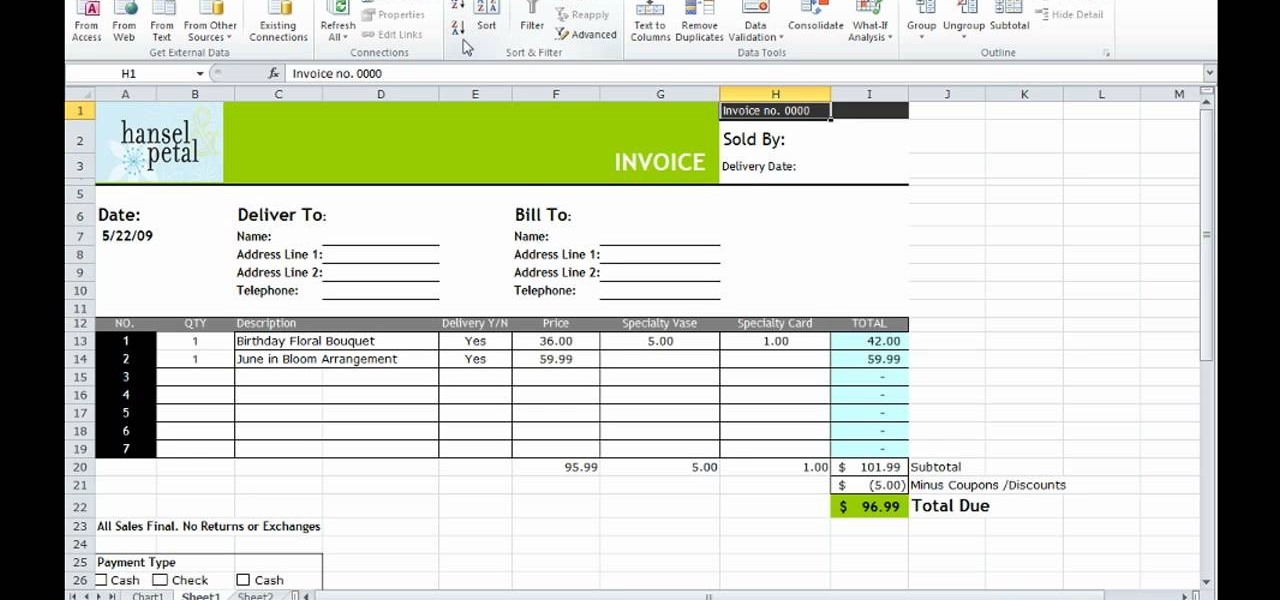
How To: Use the Ribbon and Backstage view in MS Excel 2010
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.


This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

Learn how to automate tasks in Windows using batch files. Learn basic commands that can be used in batch files and how to use commands from other programs to create batch files.
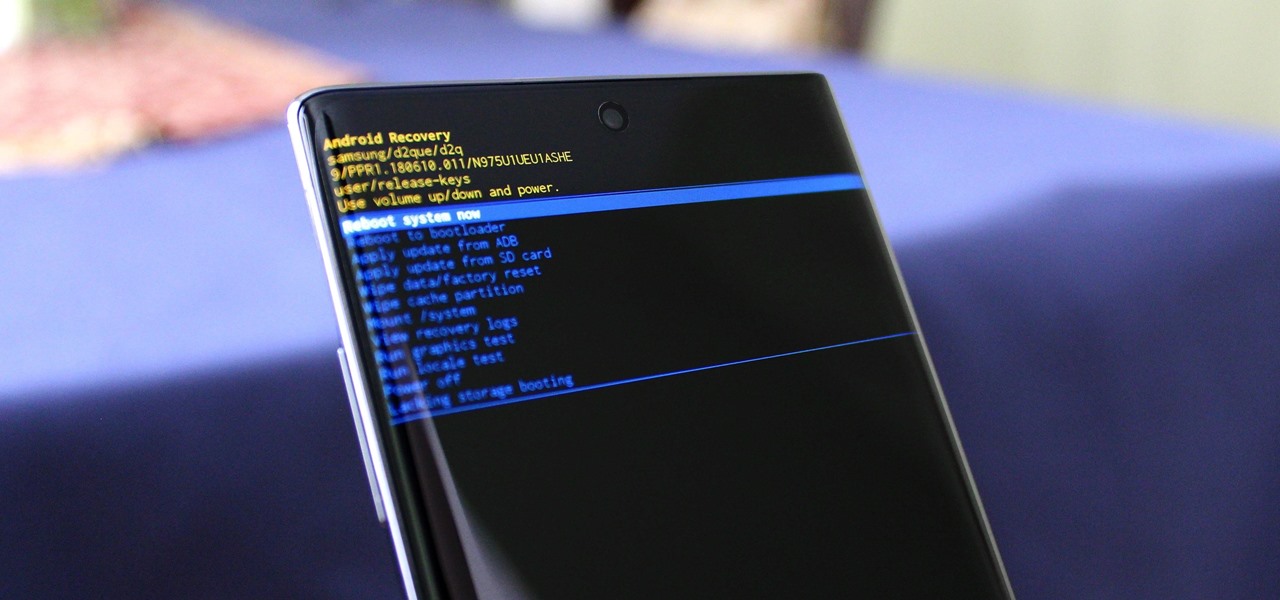
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.
Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...
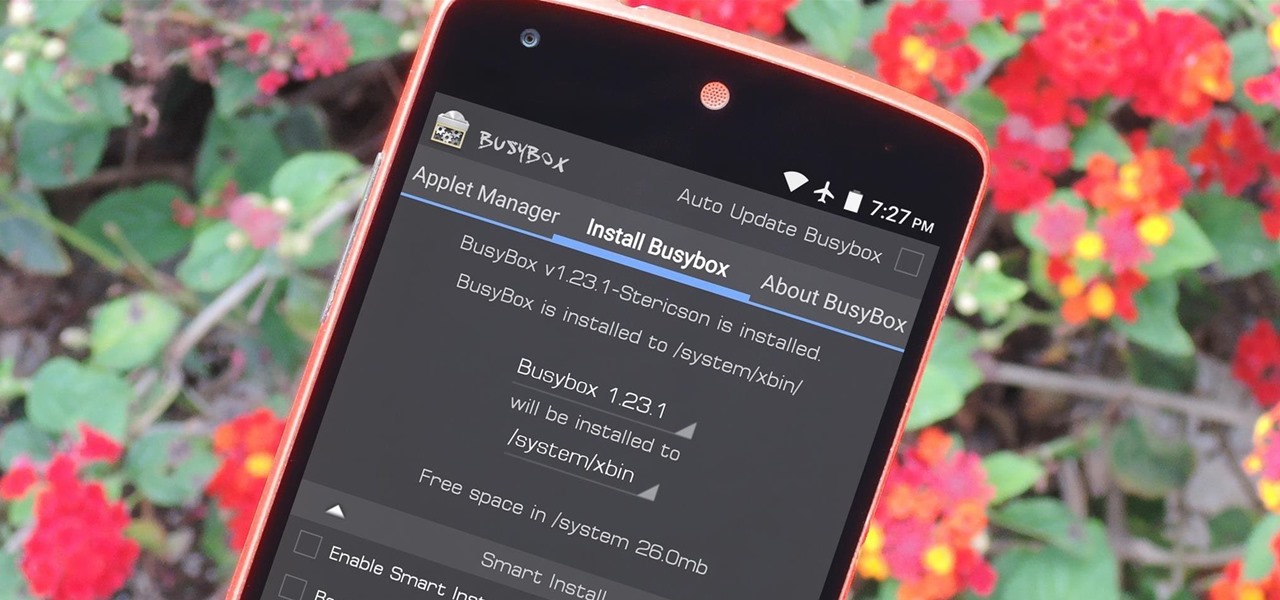
If you're a rooted user, you've probably heard the term "BusyBox" by now. Many mods require these powerful root commands, but the process of installing BusyBox can be a bit confusing for the uninitiated.
Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps.

Google Now is a wonderfully powerful service—with its predictive cards and voice search, it serves as a great starting point for any searches you need done. In fact, Samsung liked it so much that they decided to build the "Okay, Google" hotword detection right into the Galaxy S5's stock launcher.
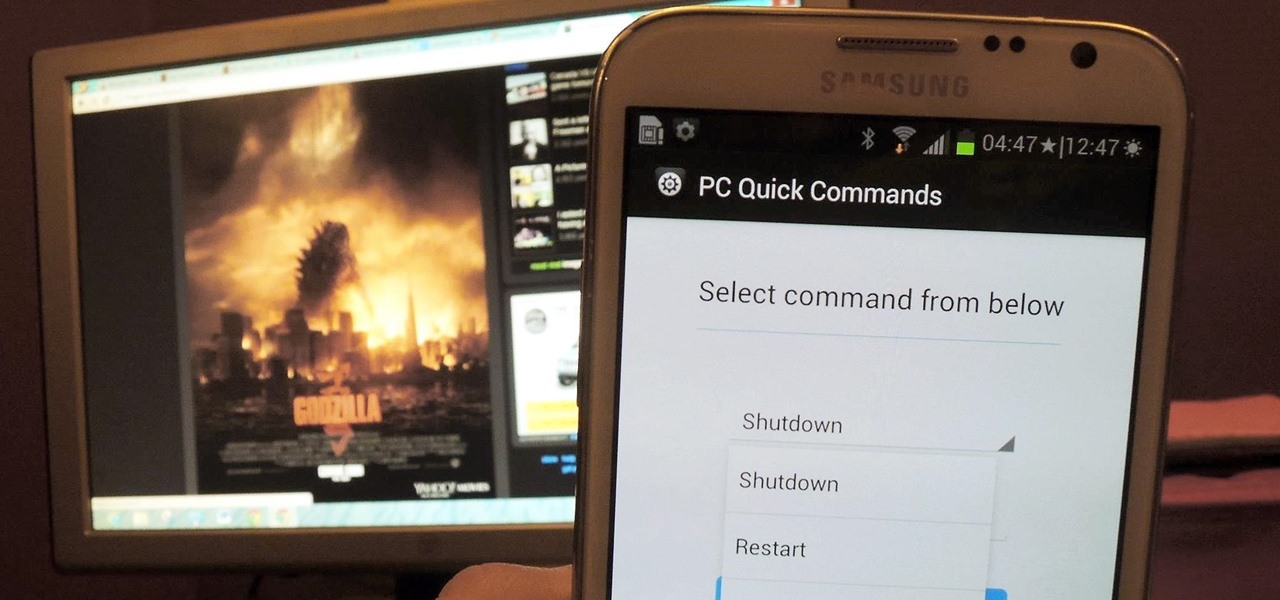
You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.
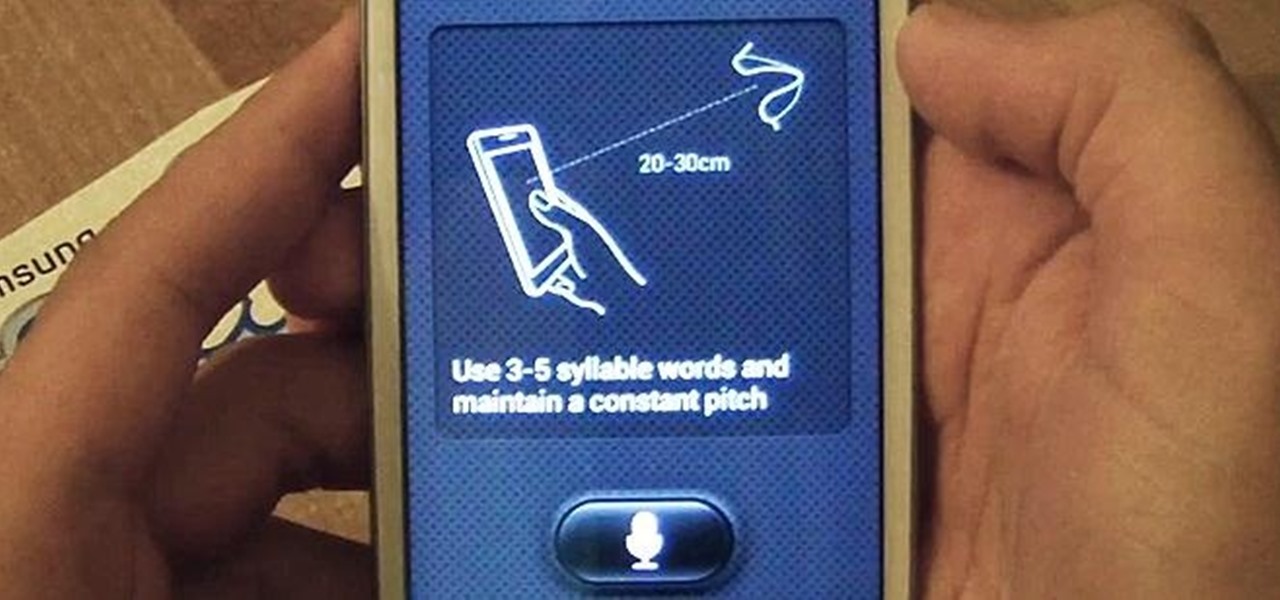
With voice commands becoming conventional on most new smartphones, it's only ideal that their abilities increase as well. Thanks to Apple's Siri, you can do things like update your Twitter account and look up who the president of Costa Rica is.
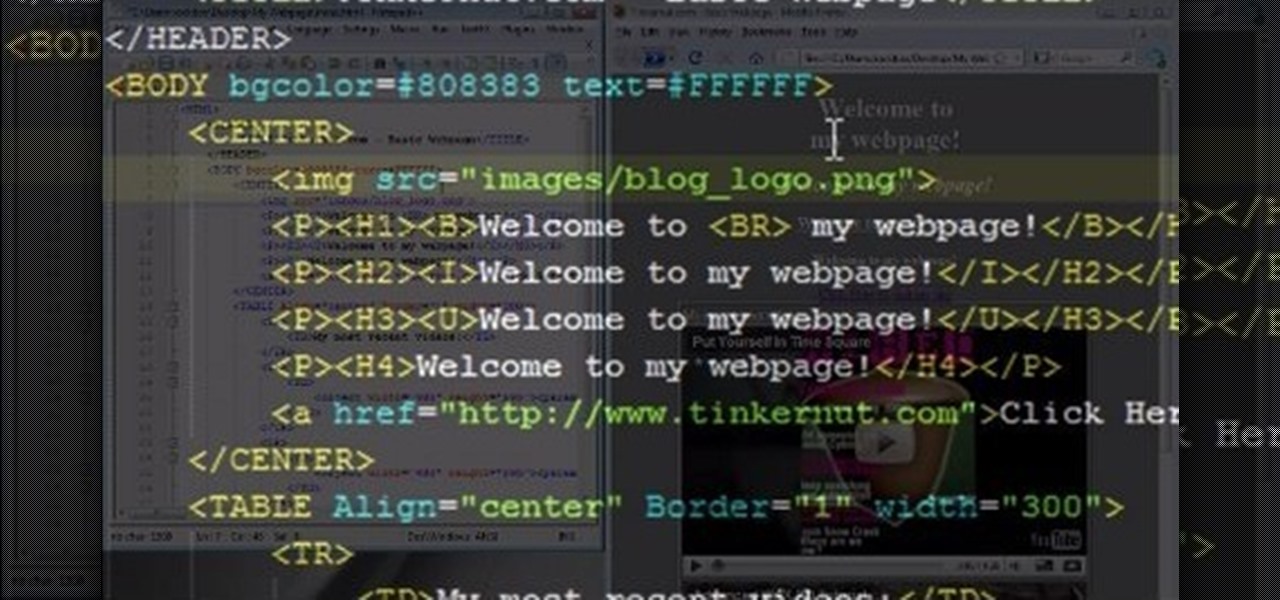
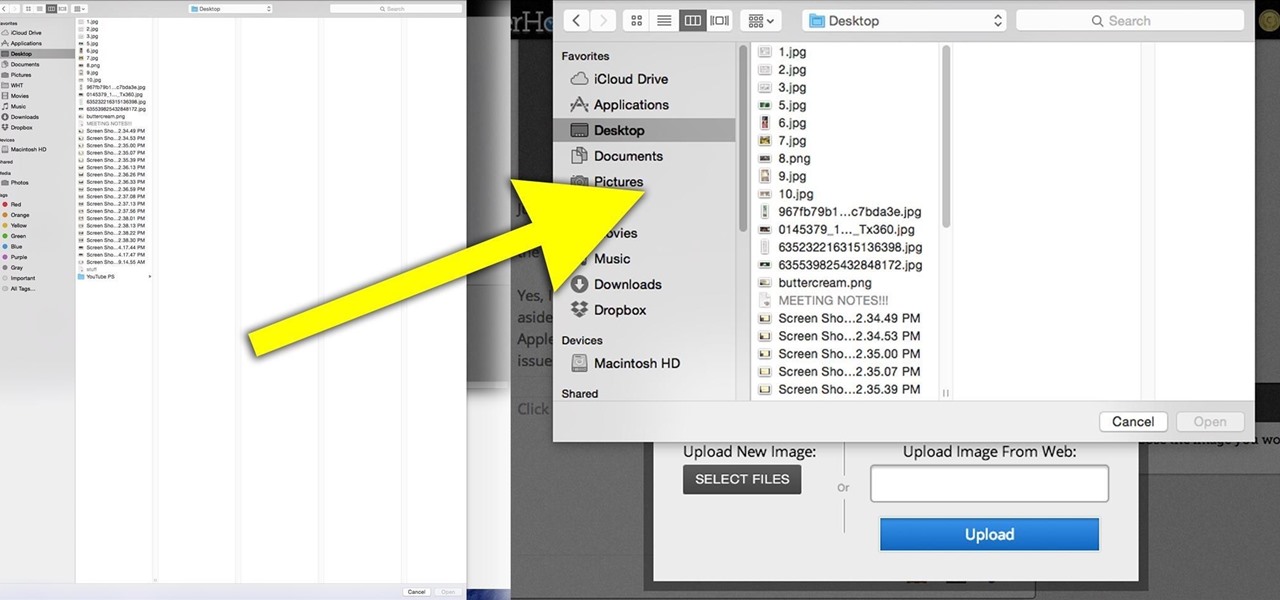
You can create a free website using HTML. HTML is hyper text mark up language. Create a folder "my webpage" with all of the images and information for the webpage. Use notepad to write the HTML for the website. Notepad plus is the best which can be found on Sourceforge. Open the browser and the notepad and begin to construct. These codes will help in the creation of the page: <html> opens instructions </html> closes instructions. These are called tags. One opens the commands or instructions a...

Soloing is something that every guitar player should learn. Being able to solo on command is crucial to being a great professional musician period! If you know all five of your patterns and are still just playing in the box patterns without much movement, then this video will help break you out of your cage! Dave Hill, a teacher at Musician's Institute, goes into great detail showing you how to use a technique called "Shape Shifting" by moving your lines through each of the patterns on the ne...
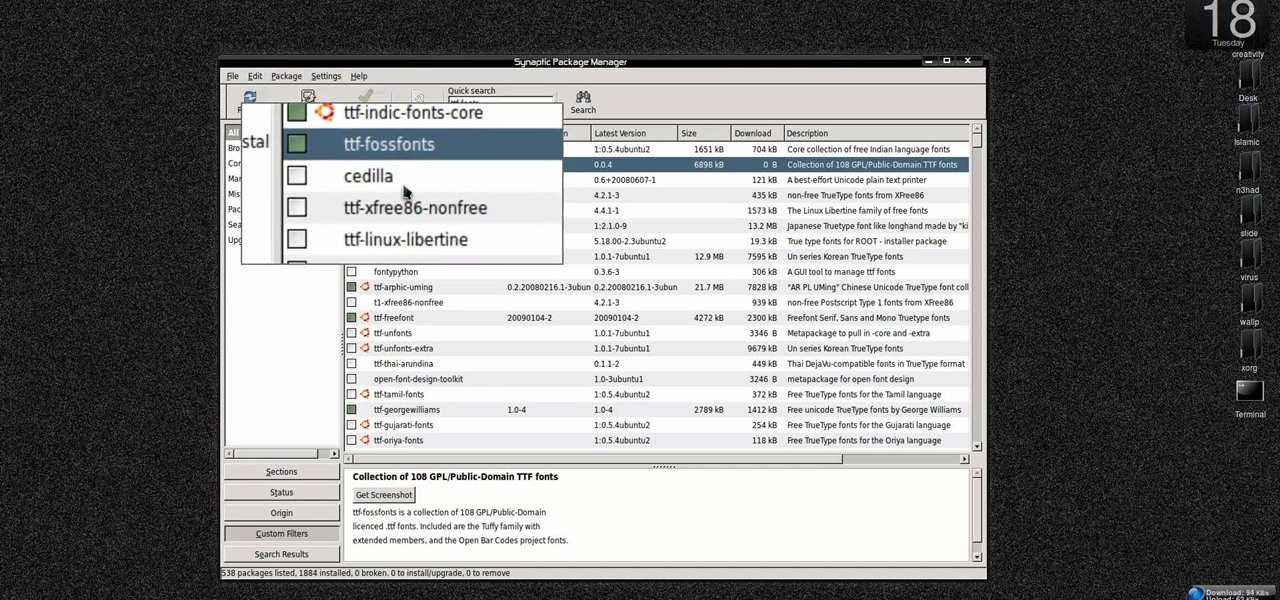
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.
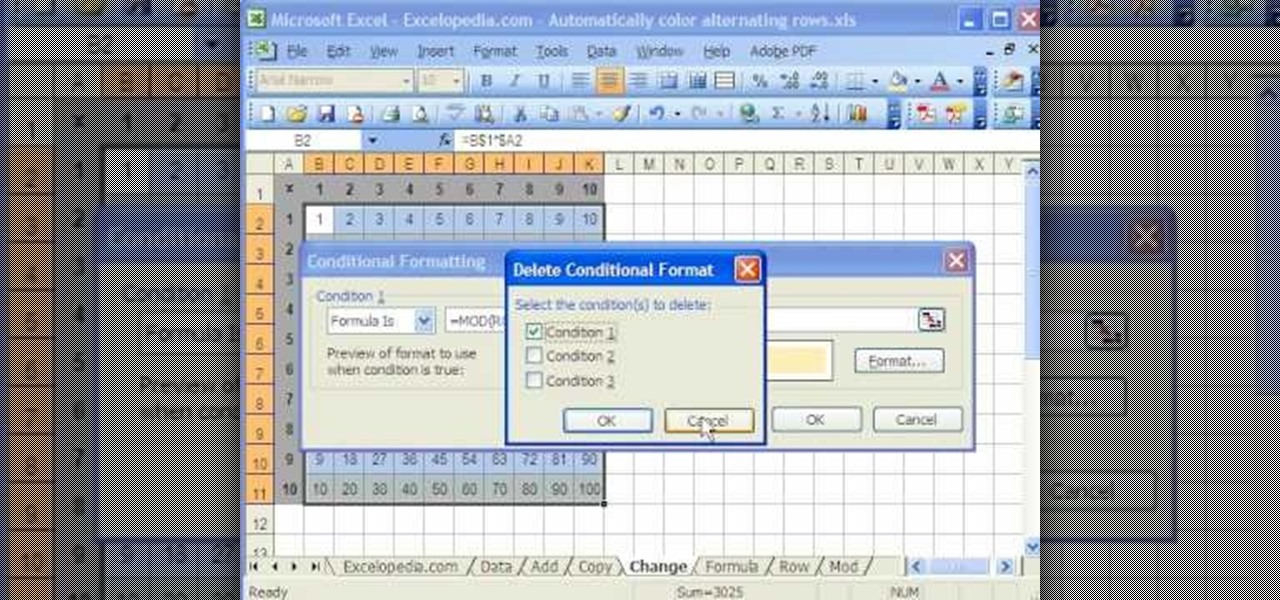
This video is a tutorial on using the Conditional Formatting function of Excel to automatically color alternating rows, which helps your eye to follow across the row. This can be done manually with the “Fill Color” button, but if you add or delete rows after applying the shading, the whole purpose is defeated.
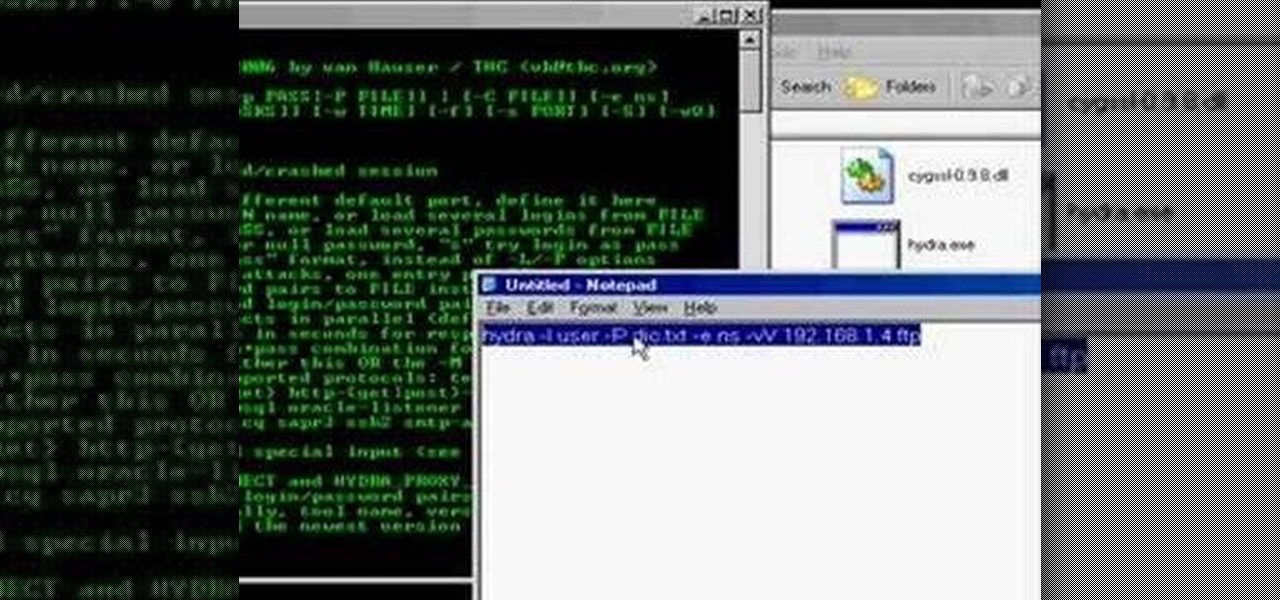
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.
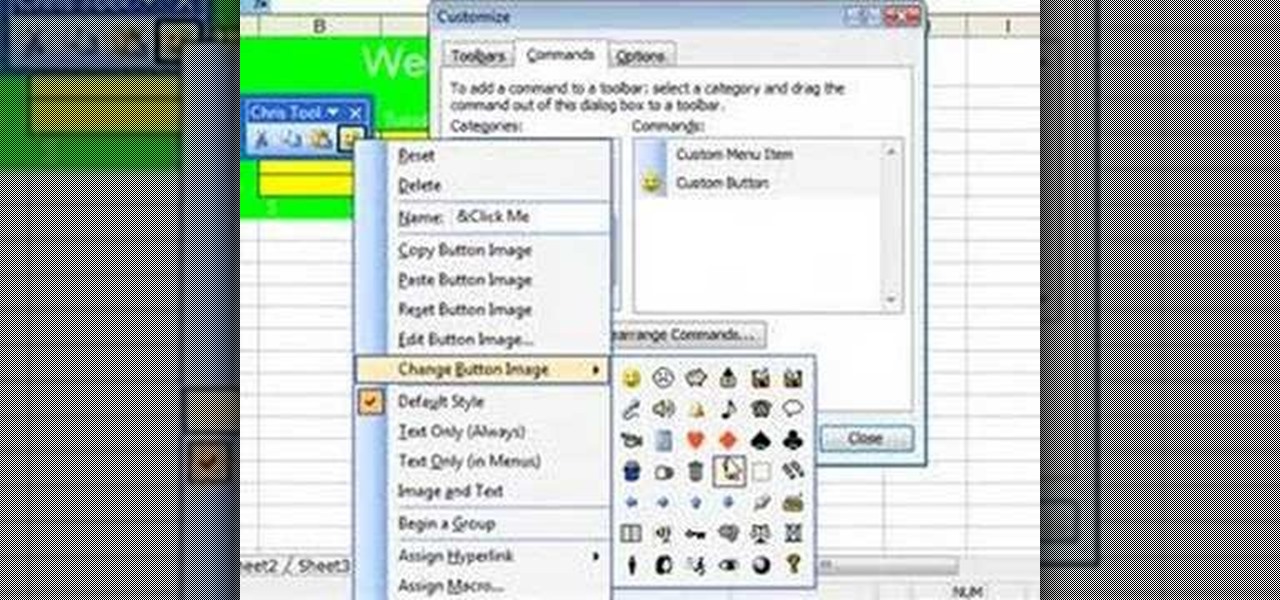
This video describes how to create a custom toolbar in excel. First we have to go to tools menu in the excel. Next take the option of customize there and then choose the toolbars there. Next there will be the option “new” tab in that box. You have to select it first and then give a name the toolbar, which you are going to create. Then will be get the tool bar. Next if you want to add the buttons to the toolbar that you have created now, you have to go to commands tab. Then you will get ca...
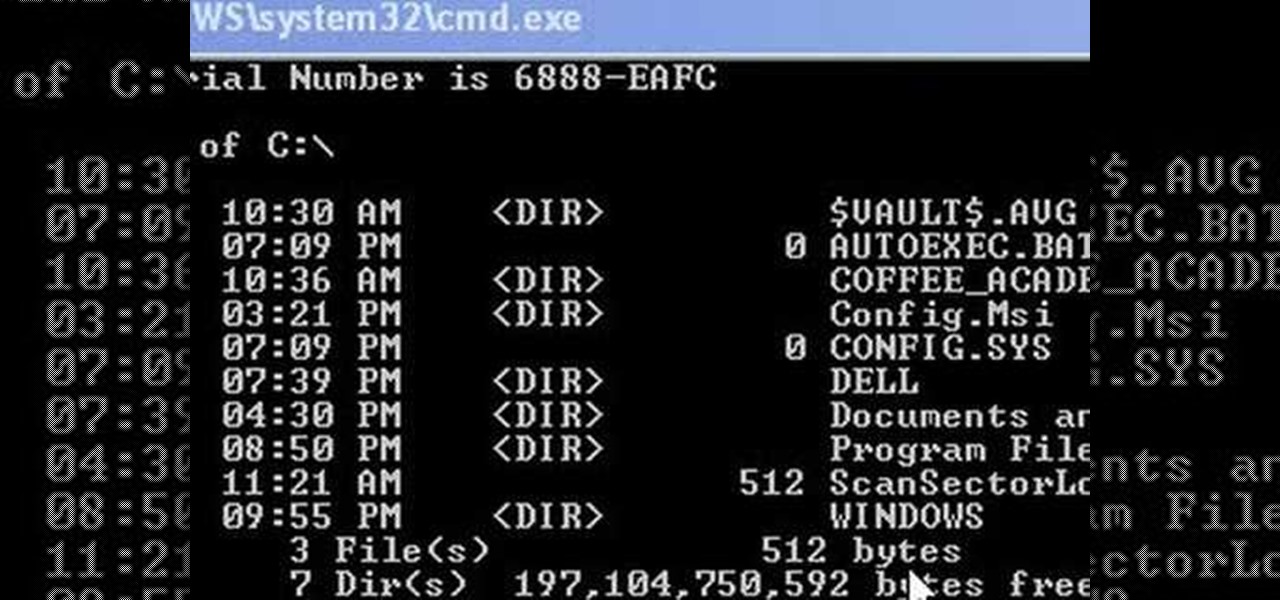
This video shows us how to change driving letters or directories in DOS command. Firstly go to start menu and then click on run. Then type cmd and press OK with which a DOS command cmd window will pop up. Now you need to change the directory and these is done by typing ‘cd..’ and after that press enter. Now you have changed the directory and now you need to see what’s in there and for that type ‘dir’ and press enter and this shows what’s in that directory. Now change to other directory by typ...
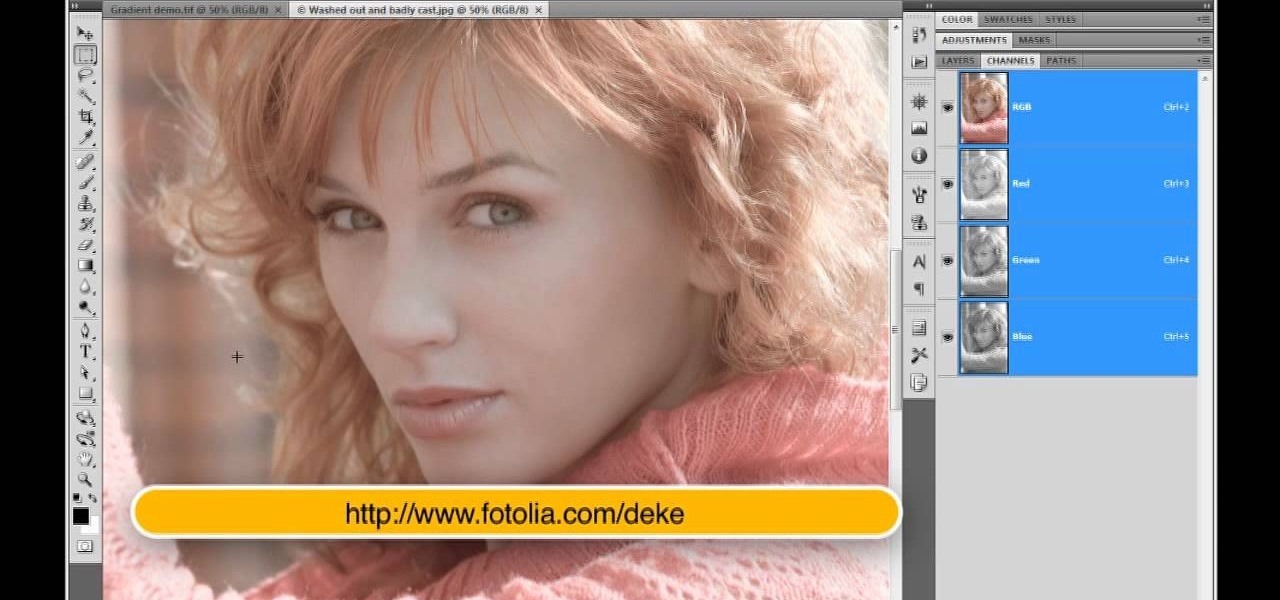
Deke McClelland explains what the Levels and Histogram commands can do in Photoshop in this video tutorial. Levels allows you to adjust the luminance levels allowing you to adjust the contrast and colors within each color channel of an image. Thus, Levels allows you to adjust the individual colors that can be found within a gradient. This command is very similar to the curves command but to a less powerful extent. It is also more efficient than the curves command. The Histogram is another col...
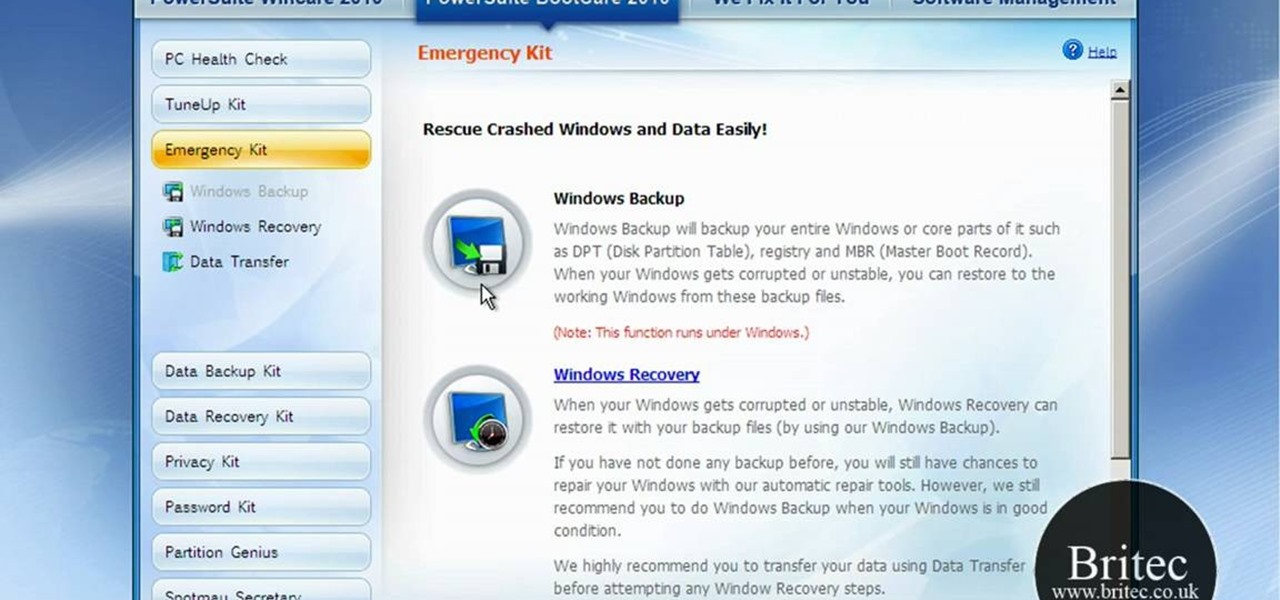
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.
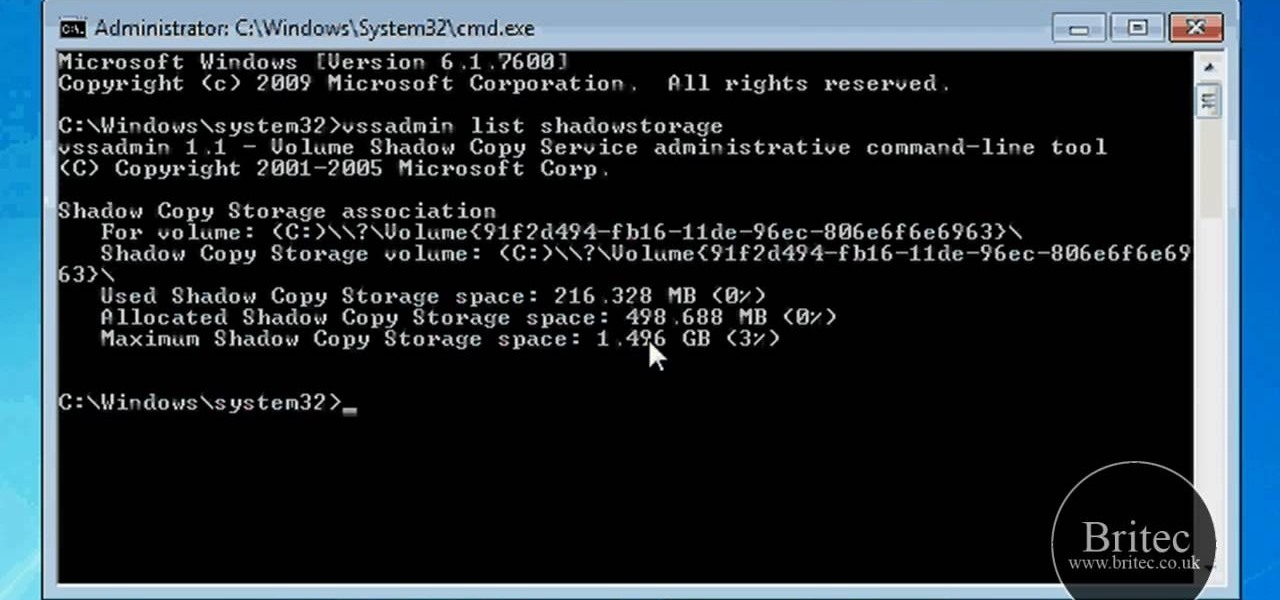
Is your computer getting up in its years and running slower than when you first purchased it? Your problem may lie in the machine's System Volume Information. Watch this video to see how to reclaim or resize disk space from SVI.

The CS4 version of Adobe Flash has altered the appearance and layout of your screen. If you draw often in Flash, this tutorial shows you how find and use the Smooth and Straighten functions efficiently and add them to a menu using the history and saving as a command.

In this video tutorial, viewers learn how to quickly copy a folder's content list in Windows. Begin by clicking on the Start menu and open the Run program. Then type in "cmd" to open the Command Prompt window. Now navigate the desired folder and type "dir | clip" beside it. Press Enter and it will automatically copy the directory to the clipboard. Essentially, it is a tool that will the command prompt command to the clipboard. This video will benefit those viewers who use a Windows computer, ...
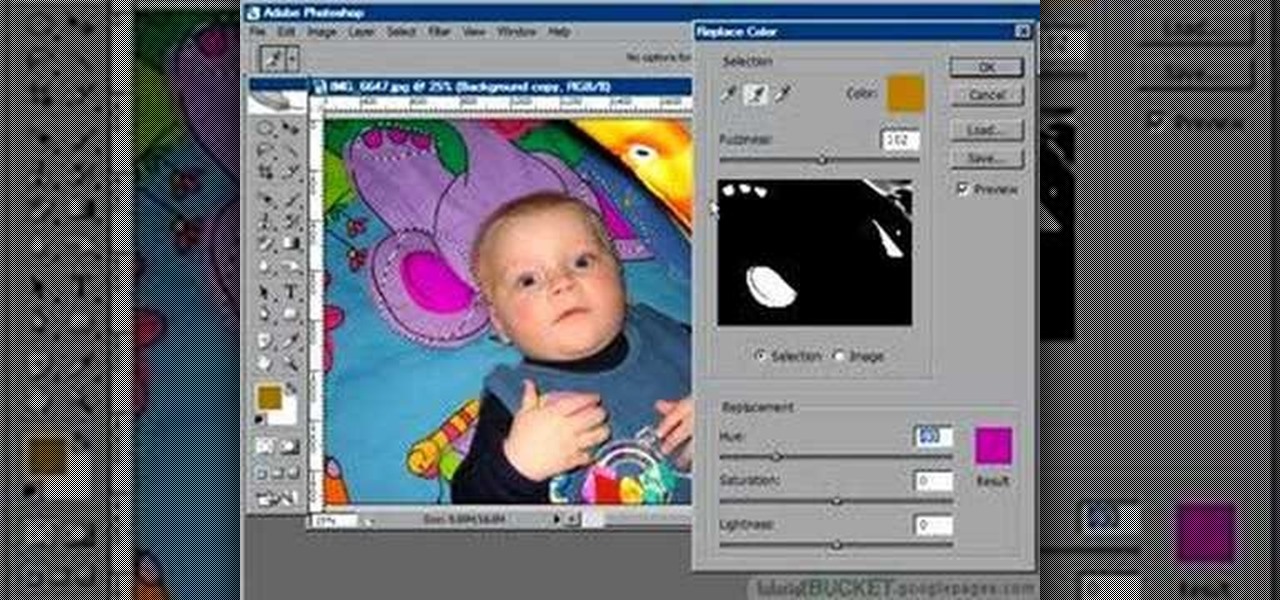
The replace color command is a nifty tool in Photoshop that enables you to change a color in an imagine very quickly and effectively. The tool requires that you make a copy of the original layer, as the replace color command is a destructive function. It requires parts that you want replacing to be selected first, to change the color of the desired areas. The result is a very realistically edited image, that is extremely fast and easy to accomplish.

Wouldn't it be handy if, while running Mac OS X, you could enlarge some of the fonts and applications like Mail or Safari? Some of those fonts can be relatively small. All you need to do to increase font size in an OS X application is to press the command, shift and plus keys. To make a font smaller, in turn, all you need do is press the command, shift and minus keys. For more on using these key commands to obviate the need for squinting, watch this Apple tutorial.

Watch this software video tutorial to learn how to control full-screen playback with keyboard commands in VLC Media Player. The tips in this how-to video will help you easily use VLC Media Player shortcuts to make full-screen playback more convenient.

This AutoCAD 2008 tutorial covers working with commands, opening and saving drawings.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.