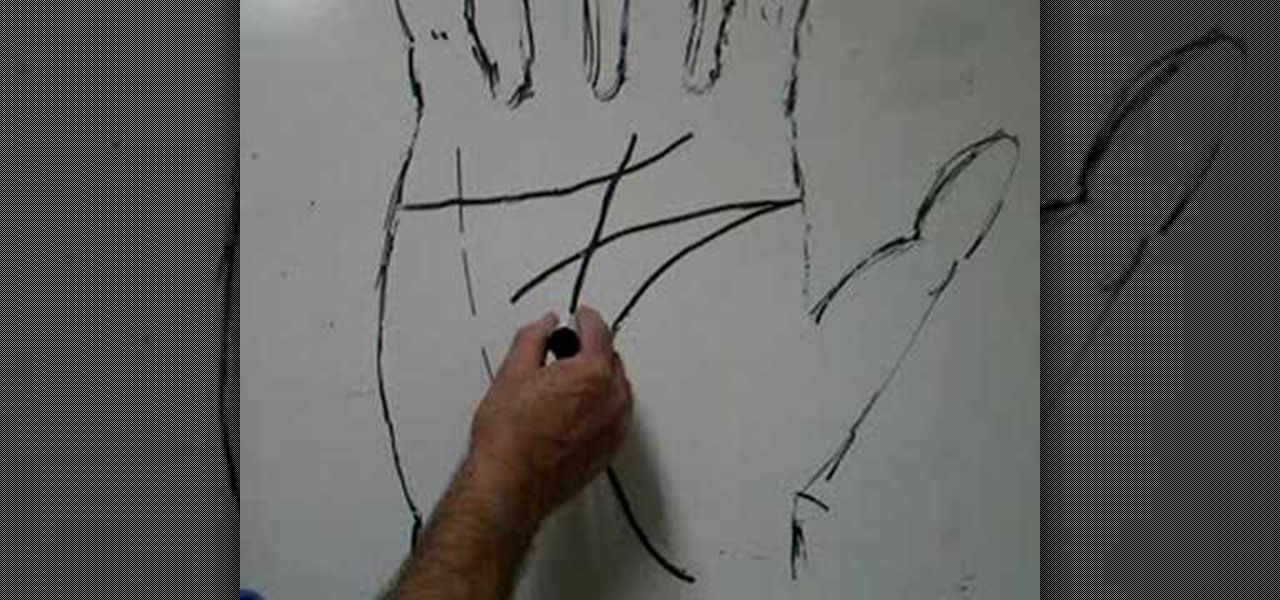
Palm reading can be complicated because chirognomy, the study of the mounts of the hand, sometimes contradicts chiromancy, the study of the lines of the hand. For that reason, it's best to do a reading as a whole. In this particular video palmistry tutorial, Peter John explains the significance of dots in the head, heart, and life line, highlighting the areas on a detailed map of the hand. Watch this instructional palm-reading video and learn how to interpret the meaning behind dots in the li...

This how to video cooking tutorial shows you how to make a heart healthy cumin crusted fish recipe using canola oil. Watch and learn how easy it is to prepare this meal, it is a fantastic way to incorporate seafood into your family's diet.

Check out this tutorial video sequence to learn how to make a Kingdom Heart's 2 Organization 13 Coat for Cosplay! In part 1, you will learn how to make the front part of the coat. Then, when you start sewing, you have to make sure that the outside of the coat is on the inside and to start sewing the shoulders first. This is one way of making Axel and Saix coats for Cosplay. This video was filmed in the hopes of helping people who are struggling to make an Organization XIII Coat. Watch these i...

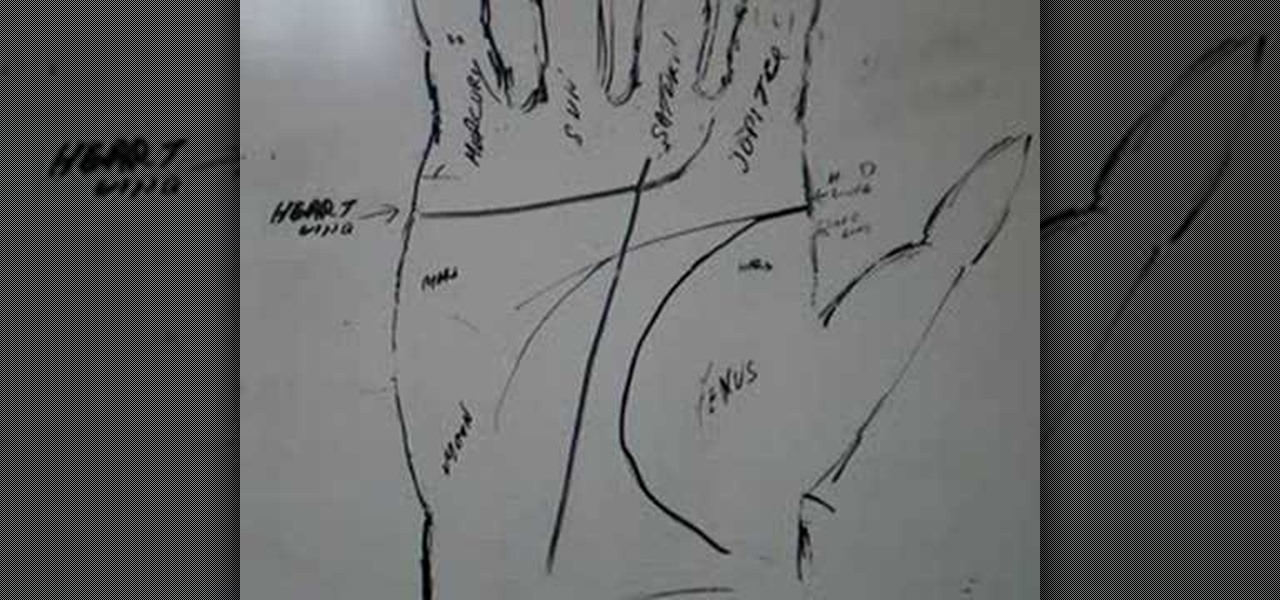
Palm reading can be complicated because chirognomy, the study of the mounts of the hand, sometimes contradicts chiromancy, the study of the lines of the hand. For that reason, it's best to do a reading as a whole. In this particular video palmistry tutorial, Peter John explains the significance of forks in the head, heart, and life line, highlighting the areas on a detailed map of the hand. Watch this instructional palm-reading video and learn how to interpret the meaning behind forks in the ...

This how to video will show you how to make a Mediterranean tuna salad that will melt in your mouth. Watch and learn how to make this classic sandwich with a modern twist.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

In this "how to" video, we learn how to draw a "chibi" form of an angel. Chibi is a Japanese term meaning "short person" or "small child". It has become a style of art in which Japanese Anime and Manga artists attempt to make all of their characters into "cute", childlike characters (with small bodies, large heads, and large eyes). The artist in this video shows his/her step by step process of drawing a small "chibi" angel holding tightly onto a heart. The artist starts with the eyes, then wo...

This video from Do as I do presents a simple card trick. Cut the deck in half.

This video shows how to make a small woven puffy heart. It Measures approximately 3 inches of yarn and 8 inches across. Use sufficient yarn and a size G crosha. Make a knot and attach the knot with the crosha. Make a chain of 3. Twin with the beginning chain to form a loop. Now make 9 rings with the center of the loop. This completes round 1. Now round 2 will have 18 rings around round 1. This completes round 2. Likewise work for two more rounds with 12 or 18 rings. Further round 4 will have ...

Any medical student could benefit from this video lesson, whether you're training to be a doctor or a nurse. The very first step to finding out what's wrong with your patient is examining him/her for their vital signs. You must check the patient's pulse, respirations, blood pressure, and know how to use every kind of sphygmomanometer. To see the entire examination procedure, perfect for nursing students, watch the video to see how to examine a patient for vital signs, and refer to the steps b...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

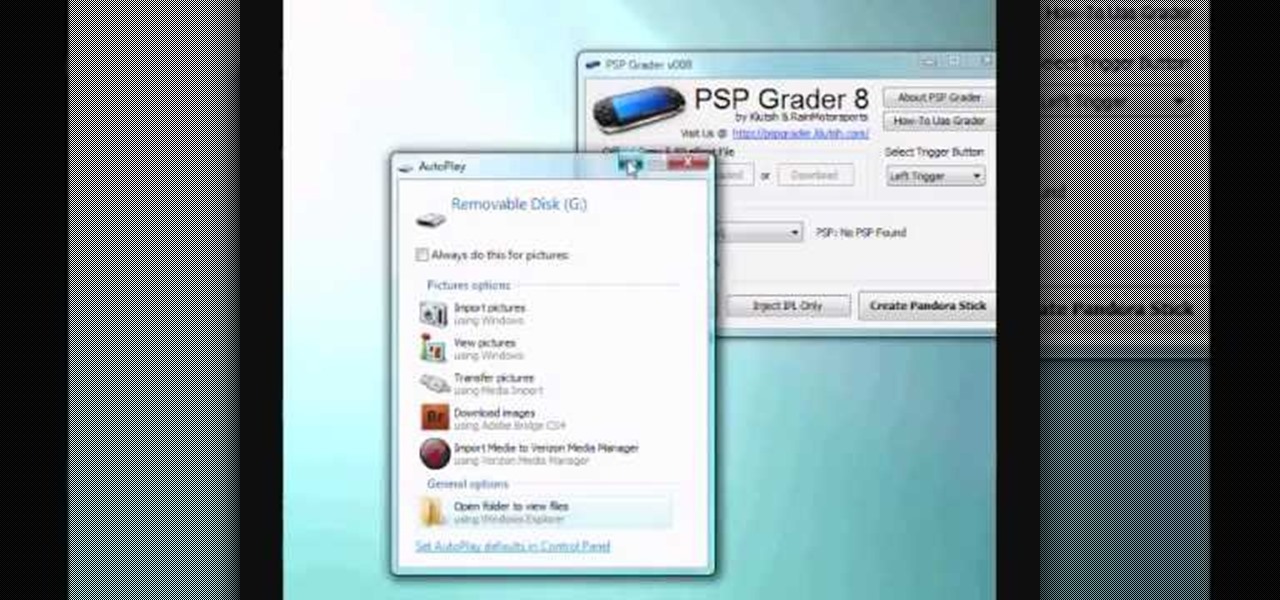
Looking for a little home brew for your PSP? This little video shows you how to downgrade from the Sony PSP 6.30 to 5.50 where you can tweak it to your hearts content and start playing what you want. Yahoo!

If you get stares from guys while walking down the street in this get up, it's probably not because hearts are welling up in their eyes and popping out of their head like in cartoons. Not that this look isn't gorgeous; it's just that you may be a wee bit overdone.

If you have a boyfriend or a girlfriend, then Valentine's Day is truly a beautiful, memorable occasion filled with lots of dining, wining, and hearts popping out of your heads like those cheesy cartoons.

Cards that fold open from the front? Pssh, that's SO last year. Make 2011 novel and interesting by sending this funky trifold Valentine's Day card to your lover.

Don't worry: You won't be actually handing your classmates and friends a matchbox for Valentine's Day. Instead, this adorable "love bandit" matchbox is just a slide-out box adorned with a raccoon holding a heart.

Before you know it, old Saint Nick's reindeer will be tapping on top of your roof and a Salvation Army bell ringer, festooned with a Santa Hat, will be around every corner. That's right, guys and gals, Christmastime is almost at our front door, which means you should get prepared for all the holiday gifting.

The Ice Titan boss is big, he's mean, and his hearts as cold as ice! (badumpsh!) All those things aside, he's tough, and thanks to Konami, they've made him pretty annoying too! If you're getting stuck in his ice fields or his shockwaves, check out this video to get the strategy to beat the Ice Titan!

Have you ever had a cold sore that just won't seem to go away? In this video, we learn how to get rid of your cold sores for good! Since there is no complete cure for cold sores, you must start with prevention. Eat a healthy diet with lots of nutrients, which will restore your immune system to fight against cold sores before you get them. If you end up still getting one, don't bite it or irritate it. You can use natural remedies or over the counter products to help relieve these and get rid o...

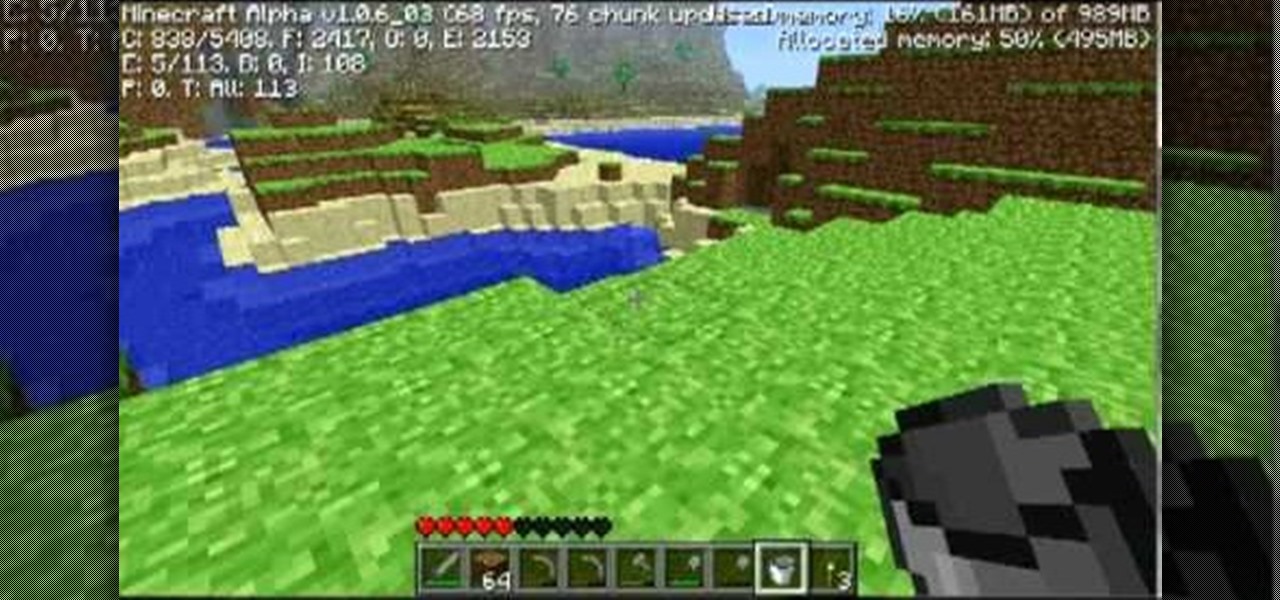
Sometimes taking the route where you don't fight at all in Minecraft is the best plan of attack! If you're looking for a clever way to take down almost all types of creatures (well, except for spiders), check out this awesome video! You'll learn how to make a crafty water trap that'll keep them stuck until they drown to death, or burn up in the sun, and then it's a quick, simple matter of running down there and getting the loot that they drop.

In order to use ThermaPure heat system to eradicate bedbugs, you will need a professional, with the appropriate equipment, including surface temperature readers.

These multicolored heart and square shaped soaps are so cute and pretty you may end up grudgingly giving several to friends before you can try them out yourself!

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get medals fast on Evony (09/25/09). Swamps are NOT the best place to attack if you want medals. A level 2 would be the best.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.

Watch and learn how to solve the Hanayama Cast Chain metal puzzle in this video tutorial. The Hanayama Cast Chain is a 6 out of 6 for difficulty.

Check out this instructional piano video that demonstrates how to play a funky jazz Rhodes beat on the piano. This instructor uses the the Roland RD-170 keyboard, and the 66 El.Piano sound, which is great. With its short attack, not many sustain on it. It doesn't matter how fast this piece of music is played. Find your own way of playing the rhythm that you are comfortable with it. Personalize this funky jazz Rhodes beat on piano and improve your piano playing skills!

You love the video game Tetris and you love the puzzle Rubik's Cube, then what's stopping you from attacking the Tetris Cube?