Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.
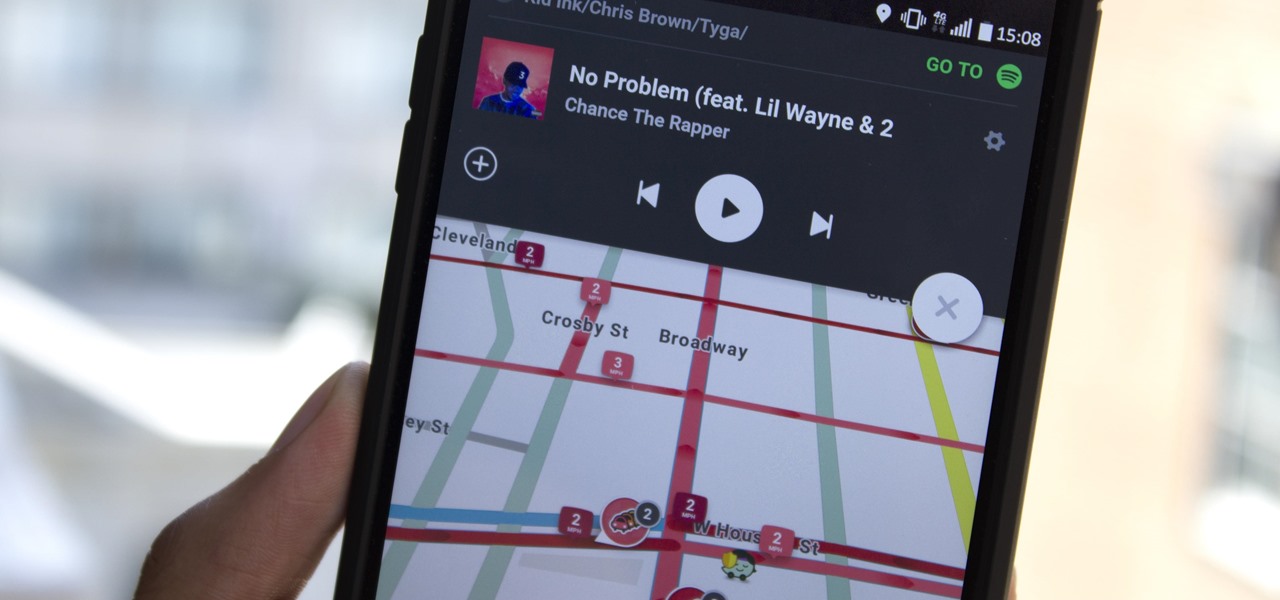
Who doesn't love listening to music or playlists when driving? The open road and an awesome playlist make for a perfect pairing, but it can become quite the challenge if you're trying to navigate at the same time. That's why Waze's built-in audio controls for compatible apps like Spotify and Pandora are so useful, so you can always keep your eyes on the map and road ahead of you.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, even without root access.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

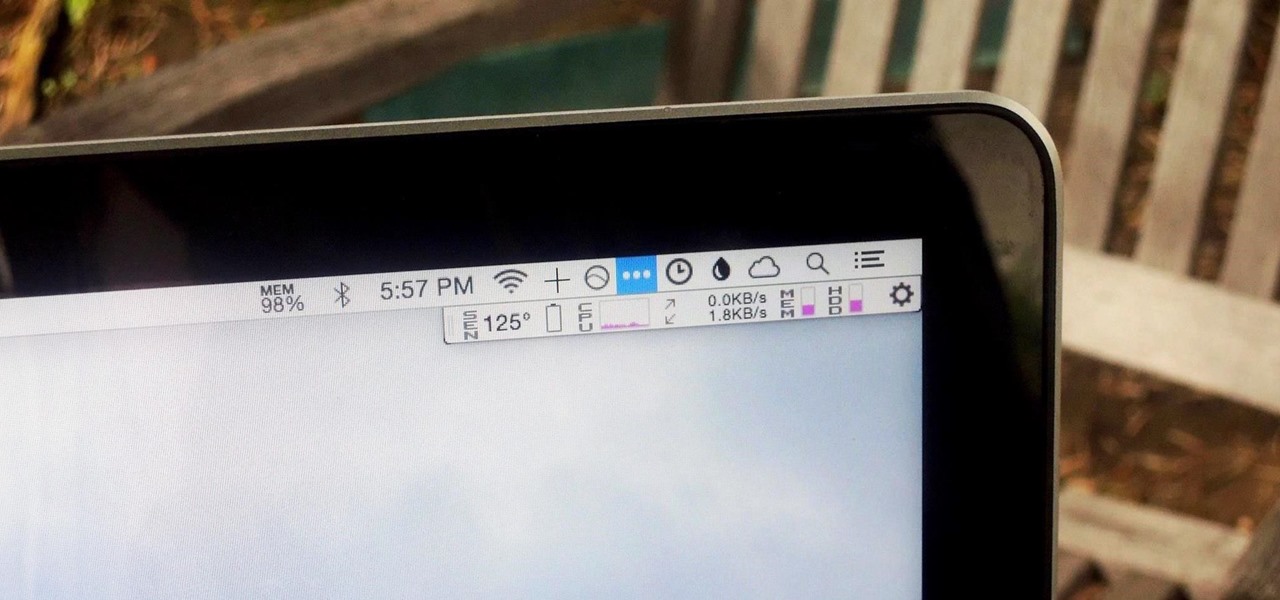
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

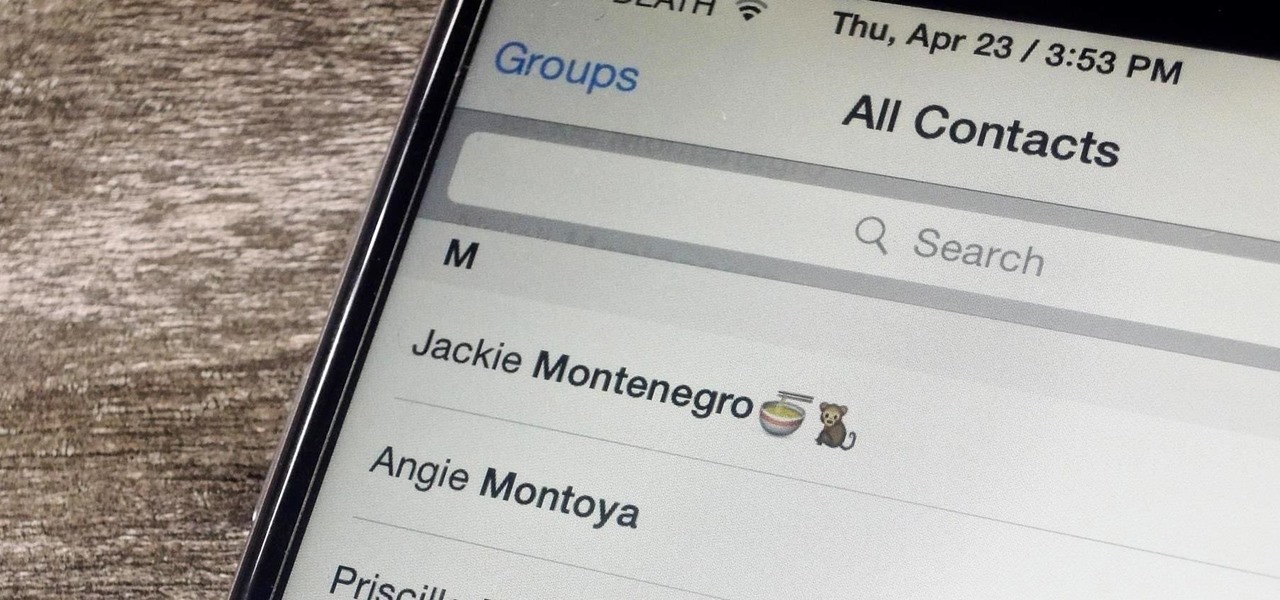
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

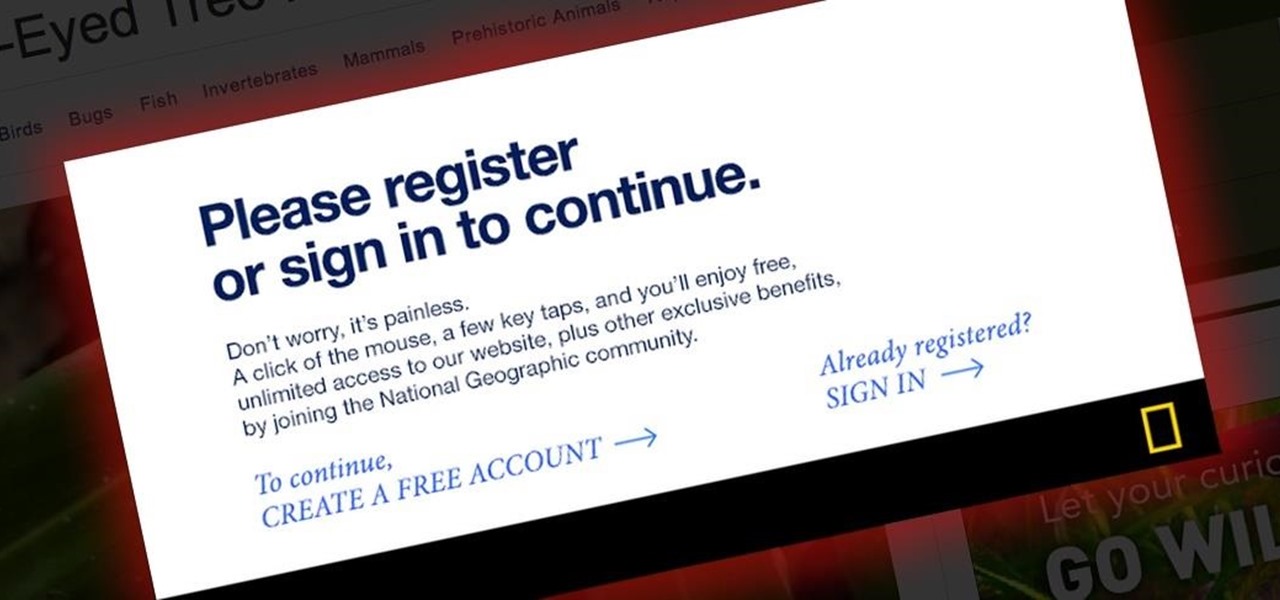
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Like many other smartphones these days, your Samsung Galaxy S4 is built to handle multitasking like a pro. With a 1.9 GHz processor and 2 GB of RAM (specs comparable to laptop computers just a few years ago), this powerhouse of a phone can switch between apps with supreme ease.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.

Dropbox lets you store anywhere from 2 GB to 18 GB of data for free, but if you want more cloud storage you're going to have to pay. Even if you do, Dropbox only gives you 500 GB for a pro membership. So how do you get more cloud storage without paying a dime? Start using Flickr.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

You hunt and you hunt, but you can never find the right pillows to go with you couch. Even your reupholstered chair needs a little pillow love, but it seems impossible to find the right color and design to make a perfect match. That's when you know it's up to you save the day. Why settle for simple decor when you can make your own chic throw pillow to match any room?

If you want to draw full body manga characters you need to make sure you know how to draw legs. First you should draw hid lines in a box and then connect legs. Make sure you have a gap for the legs and that the legs as even. Draw two circles for the buttocks and then draw legs coming down with a space in between them. Make sure you draw circles to distinguish the ankle and the knee joint. Measure out the leg to make sure the knee to hip and knee to ankle are approximately even. If you want to...

Using this tutorial, you will learn how to make a comic book style cloud in Adobe Illustrator. 1. First, select the ellipsis tool and draw a few shapes. 2. After drawing some shapes, select them and go to window and choose pathfinder. 3. Click to merge the shapes together. 4. Next, go to the layers window. Choose layer 3 and highlight the compound shape. Then select duplicate compound shape. After create one more duplicate. 5. Hide the first duplicate layer and choose the third one. Change th...

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

Watchout! Snowballs! You’re outside. You’re getting pummeled with snowballs. Time to build a snow fort and set-up teams... The snow war is on!

Get out your army pants and prepare to conquer your backyard. Learn how to play Capture the Flag with this video

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Check out this episode of Scam School from Brian Brushwood and Revision3 to see how to trick people to get free drinks with the ladies.

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

Big ears are no laughing matter, unless your a ten thousand pound elephant and your name is Dumbo. So, how can you keep your larger than life ears a secret? One answer is surgery, but that's one of the worst ideas ever. The easiest and cheapest way to hide those flaps is by simply styling your hair the right way. Camouflage your big ears behind a new hairstyle and you’ll be confident once again.

Learn the basics of drawing stick figure cartoons with this video tutorial. You need just some drawing paper, a pencil and some imagination for this!