
How To: Hide a file inside of a jpeg
Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.


Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.

Looking for a fun, educational game to play with your children? How about a game of "Hot & Cold"? Played indoors or out, this game helps children refine their listening skills and learn the idea of opposites.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

Normally, when you scroll down a webpage in Safari on your iPhone, it automatically hides the bottom toolbar and minimizes the top Smart Search field. But as soon as you scroll back up, they both reappear, which can be pretty annoying if you don't need them. Apple's iOS 13 update brings many new features to Safari, one of which solves the toolbar issue so you can keep it hidden when reading.
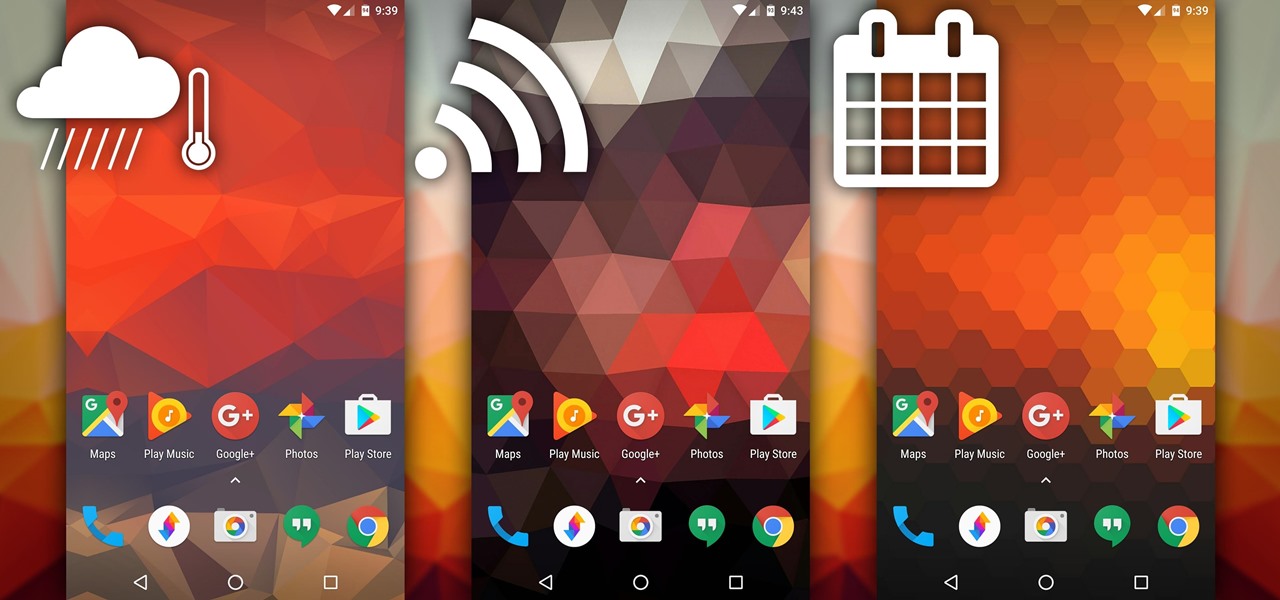
Imagine if you combined Tasker with your favorite live wallpaper—that's roughly the gist of a new app from developer feedK. With this one installed, your home screen background will finally be aware of its surroundings.

Because of Apple's iron grip over iOS, hiding stock applications is a topic we frequently like to cover. While not everyone may think that Apple's preinstalled iOS apps are bloatware, that's exactly what some of them are. For instance, the Apple Watch app; it's basically just an advertisement on your home screen unless you actually have an Apple Watch.

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!
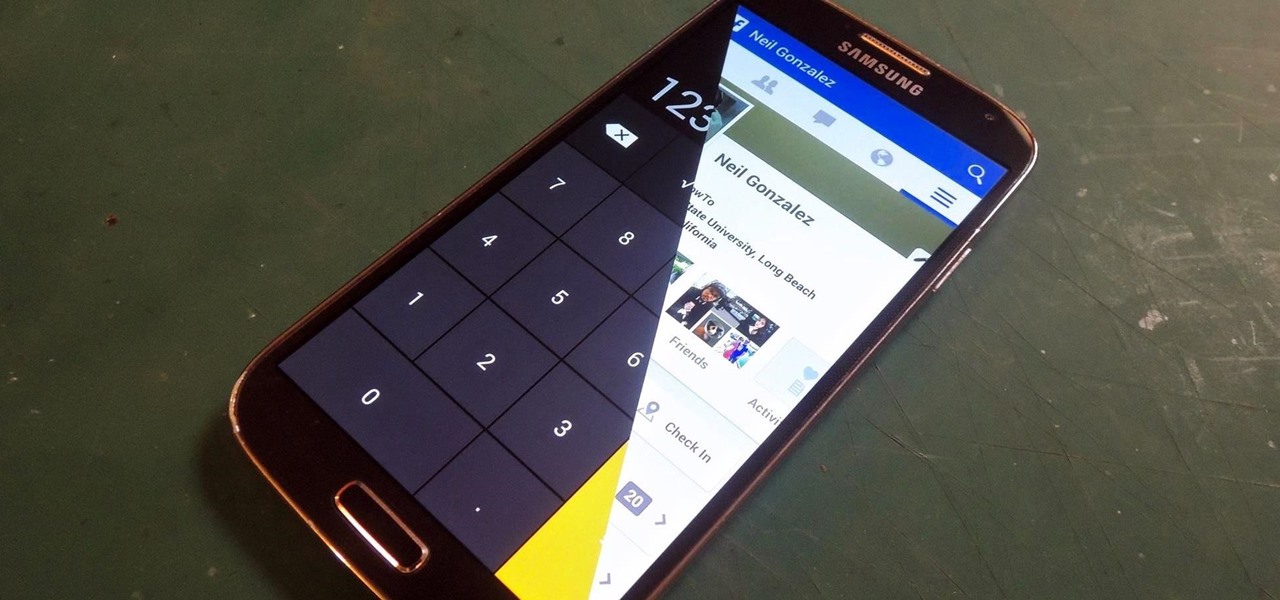
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.
This video will describe you how to hide your important files, system files and folders hidden from common users in windows 7
In this Windows 8 tutorial, you will learn how to show and hide desktop application icons. The benefit of this is it allows you to quickly hide desktop icons and show them again when you need to have access via desktop.

The villain Scarecrow reappears in Batman: Arkham City after his first appearance in Arkham Asylum. If you want to find a hidden easter egg involving him, you'll need to use your decrypter. Keep your eyes out for an invoice with a familiar name on it.

The Endor DLC that was just recently released for Star Wars: Force Unleased has three holocrons hidden! This tutorial shows you where each of these collectibles are, including the one in the indoor station that can be tricky to find.

The 1991 Suzuki Sidekick is quite vintage at this point, and they're fun little cars. If your Sidekick's check engine light is on and there's nothing wrong with the engine, use the hidden switch you'll learn about in this video to turn it off.
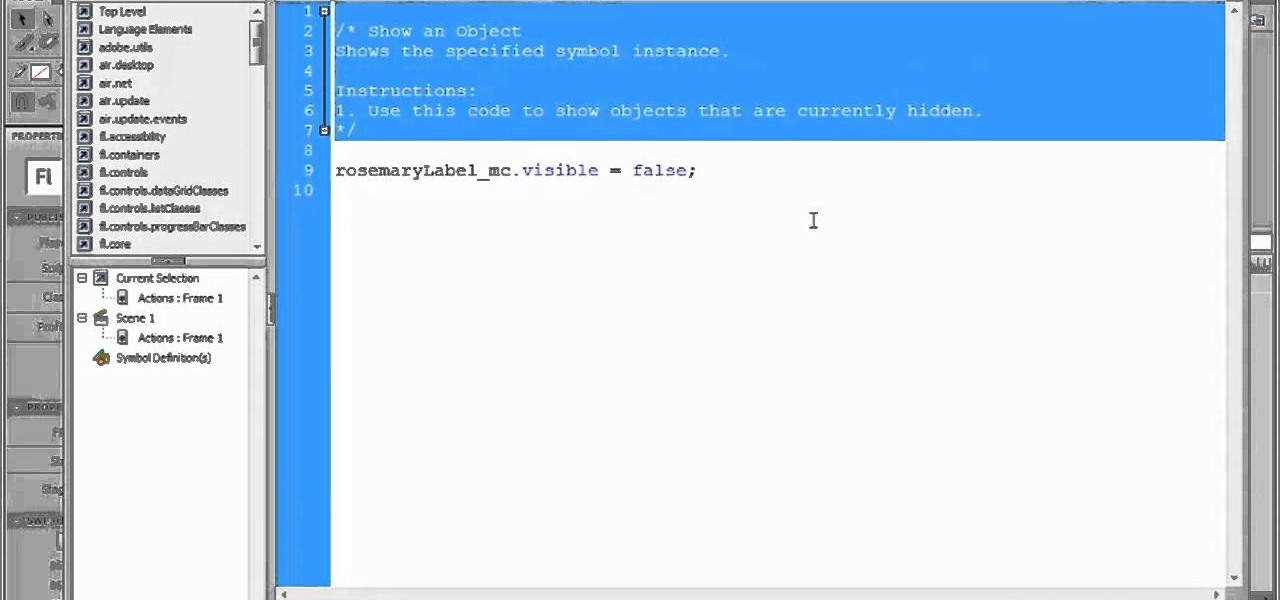
In this clip, you'll learn how to use Code Snippets to display and hide movie clips in Flash CS5.. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

Want to know how to hide the Menu and Status Bars in VirtualBox? It's easier than you'd think! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, take a look.

Cracked ukulele? Why not take a crack at its repair yourself? This tutorial demonstrates how to repair a simple cracked open seam with hot hide glue using the "percussion" technique—a method, which incidentally, will work for any wooden string instrument. For careful, step-by-step instructions, and to get started restoring your own damaged uke, watch this helpful how-to.

Here's a demo which shows a way to produce WAV sound files with TEXT using Photoshop or any photo editing software.

This episode will introduce you a cheat sheet, hidden in your necktie.

When you watch the news or a television show where someone doesn't want to be identified, it is common to see the face blurred out or obscured. In this Adobe Photoshop tutorial you will learn how to blur someone's face in an image and preserve or hide their identity. So if you are producing videos or podcasts or need to hide part of an image, this tutorial will show you how to do it in Photoshop.

This how-to video shows how you can hack a standard baseball cap into a cool invisible IR mask to hide your face from cameras anywhere, and look perfectly normal to the human eye! You have to admire a technically accomplished hacker. Now don't go out a rob a bank or anything. Watch this video tutorial and learn how to camera-proof your face with a creepy infrared mask.

Here's how to access some hidden websites at the Internet Cafe in Grand Theft Auto 4 1) Go To Internet Cafe In GTA IV

Unlock the "Closer Analysis: Hidden Intel" trophy in Call of Duty: Black Ops! This achievement is won by finding the hidden intelligence documents in Missions 1, 2 & 4.
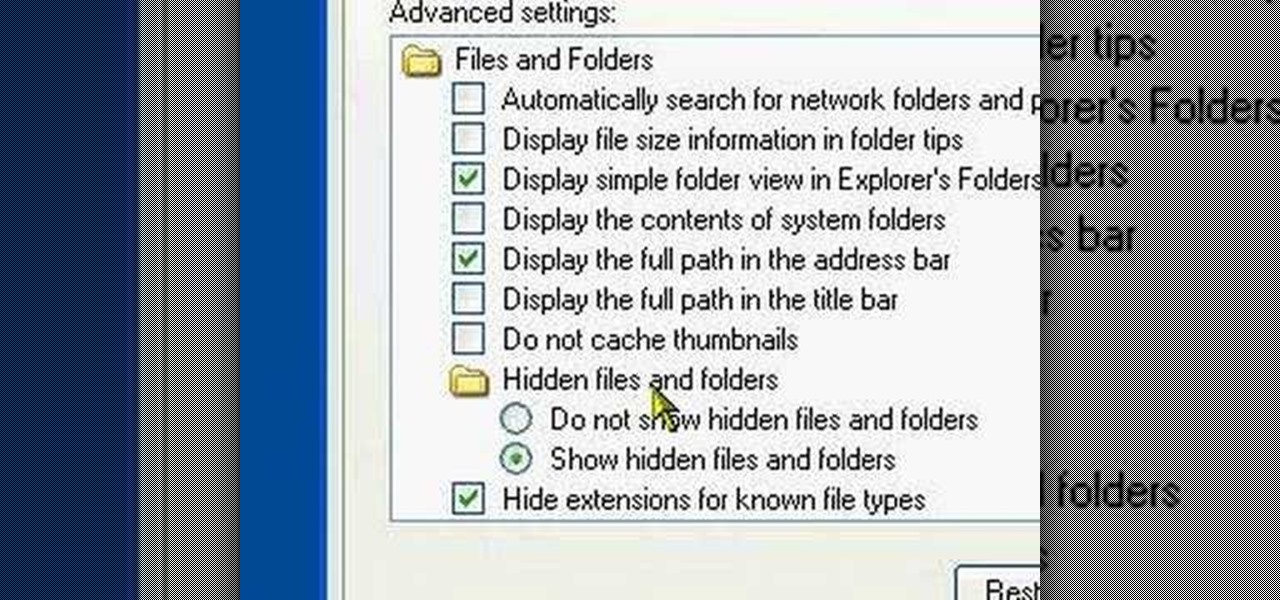
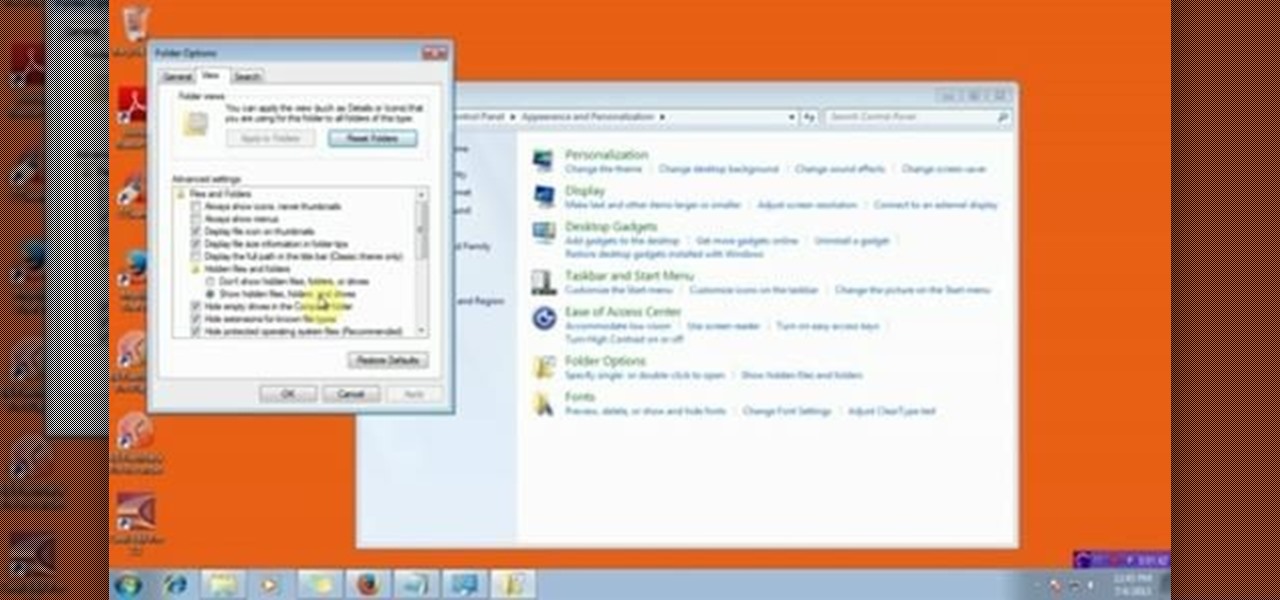
In this video tutorial, viewers learn how to view hidden files and folders in a Microsoft Windows XP or Vista computer. Begin by clicking on the Start menu and select Control Panel. Double-click on Folder Options and click on the View tab of the Folder Options window. Under Hidden files and folders, check the option that reads, Show hidden files and folders. Then click on Apply and OK. This video will benefit those viewers who use a Windows XP or Vista computer, and would like to learn how to...

Ever wanted to secretly use your iPod in class? Well now you can. A book makes for a great disguise for an iPod, and the wire can be hidden in a sleeve. Watch this video conning tutorial and learn how to hide an iPod during class in a cut-out book. One final hint: it's probably not a good idea to use a school book.

Learn how to perform simple palming techniques from this instructional video. Palming allows a magician to hide objects in the palm of their hand, while creating the illusion of having absolute nothing hidden. Watch this video magic tutorial and find out how to palm hidden objects, like coins, cards, or even poker chips, for any sort of magic trick.

Healthy, shiny hair is just an avocado away. In this tutorial, Roni Proter, host of Simply Beautiful, shows you how to make a conditioning hair mask using ingredients at home. All you need is some honey and a ripe avocado. Watch this how to video and you will have stronger, silkier hair in no time.

Watch this software tutorial video to learn how to use HijackThis to find malware hiding in the alternate data stream. This how-to video will make finding hidden malware easy and help you protect your computer.

This is a short video tutorial of the method used for body condition scoring beef cattle. Learn how to evaluate the state of cows to keep track of the weight and health of cattle livestock.

The only way to get great sound is to get the microphone as close to the talent as possible. This video tutorial will discuss the dark art of hiding a microphone in someone's clothing or elsewhere. These tips will help you keep your mics hidden and heard.

Maintaining your air conditioning can take up some of your time, but once you get it done you an save a lot of money. This how to video demonstrates how to maintain your air conditioning unit for big energy savings. You wont only be saving your bank, but you will also be saving the environment.

Watch how to build a Siberian chum from branches and reindeer hide. The BBC's Ray Mears demonstrates how to make a traditional Siberian Chum from branches and reindeer hide.
A short tutorial on how to hide icons on the Windows desktop

Jerry King teaches you how to play well despite windy conditions, by making simple adjustments to your golf swing. It's all about balance and control.

Run-in-place is another great defense drill geared at conditioning your players and increasing their overall skill on the basketball court.

Sure, all flowers look great tossed into a vase without much fuss—but if you toss them in without conditioning them first, they won't look great for long.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.
There's nothing quite like getting lost in the TikTok void. While you'll likely never run into the same video twice, the same can't be said for popular sounds and fads. Some trends get so viral, it feels like you hear the same song or track every other TikTok. Just know this: you don't have to put up with any trend you're sick of.
Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.
Let's face it — our phones are our heart and soul. We do everything on them, from banking to media consumption. However, sometimes we download apps that we don't want others to see. Sometimes, we wish to hide apps so that, in the rare times we lend our phone to someone, we don't get judged for a lifetime by what they find.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.