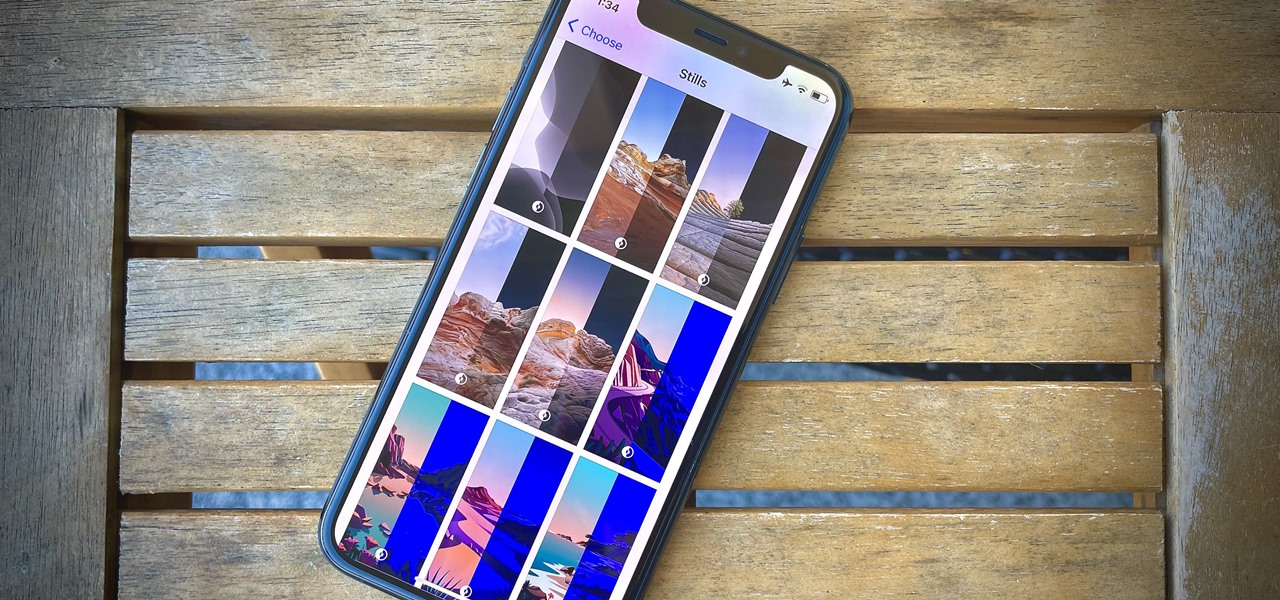
Unlike most of Apple's other apps and services, it's not always obvious when Siri gets new features. Even if you're an avid Siri user, there's no way you can catch them all, especially when half of them aren't even mentioned by Apple anywhere. But that's what we're here for, and this is everything you need to know about Siri in the latest group of features.
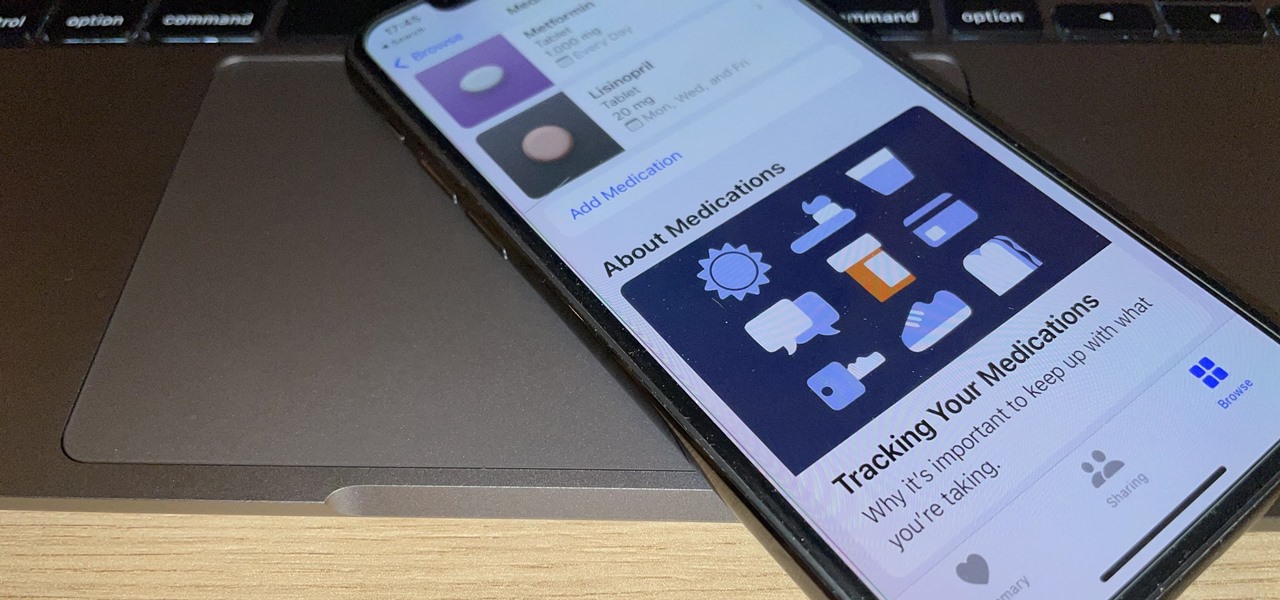
You've probably already been using iOS 16 on your iPhone for months, but there's a good chance you haven't found or explored everything the new software has to offer. Health-related features are usually the first to be ignored or go unnoticed, but they're essential to know about even if you don't plan on using them right away.

TikTok is all the rage right now, and its green screen effect is one of the more popular augmented reality tricks creators use to boost their viewership numbers. Now Snapchat has leveled the playing field by making it easier to access its own green screen effect.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.

There's a little-known secret in the world of microwave ovens that even the manufacturers don't care to tell you in their manuals. And once you know it, you'll never go back to using your microwave as you used to.

The App Store has been around for almost 14 years now, and during that time, we must have seen over a million games come and go and stay and expand. But only a tiny fraction of those games have become blockbuster sensations because of the mighty App Store's reach on iPhone and iPad, and many of the first big hits are still alive today for you to relive the good ol' days of mobile gaming.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

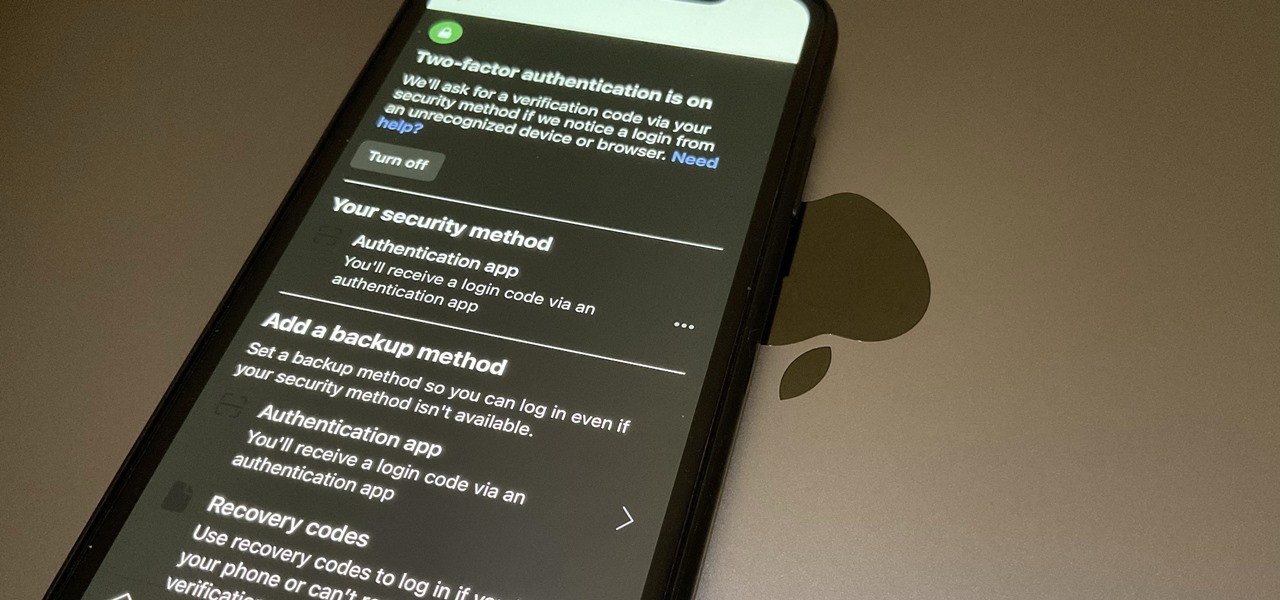
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Google dropped new features for its Pixel lineup of phones, and there's something here for everyone.

A pair of properties from the soon-to-merge Warner Media and Discovery companies chose different platforms for their augmented reality marketing, with Warner film Space Jam: A New Legacy opting to go with Facebook and Discovery Channel publishing an AR experience through Snapchat.

The Fourth of July, the celebration of US independence, as well as the second paid holiday of the summer, has arrived.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

If you have Snap Spectacles 3, the dual camera-equipped sunglasses capable of capturing 3D photos and video, by now you've likely jazzed up the videos you've captured on the wearable with Lenses via Snapchat.

For those of us without rice cookers, conventional wisdom tells us that the stove is our only real option (unless, of course, you dabble in microwavable rice). However, if you're only using the stove for cooking rice start-to-finish, you're missing out on the easiest way to make perfect rice every time.

For its latest take on augmented reality-infused playsets, Lego is giving the young, and the simply young at heart, its twist on the viral lipsync format made popular by TikTok with Lego Vidiyo.

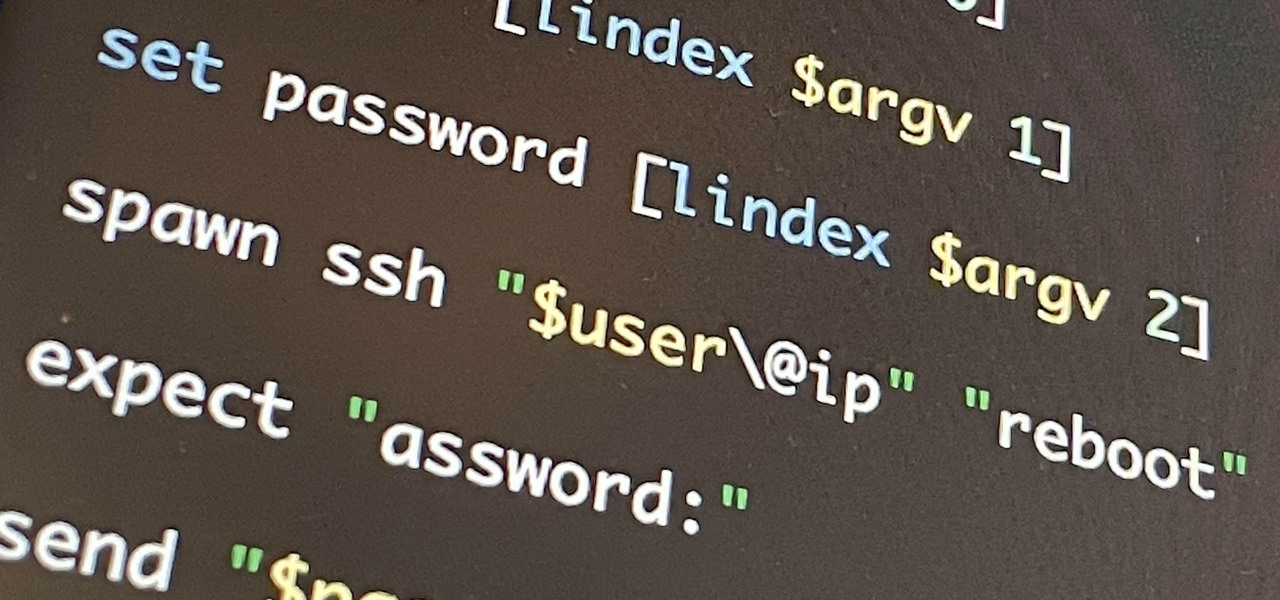
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

Apple just released the second public beta for iOS 14.5 today, Wednesday, Feb 17. The update comes just one day after the company seeded developers the second 14.5 beta. Because of that, we've had 24 hours to sink our teeth in beta 2's new features, like 217 new emoji, Apple Music lyric sharing, Apple Music UI updates, and new Shortcuts options.

Apple released the second developer beta for iOS 14.5 on Tuesday, Feb. 16. The update comes 15 days after Apple seeded developers the first 14.5 beta, which included a slew of new features such as default music app support, compatibility with PS5 and Xbox Series X controllers, and more.

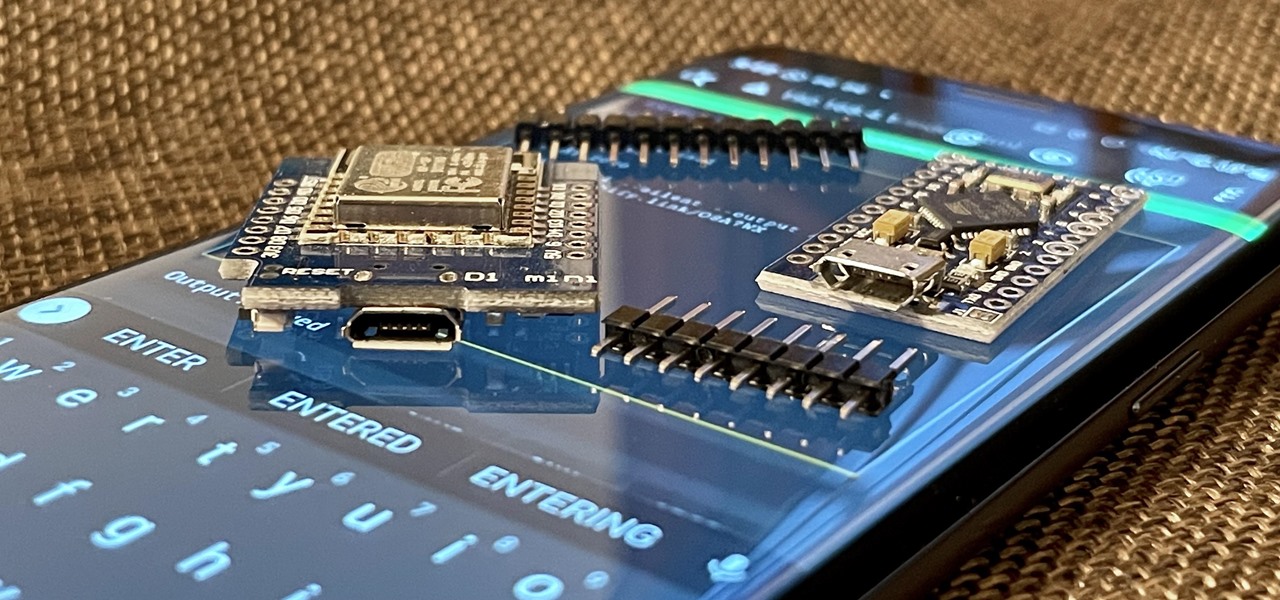
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Whether you want to give a gift that your loved one has wanted all year or one that they never even knew existed, there's something awesome for everyone in these gifts. Just as exciting as their innovative features is their price.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

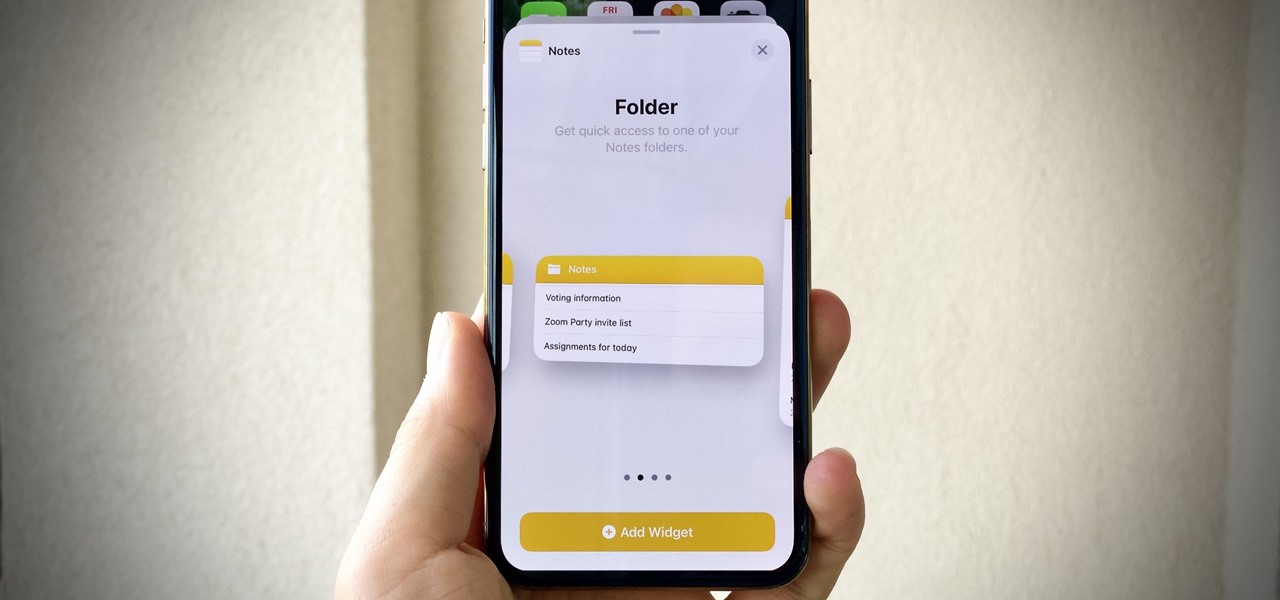
I won't mince words: the Notes widget in iOS 14 is bad. But you're not stuck with it if you want sticky notes on your home screen.

Apple's latest update, iOS 14.2, is finally here. As the name implies, it's the second major update to hit iPhones since Apple released iOS 14 in the fall. The update brings at least 13 new features and changes to all compatible iPhones, including over 100 new emoji and eight new wallpapers.

Apple released the "release candidate" for iOS 14.2 today, Friday, Oct. 30. The update is available for both developers and public beta testers, and notably fixes a pressing bug in beta 4 — users would encounter a message telling them to update from their iOS 14 beta, despite no update being available.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

For a built-in app, Notes works pretty well and can stack up against some of the best third-party note-taking tools. Apple continues to update it with each iteration of iOS, adding new features and improving existing ones to make jotting down your daily thoughts a smooth and effective experience. With iOS 14, there are twelve such changes that we think you're going to want to know about.

Possibly the most popular feature in iOS 14, home screen widgets are here to stay. Apple created a ton for its own apps, and third-party developers keep building ones for their own apps. But home screen widgets go beyond that since you can make a widget for practically anything you want, from a custom news feed to an inspirational picture of the day — and this is how you do it.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

If there's an iOS app you want to hide from your iPhone's home screen, there are a few built-in ways to do so in iOS 14, but there is a clever workaround you can use in older iOS versions. Plus, it also works in iOS 14 as a way to disguise app icons instead of just hiding them, so no app is what it seems.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.