
Today's Top News: Elon Musk Warns of Zombie Driverless Fleets
Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.


Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.
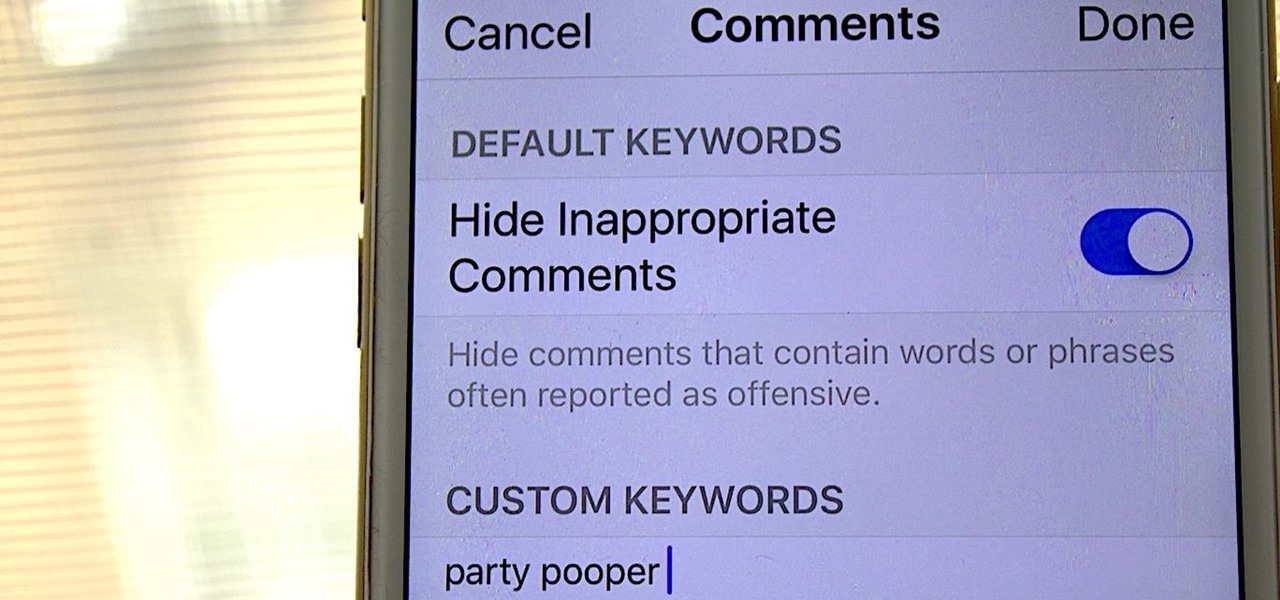
One of my favorite things about Instagram, and the reason why it's still my go-to app, is the fact that it's not like Facebook or YouTube. After our last presidential election, well, I think we've all been scarred from going anywhere near Facebook. And YouTube, I'm not sure why comments on that platform are some of the worst, but they are.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.

Legionnaires' disease is named after 1976 outbreak in Philadelphia that sickened 221 people and killed 34. More often striking adults over the age of 50, the Centers for Disease Control and Prevention (CDC) recently reported two cases where newborns contracted the often fatal disease — at their moment of birth.

Listeria monocytogenes bacteria don't play fair. Healthy people can usually handle the food-borne infection, but the bacterial infection hits pregnant women, fetuses and cancer patients very hard. Interestingly, a new study found that other bacteria may help prevent Listeria infections in those people.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.
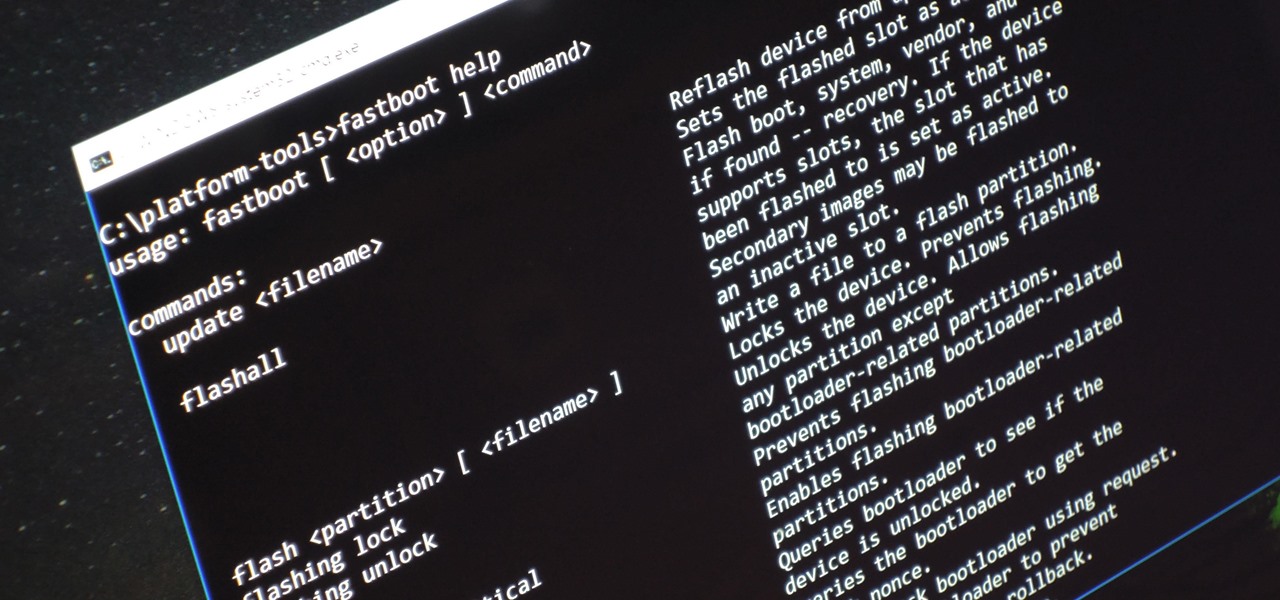
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

Fans of fighting game series such as Street Fighter and Mortal Kombat are in for a treat! Skullgirls has entered the crowded field of the mobile fighting genre and has touched down in the form of a soft launch for iOS devices, which is now available for download in Canada and the Philippines. But don't let this limited release stop you from trying Skullgirls out, as it's still possible to acquire this little gem with a little finagling.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

For those familiar with my old YouTube series, New in the Store, you will be excited to know that I am starting something very similar here on NextReality that's a bit more broad in scope. Have You Seen This? will take a look at HoloLens applications that are new in the Windows Store, as well as some that may not have gotten the attention they deserve.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

With folks drawing lines in the sand before the upcoming election this November, it's important to know where you stand on some of the most important issues: the economy, foreign affairs, domestic affairs, and apples—caramel or candy apples, that is.

In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz anyway.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

The iconic, lovable gummy bear originated in Germany, where it goes by the name Gummibär— but that's not what makes it so much fun. The base of gummy bears is made up of gelatin, which gives them the signature elasticity that makes you feel like a kid again. But the fun doesn't have to stop there.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

In the moment, buying a dozen donuts always seems like a good idea. In retrospect, however, it's always too much... and you inevitably end up with a box of stale donuts a few days later.

Greetings my fellow aspiring hackers,

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.
Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back, my greenhorn hackers!

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?