In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

The lingering smell of cigarette smoke can bother just about anyone, including smokers themselves. Unfortunately, it can be quite difficult to mask or completely get rid of the smell altogether. While you can go through extremes like washing and even repainting the walls in your home, those options don't exist when the odor is in your car.

If you've spent any time at all recently on social media, then you've probably seen pictures of fairy bread. This magical creation comes to us courtesy of Australia, so we have yet another thing to thank those clever folks Down Under for... along with shrimp on the barbie, Vegemite (the Aussie cousin of Marmite), and Hugh Jackman.

Smartphones have become such a big part of our lives these days that they're now closely associated with our personal identities. No longer is it Ford versus Chevy, rock versus rap, or PC versus Mac—now, you're either an Android person or an iOS person.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

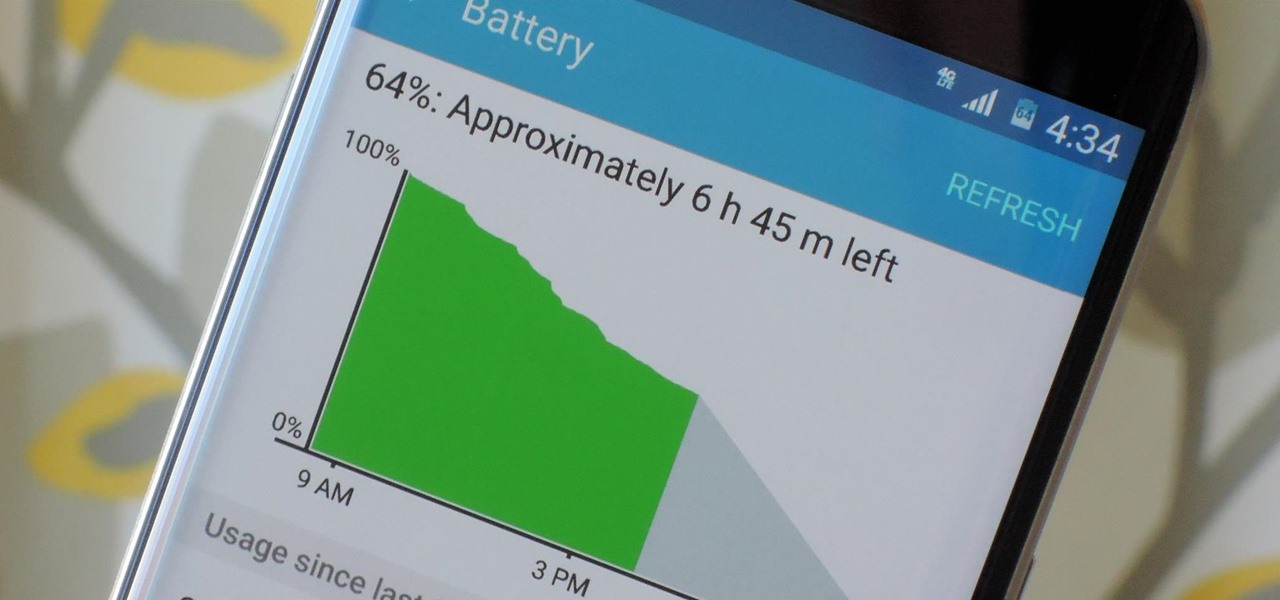
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

Being born with a sweet tooth and Japanese blood, my desire for dessert-style sushi is practically written into my DNA. At once delicious and adorable, these one-bite delights are the perfect way to conclude a meal. They're also a killer snack. Featured below are: 1) the Banana Nutella Nut Roll; 2) the Strawberry Kiwi Roll; 3) Mango and Sweet Rice Nigiri.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

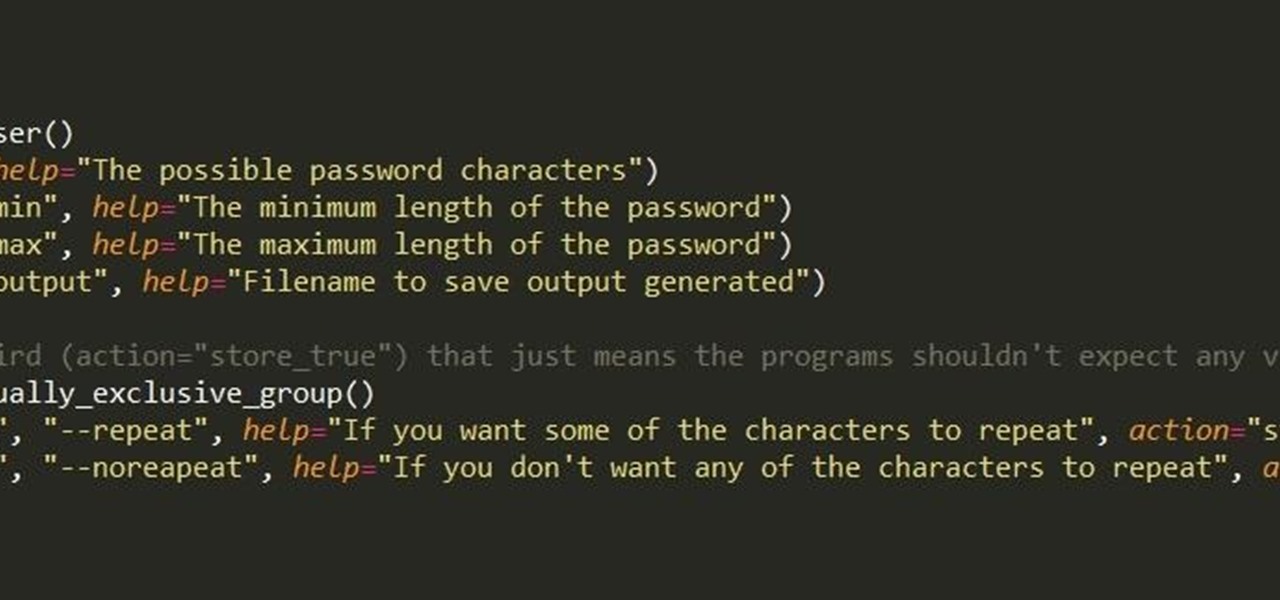
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Like most food lovers, I adore sushi. And like anyone who is a living, breathing human being, I'm a pretty big fan of sriracha sauce.

There are three huge benefits to microwave popcorn: it's quick, it's delicious, and it's cheap. But there's a way to make popcorn that's better, more delicious, and cheaper than the microwave variety. And oh yeah, quite a bit healthier.

If you've never heard of or eaten temari sushi, then you're in for a treat. These pretty sushi balls are good for parties and festive gatherings, and even though they are so colorful and striking, they are not hard to make. Just like every other type of sushi, they are customizable, and they have the cute factor necessary for kids or appetizers.

Food waste is a topic near and dear to my heart, but the truth is, no matter how dutiful we are about finding ways to double-down on food scraps, a lot of stuff goes into the trash needlessly.

It can be pretty tough to fall asleep when your brain is thinking nonstop or anxiety has gotten the best of you, and it seems to only get harder when you're lying in bed listening to yourself breathe. Yet paying attention to that breathing may be exactly what you need in order to find a calm, easy entry into a good night's rest.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

When it comes to added features, no manufacturer out there can hold a candle to Samsung. Whether it's a remote control for all of your electronics, a heart rate and stress level monitor, or a seemingly-magical stylus, Galaxy devices always have as much functionality as possible packed in.

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

The future: that time that lies ahead, unknown and overwhelming. Whether you're an obsessive planner or someone who can't think more than two days ahead, considering the future can be frightening with all of the "what ifs." Don't let the future keep you awake at night—in fact, the less you think about what life holds in store for you, the better off you'll be.

Like cigars and whiskey, Lapsang Souchong tea is an acquired taste. Some people never get over the pungent, tarry flavor and intense smell of the beverage, but using it as a rub, marinade, or other seasoning is totally smart. The tea adds a smoky yet not overwhelming flavor to dishes of all kinds. With it, you can easily get barbecue-like results for meats and vegetables, all without breaking out the grill. Lapsang Souchong tea smells like a dry campfire and tastes like a smoked sausage cooke...

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't work as advertised.

Creativity and well thought-out planning are qualities to be admired when choosing a costume for Halloween. Going out in hordes to purchase the same 'ol outfits from a local costume warehouse means you're probably wearing the same thing as thousands of other people.

Every year, some overly ambitious neighbor down the street amazes the crowds with his DIY illusion costume. While these costumes certainly require more work than pulling a mask over your head, they do have that wow factor that others lack.

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.