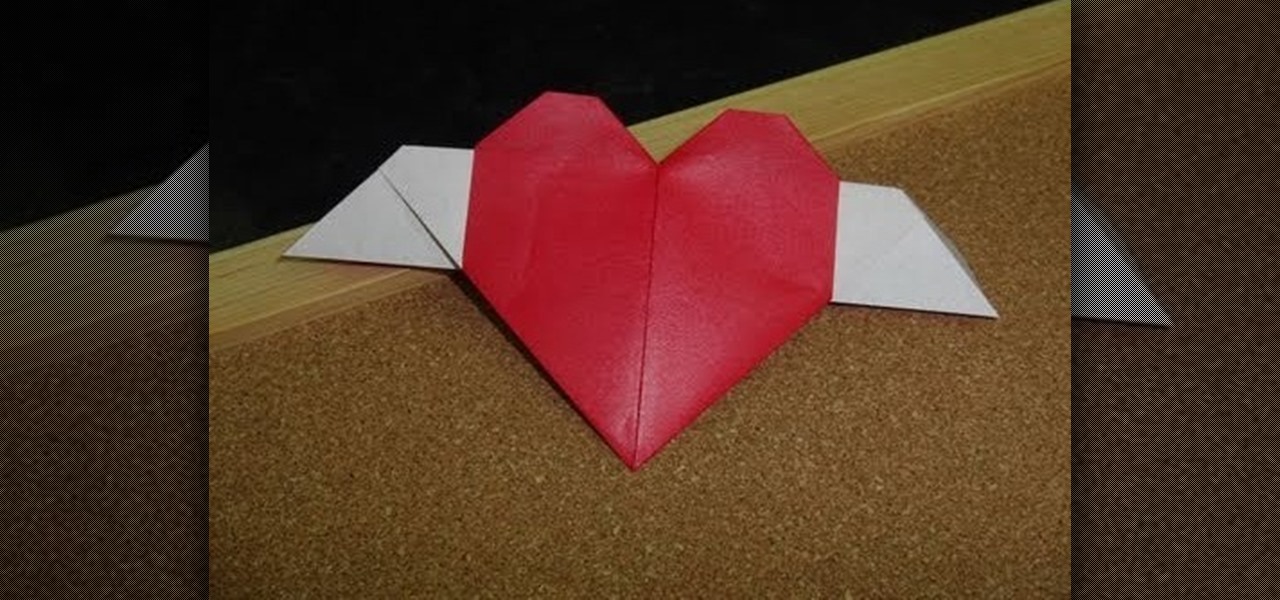
Show your amor that his love makes your spirits take flight by crafting this beautiful - and amazingly simple - Valentine's Day origami heart. Teeny white wings grow out from the sides to give it that Cupid charm.

Most people can barely be bothered to carry their wallets all the time, let alone a survival kit. When they're all dead from a massive natural disaster or terrorist attack, you'll know you were right to watch this video and prepare an every day carry (EDC) kit that ensure you will have the tools you need to survive with you at all times.

One day, you may find yourself in an emergency situation where you need to undo the chain lock of your home's front door, or somebody else's front door. Maybe someone forgot the unlock it when exiting the back door. Maybe you're grandfather is having a heart attack. Maybe your wife is cheating on you. Whatever the reason, it's fairly simple to break in by undoing the chain lock.

Becoming better at boffer combat is not a matter of mastering fancy sword moves, it's about being able to force an opening in your opponent's defenses and taking advantage of it without leaving yourself open for a counter-attack. This tutorial shows you precisely how to create these situations and take the most advantage of them.

In this video we learn how to make a big pink heart out of balloons. Start out with one side being a cuboctahedron. If you don't know how to make this, try checking out previous videos to make the shape. Once you have done this, you will use another balloon to connect and make the inside of the heart shape. Throughout the shape you will need to twist several bubbles inside the balloon, so make sure there is enough room left to do this. After you're finished, you will have a cute heart shaped ...

In this video, we learn how to make a sun catcher with your kids. First, you need laminating paper, two paper hearts, and scissors. First, cut the center of one heart out by sticking your scissors in and making your way around the heart. Next, place the outline of the heart inside of the laminating pouch, then decorate the inside of it how you prefer. You can use whatever you want to decorate the inside, including: glitter, crayon shavings, tissue paper, etc. Next, place the paper inside of a...

Nothing says 'I Love You' more than a gift that was made from scratch. Especially if that gift is shaped like a heart and is made from wood.

Drugstore valentines? Pssh, why would you want to get the same cards every other kid is passing around on Valentine's Day when you can make your own?

This video shows the method to style a heart shaped hair on a little girl. In the first step, do a zigzag part on the hair and pulling the sides to a pigtail. Part the hair till the ear before tying the pigtail. Wet the pigtails and put some pomade on it to make the pigtail stiff. Take a pigtail and divide it into half. Make sure that they are stiff. Twist the two parts of the pigtail and make a heart shape. Now clip the hair at the base using a pigtail holder. Repeat this process for the oth...

To fold an origami mandala heart you need to follow the steps below. First cut 2 triangles out of the paper you have, fold one of the triangles in half. Then, unfold the folded in half triangle and fold the top of the triangle down about two thirds of the paper. In this stage you will be making folds 3 and 4. Next, fold both of the side corners of the paper up to the top, creating the picture below. Now you will make folds 5 and 6. Then, turn the paper around. Now just fold the top flaps into...

Whether you're interested in trying out for the lacrosse team for your school or would like to brush up on basic positions and responsibilities, this video offers a great run through of the most basic elements of lacrosse. The four lacrosse positions will be covered: Midfielders, attack men, goalies, and defensemen.

This necklace is sure to get you noticed! This video shows you how to make a beautiful teal color faceted heart pendant on a knotted bead necklace. You will need waxed cord, glass beads, a heart pendant, a head pin, and scissors. Learn how to craft this necklace by watching this video jewelry-making tutorial.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

In this video from "Pour by Ian - Amante Coffee Boulder, CO" we see a quick and easy way to make a simple Latte Art heart atop the coffee drink. Unlike some videos that tend to be long (and tend to only show off) this video is direct, easy to follow and fun to try.

This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

Shaun of the Dead's Nick Frost faces an ornery alligator and learns a few useful tricks in the process.

Learn to perform a Jiu Jitsu Banana Split leg submission. This is a submission for grappling not self defense. It attacks the groin by pulling the muscles apart.

A pinch harmonic is an overtone. This video is a demonstration of how to play a pinch harmonic on the electric guitar with a right hand technique. Distortion, attack, vibrato, pick selection and more are discussed in relation to this topic.

Working with friends is always fun in Shank, but if one person doesn't really know the strategy that you need to employ to wine a boss battle, well, you can just forget it every going any better than bad. But don't worry, in this video, you and your friends can work to succeed against the Bouncer boss in Co-Op mode! You will just need to employ a simple tactic of waiting for him to use his stomp attack, and then lining up a timed trigger pull from both of you to start a double attack against ...

In this video Kiwua shows you how to make a heart bracelet. She recommends that you start braiding the wool yarn from left to right and then progress from right to left. In the middle she creates a heart shape from the wool yarn with the wool yarn extending in four rays from both sides of the heart. The same steps are repeated with a different color of string each time, braiding the yarn once again beginning from left to right and then proceeding to the right hand side and knitting over from ...

Dragon Age 2 is the latest fantasy RPG from the folks at Bioware, and if you're watching this video you've probably either just gotten it or are thinking about it. Check out the vid for a walkthrough of the prologue quest, Destruction of Lothering.

St. Valentine's Day is coming up soon in February, but do you have a special outfit planned for that special someone? Well, even if you don't have a valentine, this tattered heart black shirt will show the world you care. See how to make a tattered heart Valentine's Day T-shirt in this video from GiannyL.

This video shows the method to make a gift card holder with "Stampin' Up." First, we use the Movers and Shapers to cut a heart shape on a paper. We use the add-ons cut by the Movers and Shapers to punch windows. Next, we use the Big Shot machine. Next, put a piece of Whisper White in the machine and cut at four and a quarter to eleven inches. Fold it into half and cut an inch and a half off the front top. Score the back panel at one and quarter inch. Take bags measuring 3 5/8 inch to 6 5/8 in...

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

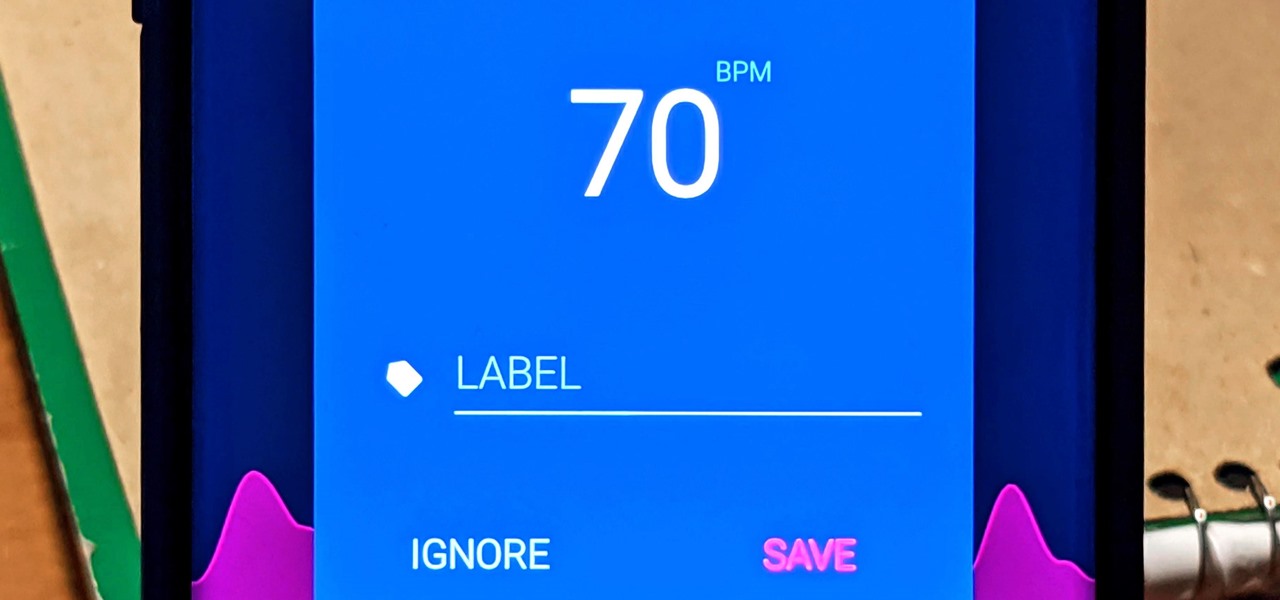
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.