ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Tired of being attacked by the goblin army in Terraria? Here's a sure-fire, or rather sure-lava, method for defeating them. Watch this video to learn how to design a lava trap that will make the goblin army vulnerable to your attacks.

This is a match that takes a look at rapidly changing from a queen side attack to a king side attack, and how that can sometimes catch your opponent off guard. The match also shows how creating complications can sometimes mask the most deadly, yet subtle threat.

Here is a match with a Reti Opening transposing to a King's Indian Attack. See how to do it, and see why to do it.

This is an introduction to the Veresov Attack 1.d4 Nf6 2.Nc3. It features a game in which Matt crushes a reasonably strong guest who only makes 2 very natural looking errors (...O-O and ...c4). Try it out for yourself.

In this series, Matt will examine the Stonewall Attack for White and display defenses which he thinks are challenging and/or interesting. Here's a prototypical Stonewall game where everything goes right for White.

This video demonstrate a system against the King's Indian Attack. Enjoy! And don't get too good, because if we ever play, I don't want to lose.

This is a trap in the Torre Attack (1.d4 2.Nf3 3.Bg5). It's a favorite in opening traps, so watch and learn. You'll need it someday.

OK, are you looking to jump in your time machine and dance the Achy Breaky Heart line dance. Well, this how to video will prep you for your trip to the past. Get you comfortable shoes, gather up your friends who are eager to dance this country classic, and start heart breaking today! One, two, three, four, leave your horse outside the door. Don't get down, stand up! Oh Billy Ray, we'd never break your heart! Even after you wrote this song.

Wilton Cake Decorating demonstrates how to make and decorate a heart fireworks tiered cake. Roll out the pliable edible cake clay so that it is about 1/4 of an inch thick. Cut out heart shapes with cookie cutters. Let them dry for a few hours. Attach the hard hearts to wire with an icing adhesive. Create a bouquet out of the candy flowers by crooking the end of the wires and sealing the bases with floral tape. Create three-inch panels for the six-inch cake out of the cake clay. Cut out heart ...

Take a look at some vectored hearts… it's fully vectored. Older versions of Illustrator should be able to handle this project just fine. Watch this Illustrator video tutorial to learn this heart-shape design. A vector heart is great for Valentine's Day. No source files are needed. Just Adobe Illustrator and some time. Learn about using the grid, the basic pen tool, gradients, swatches, blend modes, masking, and so much more.

Your job is to defeat Sapientia in this fight on the Xbox 360 game Bayonetta. In Chapter 13 - The Cardinal Virtue of Prudence, attack the red sphere over Sapientia's head. This fight starts with Bayonetta on the ocean, on a surfboard-like object. Sapientia will use two attacks. The first attack starts with his fin sticking out of the water, like a shark. He will then jump into the air and dive at you. Just keep moving in a straight line to avoid this attack. For the second attack the camera w...

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Welcome back, my rookie hackers!

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Wire hearts are cute, friendly jewelry pieces that are as versatile as they are attractive. Composed simply of a bent and twisted piece of wire, they can be shaped into bookmarks, earrings, necklace chains, and bracelets.

Ah, the heart. The eternal symbol of love and torment, the starter of wars and the locale of true victories. Heck, the heart is such an ingrained symbol in our culture that there's an entire holiday devoted to it.

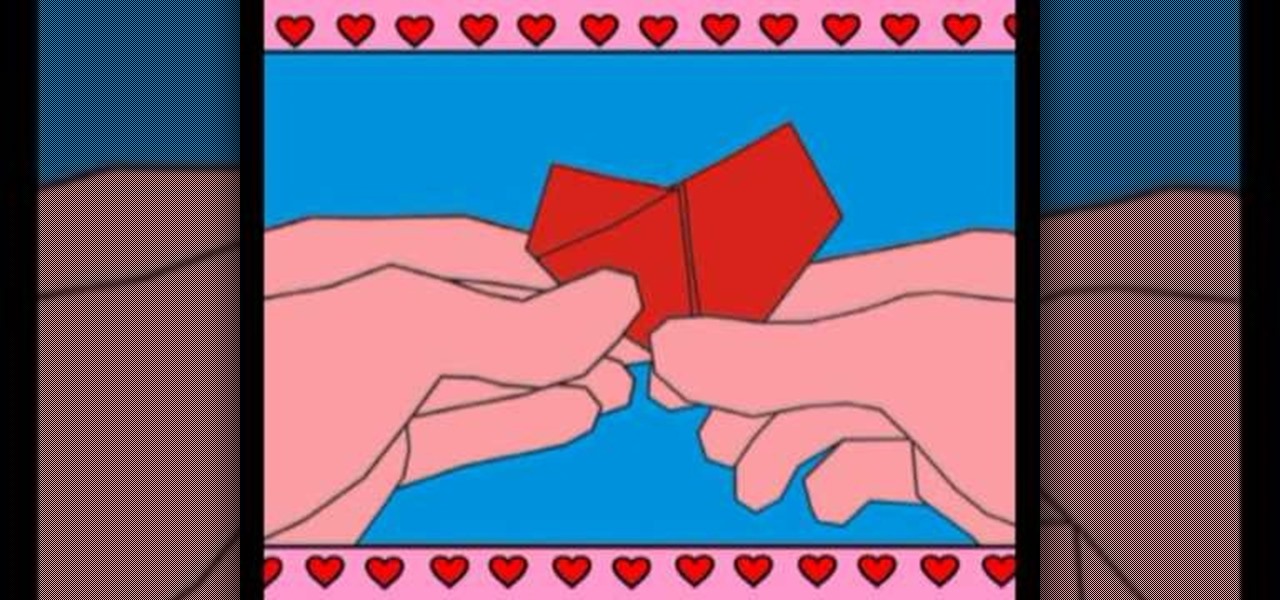
Want to give a special someone your heart (and get rid of junk mail in the process)? Make a paper heart using origami, the traditional Japanese folk art of paper folding. This free origami video lesson presents complete instructions on how to make your own paper hearts from a folded letter . For more information, and to get started making paper hearts yourself, take a look!

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

Street Fighter IV : Blanka, the Brazilian Beast unleashes havoc upon the World Warriors once again. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

Street Fighter IV : Vega, the beautiful Spaniard delivers gruesome damage. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

Want to know what a septum is? An aorta? The bicuspid valve? These are all parts of the human heart, and in these educational tutorial videos, you'll learn all you need to know about the physiology of the human heart. Anatomy, biology, physiology... it's all science, so no matter what field you are studying, these will be very helpful for you in your further medical studies, or for just know-it-all knowledge.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Minecraft 1.8 has introduced Enderman to tons of blocky servers all over the world. If you're looking for ways to fight against Enderman or just avoid Enderman all together, take a look at this walkthrough on how to do both. Be sure to grab an Ender Pearl so that you can half their attack range!

Wolverine in the most well-known X-Man and arguably the most famous face in Marvel comics. Of course he kicks ass in Marvel vs. Capcom 3! This video will teach you the basics of fighting with Wolverine, including his basic attacks, special moves, and some combos.

Okami was one of the best games of the last decade, perhaps Capcom's finest, and it's heroine Amaterasu makes a much-deserved appearance in Marvel vs. Capcom 3. She isn't quite as powerful as you'd expect the God of Everything to be, but she kicks serious butt and this video will teach you the basics of fighting with her, including tips on all her normal attacks and special moves.

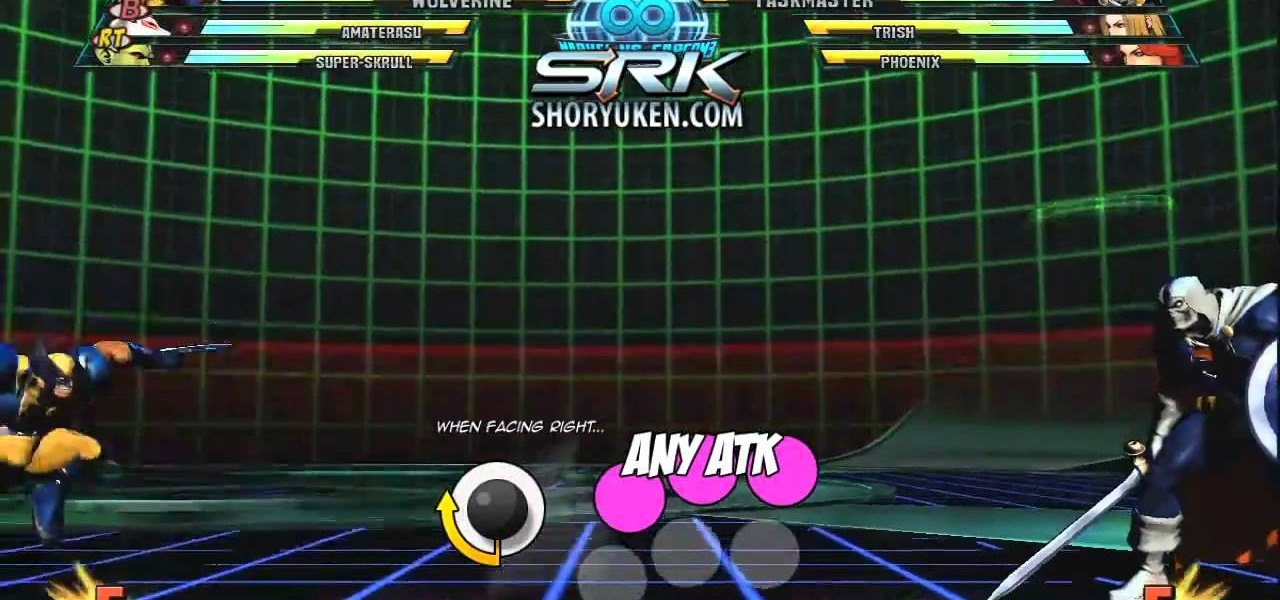
Marvel vs. Capcom has been the flagship series for frenetic 2D fighting games for years, and Marvel vs. Capcom 3 hit store shelves in February. This video tutorial will teach you the basics of the game, including basic combos, hyper combos, team combos, special attacks, and more. Everything you need to start off your MvC3 career right.

This short animated tutorial will show you how to assemble an origami heart that even the clumsiest butterfingers among us can perfect. Since Valentine's Day is coming up, you best hone your skills at this heart so you can give a few to your amor.

Beyblade is a fun game from Japan that is very similar to Spinjas but much more complex. If you're new to the game or just ant some expert advice watch this video to learn about the four mains types of Beyblade (attack, defense, stamina, balance) and how they can each be used to play better Beyblade.

The SAW lead is the most recognizable sound in hardstyle and hardcore electronic music, sounding like a swarm of bees attacking with the precision of an honor guard. Watch this video to learn how to program a patch for a SAW (or sawtooth) lead on a MicroKorg.

"My Heat Will Go On" by Celine Dion made her the biggest artist in the world for a time after the release of Titanic, the film with which it will always be associated. Watch this video to learn how to play the whole song on solo piano, which might be the most romantic thing that you could ever do.