Just like humans, dental care is very important for dogs. Having a healthy mouth will not only affect the teeth and gums, but also the heart, liver, kidneys, and the overall health of your dog. Learn the basics to doggie tooth brushing.

Check out this video to learn how to read palms like expert Jim Winter. This video concentrates on reading the heart lines of palms.

The kitchen is the heart of a home, so this week we are making an apron out of an old pair of jeans. We also accessorize our tabletop with an array of centerpieces and give you a refreshing quick tip to serve your guests.

In this episode, Jamie introduces us to four more exercises - a forward lunge for your legs, skipping for your heart and lungs, a bicep curl and shoulder press for your upper body, and a back extension for your lower back.

Learn how to make a delicious walnut pesto pasta and a hearts of palm and piquillo pepper salad with walnut oil vinaigrette.

From the depths of the gaming abyss, a classic returns to melt the heart of shoot 'em up gamers. Here's some tips from G4TV on beating the first two bosses in R-Type for the Wii Virtual Console.

The scorpion pose is a favorite of Cirque de Soleil performers and contortionists of all stripes, which is to say it's a very advanced position not for the faint of heart—or weak of back.

The fitness gals of Diet.com bring you a heart pumping circuit workout you can do anywhere while traveling for the holidays! This exercise video shows you how to hit all the major muscle groups giving you a total body workout in just 18 minutes.

In Wisconsin, is there any burger topping more appropriate than a liberal dollop of butter? Travel with Hamburger America to Glendale institution Solly's Grille, located just next to the Milwaukee Heart Hospital. The Grille' calls its hamburgers the "butter burger".

This kid's heart is in the right place. He teaches you beginner's boogie woogie. Part 1 of 2 - How to Play boogie woogie as a beginner.

In this part of Justin's guitar series on "Jazzing up your blues" you learn to link the two arpeggios playing eight notes on each one and changing to the nearest note of the following arpeggio. This lesson is great for learning to make chord changes but you absolutely must be able to play arpeggios by heart to start on this lesson.

This video demonstrates a great rainy day project for children. It is a simple heart box made and decorated with foam shapes.

Warm cheese and an ensemble of vegetables make artichoke dip a scrumptious snack or appetizer. Learn how to bake this easy artichoke dip at home. Ingredients needed are artichoke hearts, mayonnaise, parmesan cheese, roasted red pepper, pkg. frozen chopped spinach, garlic powder, onion powder (optonal), and water.

Cassandra, your old lover in Shank, and she's not exactly happy to see you. Alright, so you cut her up a little bit, I mean, she was over reacting, right? She can be a tough enemy if you don't know her pattern of attacks and counter attacks. In this video you will get a chance to see what the best startegy to use against her is, as well as her points of counter attack.

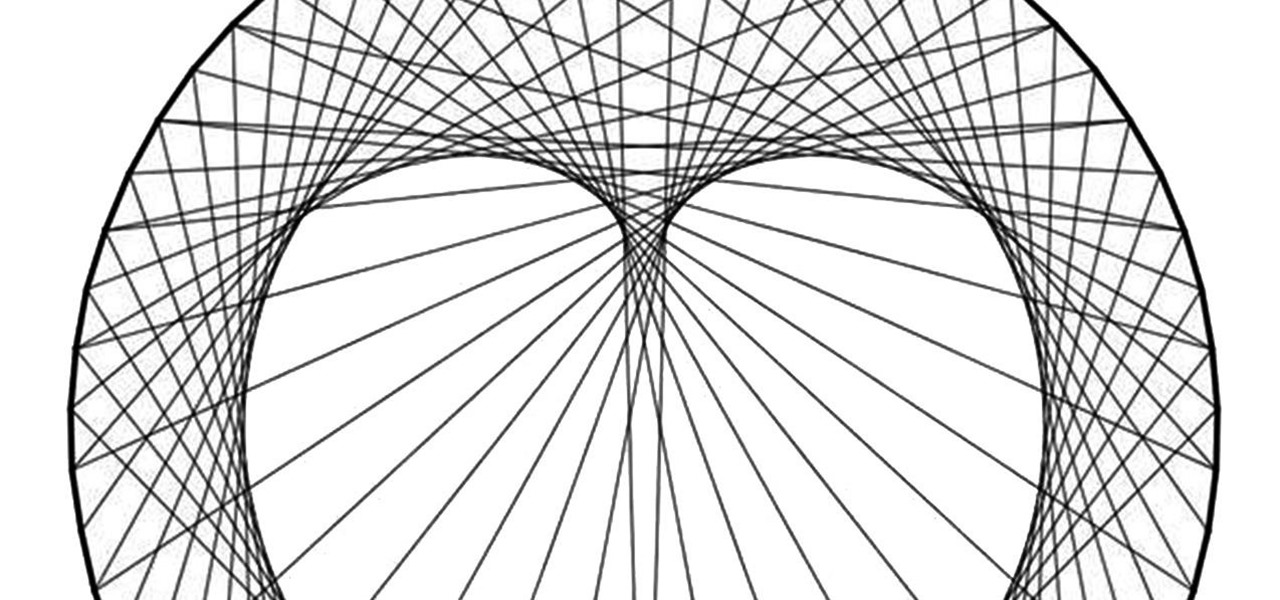
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?

Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

A little over a year after emerging from stealth, augmented reality gaming startup Illumix has launched its first title using a familiar formula, but with a new twist.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Public software testers can now run the fourth iOS 12.1.3 beta. Apple seeded this update to testers on Thursday, Jan. 10. Just like with beta 3, public beta 4 includes two resolved issues — a VoiceOver fix for ECG and Irregular Heart Rate notifications, as well as audio improvements for iPad Pros.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Continuing its unrelenting (and mostly successful) campaign against Snapchat, on Tuesday, Facebook announced the addition of "World Effects" to its Messenger app.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.