In this clip, learn all the basics about bobby pinning. These classic clips are popular with dancers and performers because they are easy to hide and hold a style really well. If you are new to bobby pins or just need a refresher course, watch this clip and start pinning!

Take your Halloween celebrations into another realm entirely by making these disgusting bloody brain soaps. Hidden within each brain soap is a gooey slime that'll ooze out after several washings.

Looking to get super creative with your shoelaces? In this video, fifteen different shoelace styles are gone over with diagram as to how they were done. Such styles include the checkerboard, the double back, loop back, sawtooth, riding bow, twistie, lattice style, footbag, ladder, bushwalk, bi-color, display, hidden knot, and the zipper style. Use two different colored laces when doing these styles to jazz things up!
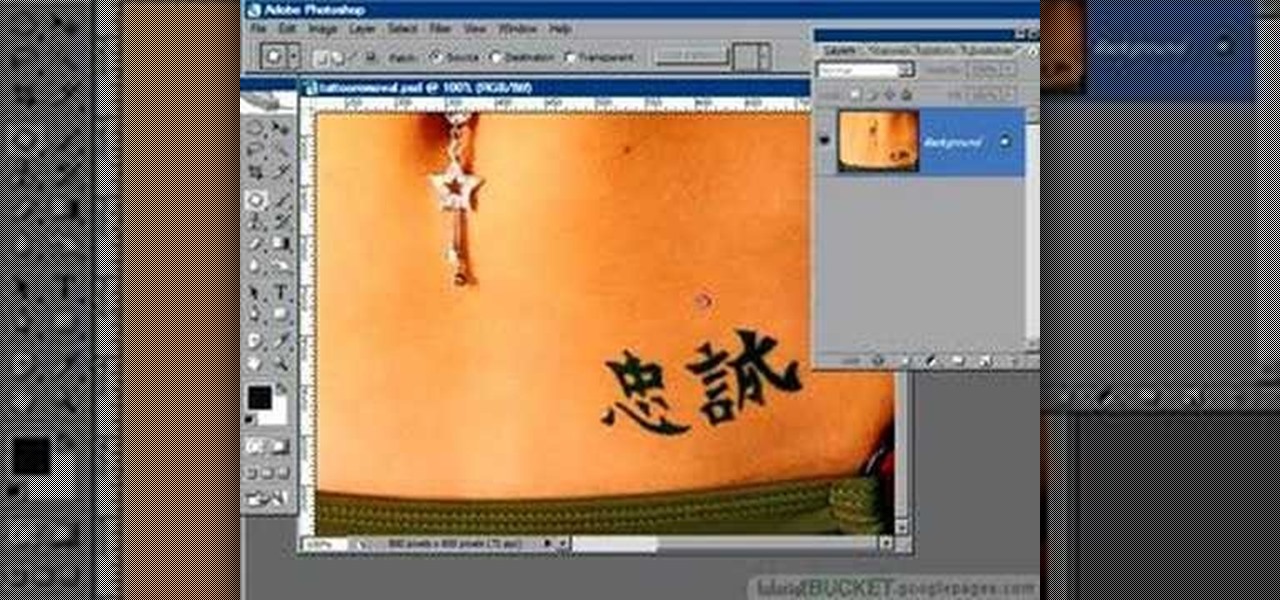
Hidden features of the Patch tool revealed as we wipe out some nasty looking tattoos. Use Photoshop CS4 to fix the tattoos or body scars with the Patch tool. Remove your ugliest mistakes with the Patch Tool, a tutorial from TutorialBucket.

This video shows how to setup and use your DynaSpy wireless video surveillance camera.

In this software tutorial Barton Damer explains the hidden secrets behind Adobe Illustrator's pattern brush. Watch and learn how to create an intricate and unique pattern with the pattern brush in Illustrator CS3. Some of the graphic elements used in the tutorial come from the Go Media arsenal sets.

Need to adjust your microphone's input volume using the Realtek Sound Manager but aren't sure how? The 20db mic boost gain appears to be in a buried spot in the Realtek HD sound cards software, but it's there! In this video tutorial you'll see how to get to it.

This video will show you how to replace a wick in a standard Zippo lighter. This method can also be used in many other similar style lighters. As you will see in the video, you might not even need to change it, but rather just use what's left. There's a lot hidden in there!

Learn how to etch an iron meteorite to reveal its hidden crystalline structure. This guy is specifically etching a Campo Del Cielo meteorite. Why? So you can see how to do it yourself.

Design your own font characters for windows, using a hidden application in windows xp. Try it now!

Learn how to make a pen in which to easily conceal and retrieve test and exam answers by watching this how-to video. If you're too lazy to do your reading, or you don't think you have a prayer of passing, try a cheat sheet. Check out this video tutorial and learn how to hide answers or notes on a pen. Just remember, you're only cheating yourself by not studying.

James (The Amazing) Randi speaks on spoon/key bending and hidden picture reproduction. These were tricks pulled by Uri Geller to show he had psychic powers. Arthur C Clarke was one of many who spoke out against Geller and sought to distance the paranormal studies from Geller's bogus performances.

See how a simple rubber band can become a hidden answer key for a school test.

Want a safe place to hide your stash? Here's how to build a miniature electronic safe out of an Altoids tin and a Hallmark musical greeting card.

Have something you want no one else to find? The best hiding places are in plain sight. Follow these steps to create a shockingly sly storage space.

Have you ever looked behind your desk and found a clutter of cords? Cords tend to find ways of tangling themselves up, so watch this video to learn how to reduce the clutter.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

In this video, we learn how to transfer songs from an iPod to your personal computer. First, open up your computer and go into the folder with your iPod. Now, go to tools, folder options, view, and hidden files/folders. Apply this, then the folder with all of your music will show up! You can now unplug your iPod and then select all of the folders on your computer. Right click then and go to properties, then uncheck the hidden. Hit 'apply' and then transfer all the music to your computer. Now ...

In this tutorial, we learn how to skin a deer with a golf ball. First, hang it up by a tree around its neck. From here, taper down from the shoulders until you reach the bottom. Then, cut each of the ankles right around the knuckle and slice it down the front like normal. From here you will take a golf ball and stick it in the hide. Hold the hide over the golf ball and then make a ball with it. Then, take a slip knot and wrap it around the golf ball, tightening it up tight. From here, you wil...

In this video, we learn how to delete hidden driver viruses. First, scan your computer with anti-virus and try to delete the virus that is harming your computer. If you have done this and your anti-virus can't delete it, download HijackThis from Trend Secure. Go through the download stages and install the new software. Now, open up HijackThis on your desktop. Once it's opened, open up the "misc tools" section. After this, click on "delete a file on reboot". Now, write the virus location name ...

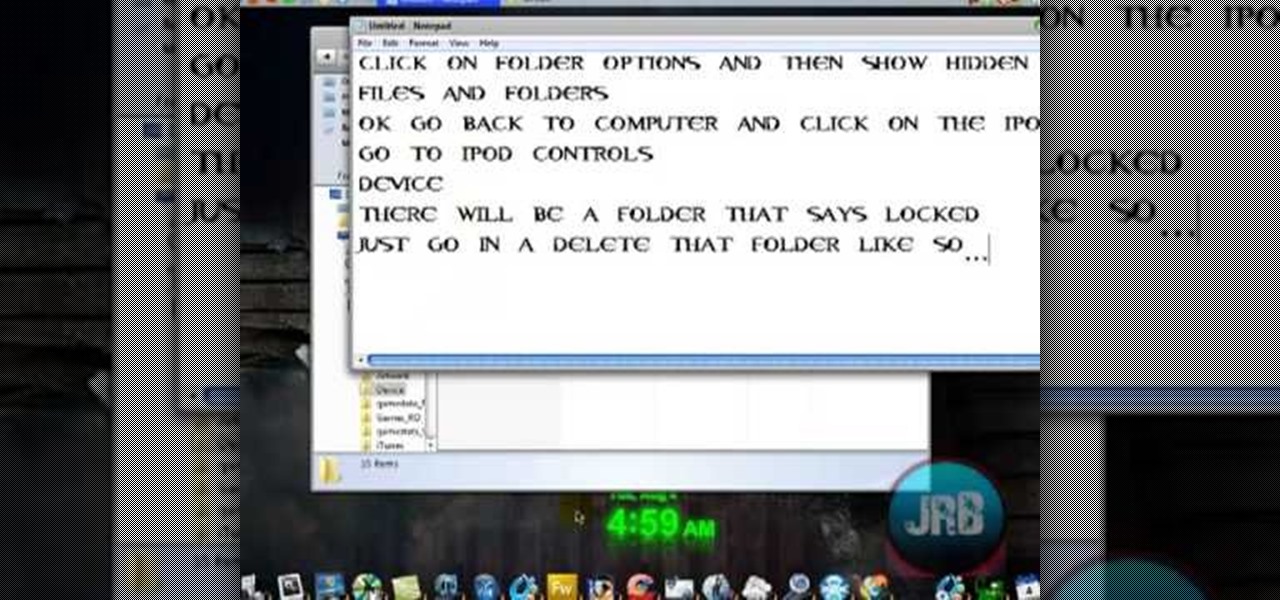
In this video tutorial, viewers learn how to unlock a locked iPod. Begin by connecting the iPod to your computer. It should fix itself automatically. If it doesn't press the Start button and select Control Panel. Click on Appearance and Personalization. Under Folder Options, select Show hidden files and folders. Check the box that says "Show hidden files and folders". Click Apply and then OK. Go to My Computer and open the iPod device. Select the Controls folder and click on Device. Delete th...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to hide and display desktop icons, such as mounted drives, computer, and trash icons, on Ubuntu Linux.

So you beat the final boss in Final Fantasy VII and it seemed way too easy considering the amount of time you've invested into this epic game. There are two additional hidden bosses in the US version of Final Fantasy VII: Emerald and Ruby Weapon, both of which are substantially more powerful than the final boss. In order to even contend with the game's hidden bosses, your characters will need to be maxed out. Take a look at this instructional video and learn how to max out your party's streng...

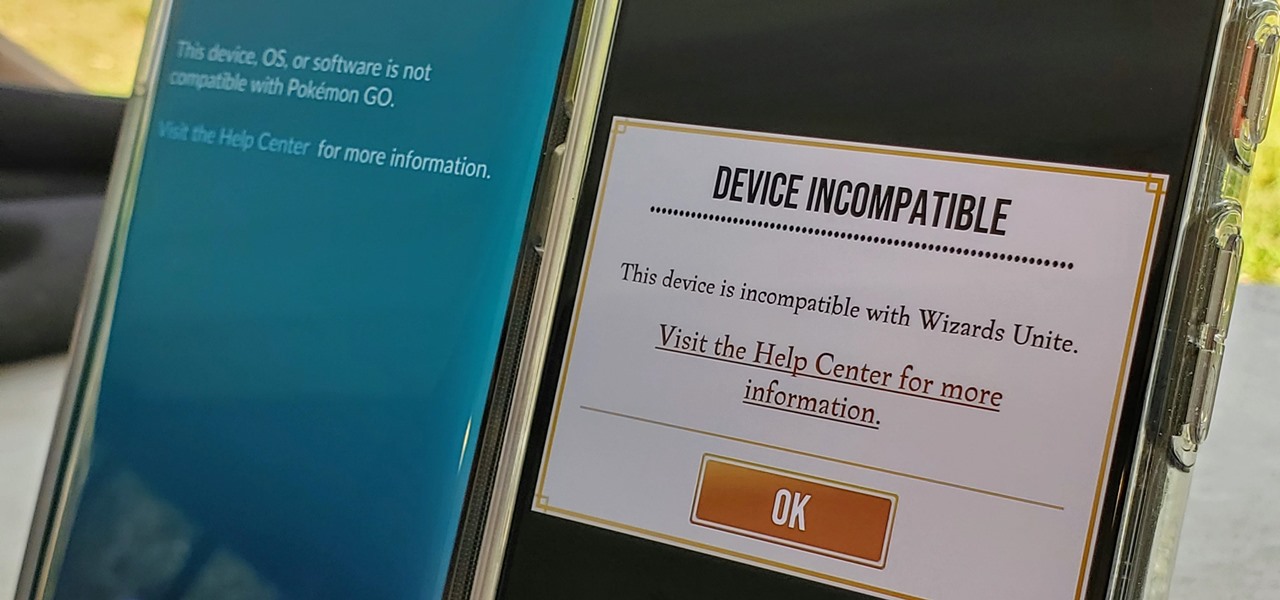
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

With the new navigation gestures in Android 10, you reclaim a lot of screen real estate that used to be occupied by the back, home, and recent apps buttons. But there's still a small bar on the bottom edge of the screen, and in most apps, it still sits atop a black background. Thankfully, an easy hack will give you true full-screen without breaking the new gestures.

The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

The first few times I posted on some of the Android forums out there, I asked things like "Does anybody how I can make my phone do this or that?" Without fail, the responses to these types of questions were always one word—Tasker.

If you want to send someone secret messages you have come to the right place. This is a way in which you can send secret messages to anyone without even making them get a clue that you have sent a secret message.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

Shadows of the Damned features a pretty cool homage to the Portal series of video games right around the first level. Take a look at this video to find out where this easter egg is hidden as the Achievement Hunter team lets you in on the secret.

If you're looking for a clever, stylish, way to disguise your Kindle or Nook, then you've found the right video. This video will show you how to hollow out a book to make an excellent cover for your eReader. The hollowed out book can make a great hiding place for anything.

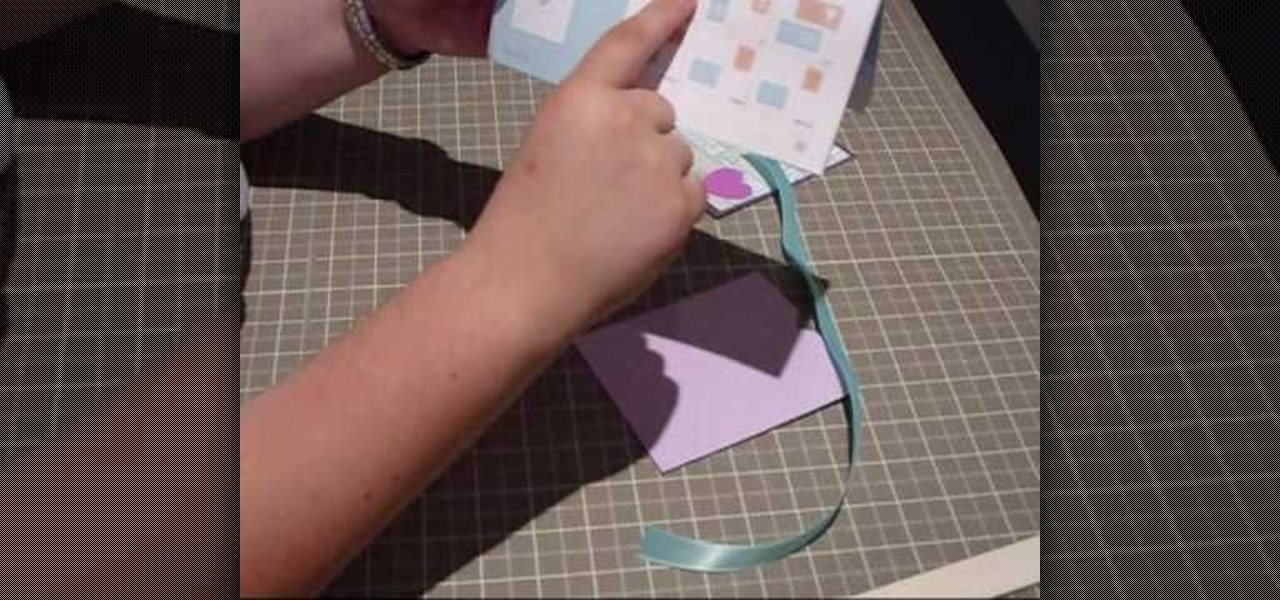
This slider card is an unexpected take on your normal fold-out cards. It slides from the side, revealing a hidden message.

World 2-2 of New Super Mario Bros Wii is a pretty standard Mario desert affair, but that doesn't make finding all three of it's hidden Star Coins any less important. Watch this video for a guide to their locations in the level.

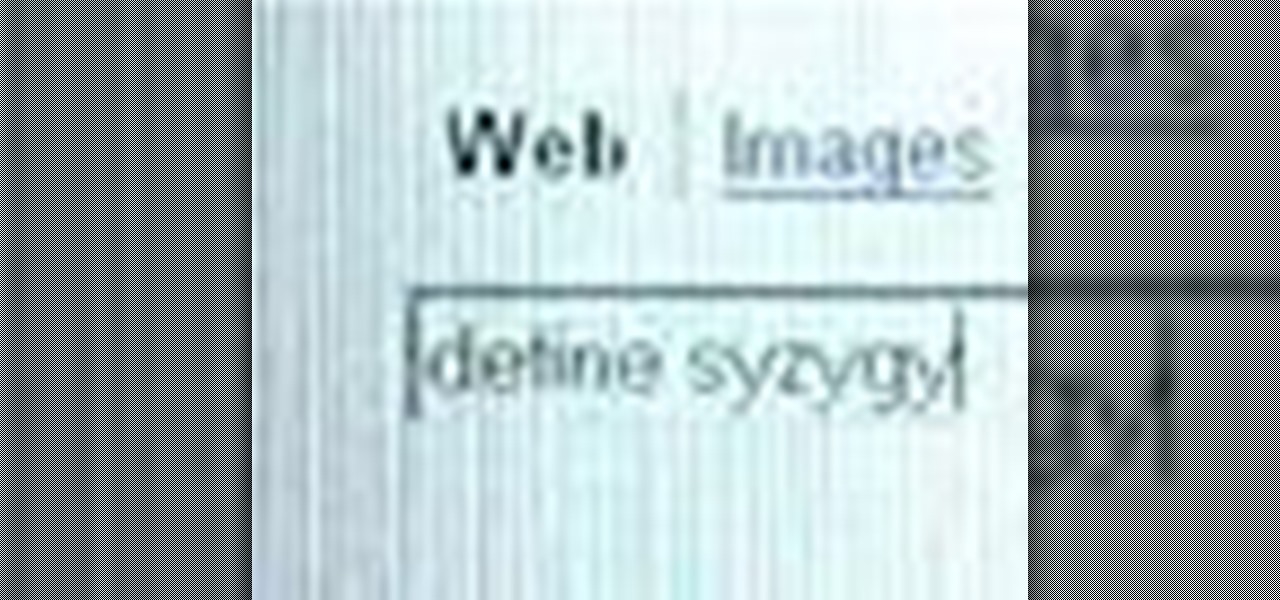
In this video tutorial, we learn how to use advanced search parameters like "define" and "site" to access hidden functions of the Yahoo! search engine. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this how-to from the folks at CNET TV.

In this clip, you'll learn a trick for accessing special characters from the Apple iPad's virtual keyboard. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Had enough of the iTunes "Genius" feature? You can turn it off (or, at the very least, hide it). And this clip will teach you everything you'll need to know. For more information, includind detailed, step-by-step instructions, and to turn off the Genius music recommendation feature in your own installation of iTunes, take a look.

If you like shortcuts, then this shortcut for Windows XP should peak your interest. In this video, you'll learn the exact steps to adding a command prompt shortcut option to the Windows Explorer right-click menu. This allows you to access hidden functionality by adding a right-click option to select "Command Prompt Here" from the menu in Windows Explorer on a directory.