Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.
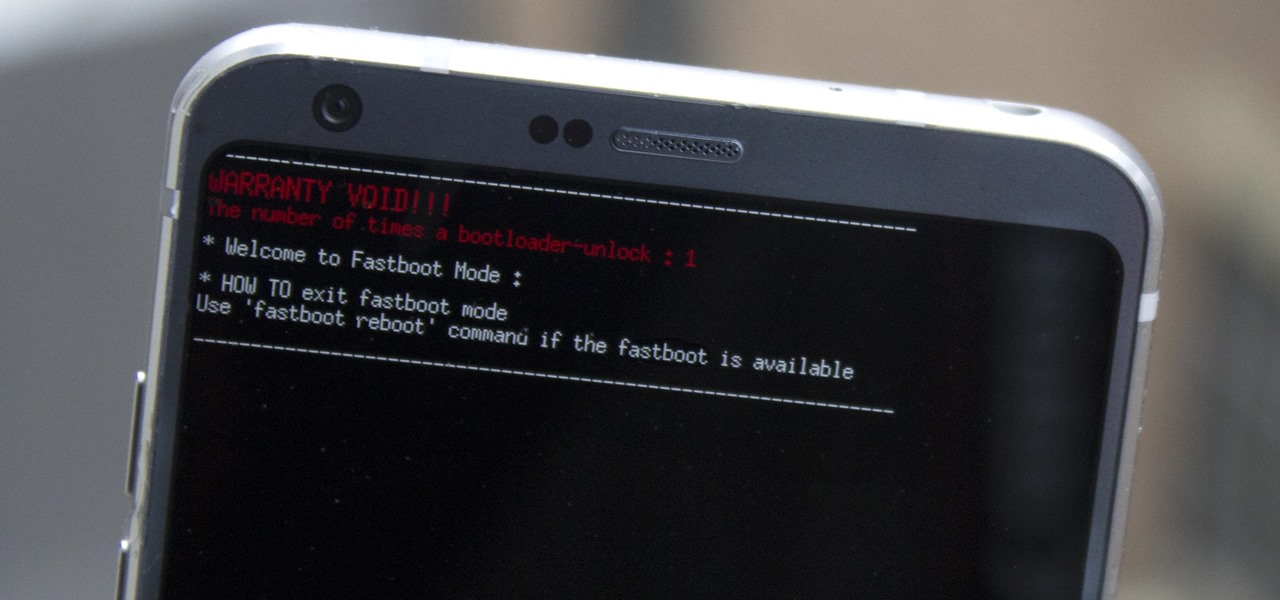
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

There are two types of bricks ("brick" as in "bricking your phone")—soft and hard. Soft bricks are recoverable—something has probably gone wrong with some critical system partition, causing a bootloop or inability to boot in some way. Fine. Re-flashing everything should fix that instantly. Hard bricks are not recoverable—if you manage to hard-brick your Nexus, you are in trouble.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Google released its long-awaited Google Now launcher a couple months ago, allowing users to access Google Now with the simple command of the voice. As great as the feature is, it requires that our screens be on, unlike the Moto X's "active listening" service that operates with Google Now, activating through a screen-off state.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.

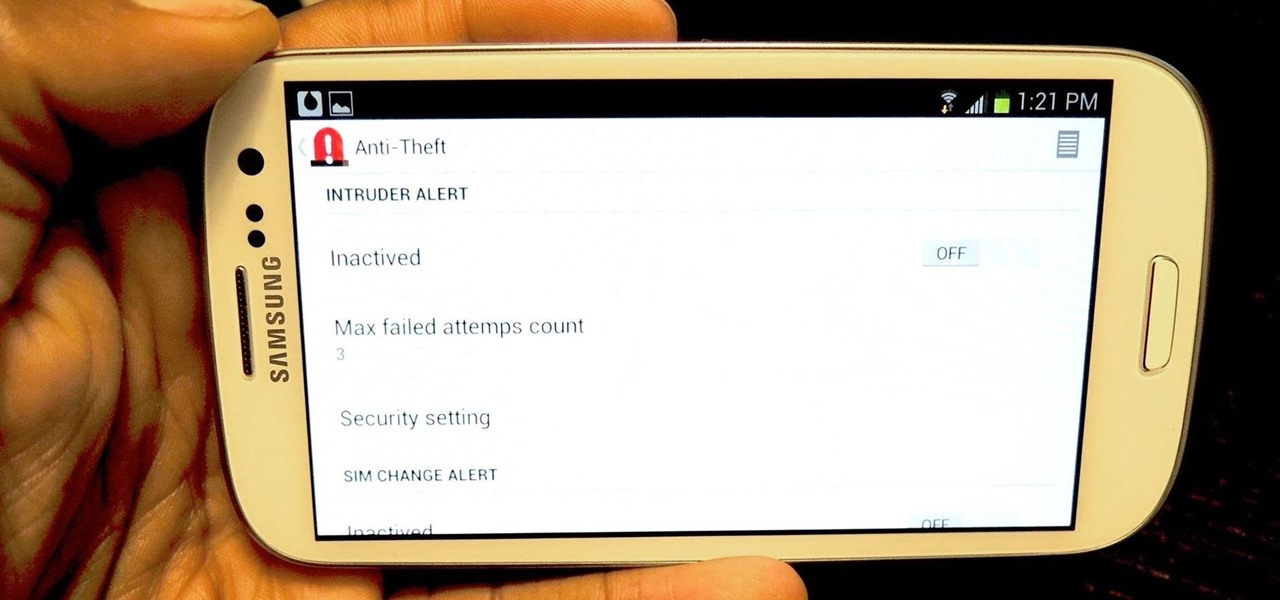
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Make voice commands on your myTouch 4G! This clip will teach you everything you'll need to know to use the myTouch 4G's Genius Button. Whether you're the proud owner of a T-Mobile myTouch 4G Google Android smartphone or are merely toying with the idea of picking one up sometime in the near future, you're sure to be well served by this brief, official video tutorial from the folks at T-Mobile. For complete instructions, watch the video!

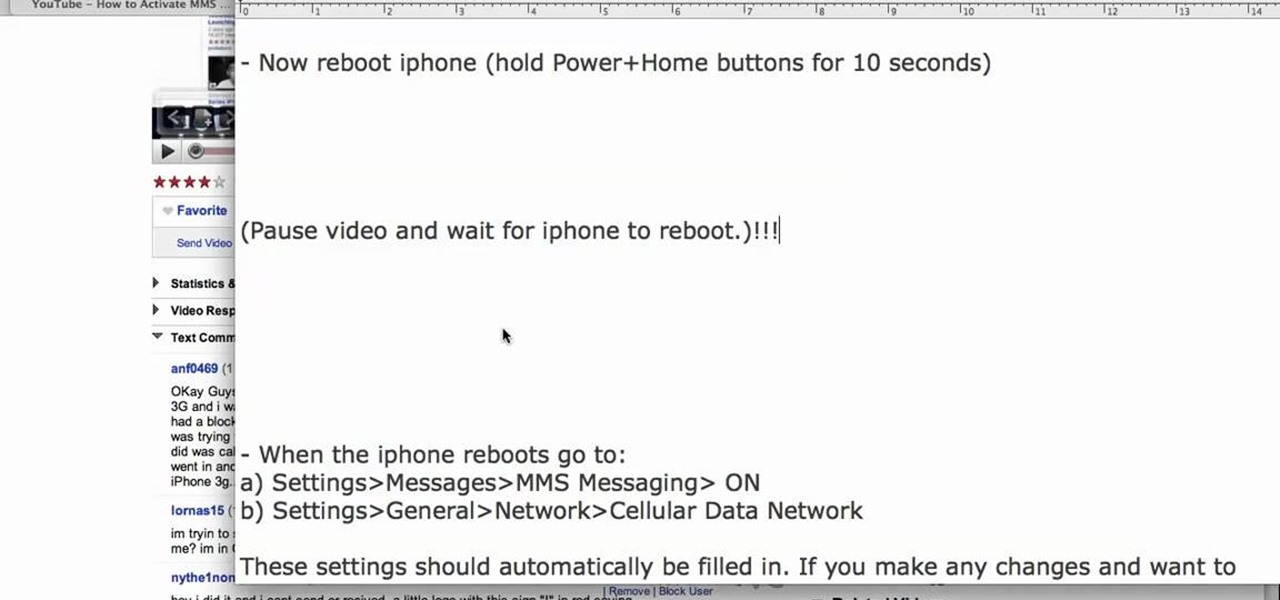
In this tutorial, we learn how to use MMS on T-mobile or ATT iPhone using 3.1 or lower. First, you need to make sure you have iTunes down and it's not running on your computer at all. After this, go to the start menu, then click on the run. Next, type in "command" and hit enter. Then, type or copy and paste "C:/Program Files/iTunes/iTunes.exe/setPreflnt carrier-testin 1" into the command console that comes up. Then, hit enter and reboot your iPhone. When this reboots, go to the settings menu,...

Shawn Powers teaches us how to install Truetype fonts on your Linux systems. First, log onto your web browser and go to Halloween Fonts. Once on this site, browse through the different types of fonts until you find one that you like. After this, save the file for the font onto your desktop. Now, install this font on your command line by first unzipping it. Go to the user share Truetype folder, then make a new custom folder. Move the file into the folder, then make sure the font and the folder...

This tutorial will show you how to hide files on your computer using an image file. The first step is to get an image file and edit it with Microsoft Paint or Adobe Photoshop. The next step is to save the image file as a jpeg file. Now create a WinRaR archive file and copy the files that you want to hide in the archive. The next step is to open Command Prompt: Click the Start button and click Run. Now enter "cmd" and hit enter. Now just enter the same commands from the video and hit Enter. Fo...

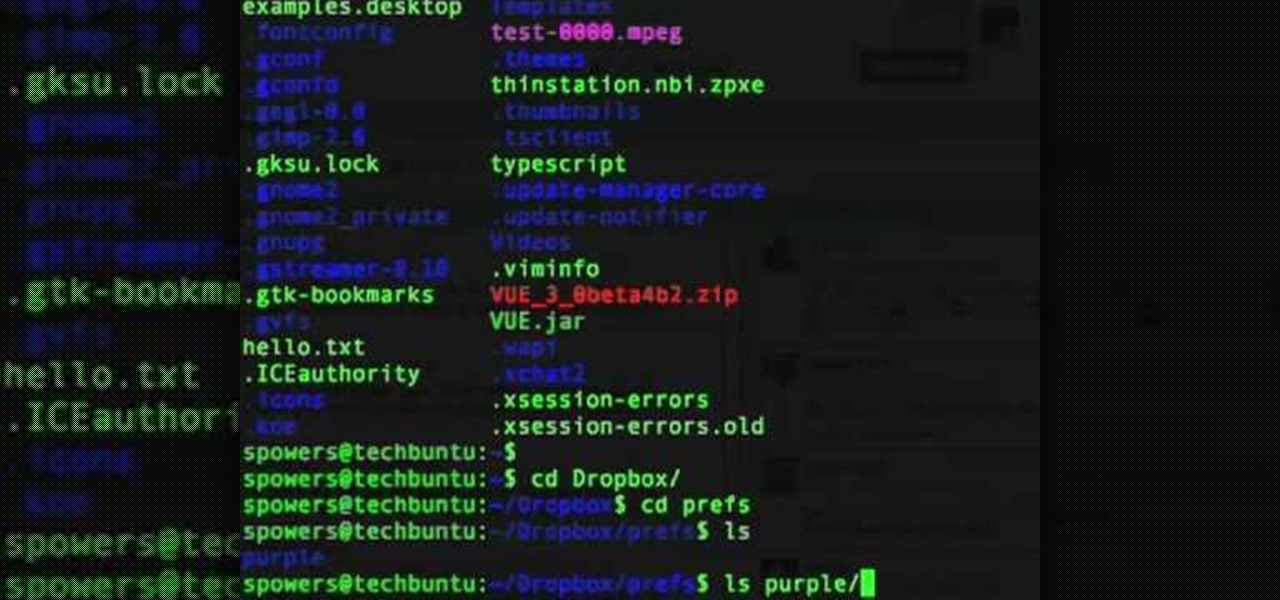
In this tutorial, we learn how to sync preferences with DropBox or Ubuntu one. This doesn't work for everything, but it will sync pigeon preference. It's a folder ".purple" and all the preferences are inside here. If you are familiar with using command prompts, then this will be very easy for you to do. Make a symbolic link from the command prompt to the drop box folder. On every folder, you will get the same result! This is very easy to do and just takes a few seconds to find, then you can c...

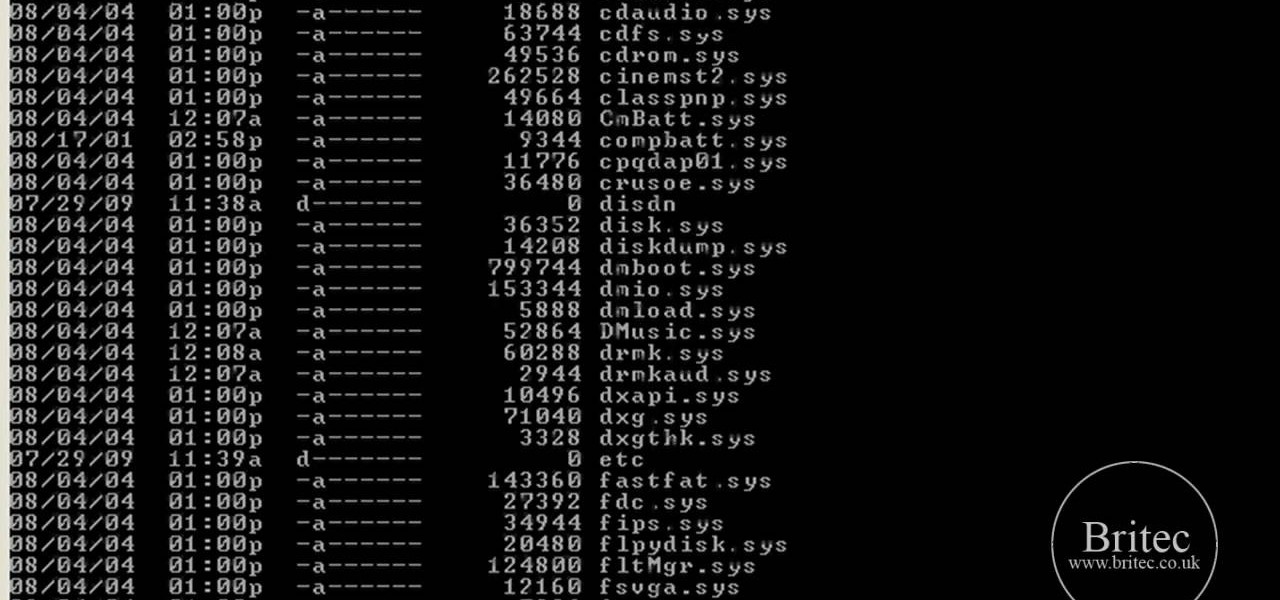
In this tutorial, learn how to fix a missing or corrupt error message "System32\Drivers\Ntfs.sys" Step 1:

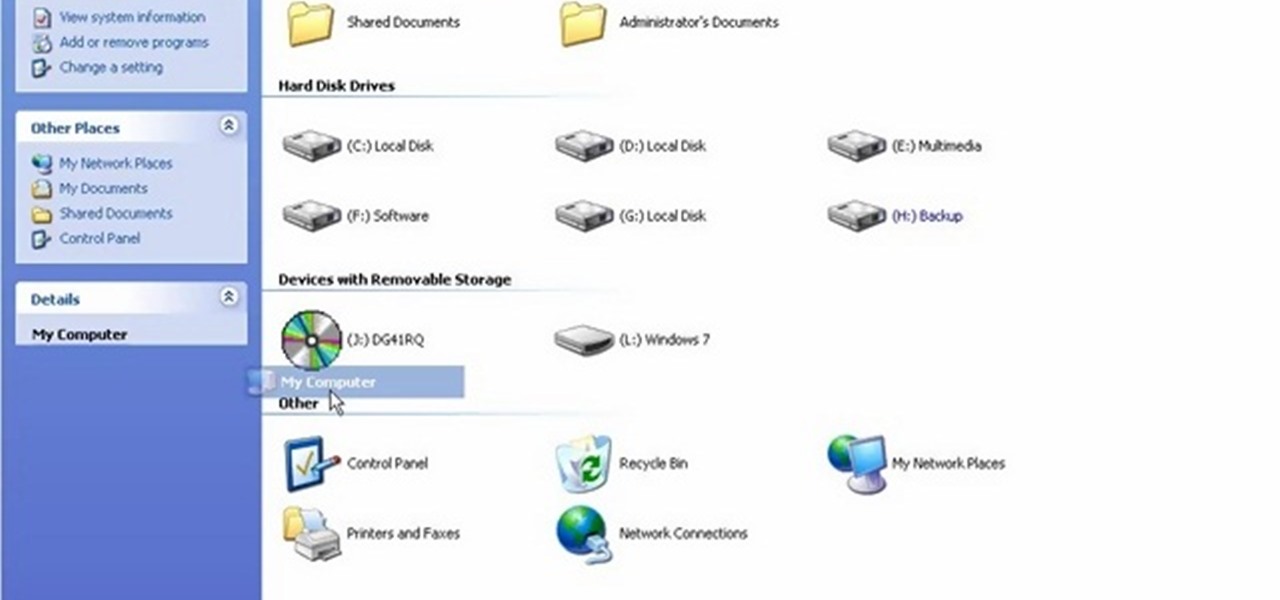
In order to install Windows 7 from a USB drive, while you are running XP, you will need a pen drive. You will also need a Windows 7 DVD and a pen driver.

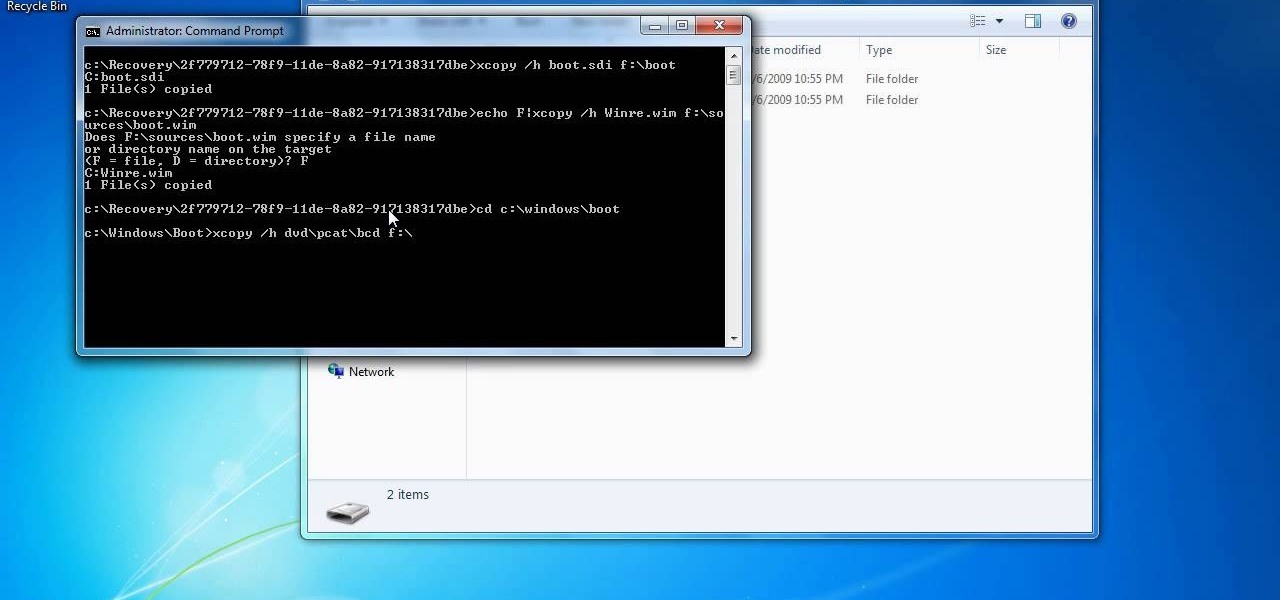
In this how to video, you will learn how to create a system repair disc on a bootable USB flash drive without having to burn a CD for your Windows 7 system. First, plug in your USB drive and create new folders in it. Name the first folder boot and the second sources. Next, open a command prompt and type in the cd c:\recovery, dir /a:sh, and so forth as shown. Once you have typed in the proper commands in the prompt, eject the flash drive. Restart the computer with the drive plugged in. Boot f...

In this Computers & Programming video tutorial you will learn how to remove ntde1ect.com & autorun.inf virus & trojan files. Go to my documents > tools > folder options > view and unhide the files and click OK. Open up the task manager. Under properties, click on explorer and end that process. Then look for wscript.exe, select it and minimize the task manager. Now open up command prompt and type in ‘dir’ against C drive. This will not list the hidden files. So, you type in ‘attrib –r ...

This video illustrates the method of using Facebook smileys. The process is composed of the following steps -Step 1While typing a wall post or a message in Facebook , click on the smiley button present in the top right corner of the text box where are typing your text.Step 2You will be presented with a drop down menu with the smileys that can be used in Facebook. Select anyone of them and insert them in your post by right clicking on it.Step 3You can add any number of smileys by following the...

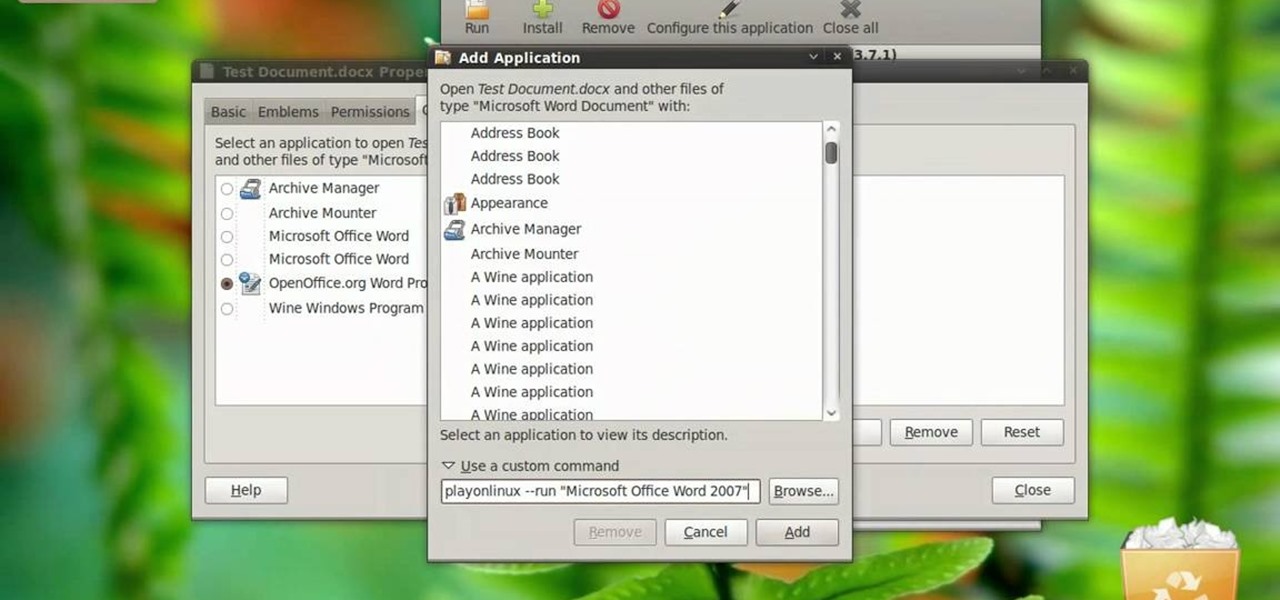
In this video tutorial, viewers learn how to open a Microsoft Word 2007 file by double-clicking it on Ubuntu 9.10. Begin by right-clicking on the file and go to Properties. Click on the Open With tab and select Use a custom command. Now type in [playonlinux --run "Microsoft Office Word 2007" and click Add. Select the custom command from the list and close the window. This video will benefit those viewers who use a Linux computer, and would like to learn how to open Microsoft Word 2007 files b...

In this video Guides4tech teaches the secrets of finding your local IP and MAC address in simple steps. First click 'Start' and select 'Run' on your computer. Now type 'cmd' to open the command prompt. In the command prompt type 'ipconfig/all' and press 'Enter'. Your IP address will displayed under the 'Ethernet adapter local area connection' menu. Your MAC address will be displayed as 'Physical address' under the same menu.

For anyone who has accidentally deleted a file, follow the steps in this tutorial to learn how to recover the file on Ubuntu. Learn what commands to type to run a search that will allow you to undelete a deleted file. This tutorial shows you letter by letter what command to type and in what format it should be typed to scan your hard drive for the deleted file. Once your search has found the file, the tutorial also shows how it can be recovered and then saved back onto your hard drive.