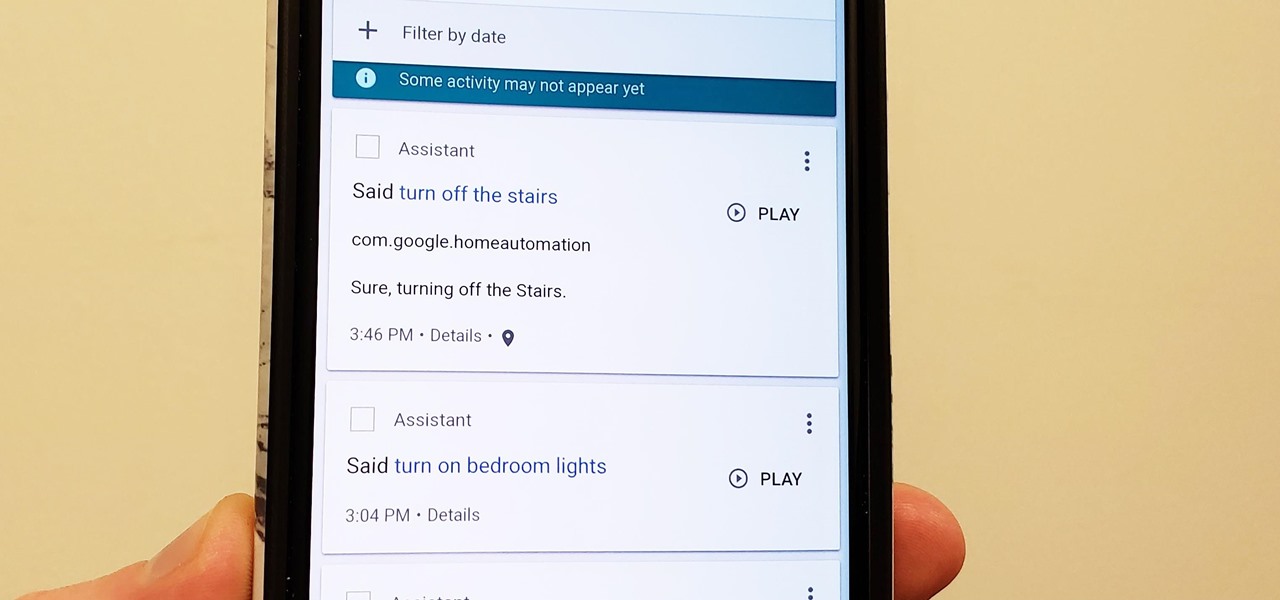
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.
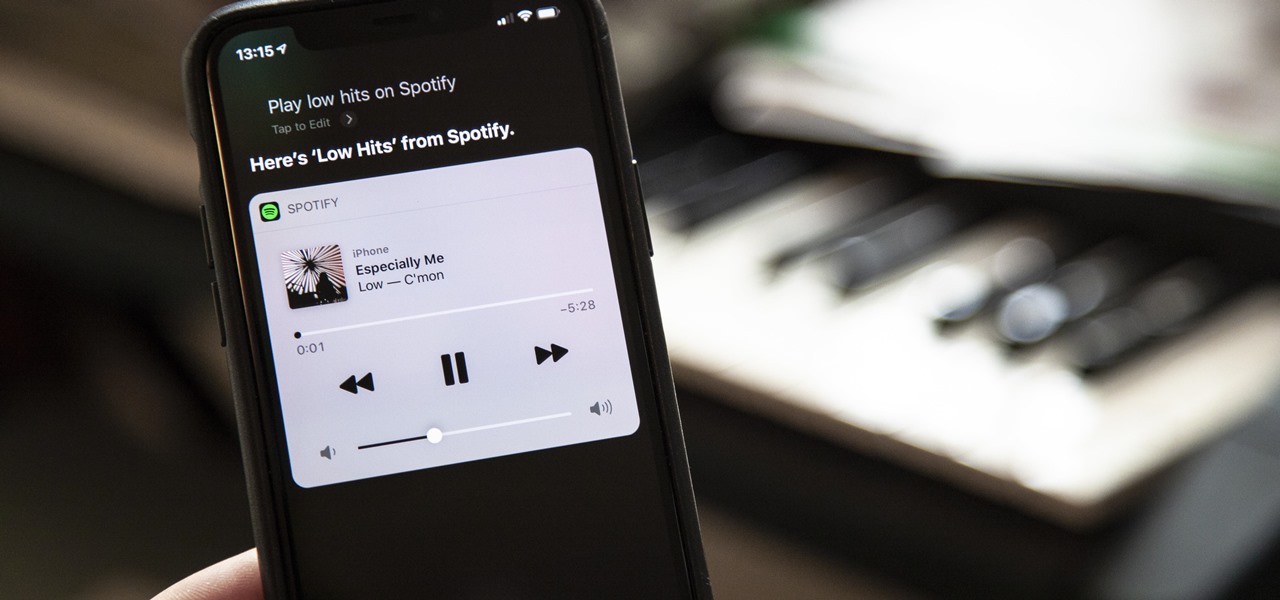
Finally, Spotify now works with Siri! It's been a long time coming, but as of Spotify Music version 8.5.6 for iOS 13, you can make Siri or Hey Siri on your iPhone play and control music in your Spotify account. But what commands can you use? We've built a list of everything you can tell Siri to do on Spotify right now, and as time goes on, the list may grow even more powerful.
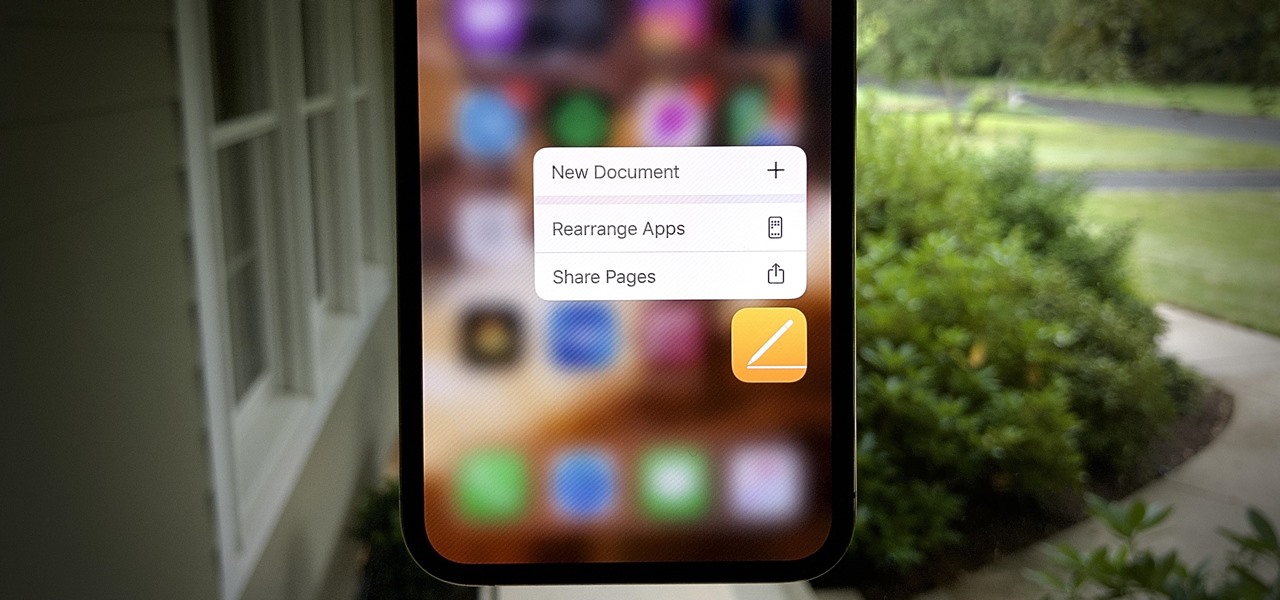
We're basically living in the future, so let's work like we are. For decades, we have, without question, opened a word processor like Pages, and clicked or tapped our way to starting a new document. What's wrong with that? It's unnecessary. We all have a digital assistant living in our iPhone, one that can start up a new Pages doc by verbal request.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

Since its introduction, the Bixby button has been a big point of contention among Galaxy fans. Many view the dedicated button as a wasted opportunity, which they argue could be put to better use if Samsung would let them use it for other commands. Thanks to an awesome app, you'll be able to remap the Bixby button on your Galaxy S9 to perform almost any function.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Whether you choose to hang an authentic or artificial pine Christmas wreath on your door — or an entirely different type, like ones made of paper waste or even food — chances are you've spent a year or two struggling with how to keep your decor hanging. With one easy to apply, quick to remove trick, you can skip the shiny wreath holder and any further damage to your front door.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

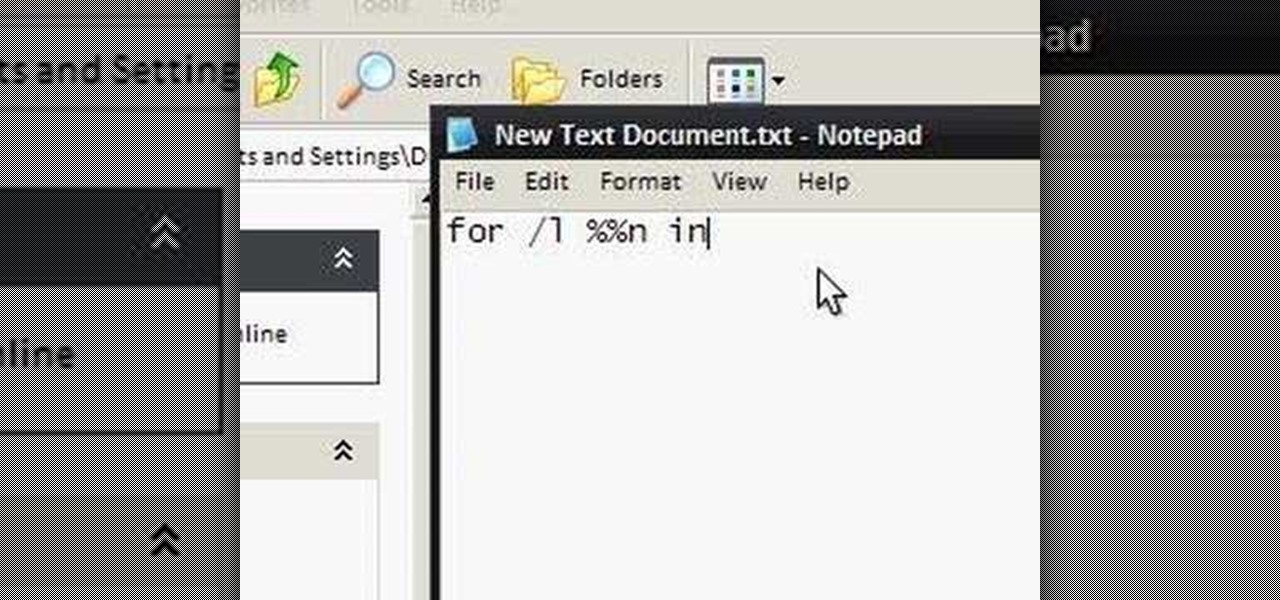
To make an annoying batch file to prank your friends you need to first right click on your screen and go to New and then Folder. In this New folder make a Text file and type in "for /l %%n in (1,1,10) DO md %%n" and that is it. Now this will loop from 1 - 10 and make a new folder for whatever n is. You can change the command if you would like to! Now, you can change this text file to 'Folder' and allow for this to be clicked. You can change the number "10" to any large number so the folder co...

This video demonstrates how easy it is to take a screenshot with shortcuts in Mac OS X. Pressing Command-Shift-3 will take a screenshot of the entire screen, while Command-Shift-4 will let you take a screenshot of just a selected area of the screen instead. For the latter, once you use the shortcut, your mouse pointer will turn into crosshairs, and you would click on one point of the screen, then drag and release your mouse to take a capture of the selected area.

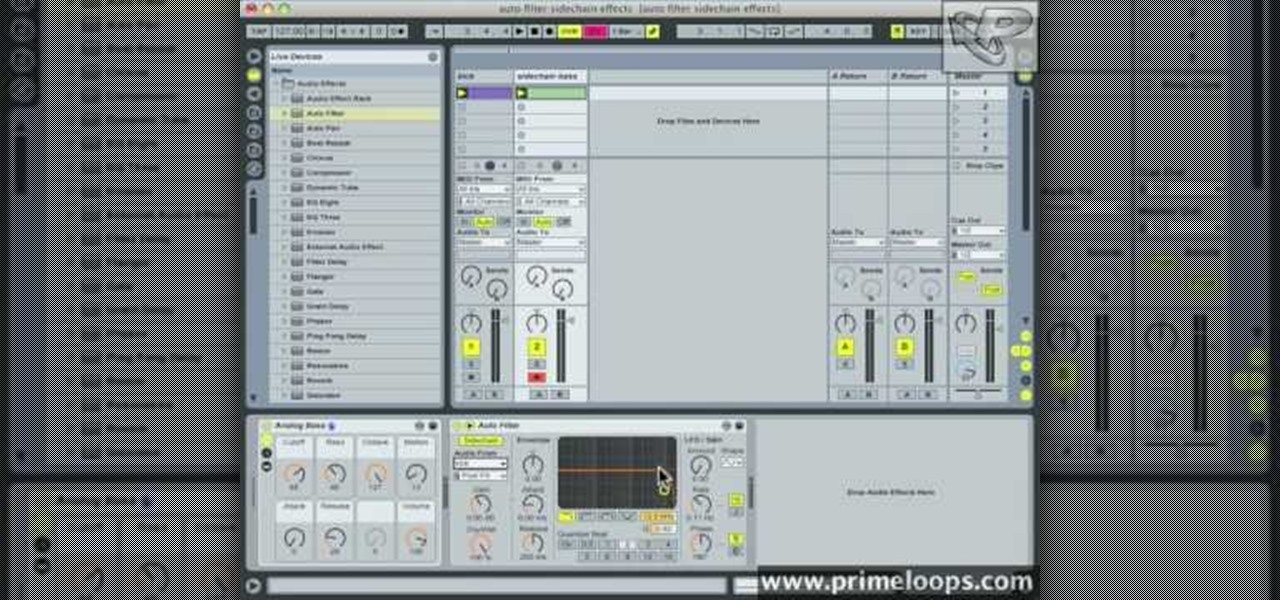
Open your program to a new live set. By using three keys (in Ableton Live), Command (Ctrl), Shift and t, you can create a short cut. Create two new midi tracks making one for (side chain) bass and one for (side chain) kick. To rename a track choose the two keys Command (Ctrl) and r. Next, you can load up the presets, located on the side bar list, one a bass, and, then a basic kick drum by opening up impulse, electronics and Tremor 1994. Now create a couple of patterns. To do this go an empty ...

Only those with supreme command of the force can properly wield a light saber. But anyone in Terraria can have a phase blade, if they know the crafting recipe. Watch this video to learn how to make a phase blade.

If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...

The yearly Victoria's Secret Fashion Show is a fashion show unlike any other. Rather than stick thin waifs floating down the runway with "I'm hungry" plastered all over their gaunt faces, Victoria's Secret showcases models with healthy, toned bodies who command the stage with their cheeky and flirty antics.

Want to get all of the possible cheats for your Sims 3 game? This tutorial shows you how to open the cheat box, and then what commands you can enter to get more money, happiness for your sims and move objects wherever you want.

Need to protect a section of your overall flash content (say movie or slideshow) from unauthorized access, learn how to do so in this video.

The primary purpose of hot keys in StarCraft 2: Wings of Liberty, is so that you can control the command card in the bottom-right portion of your screen, without using a computer mouse. But the hot keys have other uses, too. The first video covers the basics, and the second video covers using these shortcuts to building control groups. The third video shows you the other remaining hotkeys available for StarCraft 2.