
How To: iDevice Jailbroken = Your New PenTesting Tool.
What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?


What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?
Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.
In recent months, HTC has decided to start breaking its proprietary apps out of its own ecosystem and into the Google Play Store. Along with the benefit of allowing its users to update their system apps more easily, this move also means that other folks can get a glimpse of what it's like to use an HTC device.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!

Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

When it comes to pizza, everyone has strong opinions about how they like their pie, whether they prefer deep dish, thin crust, Chicago-style, or gluten-free. However, most people agree that a pizza is composed of some basic parts: a single layer of crust (usually wheat-based), sauce (usually tomato-based, cheese, and toppings. Yet enterprising cooks out there are putting a spin on the classic by turning pizza on its head. Sink your teeth into these pizza hacks before it's too late!
Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face.
It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.
Spiders are common pests that typically prefer to live outdoors. However, insects and warmth will eventually attract them into our houses. They like to spin their webs in corners, crevices and unused areas of your house. Most species are harmless and even act as a natural repellent for getting rid of other insects. However, in some cases, spiders can be very dangerous. Whichever the case may be, they are scary and people are always looking for natural ways to get rid of them.

Welcome back, my greenhorn hackers!

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

One of the down-sides of international long-haul travel is layovers between flights in unfamiliar places. We have a flight to Europe this year via Guangzhou, China, and I've been putting together my notes on how to make the best use of 7 hours between flights, which I'd like to share.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

February may be the shortest month of the year, but for iOS softModders, there were plenty of apps and tweaks to fill up those days. Whether patching major security holes or just a tweak to make speed dialing more efficient, there was a plethora of great mods for our jailbroken iOS 7 devices. These are our favorites from the month.

Some food jars seem like they're actually designed to prevent you from enjoying every last bit inside. The remnants of sticky foods like Nutella and peanut butter are almost impossible to scrape out with a knife or spoon, and it's a shame to throw out something that tastes so good—especially when it's the best part. A spatula could help you get that last drop out from the walls or bottom easier, but that's just ruining your chance at maximizing the full potential of those remains into somethi...

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

How do you begin to explain the nostalgia that's felt when you play a game from your childhood? You can't. The only thing that will alleviate this feeling is experiencing it again.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

So Christmas is coming up, and you want to make a couple of presents for your friends and family, who you don't really feel like splurging on- but want to make something from the heart. You've tried other stuff, and you totally failed at the Cross-stitch from last year, have you tried Knitting?! Well here's a beginners guide to the simple knitting technique- an easy one!

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome, my neophyte hackers!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.
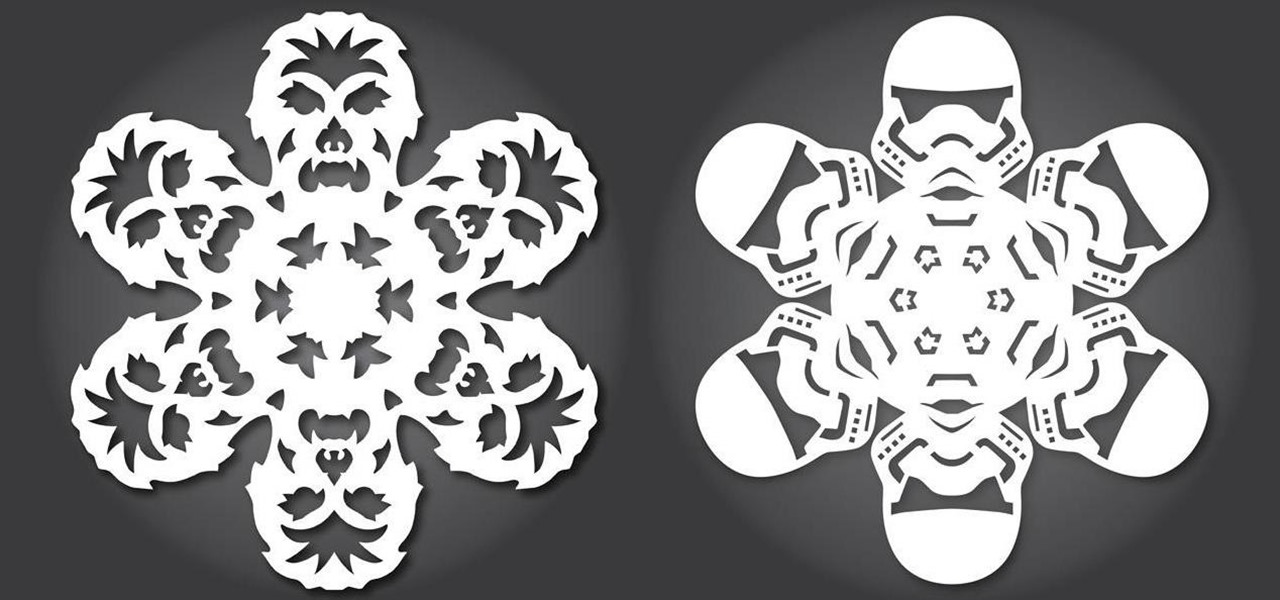
Everyone knows how to make paper snowflakes, but the kind you learned to cut in kindergarten can get a little boring. However, they are free DIY holiday decorations, and they don't have to be a generic snowflake design. They can be anything you want, from nerdy math kirigami to all the Star Wars characters you can think of!

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.