The trick to winning a Gemini’s heart is to be the yin to their yang. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Gemini work. Be coy when you meet a Gemini, they love a little mystery in their relationships.

Keren Peleg demonstrates how to make jewelry in one step. All you need is a saw and some imagination. Keren makes a heart.

This clip explains the necessary means to surviving the prison system in Chicago. Excerpted from "The Heart Broken in Half", an anthropological documentary about a Chicago street gang, the Latin Kings.

In this video, Matt explores a gambit line for Black in the Four Knight's English: 1.c4 e5 2.Nc3 Nf6 3.Nf3 Nc6 4.g3 Nd4!?

Watch to learn how to make a teddy bear from one balloon. You can also watch to learn how to make a teddy bear on a heart--it's good for Valentine's Day!

A three-part lesson in how to count and play your way through 12-bar blues changes on your harmonica. Required: a copy of "Harp Attack," a 1990 Alligator Records release.

Learn how to make a blue motorcycle, which is a derivative of the long island iced tea. Not for the weak hearted (or low toleranced) this drink is a sure fire way to get your party started.

This video is a demonstration of how to make a winged heart design with folded paper. Start with a square piece of paper and fold it in half. Unfold it and fold it in half again, and unfold it. Using the creases as a guide, fold one edge up to the crease. Turn it over and fold the corners of the folded edge down toward the middle crease. Turn it over and fold the large edges inward toward the crease and unfold them. Lift that side up, forming a pocket underneath. Fold the sides inward inside ...

This video shows us how to fold a simple origami heart. Firstly a piece of paper is taken and is cut in the form of a square and then it is folded into half to form a rectangle. Then it is properly creased and then using a knife it is cut into two halves. Then one of the pieces which are in the form of a square is taken and is folded vertically to form a thinner rectangle. It is creased and then unfolded and then the paper is folded horizontally to form a square and it is creased and then unf...

Any dope can play “Heart and Soul.” Now you can be one of them. Use your pointer finger to hit the 2nd F key up from the middle C briskly three times, then hit it once more before moving down to play keys E, then D, then F three times, briskly. Then F once more, before bouncing down and playing keys E then D.

Learn how to play "Awake" by Secondhand Serenade, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Learn how to play "Faith" by Limp Bizkit, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here:

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Keith Urban song. Not just any Keith Urban song, but one of his greatest: "Stupid Boy." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Lady Antebellum song. Not just any Lady Antebellum song, but one of their greatest: "Love Don't Live Here." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

There's actually several different kinds of fats. You have your unsaturated fats, which are typically heart-healthy fat, which are like olive oil and canola oil. And then you have other fats like saturated fats, which are found in food such as meats, especially any animal product, fatty cuts of meats such as bacon, sausage, butter, lard, high fat dairy products, whole milk, and creams. And saturated fats have actually been linked to increased risk of heart disease. So these are things that yo...

This instructional fitnes HowTo video demonstrates how to do a ustrasana pose.

This is the basic prayer that should be meant from your heart and soul, and not just saying the words from your physical tongue. A true redeeming confession to the lord Jesus Christ, asking Him to come into your heart as your personal lord and savior, asking Him to forgive you of all of your sins, rejecting all evil from continuing to be involved in your life, and rejecting this world's ways, and listening and following God's rules and directions.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The Stories feature on Instagram has a pretty great editing program, and it's one that I think is extremely undervalued. Instagram Stories goes beyond just its Snapchat-like features, but also allows you to create more creative and original content to post on your actual profile page.

There has been an outbreak of syphilis in Oklahoma County with 75 confirmed cases connected by a social network driven by drug use and sex.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

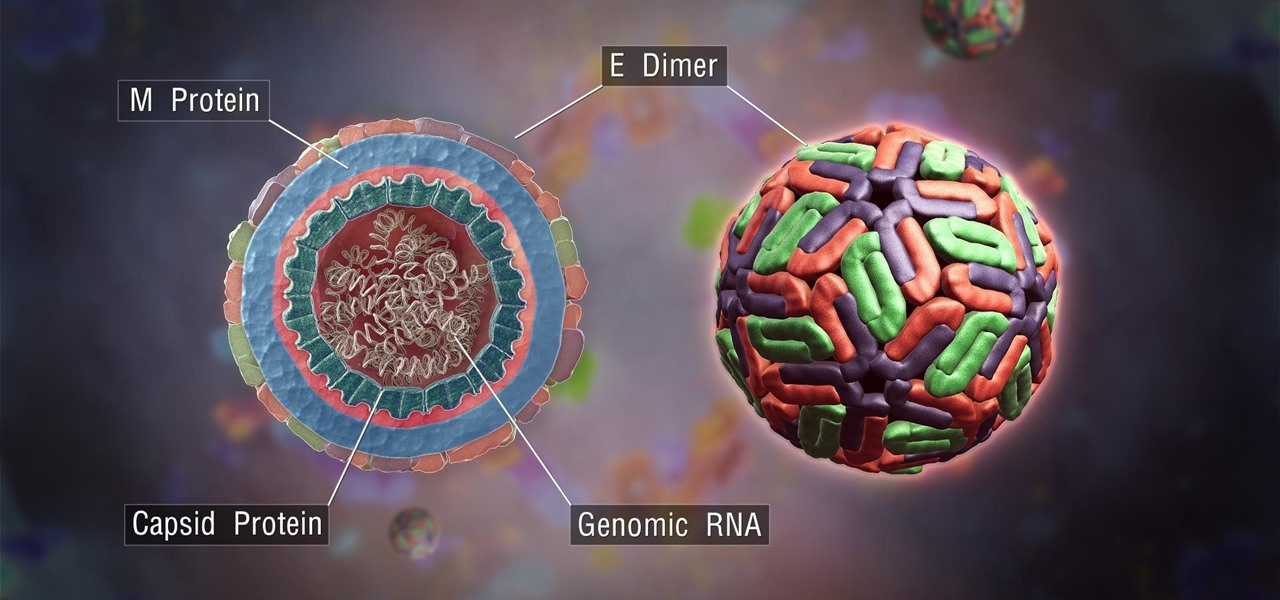
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.
Welcome back Hackers\Newbies!

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

It's time for another mobile prank. The classic pranks and practical jokes are always great, but let's hit your friends where it really hurts—their precious (and expensive) smartphones. And what better way to scare the shit out of them than making them believe their phone's been infected by malware?