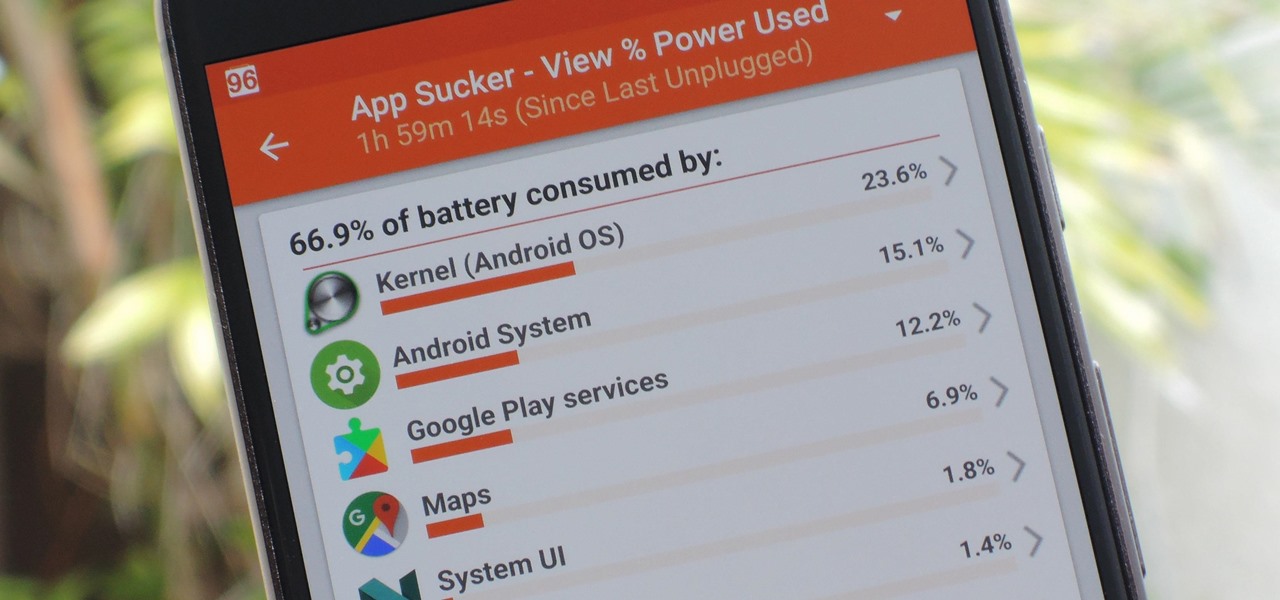
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.
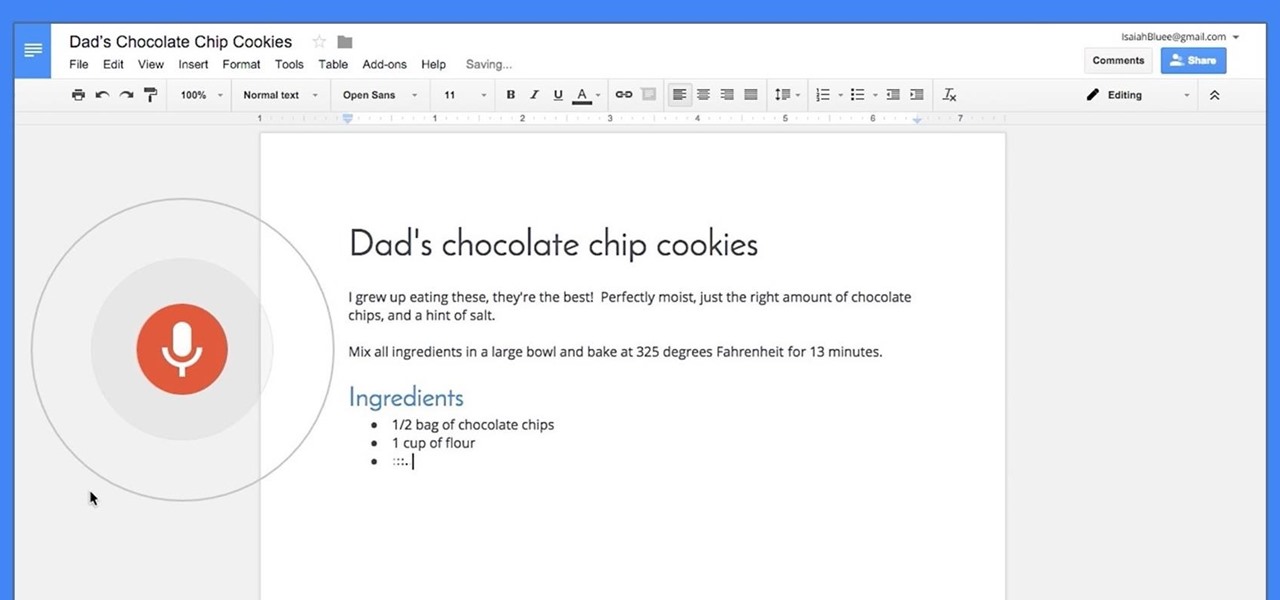
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Microsoft's latest Xbox commercial features Aaron Paul, the actor best known as Jesse Pinkman on Breaking Bad. Check it out below, but keep an eye on your own Xbox One, if you've got one.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

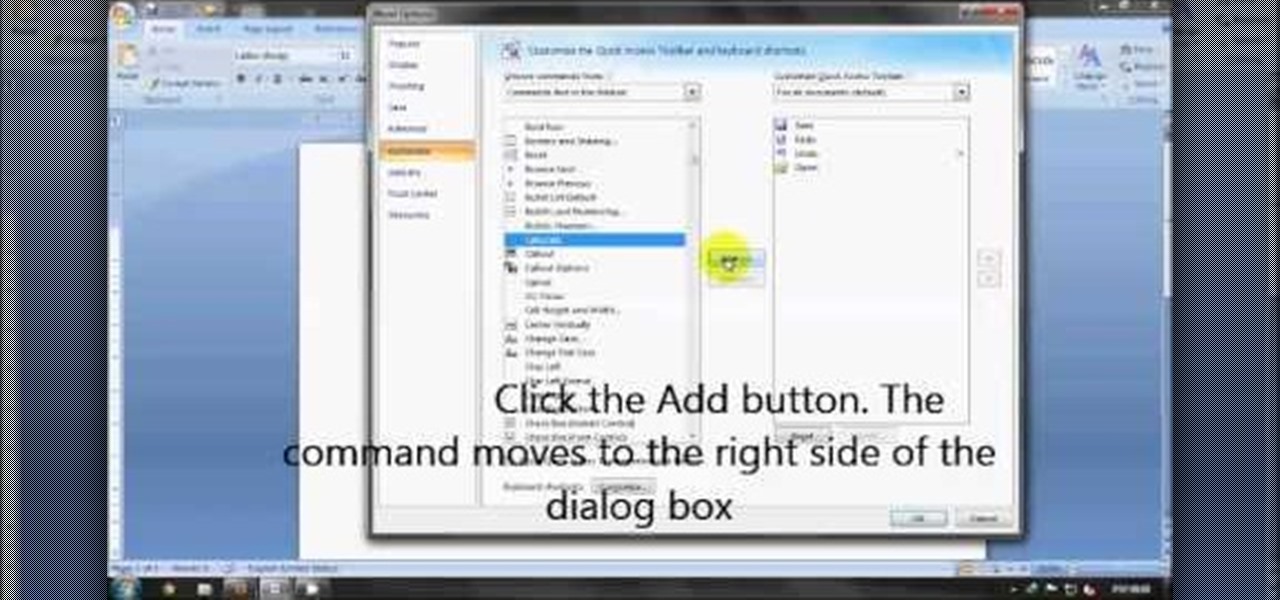
Step 1: Calculating Expression in MS Word Step 2:
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

You have to admit, the armor set on the front of the Fallout New Vegas cover is pretty awesome, but the only way to acquire the armor, besides console commands on the PC, is to kill an NCR Ranger Veteran. There's a way to pull it off without getting any negative fame with the NCR, and the info is in this video!

A dog who constantly follows you around the house wagging his tail is a dog who really likes you (or is hungry), but sometimes you're tired and just want your dog to sit and be still for once. Teaching a dog to sit is one of the most basic obedience training tricks out there, and one of the most important (especially in cases of your dog bounding onto friends who enter the house).

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

Getting text from one area to another is quite simple. You can do so between any text frames. This video will demonstrate exactly how to cut, copy, and paste on your Macintosh.

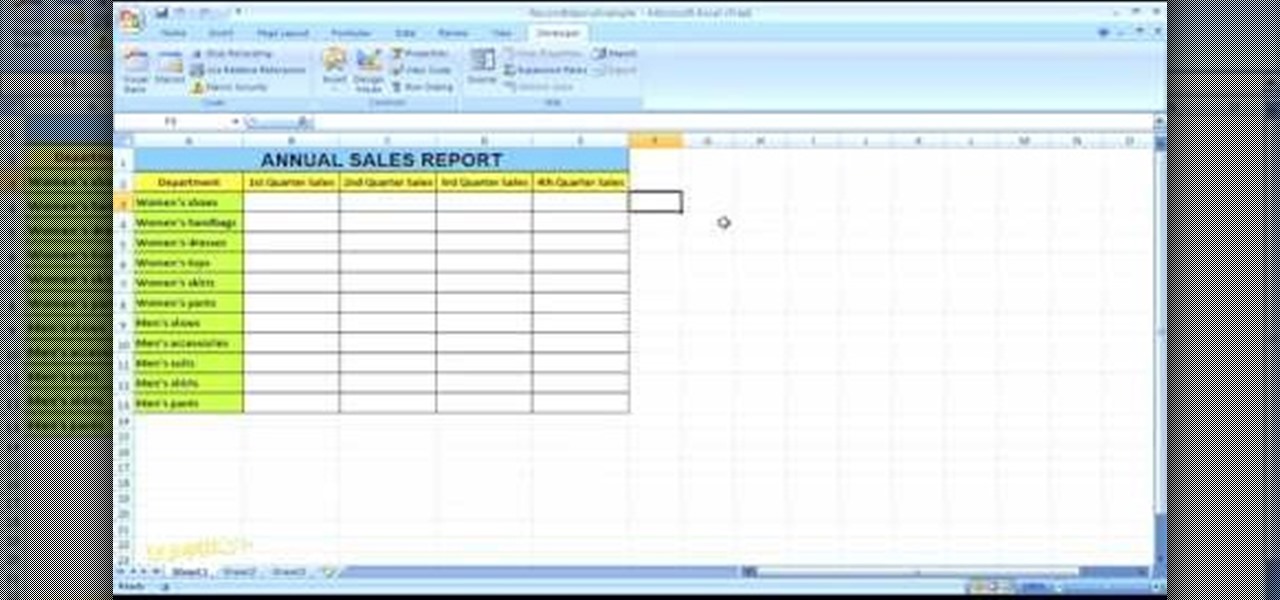
In this Microsoft Excel 2007 for Dummies video the instructor shows how to record a Macro. Macros let you create a shortcut to perform a sequence of commands all at once. For example you can create a macro to quickly build a sales report template that you frequently use. When ever you run that macro the Word will automatically build the template for you based on the recorded commands. To write macros you need to have the developer tab enabled. To enable it click on the office button and at th...

Devolped by the same team of engineers responsible for LightWave 3D, modo, lowercase, delivers the next evolution of 3D modeling, painting and rendering in a single integrated and accelerated package for the Mac and PC. And now, modo is a true end-to-end solution that includes true 3D sculpting tools, animation and network rendering! More than just features, modo is a truly elegant integration of technology, raw horsepower and refined workflow. With such a wealth of inbuilt features, however,...

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient and safer to use.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.