In its heyday the Atari gaming console was the Playstation of the 80s. Sure, you could download some wannabe emulator, but why not go a step further and purchase an actual Atari. They're still floating around and just think how cool it'll be to play pong in hi-definition.

Dawn5377 teaches you how to make a pink sweet treat cup door. You need a stamp from the sweet center set and you use it on a small piece of pink cardboard. You punch the middle out. Also punch the middle of another piece of pink cardboard. Insert the treat cup door and stick it in. You use dimensionals to hold a white piece of paper, which acts like a tray under the plastic dome. You add some sweet treats inside and stick the other pink piece (with the heart) on the other side. Also remember ...

Two hunky guys demonstrate how to improve your abdominal muscle tone. Work your abdominals in a unique motion and boost your anabolic hormones to gain muscle and lose fat. In addition to this workout, add healthy eating and positive thinking and you will accomplish your goal. You can get your heart rate up to over 160 using these tips. The movements are simple, they are basic boxing hits. You must work the right muscles and move the right way, as with any exercise, and it works.

Ingredients: 1 cup Sooji (semolina)

Fighting Straga is the main boss fight In the Xbox 360 game Darksiders - The Black Throne. Can you beat him? Quickly shoot a portal onto one of the floor stations in front of Straga. Watch his mace carefully and you'll see another orange portal point on the side of it. Shoot a second portal onto the mace then wait for Straga to raise the mace back behind his head. When he does this, drop through the portal you made on the ground so your pop out of the portal on his mace and land on the platfo...

Get ready for car throwing in this Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

This Shadow Arena Challenge isn't the easiest in the Choking Ground on the Xbox 360 game Darksiders. Meet the requirements of each portal to free the Tormented Gate so that you may proceed.

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

In this level on the Xbox 360 game Bayonetta, make sure the bullet enters Balder's head. In Chapter 16 - The Lumen Sage, keep that bullet in line. Father Balder doesn't do much damage, but he tends to stay out of range. When you do have him in range do as much damage as you can. Keep fighting until you get his health meter down to zero and can do a climax attack. For more info, watch the whole gameplay.

Defeat Iustitia in this installment for the Xbox 360 game Bayonetta. In Chapter 11 - The Cardinal Virtue of Justice, attack the tongue. The first part of this fight is against one Ardor and a bunch of smaller enemies. After defeating them you'll see another cinematic and face the boss named Iustitia.

In this five-part video tutorial, learn how to double crochet intarsia using a graph or chart. Intarsia knitting is an advanced knitting method, used to knit with several colors of yarn. The simple heart chart used in this video is available here.

Fight Enchant Angels, Trash Mobs, and Fortitudo in the Xbox 360 game Bayonetta. In Chapter 2 - Vigrid, City of Deja Vu, it's time to shine as one mean mama-san. In the first battle you can walk on walls. To get back to the floor quickly press down on the left stick while jumping. Because this fight takes place on six different surfaces it can sometimes be hard to locate Jeanne (your opponent). If you don't know where she is, just shoot her. Your guns don't do any damage, but you will see wher...

Right off the bat you have a horrendously hard battle against Straga in the Xbox 360 game Darksiders. The Prologue battle with Straga is difficult, unless you have your car throwing skills down. Straga is a massive demon that looms over the streets and War. During the battle, hold the Focus Button to keep the camera locked on this massive creature which also gives you a nice wide perspective so you can really see your surroundings. You'll want to get used to using the Dash Button to dart left...

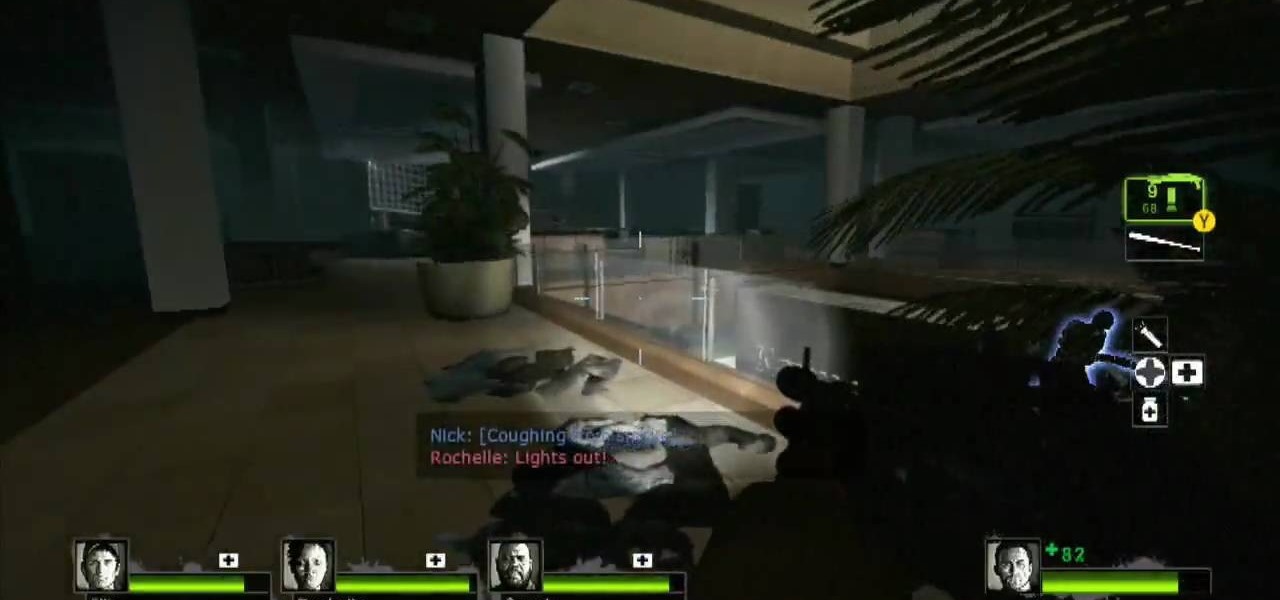
Prepare to delve into the world of L4D2 and check out the gameplay for Campaign 1: Dead Center - Streets. Stock up and open the safe house door. You should see a bunch of infected milling about here. Kill them and make your way straight up the hill past the port-o-potties. Turn right at the fence and take the street down. Watch out for zombie attacks from the walls to the left and right of you. They will drop down from above. Duck into the building on the right when you reach the fence at the...

L4D2: One of the best horror video games of all time. Check out the tips and gameplay for Campaign 1: Dead Center - Mall. Restock on supplies and head out of the safehouse. Feel free to kill any zombies trying to reach in the door before you unlock it. Hang right and make your way up the giant escalator in the middle of the floor. Loop around and exit Kappel's department store. Go down the first escalator you see. Watch out for zombie attacks from the floor above. They will jump down and catc...

Everybody needs a little dating advice, especially the men… or boys! Alec Greven, the nine-year-old author of "How to Talk to Girls" shares some of his successful tips on talking to girls. And surprisingly enough, this dating information can be applied to all ages. Are you smart enough to take over a girl's heart? See how to talk to girls!

Play Along: At the start of the mission, you simply need to follow the leader through the city. Do your best not to bump into anyone, as Ezio will drop the chest if you do. Eventually, you read the end of the trail and a cut scene takes over.

Ace Up My Sleeve: It's not a playing card though. Talk to Paola again and she'll give you the hookup with a cool weapon. Problem is, it doesn't work yet. You need to bring it to Leonardo da Vinci, who's just across town. Make your way to him and knock on his door for a lengthy cut scene.

Dogmantics dog trainer Emily Larlham shows us some exercises that should be repeated once a day in the first sixteen days of your dogs life to create a super puppy!

We all know that movies now-a-days don't use real rocks, but fake rocks for their film sets. Why? Because it's safer, lighter, easier to movie, and you can design them exactly how you want them. So if you need a rock for your indie film project, make it yourself. There's nothing better than imitation. Watch this video tutorial to learn how to build a fake rock movie prop.

The FN P90. Everybody wants one, but more than likely, you can't get your hands on one, especially if it's illegal in your area. Designed by FN Herstal back in the 80's, the P90 personal defense weapon is the cream of the crop. It's full name, Project 90, specifies a weapon system of the 1990's. If you want this firearm for a weapon prop or just to have, you can easily build one yourself with household materials, mostly cardboard. Watch this video tutorial to learn how to build a P-90 prop ca...

It's medieval mayhem and you need a sword prop. Maybe you're larping, or maybe you just need a fake, dull movie prop blade for your action epic. Either way, this is a great weapons build project for a cool replica wooden sword. Watch this video tutorial to learn how to build a fake sword prop.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

This is a video walkthrough of Mission 14: "Heart of the Reich" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

The Master Cleanse is soooo yesterday. Here are the best new ways to drop pounds fast. You Will Need:

This is how to do the Manu Ginobili step back jumper! NBA hot shot show's us how to pull the step back jumpshot, one of his Signature Moves on Nike's series. First the long step and catch your balance. Then setup for the rim. Go behind the back and then see what you have in front of you.

Studying to be a pediatric nurse? Then here is a nursing how-to video that teaches you how to take a three year old child's vital signs. Every nurse should know the basics of this technique, follow along and see how easy it is to distract a child and read their vital sings. Accurately taking their temperature and heart rate is an important aspect of nursing. These medical tips are sure to help you pass your nursing exam with flying colors.

Pack some fun for your next gathering of family and friends. Imaginations run wild with everyday picnic supplies and your favorite Crayola Crayons and Markers. You will need crayons, markers, colored pencils, scissors, glue, tape, and picnic supplies (paper plates, napkins, cups, and plasticware.) This is a great project for summer parties with lots of children or just the young at heart. With this how to video you will be able to have a fun summer picnic craft challenge at your next family g...

Learn how to hold plank position while doing a cross kick under. Presented by Real Jock Gay Fitness Health & Life.

Learn to access a number of Google Easter eggs with this simple Google hacker's how-to. Best of all, each of these Easter eggs can be found directly from Google search through use of Google's own "I'm Feeling Lucky" tool. The full list of Easter eggs explored in this video is as follows:

This video walkthrough guides you through the "Forest Temple" chapter of Legend of Zelda: Twilight Princess for the Nintendo Wii including the boss fights and locations of any heart pieces, golden bugs, and poe souls.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.