Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

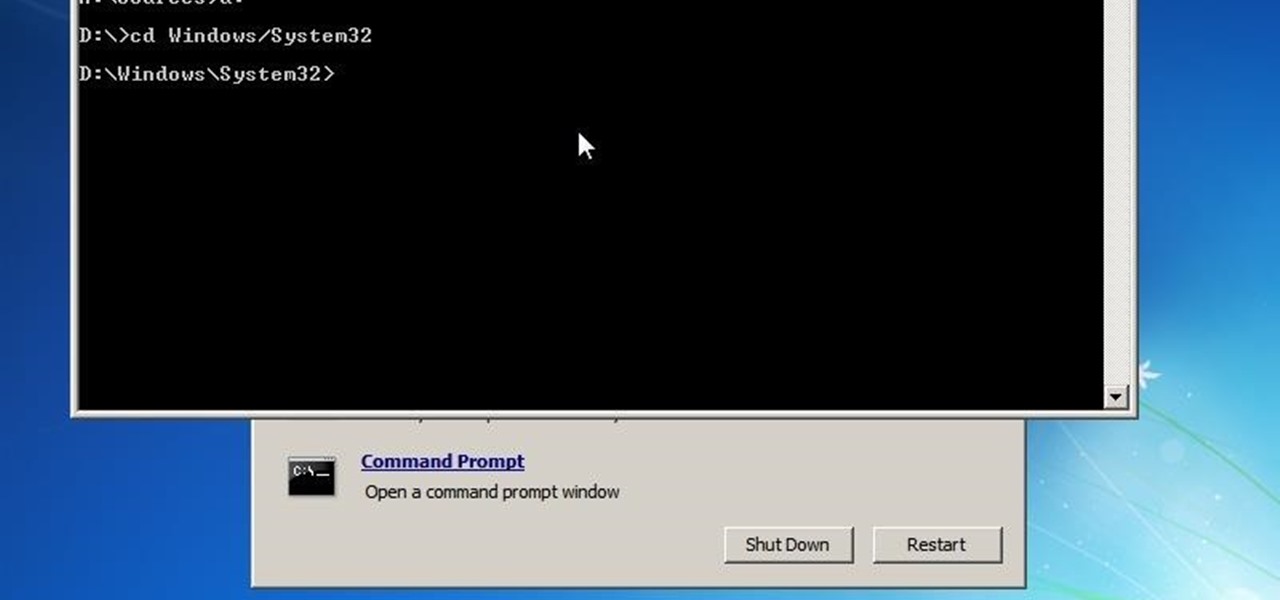
Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

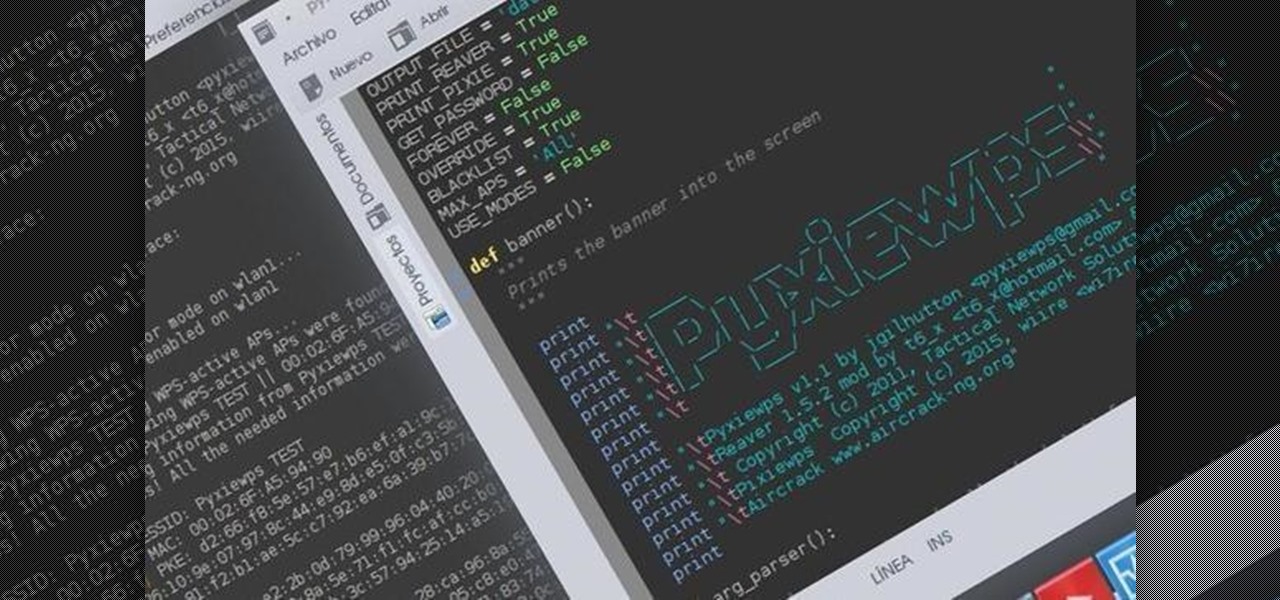
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

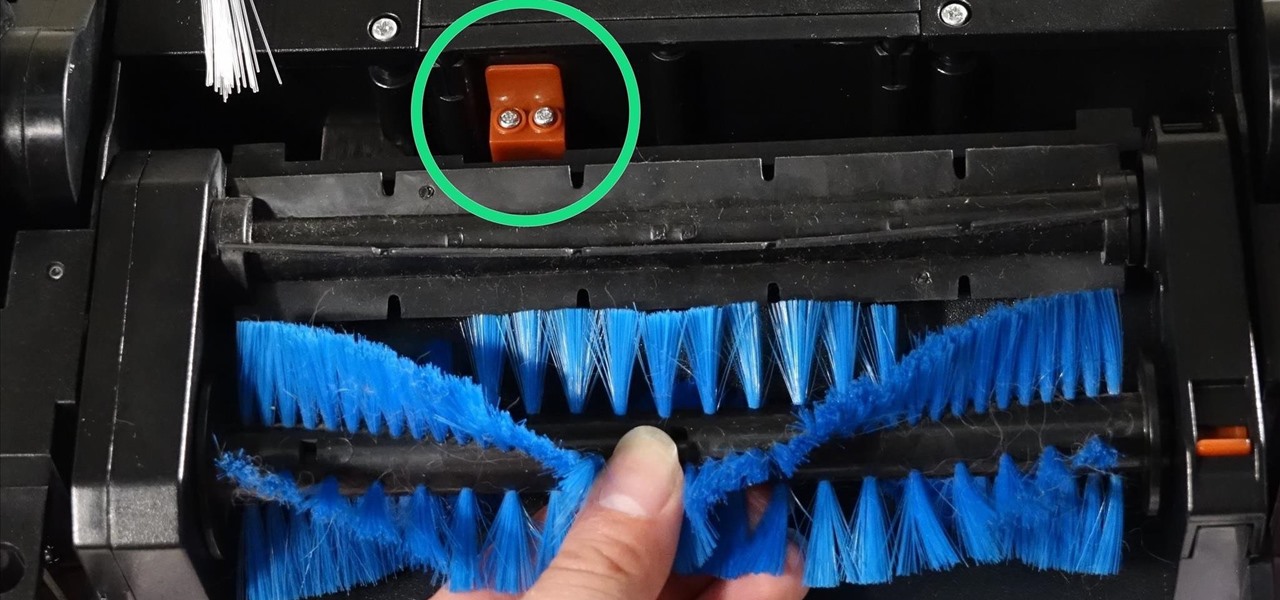
One of the quickest repairs for bObi is replacing the main brush motor. To do this, you'll need a Phillips head screwdriver and a replacement main brush motor.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud song may jolt you awake in the middle of the night. With an iPhone, however, that issue can be avoided with a little setup.

The weather outside might be frightful, but heating bills are downright scary this time of year. Heat is absolutely essential during the winter season, but it's also really expensive. If you aren't blessed with a fireplace or unlimited disposable income, fear not, because you can still heat your home on the cheap using flower pots and tea lights—even if the power goes out.

We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Both professional and home cooks have been rinsing raw chicken and turkey before cooking it for what seems like forever. It's one of those divisive practices—either you do it or you don't, and people tend to be rather opinionated on their stances.

When we take pictures with our smartphones, it’s safe to assume we’re taking more than one. We're either trying to capture the right light, look, or expression… or maybe a slight nod to the right to show off your good side.

Note to admins: If there's anything wrong with the links or the article itself (legality), let me know.

The thermal fuse in your dryer is a safety device designed to prevent the dryer from overheating. The fuse is heat sensitive and when the dryer becomes too hot it will blow. If the fuse has blown then the dryer will either stop working or there will be no heat when the drum is turning. A blown thermal fuse is simple to replace. With a few tools, a do it yourself warrior can save valuable money from being wasted on a service call. Here is a detailed set of instructions on how to replace a ther...

Video: . How To Use a Tampon

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

We don't generally think of medicine as being very relevant to Steampunk, but it was a big part of Victorian science fiction. Notable examples that you may be familiar with would be Frankenstein and The Strange Case of Dr. Jekyll and Mr. Hyde.

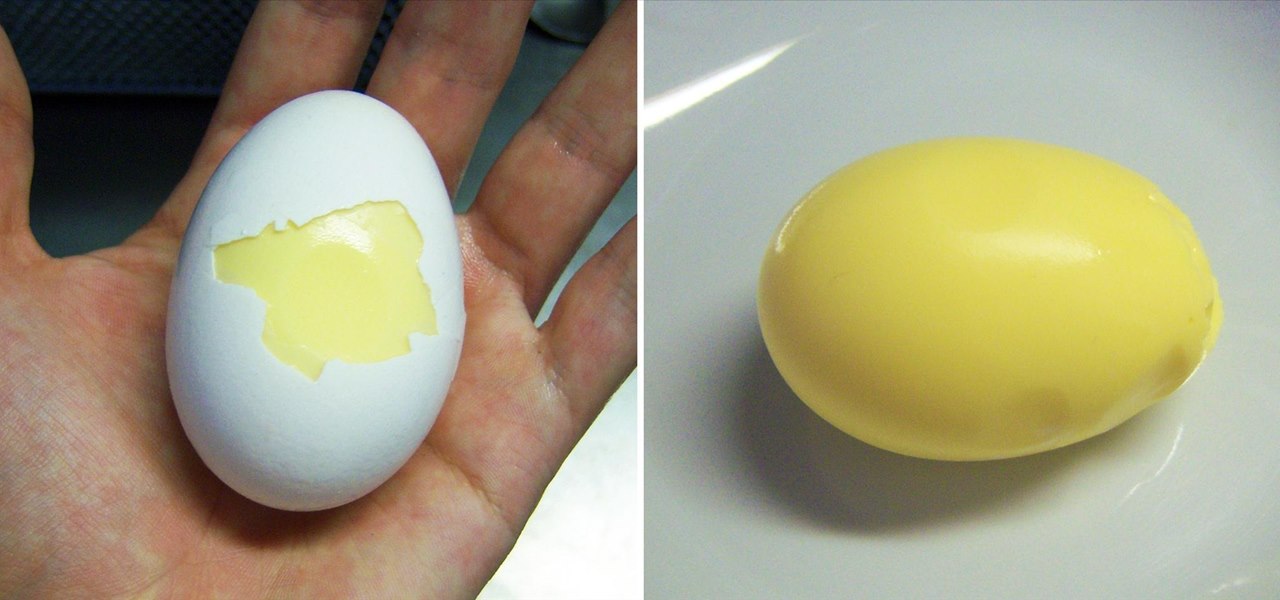
Eggs are one of the most versatile foods imaginable. They can be cooked in tons of different ways, eaten for breakfast, lunch, or dinner, and go with just about anything. Most of us have hard-boiled and scrambled eggs before, but have you ever thought about combining the two? That looks pretty good, doesn't it? But it's not exactly the kind of scrambled and hard-boiled eggs combo I'm referring to. And thankfully, this isn't what I'm talking about either... No, even though balut may look like ...

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

There are a number of different techniques for building underwater in Minecraft. The easiest is to fill a room with wood or leaves, then set them on fire. It'll burn down, leaving a pocket of air for you.

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars