If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Almost half a year after we broke the story about the demise of Meta Company, there's good news for fans of the augmented reality startup — a rebirth is at hand.

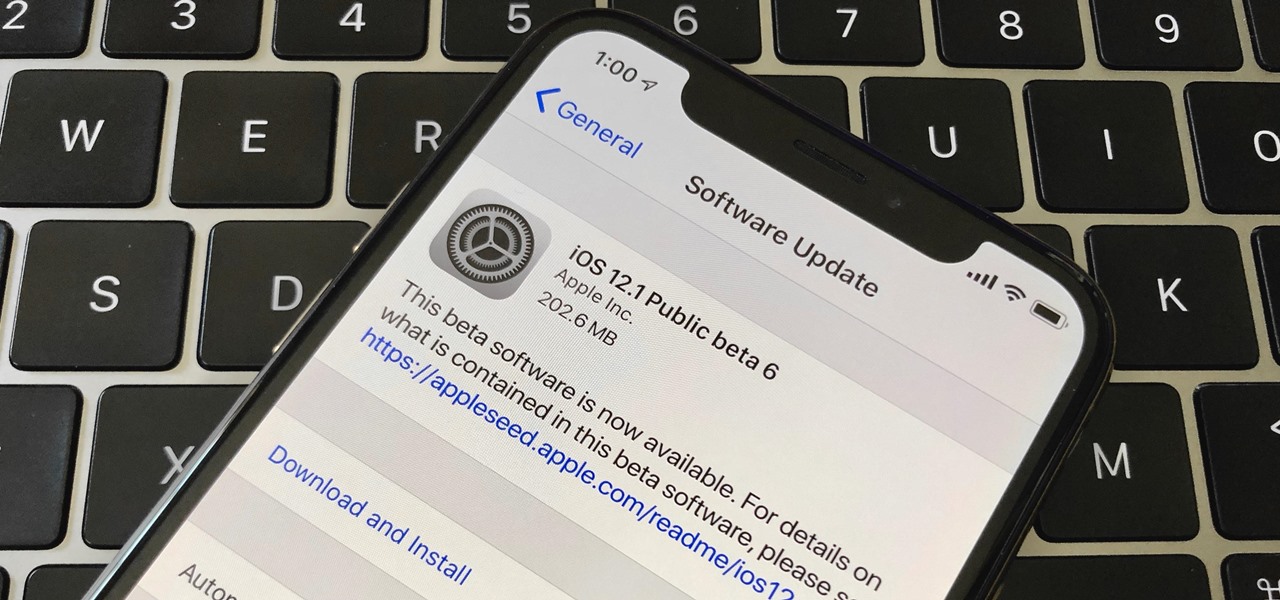
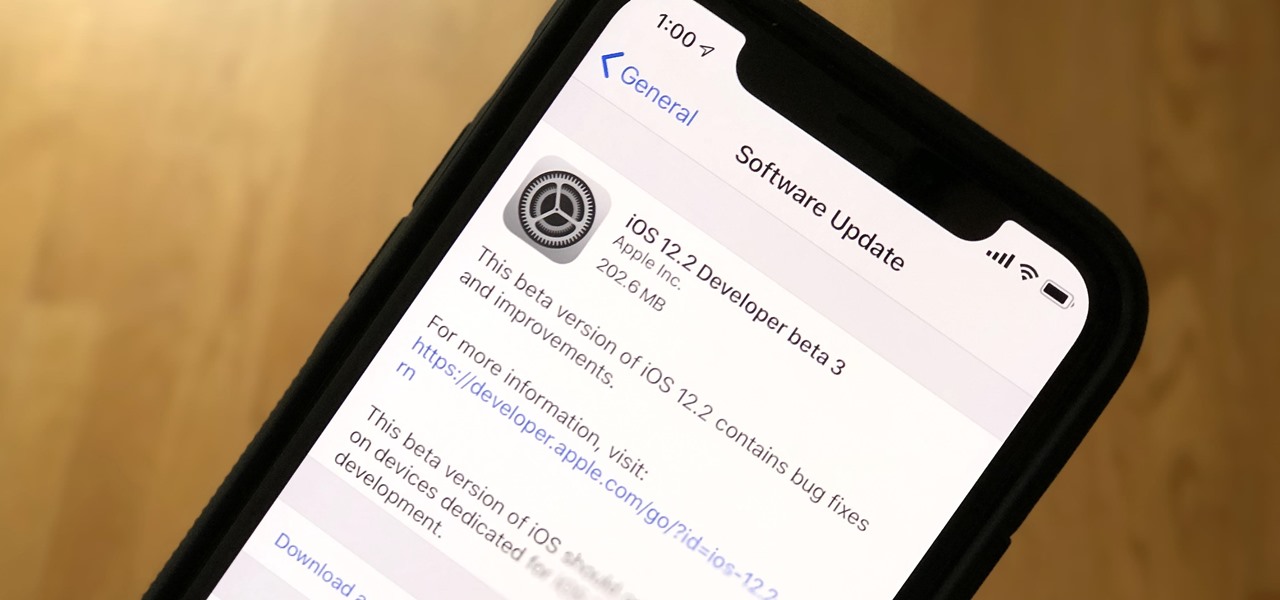
Right after Apple released iOS 12.2 dev beta 6 on Monday, March 18, it seeded the public beta version. So far, from what we can tell, the sixth beta includes a patch for an Apple Pay issue and yet another update to the "About" page in Settings, this time with a new section for warranty and insurance information.

Public beta testers are in for a treat today. While Apple is extremely inconsistent with the release schedules for the developer and public betas, the company has once again released both versions of iOS 12.2 beta 5 today, March 11. If you're a public tester, you now get to experience all of iOS 12.2's new additions for yourself, instead of needing to read about them for up to 24 hours in advance.

If you're an iOS app developer, your Monday just got better; Apple just released iOS 12.2 developer beta 5 to your Software Updates today, March 11. This fifth beta includes a number of small UI changes and tweaks, and likely some degree of under-the-hood improvements and bug fixes.

Apple released iOS 12.2 beta 4 to developers on Monday, March 4, then shortly thereafter also pushed it out to everyone on the iOS 12.2 public beta program. All previous public beta updates for iOS 12.2 were released the following day, but this one changes course. In the iOS 12.2 public beta 4, there are new icons, an updated "About" page, and better Now Playing tile.

Apple released iOS 12.2 beta 4 to developers on Monday, March 4, and that means public beta testers will likely get the update on Tuesday. The update features a fresh "News" app icon, a new "Apple TV Remote" tile in Control Center, and a tweaked "About" page, in addition to seemingly under-the-hood updates. If you're not yet on the beta, now's your chance to see it for yourself.

While developers received iOS 12.2 beta 3 on Feb. 19, public beta testers had to wait one extra day, following suit with previous iOS 12.2 beta releases. The third beta update includes fixes for Group FaceTime and the missing date on the lock screen, as well as a few tiny app updates.

Apple just released the third iOS 12.2 developer beta Tuesday, Feb. 19, fifteen days after the release of iOS 12.2 developer beta 2. Beta 3 fixes an issue with the lock screen, and reintroduces Group FaceTime to beta testers. Overall, iOS 12.2 hosts a wealth of new features as well as bug and security patches.

According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

It's been a long road, but the guys over at CoolStar have finally come up with a stable, semi-untethered jailbreak for 64-bit iPhones, iPads, and iPad touches running on iOS 11.2 up to 11.3.1, with the latest update extending coverage to 11.4 beta 3. So if you've held off on updating to the latest iOS 11.4.1, your patience has finally paid off.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

Smartwatches are an excellent way to keep track of our smartphone's notifications as well as our own fitness. However, these devices are not usually cheap. If you'd rather not pay a premium for a piece of wearable technology, check out all the Black Friday deals on smartwatches — we've got all the best ones listed right here.

Directive Games received the enviable honor of unveiling their ARKit game, The Machines, on stage as part of Apple's iPhone launch presentation.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.