Maybe it is narcissistic to take selfies, but it has become a socially accepted norm, no matter how stupid you might look doing it. Since so many people are seemingly in love with themselves and mobile photography, I thought it was about time to show you how to step up your selfie game.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.
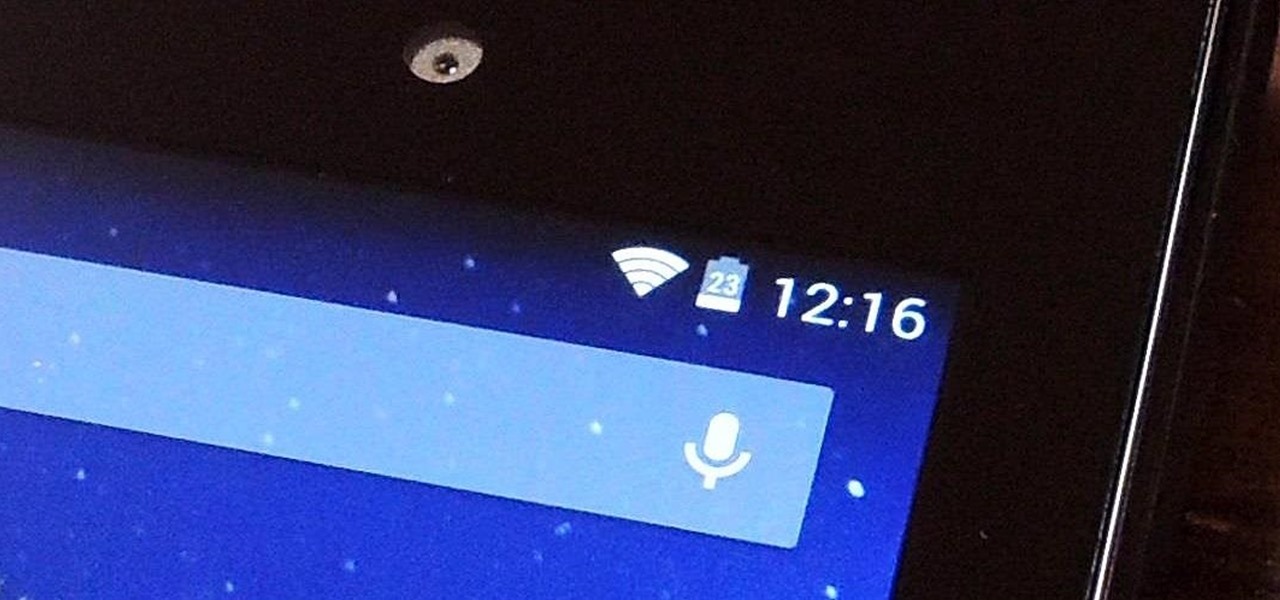
Much like the built-in screen recording tool on Android 4.4 KitKat, hidden features like the new battery Status bar icon must be manually unlocked on your Nexus 7 tablet. This is both exciting and annoying.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Teaching your dog to sit establishes trust and also creates a foundation for other tricks. Learn how to teach your dog to sit with this dog training video.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

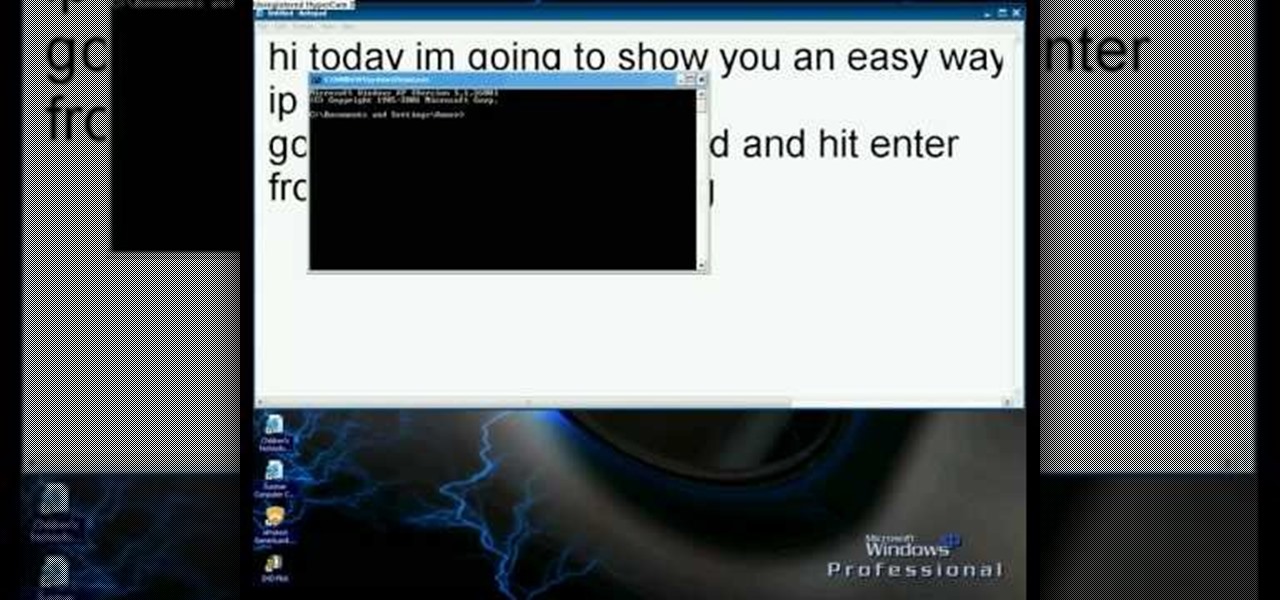
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

In this clip, you'll learn how to generate admin command prompts on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

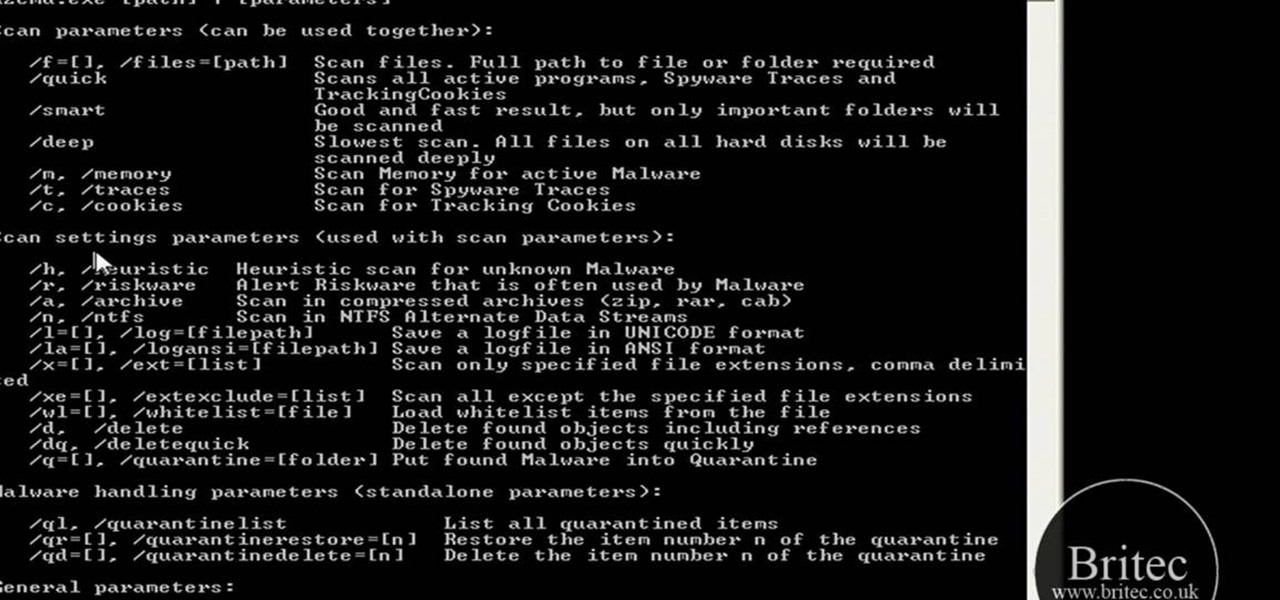
Want to know how to remove viruses, adware and other sorts of malware from the Windows command line? It's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, watch this video guide.

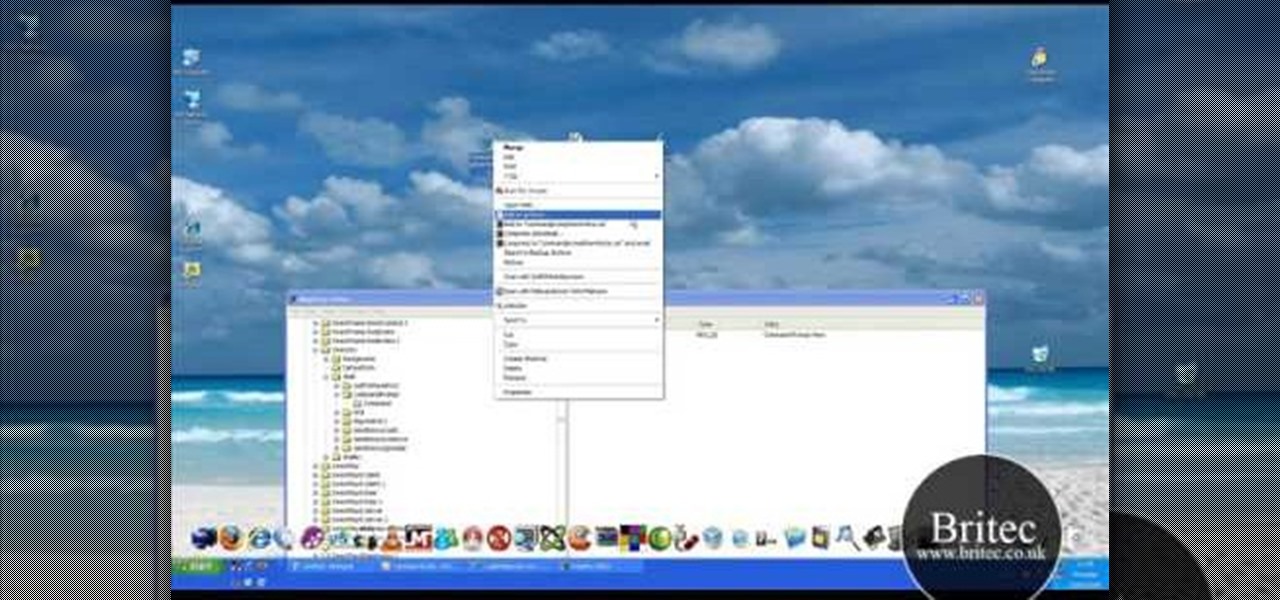
Interested in adding a shortcut to the command prompt to the right-click Explorer menu in Microsoft Windows XP? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under five minutes. For more information, including step-by-step instructions, take a look.

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...

In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...

This walk-through video tutorial shows you how to find out your IP address for XBox live. First press the start button and search for run as shown, click the result, bring up the dialog and type in the given command to open the command prompt window. Type the command in the given window and hit enter. The number that appears is your IP address, use it as the key for XBox Live. In the case of XBox 360, it automatically detects it.

Ever plug in a Windows keyboard to a Mac only to be frustrated by the swapped layout? This computer tutorial video shows you how to iron out the mix up with this quick tip. Watch this how-to video to learn how to easily make the transition from Mac to PC (and vice versa) by taking control of your command keys.

Linguist Bud Brown shares some insights and advice about learning Vietnamese. This video talks about how to say the imperative (command) form.

These tricks are all based on nothing more than solid command of double flips. Watch an actual demonstration of double flips. Learn how to use consistency and command.

Bob and Brett show you how to burn your mixes on CD using a command called "bounce" in Pro Tools.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

In this tutorial, we learn how to create interactive shortcuts in Gmail:Greasemonkey. Start off by searching for "Greasemonkey", then click on the very first result. Click to install this, then once you have it you need to restart Firefox. Now, on the bottom of the screen you will see a little monkey icon. After this, type in "Greasemonkey scripts" into Google, then search for "modified Gmail macros" and install this. After this is installed correctly, go to your Gmail account. First, type in...

This video tutorial from Help-Vids shows you how to setup the automatic login in Windows XP so that you are automatically logged in as a specific user when you turn your PC on. Go to the start menu, select run and type the given command. When the user account dialog opens un-check the setting requiring the user to enter a name and password to use the computer and click apply. Fill in the user name and the password of the user that needs to be automatically logged in and click OK. Now when you...

The Toyota 4Runner has a DVD based navigation system which features a touch screen display and is quite user-friendly. The system can provide voice guidance in English, French and Spanish. One can find an input destination quickly and easily using either voice commands or manually. You can even store your home address as well as five of your favorite destinations by clicking the map button on the right hand side of the panel. This system will help one reach their destination as quick as possi...

Pixelated photos are always a site for sore eyes. When you crop your photos in Photoshop you can keep your aspect ratio to stay wayward of the "pixelation desecration". When you hold down Shift during your crop it will retain the aspect ratio so you have nothing to worry about. There are also some more commands to help keep aspect ratio during zoom, crop, moving, or anything else of that matter. This video will demonstrate exactly how to retain aspect ratio when cropping in Adobe Photoshop.

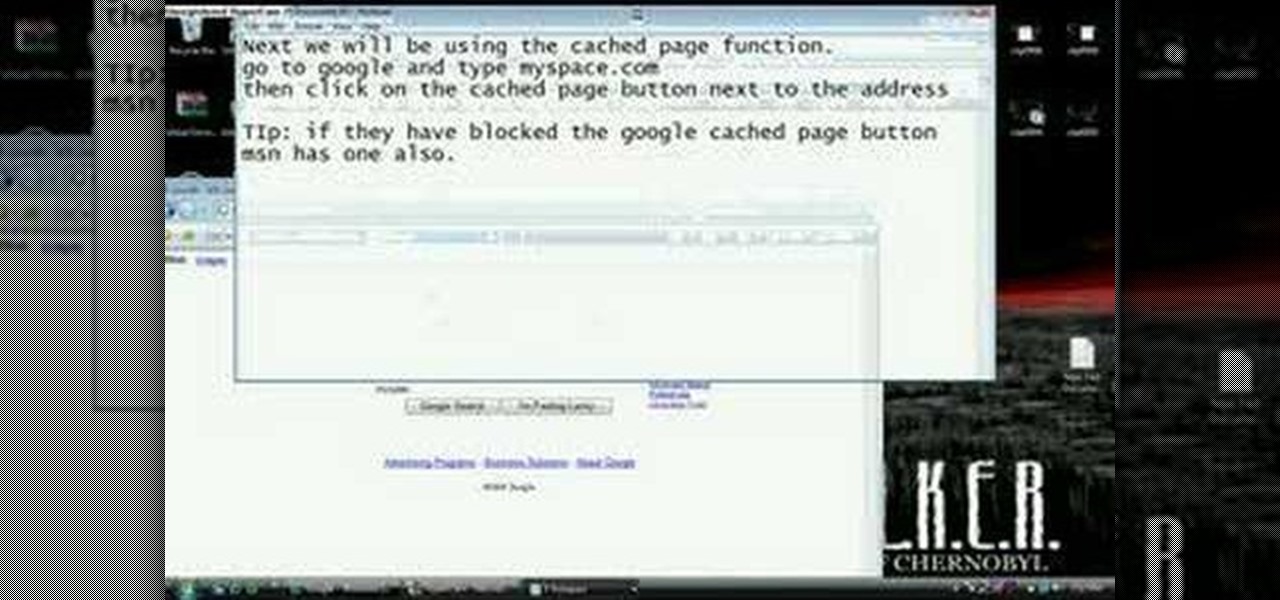
The video provides you two easy ways to get onto MySpace at school. There is no need to install anything at all. If you have a Windows operation system, open a command prompt window and just ping MySpace. Then copy and paste the IP addresses you found directly into your browser's address bar. In case you have a Mac computer, try search 'ip address finder' on Google and tool sites such as ip-address.com can help you find the same information. Now getting onto your favorite MySpace will never b...

Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

After learning the foundation tricks of "sit!" "stay!" and "come!" have your dog try their paws at a jump.

From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

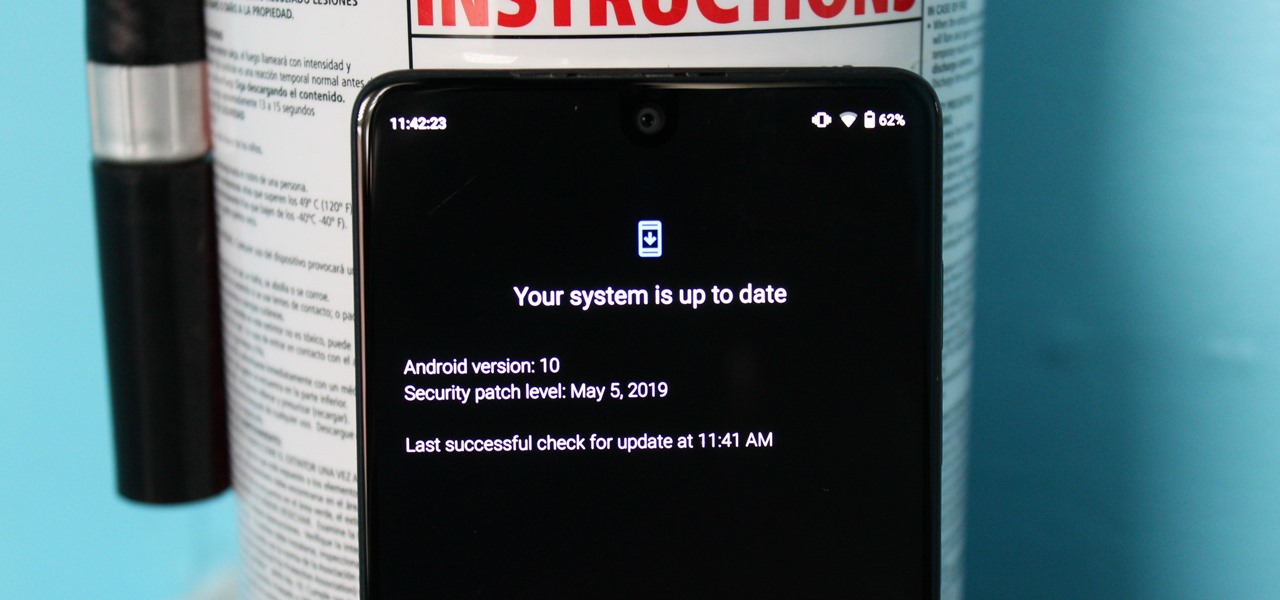
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

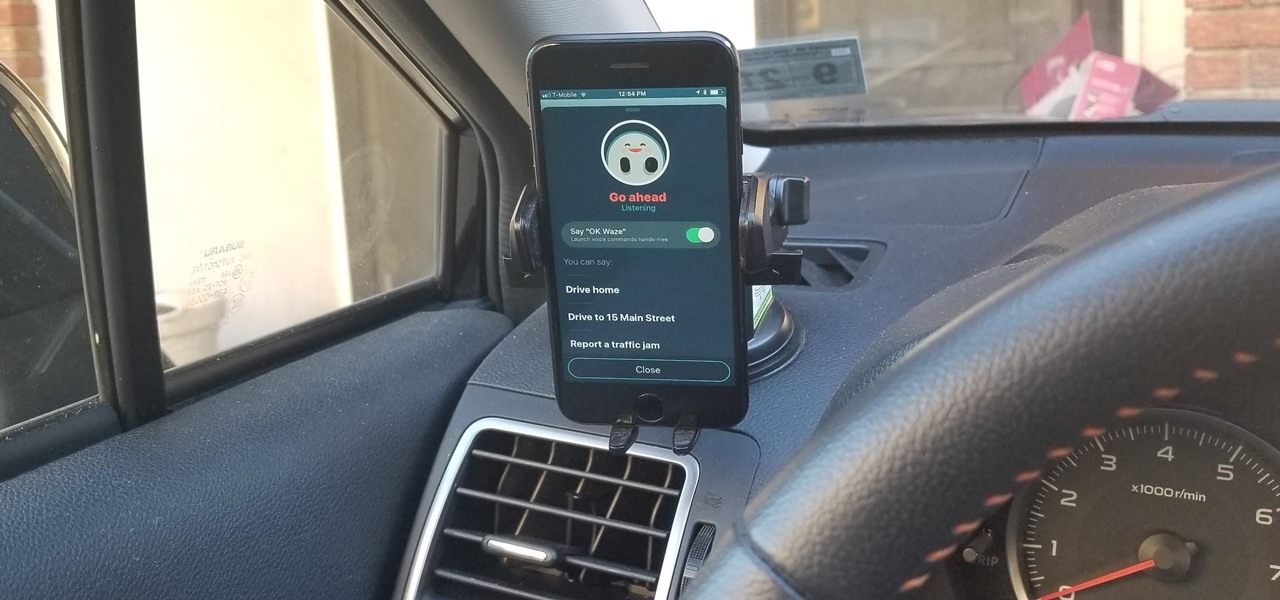
Drivers the world over are painfully aware of the inherent danger of taking their eyes off the road even for a second. In fact, according to the National Safety Council, 27% of all car crashes result from distracted driving due to attempted cell phone use. Fortunately, Waze comes with a feature that can help keep you from being a part of this grim statistic.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

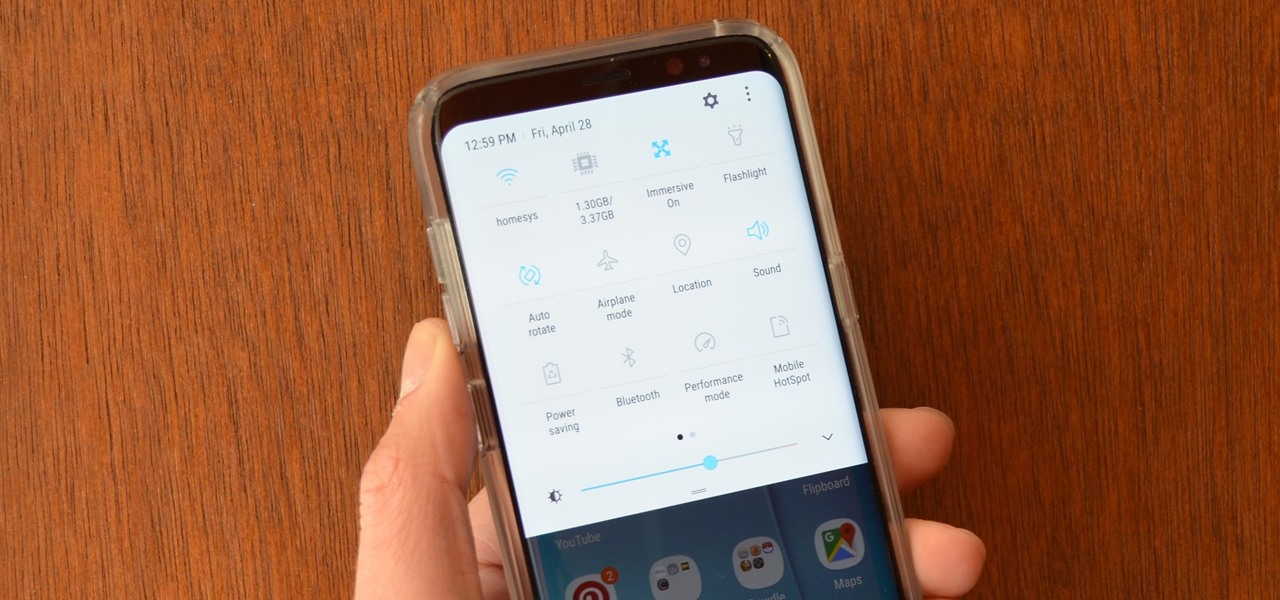
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by auto-hiding your navigation and status bars.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.