Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Would you want to be able to defend yourself and your loved ones if someone were to physically attack you? This video will show you how to defend yourself against an attacker choking you from the front. It' the best MMA for self-defense, especially for a teenager.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

When Penguins Attack - TD hacks, cheats, glitches. How to hack the flash game When Penguins Attack - TD. Defend the human race against the onslaught of evil penguins. Watch this video tutorial to learn how to hack When Penguins Attack - TD with Cheat Engine (09/27/09).

If you've mastered a basic origami heart and rose then it's time to move on to a more difficult and lifelike origami project: This origami iris. Made of intricate and complex petals that jut up and out, this flower is gorgeous.

Tell your friend you hope you feels better in the sweetest and cutest way possible by crafting this bandaid greeting card. A paper bandaid, embellished with a sparkly red heart, says it all.

There are so many occasions in life for which you could use this "Congratulations" greeting card. From your nephew's graduation to a perfect 2400 on the SATs to the arrival of a new baby, this pretty card says it all.

It didn't take Spiderpig from "The Simpsons" movie to convince us that Spiderman was cool. A staple comic and TV show from our childhood, he was a masked hero who always had a heart...and a taste for redheads.

This tutorial shows you how to find the last few items you need to get the Audiophile and Happy Ending? achievements when playing the horrorcore game Splatterhouse. Find all the gramaphones and photo fragments in The Ruined Heart, The Wicker Bride and Blood Eclipse.

In this video, you'll be learning how to crochet a very beautiful lace pineapple pattern. Use this pattern as the base for an afghan blanket, a scarf, or anything your heart desires. Mikey takes you through the process step by step, so just watch the video!

The Care Bears have stood the test of time, from their first appearance on greeting cards, to cutesy, plush teddy bears, to animated television series, to adventure-filled movies. The Care Bears may be long gone from television, but not from out hearts (especially Sara Griffith's of SharksBiteOfLife).

Decorative dragonflies are usually associated with little girls' shams and pink backpacks also plastered with iron-on hearts and happy faces. But you don't have to be ten years old to enjoy the dainty beauty of these winged creatures.

In this clip, learn how to do the super cool kiteboarding trick "313". This move is taught by pro Mathias Wichmann and is definitely not for the faint of heart. So, if you think you can handle it, check it out and start flying!

Practicing softball by yourself can be a challenge, since the interplay between pitcher and hitter is the very heart of the game. This video demonstrates some softball hitting drills that can be performed without a partner. All you need is a tee and the motivation to go out and get the balls after you hit them.

In this tutorial from the Food Network, learn how to make the ultimate Italian dessert, chocolate pizza! This recipe, presented by Giada De Laurentilis, is guaranteed to melt the heart of any chocolate lover.

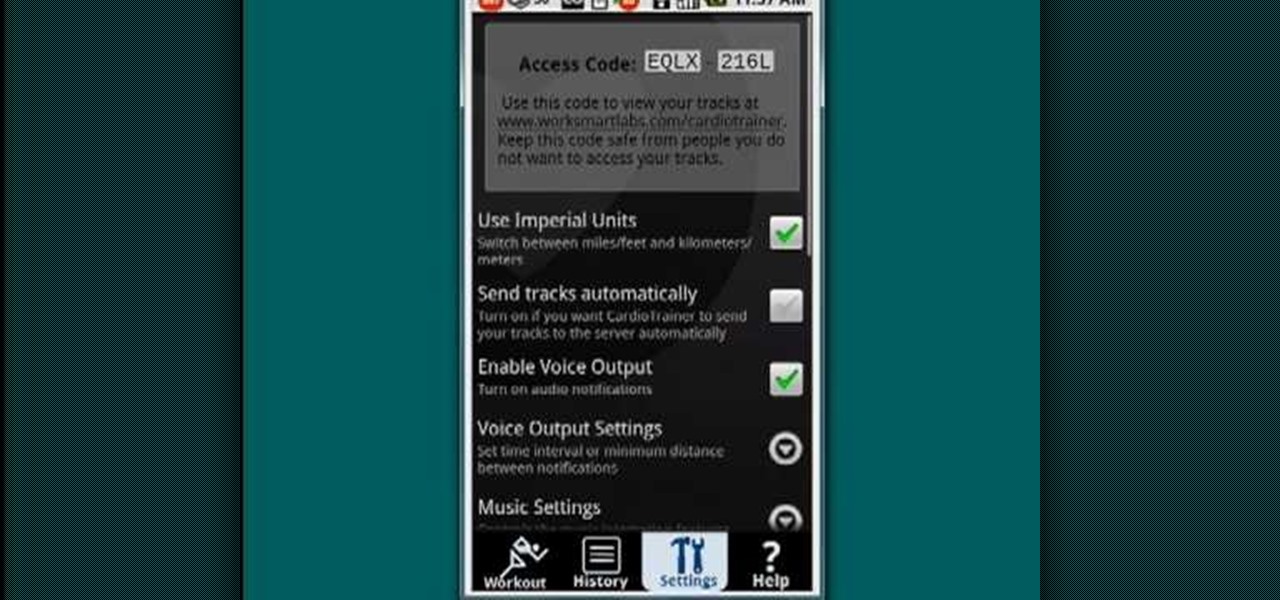
Need to get in shape? Your Android device may just be your best friend. One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial, in particular, discusses how to use the CardioTrainer application to get heart healthy.

Everyday Italian with Giada di Laurentiis took over the heart and attention spans of food network viewers for years, and now on Giada At Home she shares her culinary skills with more of a California bent. Her worlds collide in this video, where she prepares a butternut squash penne pasta with goat cheese and walnuts. This dish is quick to prepare, robust, and delicious, with just the right texture when done properly.

Peggy Erbison shares her knowledge of palmistry in this video. The heart line starts under the pinky and moves across and up towards the middle and index finger. The next line she talks about is the head line. This line is the center line that explains how your thinking is. The line that rounds out and wraps around the base of the thumb is the life line. This line connects to the head line at the beginning. These are the 3 main lines on the palm. Contrary to popular belief, the life line does...

This video is actually about how to perform a math addition card trick. Firstly take two sets of four cards in which one of the sets consists of 2 of hearts whereas the other set consists of 3 of spades. Then take the set of 3's and place it under the 2's then once it is turned over you get four cards of 3's on the top which is placed aside and the remaining cards are of 2's. Now if you just give a shake then one of the cards of 2's turn into 3 of spades and when the shake is repeated another...

In this free two-part video yoga lesson from Manhattan yogi Sadie Nardini, you'll learn a creative, heart-healthy and body-transforming flow with Crow, Pigeon, Bridge, Wheel and Handstand preparation hops all in one! With Sadie Nardini, founder of Core Strength Vinyasa Yoga.

Thread Banger and their friends at Ruffeo Hearts Lil Snotty show us how to transform our old backpack into a now hip (yes, they're hip again) fanny pack in just under two hours. With a disposable backpack, pattern weights, marking chalk, a zipper, seam ripper, scissors, a buckle, some pins, a sewing machine, and a downloadable pattern courtesy of RHLS, you can make your own custom-made fanny pack in time to show off at school the next day! A definite must-try.

Ok, so here’s this weeks DirtSalad video. It’s about making popcorn. Why? Well, my girlfriend Kristin is a therapeutic chef and typically cooks or prepares meal plans for people that are trying to prevent cancer, heart disease or diabetes by using foods as medicine. In this video, you will learn how to make popcorn that tastes crazy good and uses ingredients that are actually good for you.

Knowledge of first aid procedures can save lives. Watch this first aid video tutorial to learn how to perform rescue breathing on an adult whose heart is working.

In this video you will learn how to create a chocolate effect using Adobe Photoshop. In order to do that, just follow these steps: Create a new file with 1000x1000 px. Then create a new layer, select the Shape Tool and create a heart with a brown color for the chocolate. Then add the same effects just like in the video in order to get the same result. The next step is to add the text. For the text use a large font and a light-brown color. If you correctly follow these instructions, the result...

In this series of video clips, you’ll learn more about these different weapons. An important component of fencing is the footwork and balance. Get informative tips on the choreography of a sword fight from our expert. Learn more about the modern scoring apparatus and other fencing equipment. If you are a novice fencer, you can get more advanced tips and ideas for fencing foil techniques and vaulting and linear footwork.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.