It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command to unlock the bootloader.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

The Google Assistant is great about understanding what you actually mean, so you don't have to issue exact commands like you do with Amazon Alexa, for instance. But even though it's a master of colloquial speech, it could still be better, and that's where shortcuts come into play.
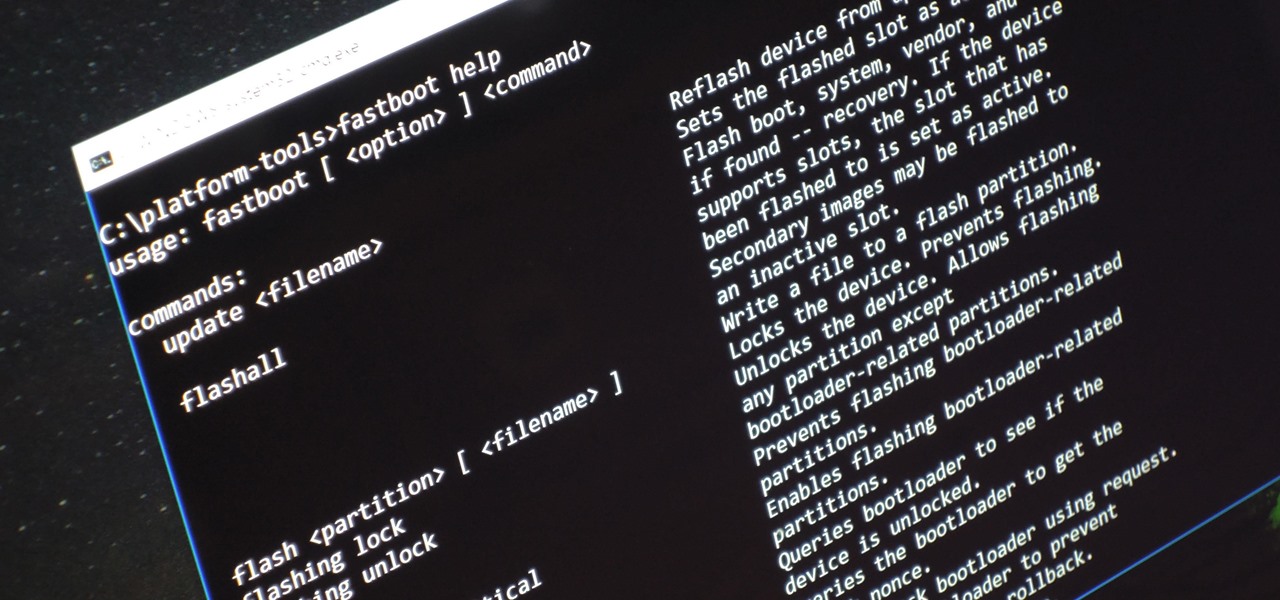
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Like Gesture Input, Voice Input allows you to act on the focus of your Gaze. However, the commands you can use with Voice Input are only limited by your imagination.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

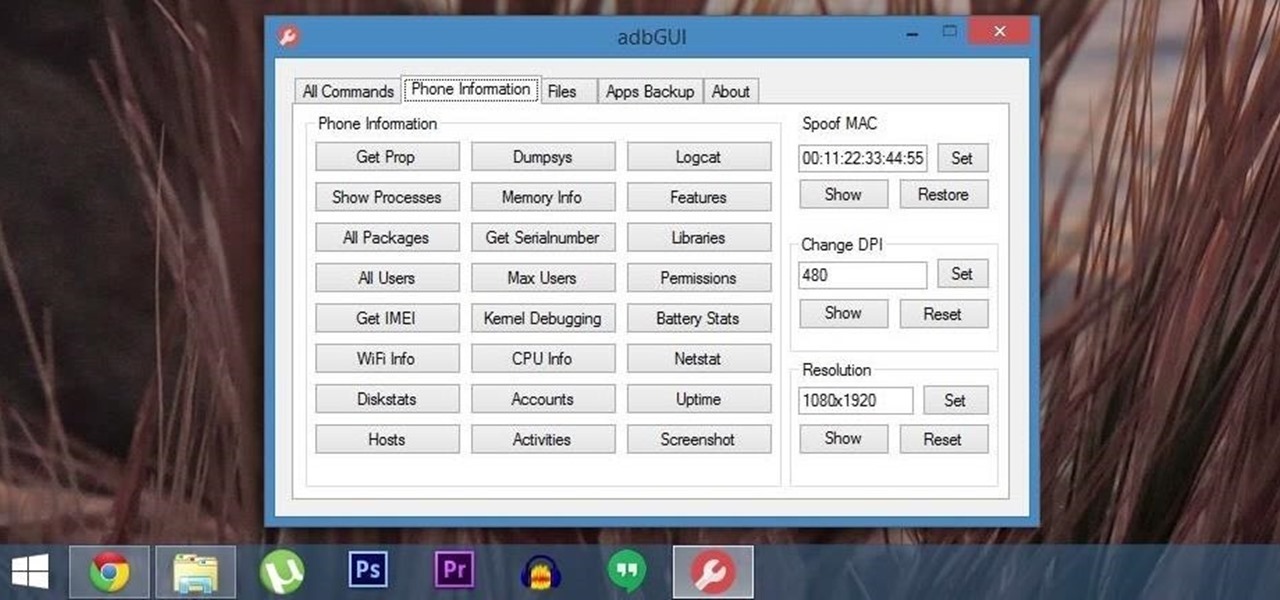
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

One of the lesser known features brought along by the roll-out of Android 4.4 KitKat is the ability to screen record from within the device. This features isn't overtly obvious, nor is its implementation the most streamlined, but if you were ever looking for a way to capture video of what's happening on your screen, this is now the best way to do it.

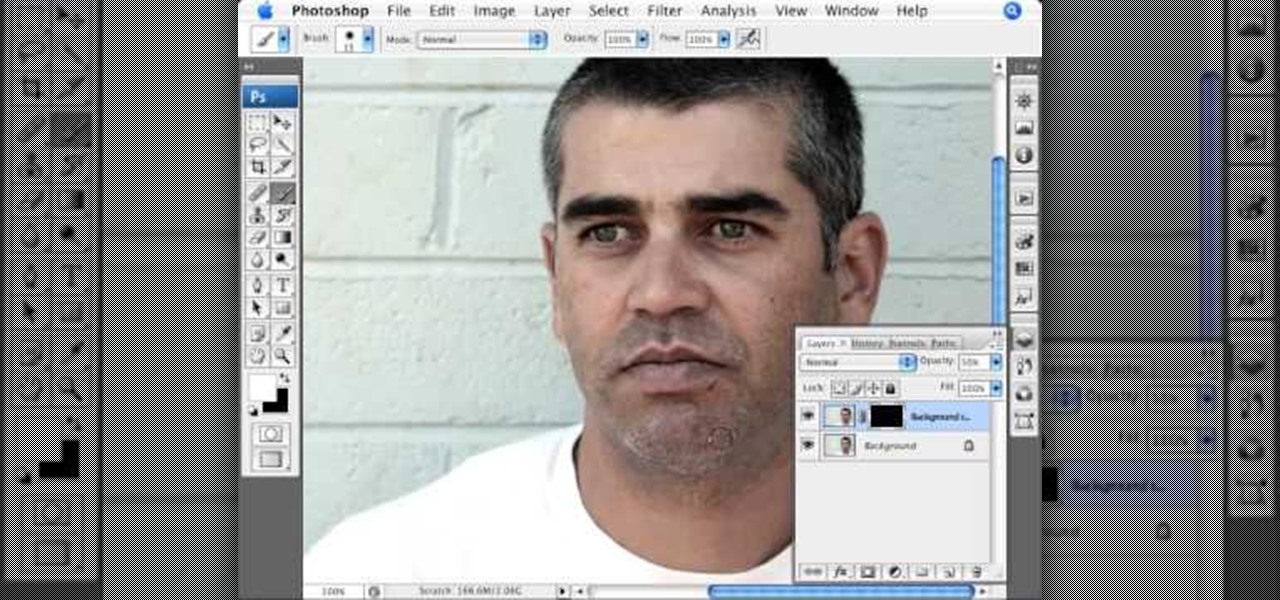
This video, produced by Photoshop Universe, teaches how to reduce beard stubble or 5 o'clock shadows from male pictures. We are shown how to use the dust and scratches filter, layer mask, as well as the advanced layer style command "blend if" on the underlying layer helps us to make this possible. The first step is to duplicate the layer and then select filter, noise, and dust and scratches. The second step is to apply some dust and scratches to the beard selection. Finally we blur the layer ...

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that gives you a nearly identical experience?

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

After years of user complaints, Samsung is finally letting us remap the Bixby button without the need of a third-party app. The new feature requires One UI a simple app update to Bixby, but there's one major downside: Samsung won't let you remap the button to open other digital assistants like Amazon Echo, Microsoft Cortana, and Google Assistant. Luckily, there's an easy workaround.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Nearly one year after its announcement, AirPlay 2 has finally landed on iPhones everywhere. Not only can you easily control multiple speakers including Apple TVs and HomePods from your iPhone, but you can use Siri to help you get the job done. It's one of the iOS assistant's best features, and if you're running iOS 11.4 with a compatible speaker, you can try it out right now.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app.

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

While my desktop is usually neat and organized, it quickly fills up with screenshots each and every day. Usually, I end up putting them in a folder or just trash them, but why not make the entire process of taking and organizing screenshots easier by changing their default save location? With the help of Terminal, I'm going to show you how to change the default save location of screenshots to anywhere you want in Mac OS X.