Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.
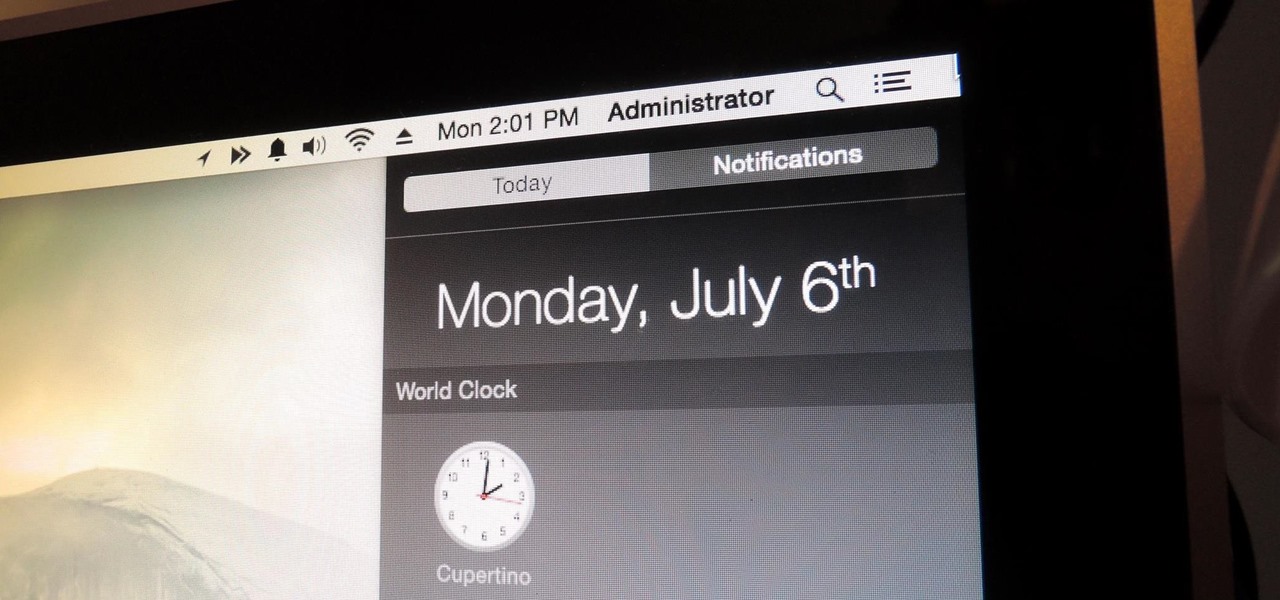
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

Tony Stark is a smooth talking, genius billionaire playboy that occasionally saves the world... what's not to like? The Marvel films starring Robert Downey, Jr. have grossed well over a billion dollars in the U.S. alone, so it's needless to say that Iron Man is a very popular superhero.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

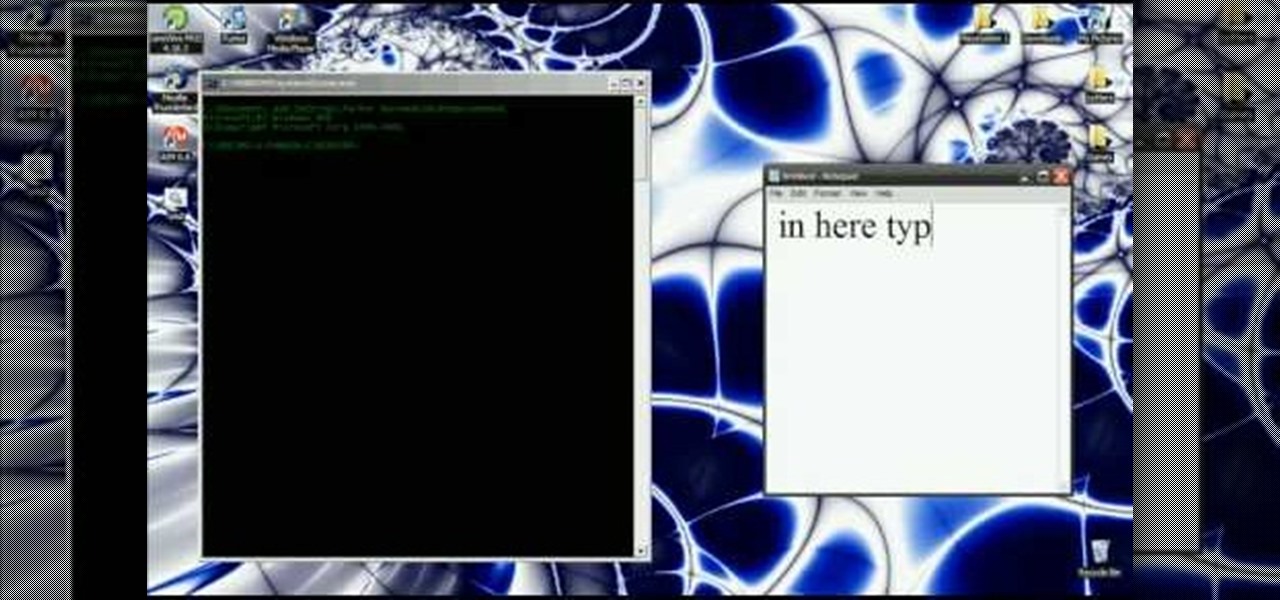
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

Finding Linux hard to handle after using Windows? Well this should help, here is how to install software on Linux. Start off by clicking on application launcher. Here go into applications, then into 'system' where you should find software management. In this program go straight into the settings and then edit software sources. Under 'downloadable from internet' make sure every option has a check against it. Now press the software management tab on the side. Now this is where you can get which...

If there's nothing else you take away from this video, know this: Dogs, and especially puppies, thrive on consistency. If you want them to do a down command, ALWAYS say "down" - don't ever switch the wording.

In this video tutorial, viewers learn how to zoom in and out on a Mac computer. To access the zooming tool, begin by clicking on the Apple menu and select System Preferences. Under System, select Universal Access and check On under Zoom. In Options, users are able to set specific settings such as the maximum and minimum range of zoom. The keyboard shortcut for zooming in is: Option, Command and =. The keyboard shortcut for zooming out is: Option, Command and -. This video will benefit those v...

In this how to video, you will learn how to teach your dog to retrieve. First, you should teach your dog the a regular retrieve. You will toss the object so that the dog sees where it lands. Next, give it the command to retrieve. Next, attempt the semi blind retrieve. This involves tossing the object, allowing your dog to see where it has gone. Next, distract the dog for a bit before giving it the command to retrieve. The full blind retrieve should now be attempted. This is done by hiding the...

Open your first image and go to the rectangular marquee tool and select all of the image. Next click command or control C to copy image. Then go to your second image and click command or control V to paste the image. Select both the layers (hold down shift when clicking the layer), then go to edit, auto align layers and choose the top option then click ok. Last add a mask to your top layer, this is done by selecting the gradient tool (make sure its set black to white, the mode is normal and o...

If you're interested in seeing what it would be like to run Android on a real computer rather than a tablet or smartphone, you don't have to wait. This Android project has now made it possible to run Android in a virtual machine on either a PC or a Mac computer. You'll need the following command to merge the ISOs:

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 618th installment in their series of digital spreadsheet magic tricks, you'll learn about a handy key command that will allow you to enter both today's time and date into a single Excel cell.

This is the most important thing that a dog should know. In this video will learn the fundamentals of how to begin to teach this. It is by no means entirely conclusive to the training that is involved in teaching stay. Tab with his German Shepherd "Solea" demonstrate the do's and don't when training your dog to "stay". You'll also learn the importance of this command for the dogs safety.

Check out this lesson on how to understand your dog and train her to listen. This video will show you how to use a clicker to communicate with your dog. It will also show you how to teach your dog the "Leave It" command. This is a helpful video for training puppies and older dogs.

Following the success of Mimic Baby (sign language for babies) Selena Lohan developed Mimic Mutt - sign language for dogs. It turns out it's easier to communicate with your dog using regular sign language than voice commands. Watch the video to find out more.

Do you constantly let people walk all over you? Go from doormat to dominator with this advice. You Will Need

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

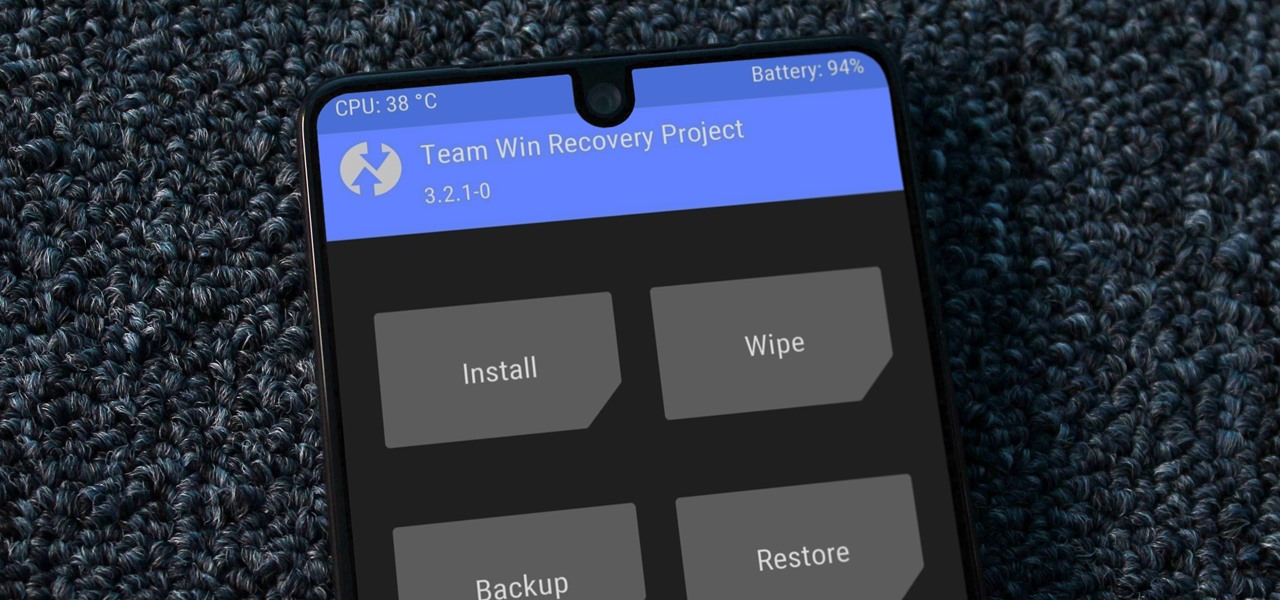
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.