You'll be breaking hearts this Valentine's Day, literally, you'll be "breaking hearts"… if you try this science experiment. A live heart. That disgusting thing you swear your love by. How do nerds break hearts? With liquid nitrogen!

Your family and estates have come under attack, and you must defend them! This walkthrough for Assassin's Creed: Brotherhood shows you how to get through this part of the game, in large part by manning the cannons against your enemies.

In MMA nearly every part of the body is fair game for attacks and attacking, even the toes. In this video Joanne and Risha of MMA Girls will teach you how to use a toe hold to submission an opponent.

In this Sports video tutorial you will learn how to play midfield in soccer. Adrian Heath, Head Coach of Austin Aztex, explains the role of the midfield player in this video. Midfield player is the engine room of the team. He moves forward and feeds the ball to the strikers for attacking the opponent's goal and falls back in to his own half when defending. Two midfield players combine to pass the ball from the defending half to the attacking half past the opposing midfielders. There are many ...

In this video pest control specialist Mark Govan of ABC pest control shows you how to fight the war on fleas. Protect your home and animal from getting attacked by these blood suckers.Follow the advice in this video and make sure you prevent an invasion or attack on these annoying little creatures.
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.

COD4 Pro Nade Tutorial See how to do a pro nade attack in Vacant on COD4. For this grenade throwing tutorial, you need to be in Multiplayer mode, Search and Destroy, on Call Of Duty 4: Modern Warfare.

COD4 Pro Nade Tutorial See how to do a pro nade attack in Crossfire on COD4. For this grenade throwing tutorial, you need to be in Multiplayer mode, Search and Destroy, on Call Of Duty 4: Modern Warfare.

Cary Kolat demonstrates wrestling technique - collegiate offense - single leg series - shoulder roll attack below hips. Check out this coaching video from Kolat.com archive of wrestling drills and moves.

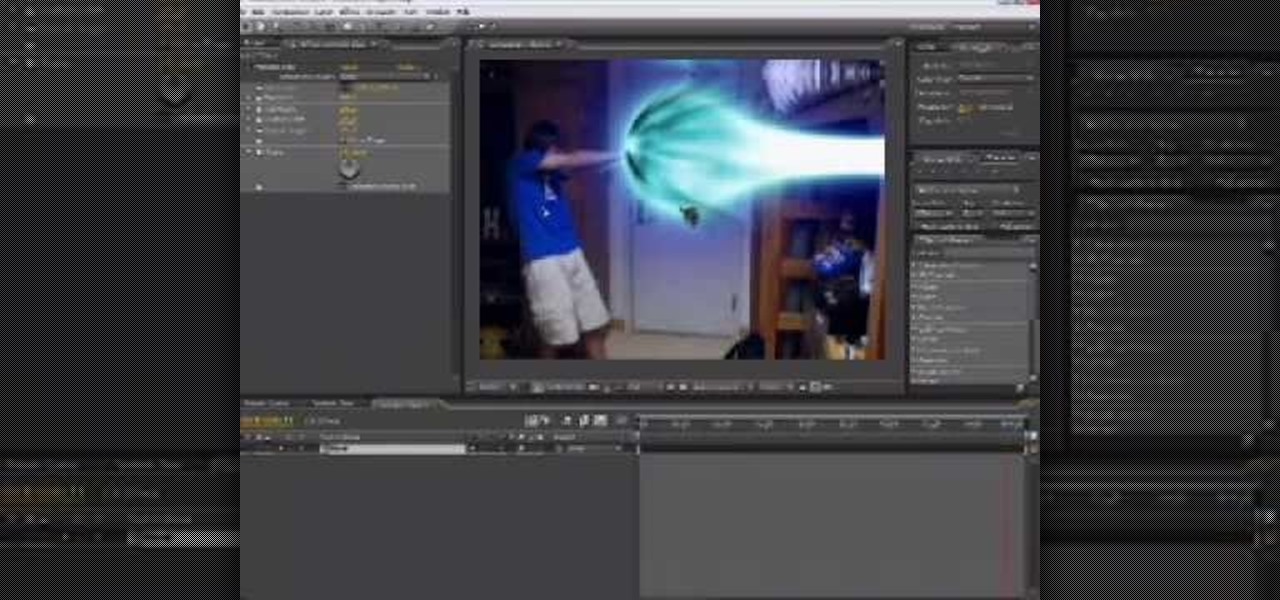
No, the Kamehameha is not the famous Hawaiian king who united all the islands under his rule from 1795 to 1819. Nope. However, it is named after him. But in this case, Kamehameha is an energy blast attack shown in the Dragon Ball Z series. And with this After Effects tutorial, you're going to learn how to recreate this energy attack.

Jarret Waldman explains why Imi the founder of Krav Maga uses a single handed defense instead two in other systems for gun from the front attack.

What makes you better than your opponent in Jiu Jitsu? The ability to chain attacks, one right after the other.

How to attack from someone's guard (you in the mount position) in Jiu Jitsu using the heel hook technique.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

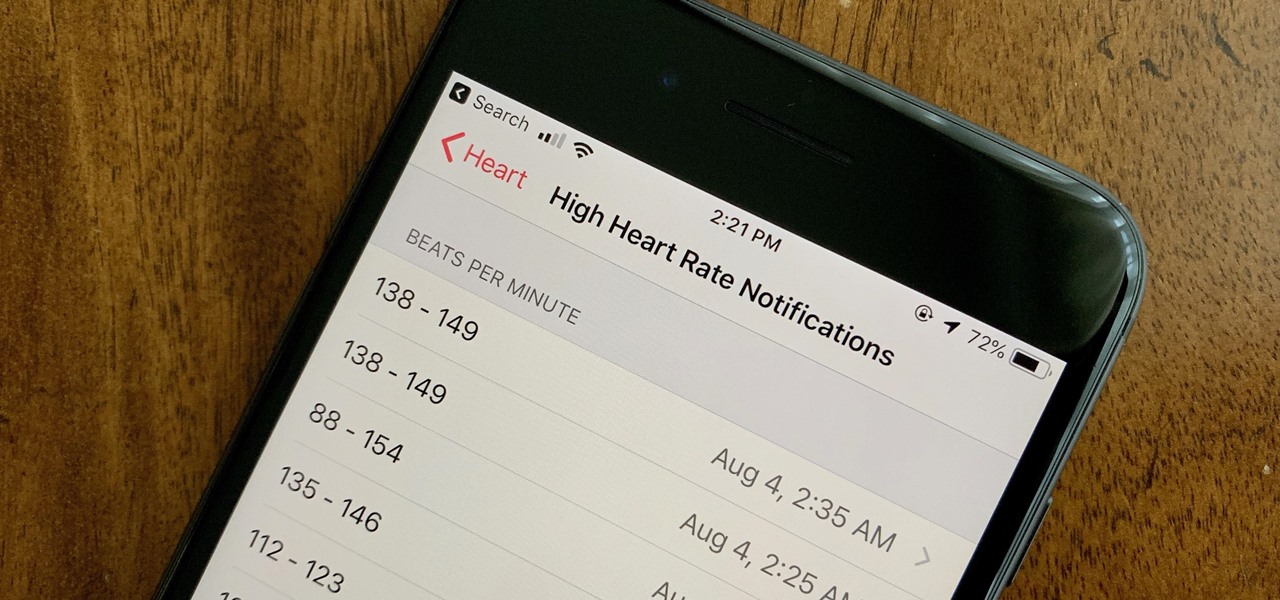
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

Twin hearts, what could be more lovely? This how to will walk you through the steps to fold an origami double heart with a 10 pound note. It's easy, it's fun, and it's beautiful. Try it today, and show your loved one you care, with a little folded piece of paper. Whether it's for Valentines Day, or any day of the year, this clear and helpful how to will show you the steps to fold up this sweet little creation. Go for it and get your fold on today! I heart hearts and you'll heart hearts as wel...

What's the only thing better than one heart? Well, it must be 2 hearts. Whether it's for Valentines Day, or any day of the year, this clear and helpful how to will show you the steps to fold up this sweet little creation. You can use any size of paper you want, but you'll want to choose paper that has different colors on either side. Go for it and get your fold on today! I heart hearts and you'll heart hearts as well with this tutorial.

Valentine's Day is near, and Judy Topaz has the perfect project for you… a knitted heart. If you want to add a little bit of sweetness to your scarf, sweater or other knitting project, then this knitted heart will surely do the trick. Just make sure to choose a good yarn for good color contrast. Watch all four parts of this comprehensive Valentine's Day knitted heart!

In this video you will learn how to complete the "Finish Him" achievement in GTA IV. In order to do that just follow these steps. First you will need to go in a crowded place. You will need to get 10 melee counters in 4 minutes. To complete a counter attack you will have to press the A button when the enemy tries to hit you. After you dodge the attack you will have to press the B button in order to punch him back. Just repeat this process for 10 times and you will successfully get the "Finish...

In these two videos, Matt discusses 1.d4 d5 2.e3 Bf5, preventing White's Stonewall setup by beating White to the d3-h7 diagonal. The only way White can play for an advantage is to play 3.c4 with the goal of an early attack on b7. Some of these positions can also be reached via the Slav Defense.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Oh god, don't you break my heart, my achy breaky heart, I just can't take it anymore. Oh well, if you still need more achy breaky, check out this video and learn the line dance that years ago caused a nation to pause and reflect.

Origami double hearts are easy to make and a great way to show your loved one that you care. Plus, it's cheaper than a dinner out, so watch this video, follow the steps, and profess your love with a piece of folded paper. Hey, at least your loved one will know you went through the effort, and it's the thought that counts, right?

Finding all of the rare trade objects in Assassin's Creed: Brotherhood can be infuriating, what with random item drops and quests to juggle. Watch this video for a guide to farming trade objects by killing bandits along a particular route.

Learn how to make a pretty red Valentine angel heart pendant and earrings using a push mold and polymer clay.

Hearts are fairly easy to cut out of paper, but origami hearts take a little more work, and that means more appreciation from their recipient. Even better, flying origami hearts. What better way to tell your loved one you care on Valentine's Day than with some bat-winged hearts? It'll send them into cardiac arrest just knowing how much effort you put into making your love known.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!