
Enough with zoodles (zucchini noodles), spaghetti squash, and carrot 'pasta' spirals. A well-prepared dish of zoodles with sauce is beautiful and tasty, but let's get real, it doesn't fill you up. If you use it as a meal replacement, then you'll be hungry about 30 minutes later.

Unlike wine, you can't re-cork or stopper leftover bubbly after you've opened it, but all is not lost even if you haven't managed to finish every last drop. You can use your leftover champagne to make light-as-air crêpes or pancakes, to create a detox face mask, to cook seafood and rice, or to make dips and salad dressings.

It's that time of year again. The month after we exchange gifts, most of us tend to exchange germs. Cold and flu season always seems to creep up on us, often leaving us ill-prepared to deal with the ailments.

Somehow, we end up with a pile of leftover candy canes at the end of every December. Yet just because the enthusiastic holiday commercials are gone and the Christmas cards are on discount doesn't mean you have to let the minty sweets go to waste.
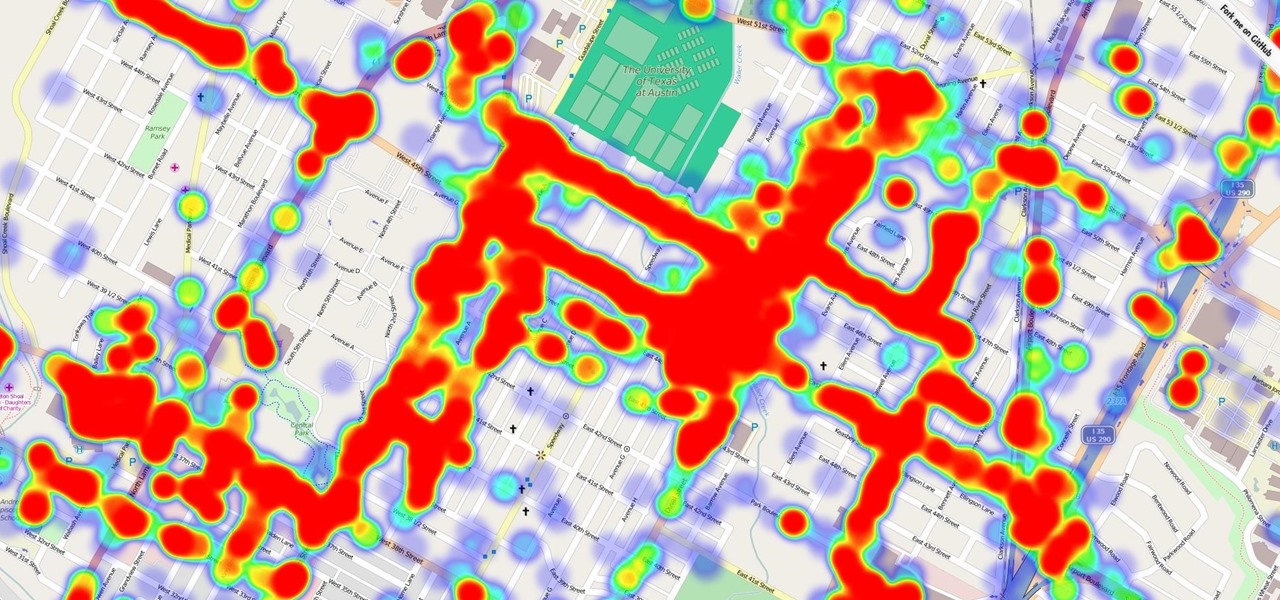
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

The noodle is a noble thing. And while I love ramen and pasta, I have a real soft spot in my heart for macaroni salad (especially the kind that comes with Hawaiian plate lunch) and the type of pasta salad that's dished up during picnics and barbecues.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

Butter can be even more delicious than it already is. While that may be a shocking claim, it's most definitely true. Many new cooks and even seasoned chefs don't realize this, but the few minutes it takes to do these things will pay you back exponentially when it comes to that buttery taste.

Video: . Dent Repair - Using a Stud Welder Gun

Instinctively, we reach for popsicles and cold drinks when the temperatures climb, but doing something counterintuitive, like going for a hot drink or eating something spicy, is actually more effective at keeping you cool.

There are plenty of times when we need to charge our phones but don't have access to electricity. Whether the power is out do to storms, you're camping and run out of juice, or you're in a Tom-Hanks-like Castaway situation, it's important to have a charged phone in case of an emergency.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

If you're breaking a sweat in the summer heat, but not trying to break the bank, this dead simple trick will show you how to make your own air conditioner for under ten bucks.

Sometimes, ceiling fans just don't cut it. They spin meekly, barely generating any air flow to cool down your sweltering room. Or, when turned up high, they can wobble wildly, shaking and vibrating as if the ceiling is about to come crashing down. If this sounds like your ceiling fan, chances are the solution is a simple as flipping a switch.

French fries, like mashed or roast potatoes, are the type O blood of the food world—they're compatible with just about everybody. That's why it's so sad to bring home leftover frites (that's French for French fries) and have to toss them out the next day because they don't taste as good when they're reheated. Warning: Do Not Ever, Ever Use Your Microwave

Hopefully you never have to deal with a grease fire, but if it happens, how you handle it is important. A grease fire isn't like a regular fire, and trying to put it out the same way can make it worse. Grease fires are caused by letting oil get too hot, so the best way to prevent them is to never leave your kitchen unattended. Oil smokes before it burns, so if you see your pan start to smoke, take it off the heat before it has a chance to catch fire. If you're outside grilling, you can add a ...

Mouth burning with pain from eating too much hot sauce or some seriously "spicy" food? Well, ignore your first instinct and steer clear of that cup of cold water — it won't help. Instead, reach for a glass of milk, a lemon slice, a spoonful of sugar, or some starchy bread to dilute the painful heat on your tongue.

You have warm toast, but your butter is chilled to a rock-solid state. Sure, you could warm a bit of that butter up in a microwave before spreading, but chances are you're just as impatient as the rest of us, so you slap that frigid butter on and hope for the best. It always ends up the same, though.

We all have our favorite cooking oils, but not everyone knows that they're not all interchangeable. Each type of oil is best for certain jobs, and they all have different smoke points and flavor profiles, which are the two most important criteria in determining which one to use.

I know Americans love to hate on the French, but from my standpoint, they've given us a lot of things we should all be thankful for, like French kissing, casual sex, Pepé le Pew, and of course, French fries. Well, maybe not...

Everyone enjoys summers more than I do. At least, that's how it seems. While I take pleasure in the decline of clothing covering up my lady friends, I could definitely pass on the heat and absurd air conditioning costs. However, one summer staple that balls above all else is cooking on the grill.

Wet shoes are uncomfortable, no one can deny that. Just think about walking around with soaking wet footwear ... and each squishy step you take. Makes you cringe, doesn't it? It can happen in heavy rain, at the beach, or from an unforeseen puddle on the street. And while you can't always avoid soggy shoes, you can rest easy knowing that the next time this happens to you, you know the secret trick to drying your shoes faster without damaging them with excessive heat.

I hate being cold. That's why I live in Los Angeles. But, there are plenty of folks who are experiencing some pretty chilly temperatures this year, despite global warming, and one of the worst places affected is the garage. C'mon, who has a freakin' heater in their garage?

Here's a survival technique for making a fire with the most basic of resources—assuming you can find two sticks to rub together!

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

If you have children, then you know firsthand how many crayons parents end up buying. There is no such thing as using a crayon until it disappears. Kids use crayons until they are a nub, and then they toss the crayon aside, never to use it again.

Jennifer Pompa suggests that the 20" easiXtend Elite is the extension to start with. It's an 8 piece extension made with human hair that's not been too processed and so looks very natural. Jennifer is wearing a Kim Kardashian look with flowing curls. The extensions can be purchased as Extensions. Blow dryer, flat iron or curling can be done to these extensions because it's real hair. The extensions come in many colors but also can be dyed to match your hair. To remove them, Jennifer unclips t...

There are three main types of exfoliates : the mechanical ones with the little scrubby beads; enzymatic ones made from the acids of fruits such as pineapple or papaya; and AHA’s (Alpha-hydroxy Acids).

This video is about how to get rid of pimples. It's a nightmare to wake up and discover a big, red pimple right on your face. Here are some tips to help you out. 1. Do not touch, or try to squeeze or pop the pimple. This can cause pain, redness, swelling, and even infection. If you keep doing it another possible problem that can develop is scarring which can be permanent. 2. Wash your face gently with a mild, medicated soap and water (the water should be warm, but not too hot). Do this for 30...

This video demonstrates a method of fixing the E 74 Xbox 360 error. In order to do this, you first must disassemble your XBox, which will void your warranty, so this is at your own risk.

This android can talk, listen,and, with some tuning with a voice recognizer software, it will open and close many different applications.

Every good illustrator knows the advantage of using a Wacom tablet with Adobe Illustrator. When you plug in a Wacom tablet it doesn't automatically set your tools to be pressure sensitive. Terry White will show you how to set your brushes to really take advantage of your new tablet.

Once you've reached an age where sparklers are no longer fun, it's time to upgrade to science and steel wool. It may be basic chemistry, but as you'll see in the video, simplicity can amaze more than complexity, as well as create some really impressive fireworks that are perfect for the Fourth of July.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.









































