
How To: Drive a manual transmission (stick shift) car
This automotive video tutorial will show you the steps on how to properly drive a manual transmission car.


This automotive video tutorial will show you the steps on how to properly drive a manual transmission car.
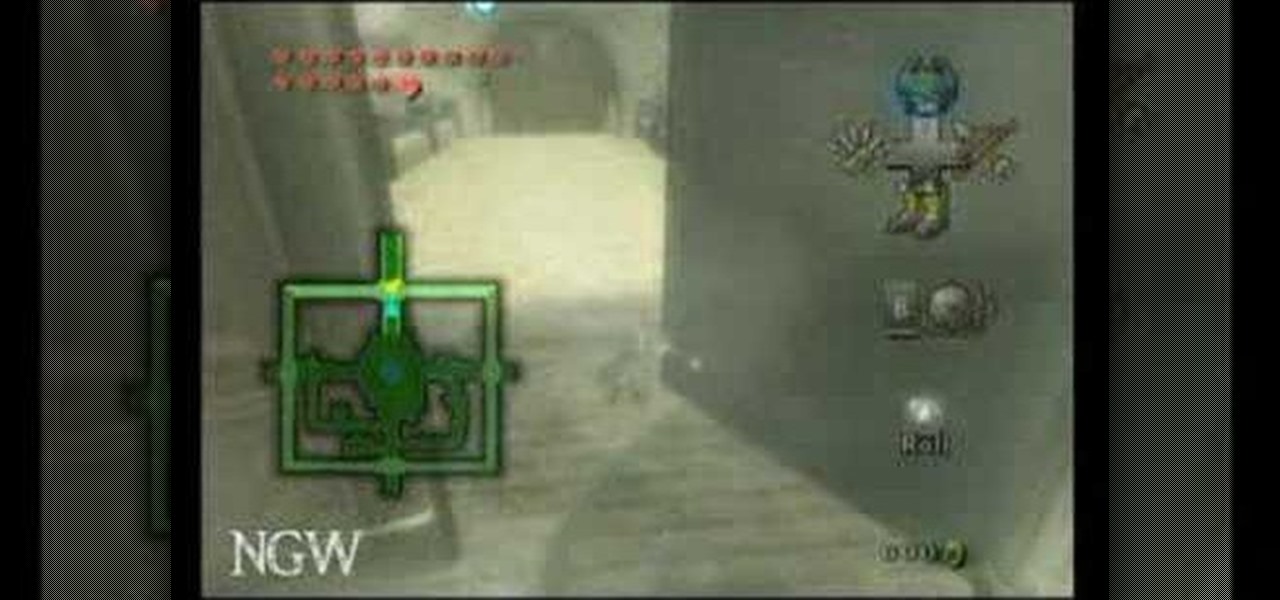
This video walkthrough guides you through the "Hyrule Castle" chapter of Legend of Zelda: Twilight Princess for the Nintendo Wii including the boss fights and locations of any heart pieces, golden bugs, and poe souls.
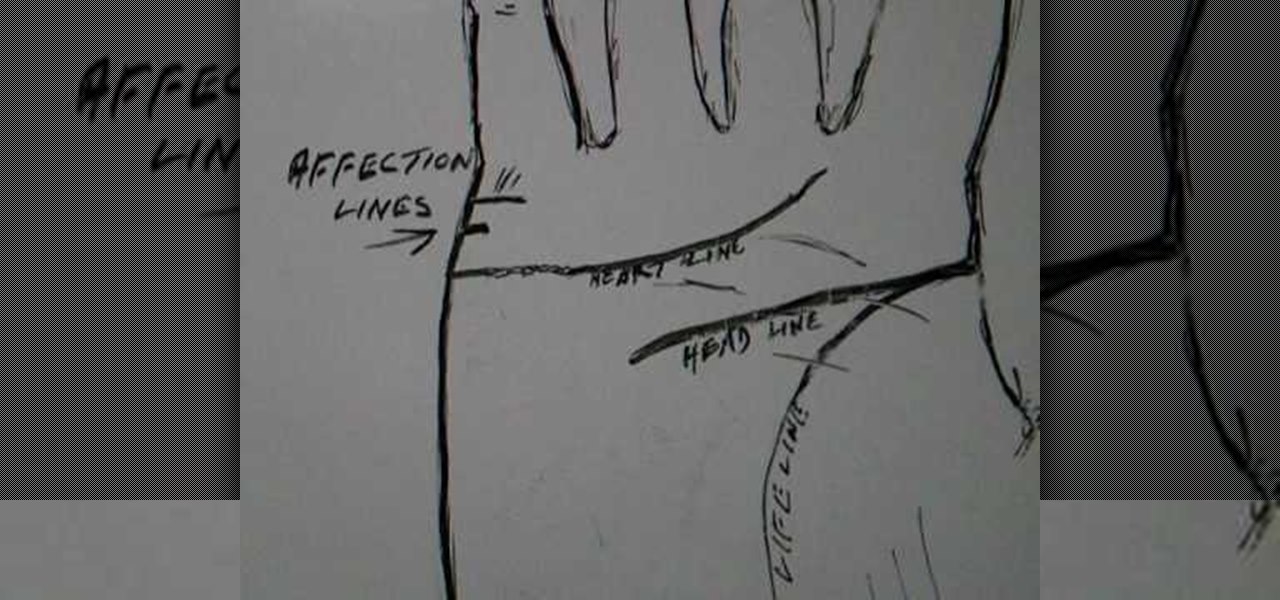
Read affection lines and the heart line in palmistry. The affection line sometimes two and some time just one. Looking at the affection line one by another person. Now looking for married not necessary a two affection line and heal the heart line finishes up. Some time settle for the head. Dividing the affection so feel change time to time. On the wide life feel about different people. Now looking for the heart line show early in beginning. We can show under the little finger. After early mar...

Learn how to play "Human" by the Killers, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

In this video we will look deeper into astrology, we begin to recognize there is more

Want to put a heart frame on your pictures but don't know how? This wonderful video teaches you how to do it using Photoshop. Watch now to learn its easy and simple steps.
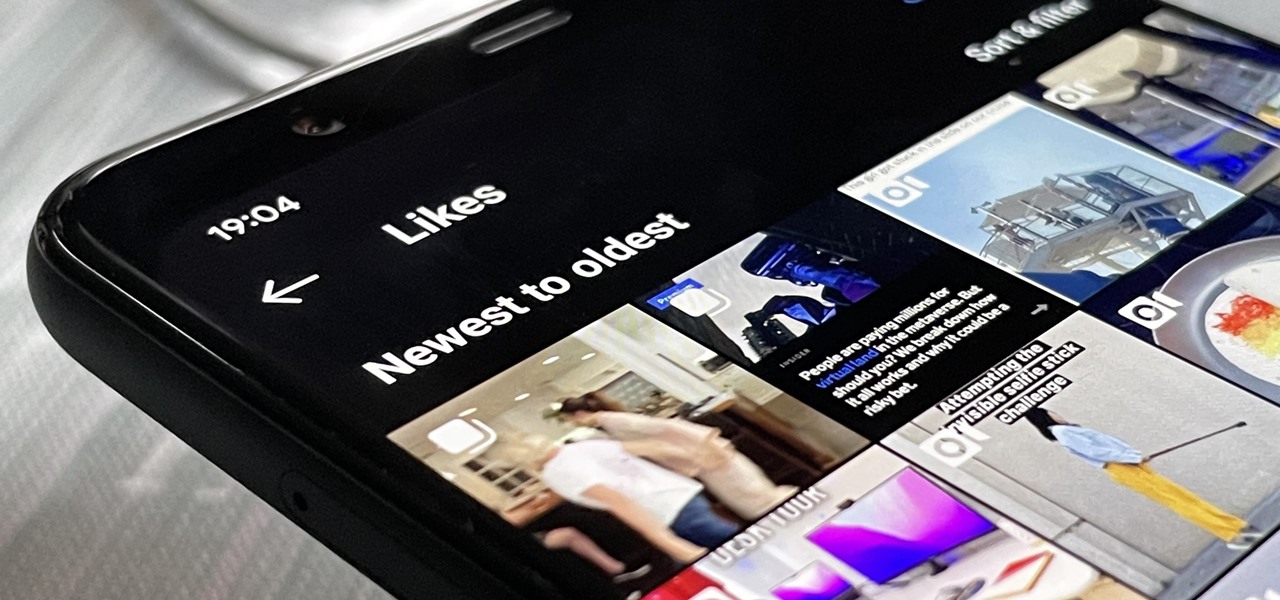
Unlike TikTok, there isn't a convenient "Likes" tab directly on your Instagram profile page to see all the posts you've ever loved. That's too easy. Instead, you have to dig a bit deeper if you want to take a trip down IG memory lane.

If you consider yourself an emoji master, you'll have to retrain yourself once you install iOS 14.5 on your iPhone. Why? Because there are 217 new ones available to incorporate into your sometimes cryptic emoji messages.

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.

Snapchat is probably used to Facebook copying its features by now, but Apple borrowing a page out of its playbook is likely a bit more surprising.

Legendary drum-and-bass artist Squarepusher, the Warp records labelmate of fellow electronic music legend Aphex Twin, is back with his fifteenth album called Be Up a Hello, which is set to drop on Feb. 1.

As Microsoft works toward fulfilling its $480 million contract to supply modified HoloLens 2 headsets to the US Army, Airbus is preparing to supply advanced augmented reality apps for the device.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In a world where augmented reality is becoming the hero of the movie marketing, Universal Studios has decided to use the technology to reinvent the traditional movie trailer, a time-tested tactic of film promotion, in support of the forthcoming Robert Zemeckis film, Welcome to Marwen.

Location-based AR game Ghostbusters World is creeping closer to launch, and developer FourThirtyThree has released some new gameplay footage and a trailer to capture the interest of the living.

Less than four months after Snapchat introduced its Snappables platform, Facebook has met the challenge with its own AR gaming feature that surpasses the originator.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.
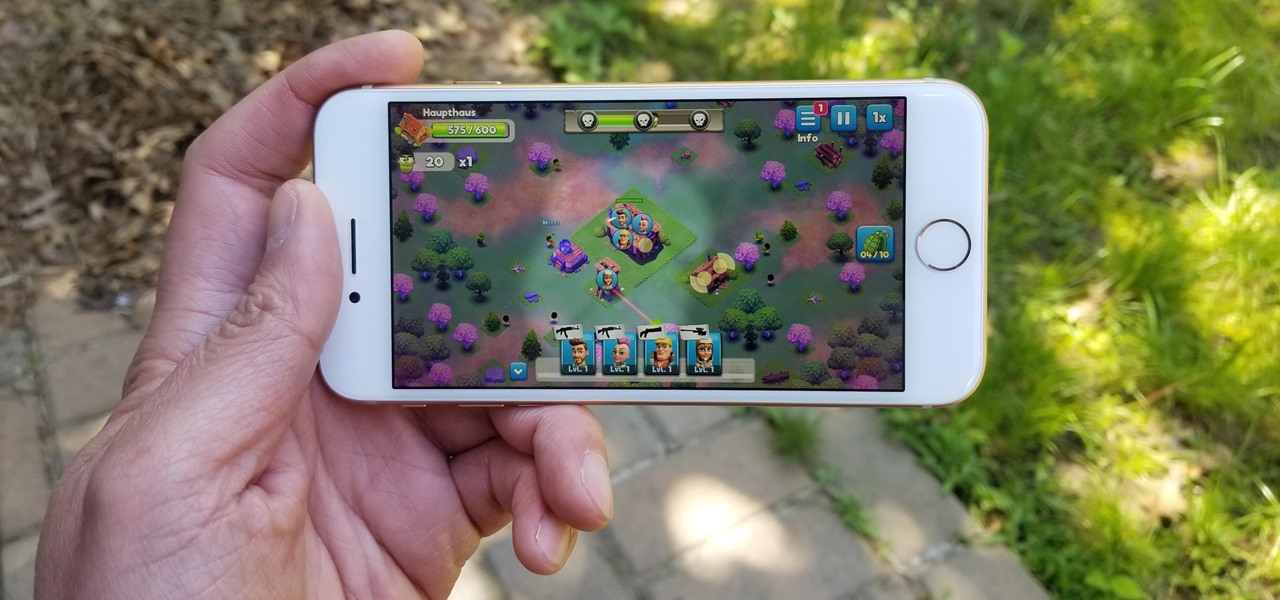
With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

Soon, Pokémon GO allies attacking a raid boss at a gym will be able to do so together in augmented reality.
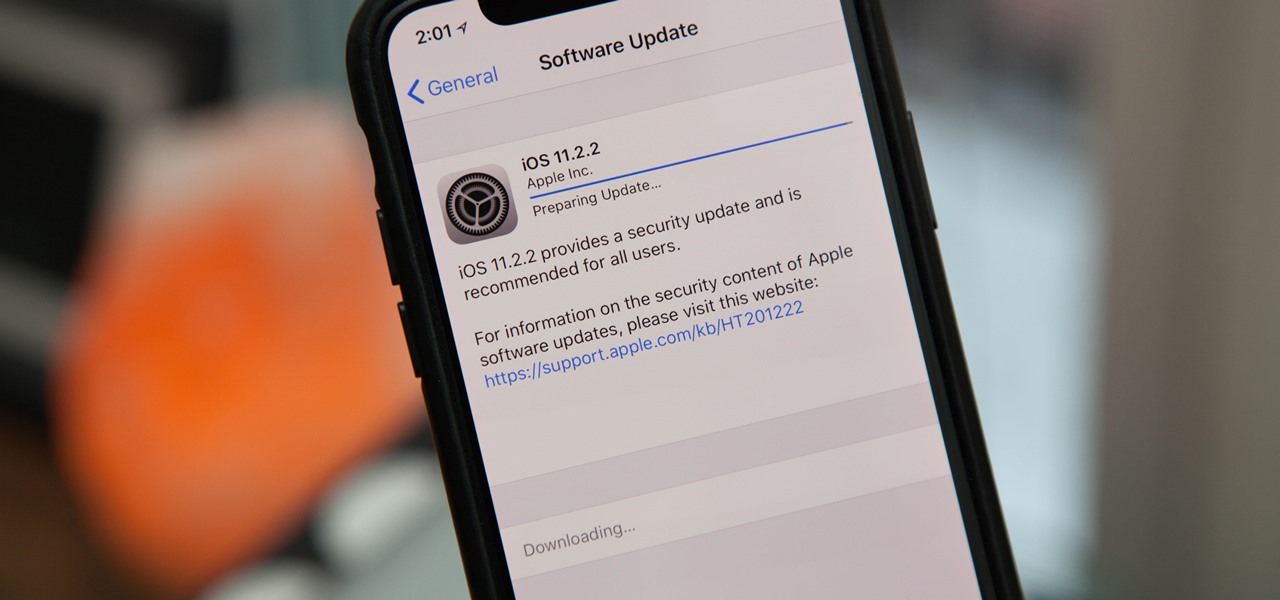
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Until Star Wars Jedi Challenges arrives in November, a forthcoming ARKit revision of HoloGrid: Monster Battle from Tippett Studios and Happy Giant, might be the closest most Star Wars fans can get to playing the HoloChess game from the movie.
Google largely helped to pioneer the concept of a steering wheel- and pedal-free self-driving experience when it began testing its Firefly pod-like vehicles a few years ago.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

You know the drill. It's time to d-d-d-duel! This time you're a part of the Shadow Games in a way you've never been before, thanks to Micorsoft's HoloLens.

Disasters can happen at any moment, and when they do, it's often hard to find the right information to help you get to safety as quickly as possible.

As a side scrolling game, performing various jumps in Super Mario Run on your iPhone or Android is as vital as eggs in a breakfast buffet.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

The Sharknado franchise is, somehow, releasing a fifth movie "Sharknado 5: Global Swarming" (groan) next month. In anticipation of the film's release, the company has decided to create an augmented reality mobile game called, prepare yourself, "Sharknado: ShARkmented Reality".

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

As researchers from Yale searched our environment for compounds to aid in the battle against drug-resistant bacteria, they got an unlikely assist from ticks.