After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.
Activating the body's own immune system to fight cancer is the goal of immunotherapy. It's less toxic than chemotherapy and works with our body's natural defenses. The trouble is, it doesn't work for most patients — only about 40% of cancer patients get a good response from immunotherapy. But coupling it with another type of cancer therapy just might deliver the punch that's needed to knock out cancer.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Greetings my fellow hackers.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

This is a super cute girly pink punk nail design that is done in the backdrop of pink and black gradient - ombre nail art style!

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

A team of scientists might have just put Jellyfish Art out of business with their new cyborg jellyfish. By arranging the heart cells of a normal rat on a piece of silicone, they've successfully created their own Franken-jellies. When in salt water with a fluctuating electrical field, the rat's heart muscles on the rubbery silicone contract the lobes downward and back up, which mimics the pulsing movement of a young moon jellyfish swimming.

Nothing touches a mother's heart more than receiving a handcrafted gift. If you're looking for ideas of what to get mom this mother's day, watch this video and learn how to draw her a gorgeous bouquet of flowers. Your mom will love it.

Valentine's Day sweets can be made even sweeter when they're packaged in delightful way. Martha Stewart herself would approve of this red and pink gift box, which features Valentine's Day hearts on the front.

Melting chocolate is the first step in making a delectable chocolate bunny, heart, or other shape of your desire. Chocolate must be melted in order to pour into molds to create these fun shapes, which can be used on their own or to adorn cakes.

While this ornament gift card holder is indeed intended for Christmas gift giving, it can be easily modified into an egg or heart shape for Easter and Valentine's Day, respectively.

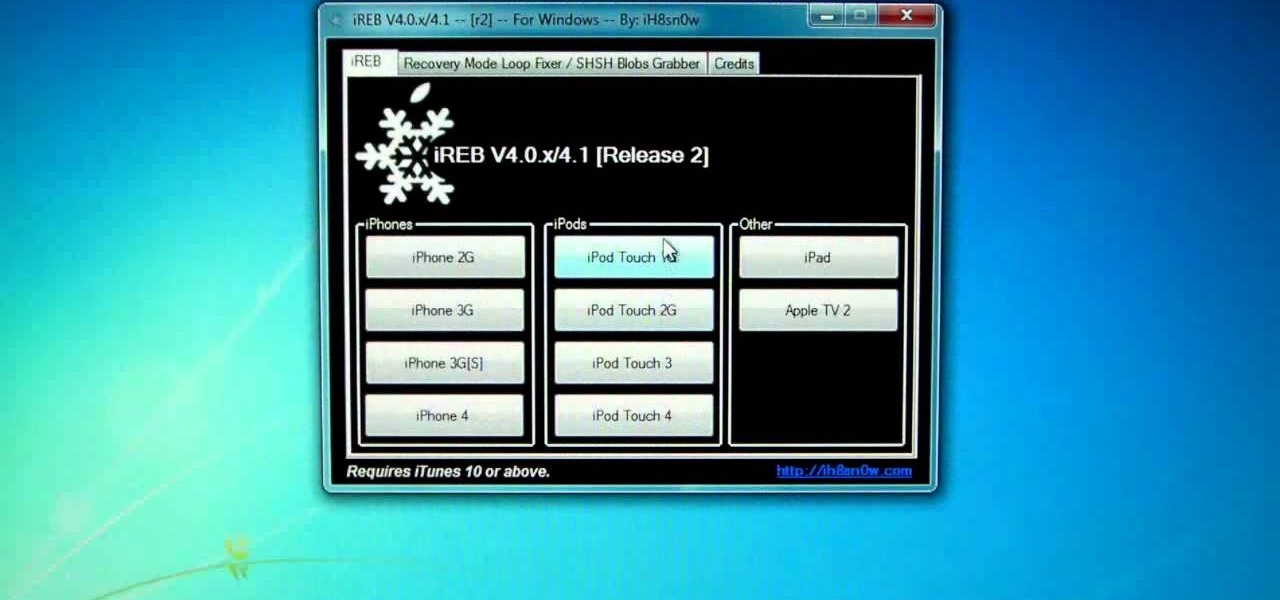
Faced with a 1600, 1601, 1602, 1603 or 1604 error when loading custom firmware on your Apple iPhone with iReb 4.1? Take heart: this jailbreaker's guide will teach you how to fix it. It's easy! So easy, in fact, that this tutorial can present a complete walkthrough of the process in just two minutes.

The Galactic Imperium was responsible for the deaths and enslavement of millions in Star Wars, and their symbol still sends fear into the heart of Republic sympathizers throughout the galaxy. This video will teach you how to show your love for the Imperium by making their logo your Call of Duty Black Ops player card / emblem.

Can't figure out how to install the Firesheep Mozilla Firefox extension? Take heart; this quick video guide presents a complete walkthrough of the download and installation process, teaching you everything you'll need to know to use Firesheep to hack your friends' Facebook and YouTube account information. For all of the gritty details, watch this hacker's how-to.

The limit to the heights of buildings in Sims 3 is five stories, so what to do if you have your heart set on urban sims? You can certainly create the mockup of a skyscraper by following this tutorial that shows you how to build something that at least has the appearance of a tall building.

If you're getting tired of doing your cardio workout tapes because they're getting tedious and boring, then dance may be just what you need to get your heart rate up while having fun.

The Chevy Tahoe isn't the most reliable vehicle, bless it's heart, and home maintenance skills are a must if you're going to enjoy owning one. If you're replaced the rear brake backing plates recently and noticed the E-brake not working after that, watch this video to learn whether you lost the pin under the adjuster pad and that's causing the problem.

The air horn is one of the cheapest and loudest things that you can buy, and it forms the heart of many amazing pranks. This video will give you some ideas for easy air horn pranks that require no fancy setup or planning. Just an unsuspecting victims and a little bit of patience.

Looking to make chocolate brownies equal parts delectable and adorable? With the right ingredients and proper technique, it's easier than you'd think. So easy, in fact, that this free video cooking lesson can present a complete overview of the process in about four minutes. For more information, including the full recipe, and to get started making your own cardiod chocolate brownies, watch this video guide.

Looking for a tasty lunch for a hot summer day? In this clip, learn to make a yummy summer salad, corn on the cob and an extremely tasty grilled tuna sandwich. This sandwich is healthy and good for your heart and even kids will love it. Give it a try!