Does your iced coffee get watered down from adding in ice cubes? Enjoy a tastier iced coffee at home with these handy tips. Take a pot of hot coffee and pour it into an ice tray and make cubes. Whenever you want ice coffee, just pull out your coffee cubes. A secret for sugar users..put your sugar in first, then a bit of coffee, then your ice coffee cubes and a bit more coffee. Perfect ice coffee.

One of the best ways to warm up a winter meal is to serve a big platter of richly caramelized roasted vegetables. Our favorite combination is a jumble of parsnips, fennel, carrots, red or Yukon gold potatoes, whole garlic cloves and the secret ingredient -- lemon slices. The lemons caramelize and lend a brightness to the other veggies, but should be removed before serving. Cut the veggies into (mostly) uniform pieces and toss with olive oil, coarse salt, pepper and maybe a few herbs (fresh ro...

This video demonstrates how to hid your IP address on a PC.
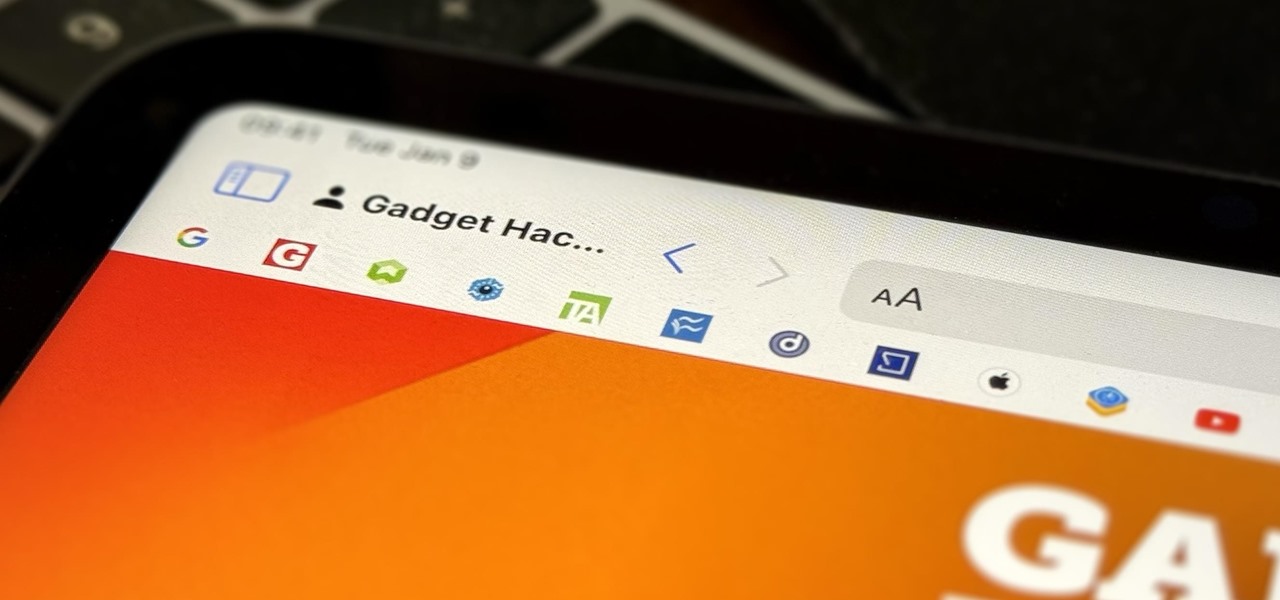
Apple has a new way to tidy up your favorite bookmarks in Safari, making them easier to access than ever before. This new feature saves space, allowing you to quickly see more of your favorites at the same time.

If you're sick of seeing some of your contacts' faces in the sharing menu every time you share photos, apps, webpages, or other content on your iPhone, or if you want to keep nearby eyes from sneaking a peek at the people you frequently share things with, you can make some or all of them disappear.

There's a world of hidden features on your iPhone just waiting to be explored, and one of them is hiding in plain sight right in front of you. You likely see it multiple times a day after performing a routine action without ever thinking twice about what else it can do, and you're not the only one.

By default, your iPhone's share sheet will have a row of contacts iOS thinks you'll want to share the content with. Those suggestions are handy if you frequently share things with the same people, but they also clutter the share sheet, invade contacts' privacy in screenshots, and tell nosy people in eyeshot who you share with the most. Thankfully, you can remove or hide them whenever needed.

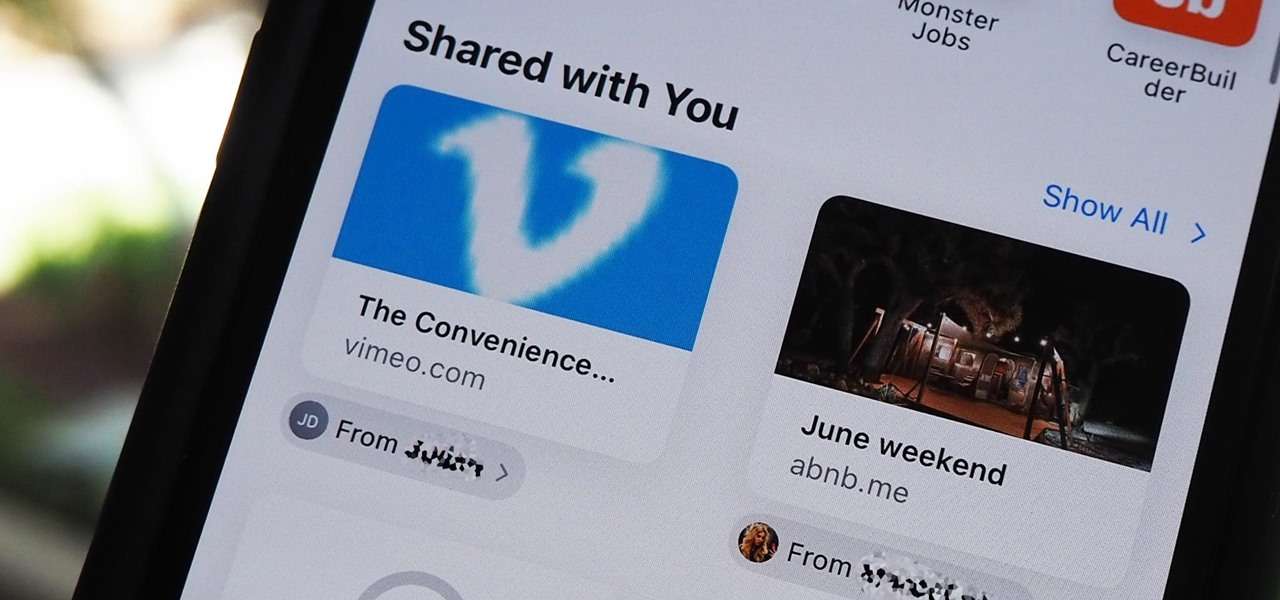
After updating to iOS 15 or iPadOS 15, you'll notice a new "Shared with You" section in certain Apple apps that contains recent shares from conversations in Messages. If you don't like seeing shared content from specific contacts or groups, there's a way to block them from Shared with You on your iPhone or iPad.

You know that you have the Gmail app on your iPhone. After all, you get Gmail notifications, you see it in the app switcher, it's in the Settings app, and there's an "Open" button in the App Store instead of "Get" or a download icon. But you cannot find the app on your Home Screen. If this situation sounds like something you're dealing with on iOS 14 or iOS 15, there's an easy answer.

People are going nuts with their iOS 14 home screens. One look on social media shows just how creative people can be with their home screen widgets and customized app icons. That said, maybe you aren't looking for a crazy setup. Maybe you're someone who wants a simple, clean home screen. Friend, this trick is for you.

If you're asking yourself where your newly installed iPhone apps are, you aren't alone. Upgrading to iOS 14 offers many beneficial features, but it also can stop new apps from appearing on your home screen. Sure, they're always in the App Library, but that shouldn't prevent you from accessing your favorite apps the old-fashioned way. The good news is that you can make iOS set things back to normal.

These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

The ability to hide entire pages on your iPhone's home screen is an excellent privacy upgrade packed into iOS 14. That said, it can be a bit of a pain to find and open the hidden apps on those pages in a timely fashion. Luckily, iOS 14 has a solution that makes opening those apps, as well as any others, faster and more convenient — and we're not talking about the new App Library.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

In many places, May has given way to a surplus of strawberries cluttering the produce aisle. These sweet berries are great in a wide variety of delicious baked goods, from pies to cakes and everything in between.

If your iPhone has a Home button, such as either iPhone SE model, old or new, then it has a secret triple-click gesture to activate a suite of shortcuts. These options, dubbed accessibility shortcuts, can work wonders for folks that are hearing impaired, have limited use of their hands, or have vision problems. Still, the shortcuts have plenty of everyday applications that everyone should know.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Whites are the hardest color to keep looking bright and new after just a few months' time. Your sweat and oils quickly become stains, and colors from other clothes will eventually bleed into the fabric, discoloring your bright whites into something merely whitish. But before you reach for the bleach, the ultimate chemical cleaner, try some a few of these safer, less-toxic DIY solutions out instead.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

Dropbox lets you store anywhere from 2 GB to 18 GB of data for free, but if you want more cloud storage you're going to have to pay. Even if you do, Dropbox only gives you 500 GB for a pro membership. So how do you get more cloud storage without paying a dime? Start using Flickr.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

How to Hide IP from Hackers. Hide your IP address to get more security. Hotspot Shield (free) change your IP address and your location. To see the changes visit http://www.ip-adress.com/ before and after running program.

The Improper Behavior achievement in Dead Rising 2 demands that you spraypaint all of the 33 Zombrex posters hidden in the game. This take a lot of paint and lot of observation, and some help from this video. It will show you where each poster is, and the creator wrote up a handy guide to getting enough paint.

Homopolar motors tend to be typecast as simplistic in nature, and that's true for the most part. The bare minimum requirements are a battery, conductor, and magnetic field, but when it comes to Valentine's Day, they're nothing short of complex.

In order to perform the ultimate transportation two card trick, you will need the following: 2 jokers, 2 contrasting cards, the remainder of the deck of cards, and a flat surface.

Weddings are very expensive and one way to say a little is to make or have you maid of honor make the wedding bouquet and the bridesmaids’ bouquets. You need a straight handle bridal bouquet holder and a stand to hold the bouquet holder in place while you work on it. You will need 12 roses fully hydrated and open.

This video tutorial will show you how to apply four styles of lighting. This video teaches you how to apply four styles of lighting, namely Rembrandt, Beauty, Cameo and filling in from the Key Side. You will learn about high contrast lighting schemes, dealing with the amount of contrast used to highlight a person's face, as well as spotlight effects, and how these tend to draw the viewer into the scene. You will be shown how the Rembrandt Lighting setup contains three steps, namely taking a K...

This is a slight of hand magic trick. You show four cards. The top card is a Queen of Spades. Place the Queen of Spades on the table. The bottom card is a Queen of Hearts. Shake the cards. The four cards are now Aces. To do this trick, you need a gimmick card. Use double stick tape to attach the Ace and Queen together. Then, you have another Queen and three Aces. Put double stick tape on back of Queen. Now, you have Ace, Ace, Queen, Ace. Put double stick tape in the middle of Queen of Hearts....

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.