
News: Anyone Else Likes TDoS?
Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.


Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

For 365 days of the year, our mothers show their love for us by driving us places, cooking us food, doing our laundry, and being our number-one cheerleader. But for one day of the year, we all get up early in the morning and show our love for our favorite women. Often, that means cooking breakfast or making brunch, or running to the store to grab a pre-selected bouquet of flowers.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

On the Apple Watch, along with the conventional emojis we've grown to love, there are new animated emojis that add a new dimension of fun for you and your friends. Unbeknownst to many, these animated faces also include a feature that allow you to change their color.

Creating a haunted house for Halloween was a big deal when I was growing up, and the neighborhood kids were always coming up with ways to try and out-do each other when it came to this frightful night. One beloved game was to blindfold the participants and play the Withered Corpse.
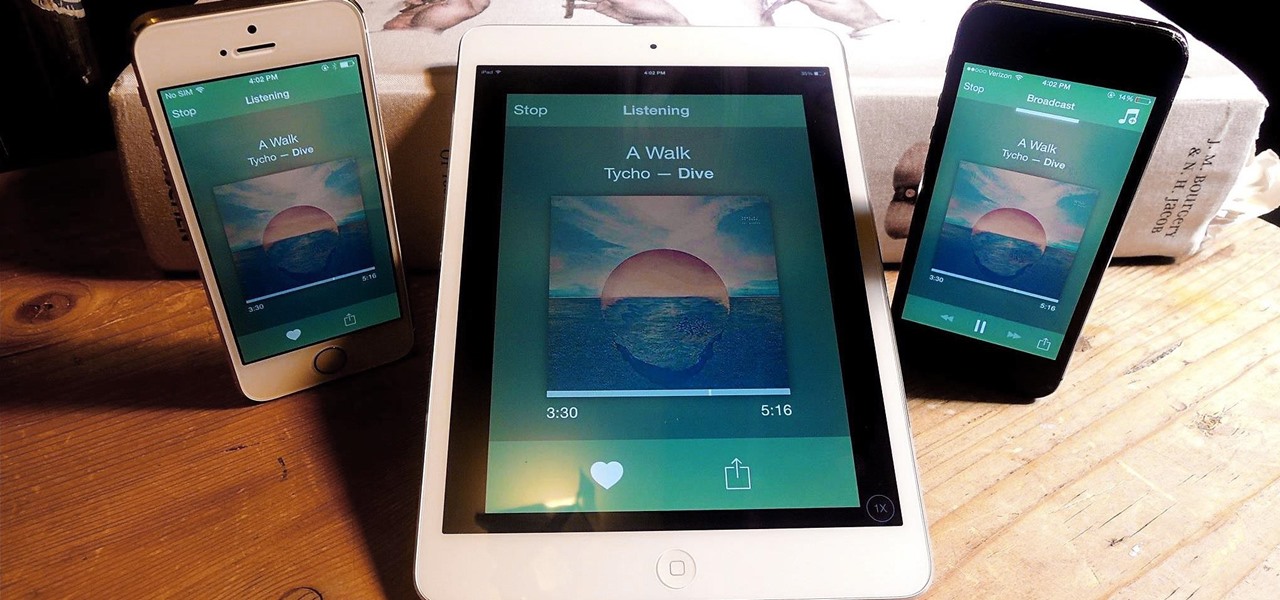
Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

Video: . How to Remove a Callous from your Feet.
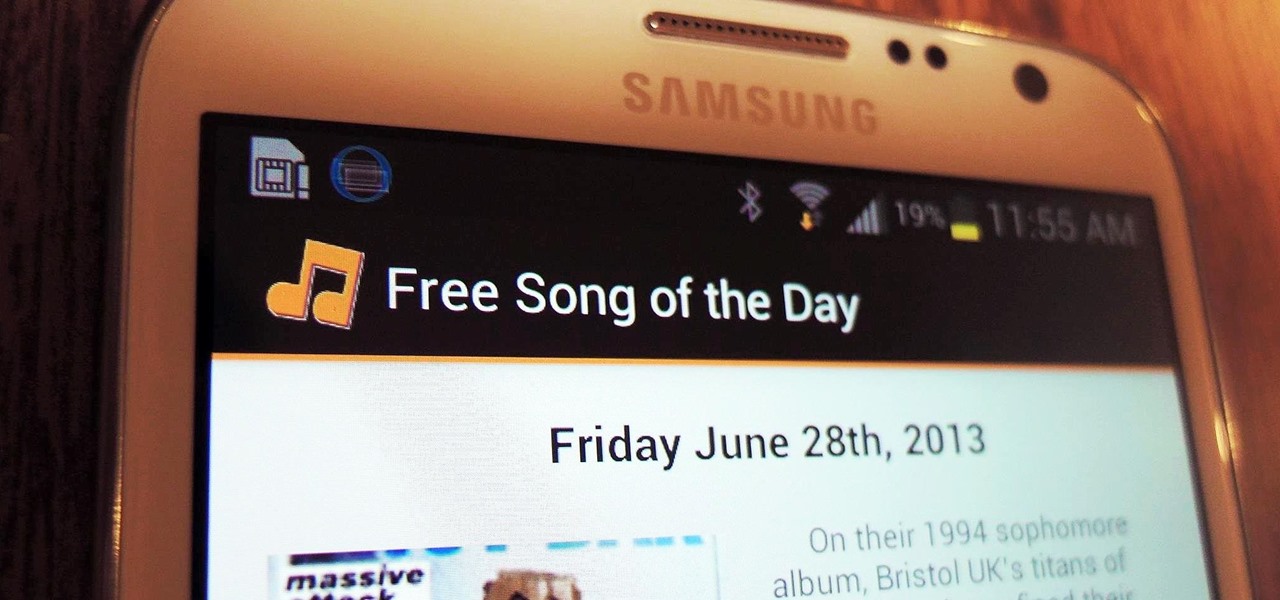
With millions of options to choose from in Google Play's expansive library of songs and albums, it can most definitely take a toll on the wallet after a while. As (slight) consolation, Google offers one free song a day, available for download straight from Google Play onto your Samsung Galaxy Note 2 or other Android device. Google's daily free song sure beats other services' free selections. Apple only offers one free single each week, and Amazon offers a decent selection of free songs from r...

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

When it comes to melee combat, two swords can definitely be better than one. Throw a stun gun on top of that and you've got a seriously terrifying weapon. That's exactly what YouTuber jonathanj9969 did with his homemade double-bladed stun sword.

This is a very cute baby pink nail art design that I did last week and wanted to share with all of you because it looked so very adorable and I knew lots of girls would like it !

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

Michael Faraday was awesome. He discovered electromagnetic induction, diamagnetism and electrolysis, and he invented the Bunsen burner (before it was the Bunsen burner). Because of his work, we can make suits that can withstand 1,000,000 volts of electricity and cases to protect our gadgets from nuclear attacks.

It can get pretty chaotic when you're gaming. When you're playing a fast-paced game like Black Ops, frustration, urgency, and confusion will lead to a sudden loss of control, i.e. a panic attack. There's an enemy at your six and you try to spin around, but it's too late—and that sudden rush of adrenaline will tear your controller to shreds. It's a step beyond mere button-mashing, because it's not really intentional—you just put a little more force on that thumbstick than needed. And now you'r...

Want to give a special someone your heart (but maintain vital functioning)? Make a paper heart using origami, the traditional Japanese folk art of paper folding. This free origami video lesson presents complete instructions on how to make your own paper hearts from folded paper. For more information, and to get started making paper hearts yourself, take a look!

So you've made it this far, and there's only one man that is standing in your way, and that's the masked butcher. If his exploding barrels, or grapple attacks, are causing you more than a little bit of an ache, don't worry, it's easy to beat him. In this video you will learn the strategy you will need to be victorious!

Watch this piano tutorial to learn how to play "Your Heart is an Empty Room" by Death Cab for Cutie on the piano. Instruction features chord breakdowns and individual melody note names. Beginners will have no trouble learning how to play Death Cab for Cutie's "Your Heart is an Empty Room" on piano after watching this helpful how-to video.

Learn how to make the MAPAJET (most accurate paper attack jet); loads of office fun! This video origami tutorial shows how to fold an accurate paper airplane.

This video demonstrates how to select your weapon in Gears. The video walks you through switching weapons and performing melee attacks with different weapons.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

The bigger the group chat, the harder it is to follow. Messages start flying one after the other, and before you know it, you're hopelessly lost in the conversation. With most chat apps, there's nothing you can do, other than telling your friends to slow down a bit. But on Telegram, you can make them slow down.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.
Apple's upcoming iPhone update, iOS 13.3, doesn't add as many new features as iOS 13.1 or 13.2, but there's one under-the-radar change you'll love if you use Apple News on a daily basis.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Snapchat and Snap Camera aren't the only augmented reality apps available for couples to use on Valentine's Day.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.
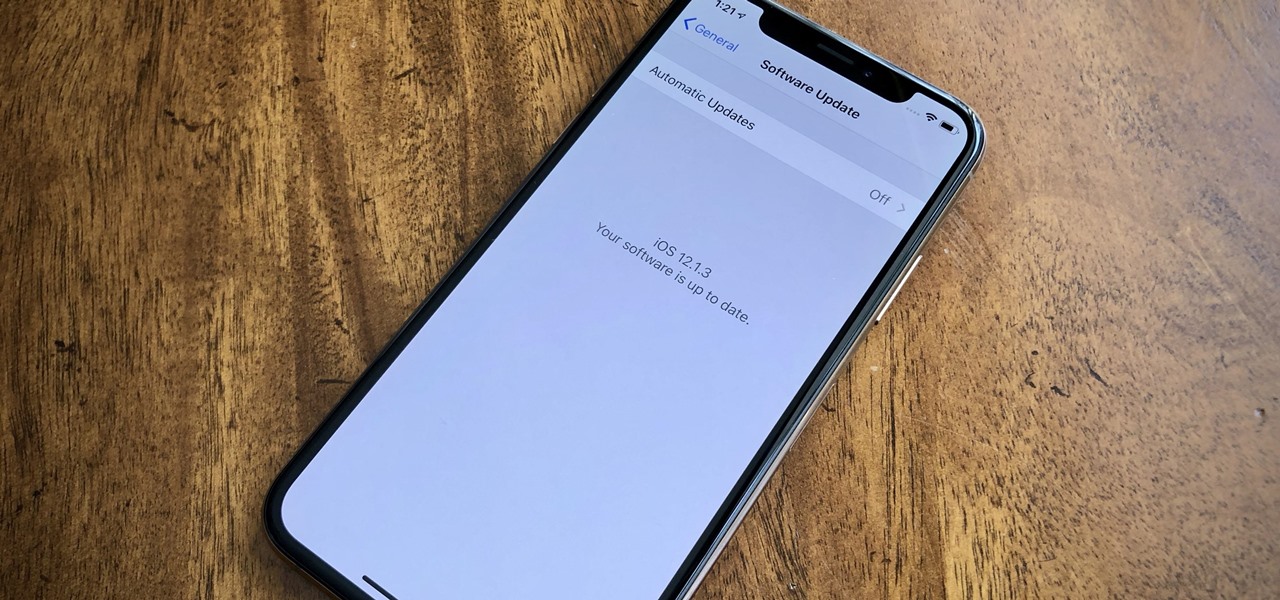
Just after a month of testing, iOS 12.1.3 has been released for iPhones. Like the previous iOS 12.1.2 update, there's not much to get excited about. There are no new features discovered yet, but there are a few fixes for issues with photos in Messages, imperfect pics when using the share sheet, and disconnecting CarPlay.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Apple released the iOS 12.1.3 developer beta on Monday, Jan. 7, and the iOS 12.1.3 public beta followed shortly behind. Apple has been pretty on point with its public beta releases for iPhone, always releasing the same day as the dev version unless it's the very start of a beta build (i.e., iOS 12.1.3 beta 1), in which case they come out a day later.
Attention all iOS software developers — Apple just released iOS 12.1.3 beta 3 today, Monday, Jan. 7. This is the first update in quite some time for beta testers, as Apple released 12.1.3 beta 2 nearly three weeks ago. While we don't expect beta 3 to offer users a monumental upgrade to iOS, it's still an important update nonetheless.

Apple pushed out iOS 12.1.3 developer beta 2 to all developers on Wednesday, Dec. 19. It's an interesting and mysterious update, as it follows the sudden release of iOS 12.1.2. That software only had one beta version before its stable release, which would explain why the iOS 12.1.3 dev beta skipped version 1 and went straight to version 2 since it's basically a continuation of the first iOS 12.1.2 beta.