While change is good, it isn't always welcomed. All software updates with radical redesigns and brand-new features bring at least a few complaints from those accustomed to previous versions. iOS 7 got a lot of flak from iOS 6 users, as did iOS 8 from iOS 7 users.
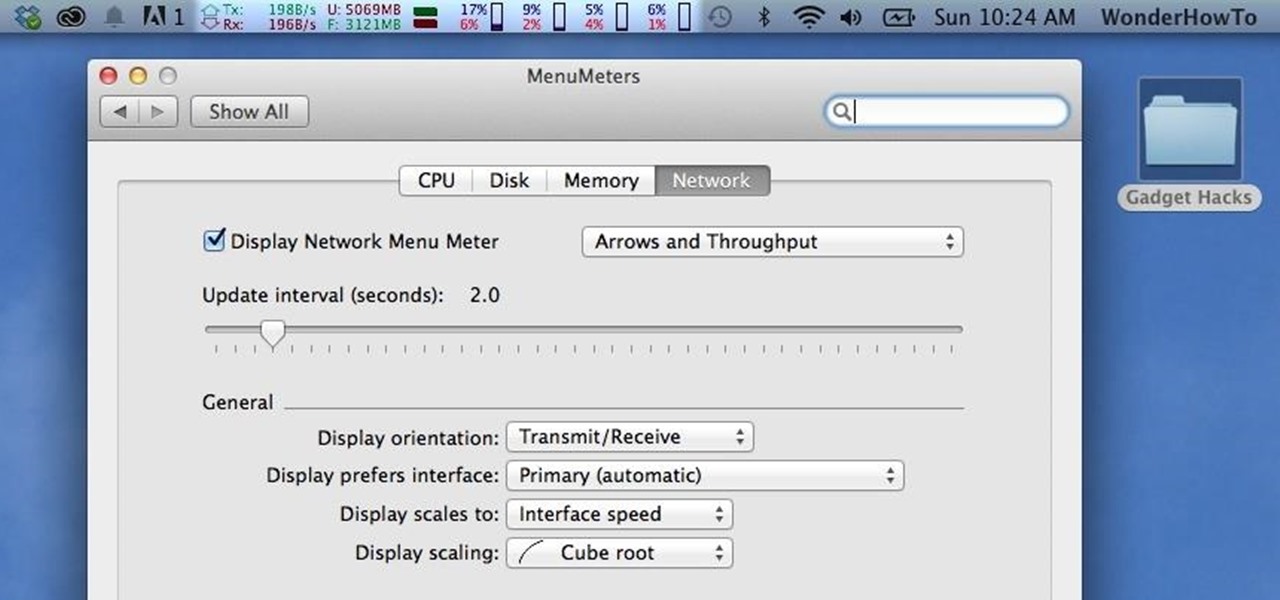
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

The internet was ablaze this week after it was found out that evasi0n's newest jailbreak for iOS 7 secretly came bundled with a highly obfuscated Chinese app store. The application, called Taig, was filled with pirated software and was rumored to have permissions capable of tracking your information and sending it elsewhere. It was reported that the team at evad3rs financially benefited from this move, netting them a very high six-figure number close to a million dollars. The controversy incr...

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

In 1958, Patrick Flanagan invented the Neurophone, a device patented in 1962 that allows radio signals to be picked up by the human nervous system. The skin is the organ that receives the signal, converting it into a modulated molecular vibration, which the brain interprets into sound. Basically, it gives one the ability to 'hear' through the skin, making it sound like the audio you're hearing is actually in your head. It's kind of like having headphones in your brain. The only problem was th...

Three disparate but useful indie filmmaking techniques, one video. One stop shopping just in time for the holidays. This video will teach you how to make day into night with editing, normal things giant with filming, and make actors fall from high places without hurting themselves unduly.

Watch this amazing USB Bluetooth adapter hack from Kipkay. It's easy and effective, plus it will work with other wireless devices, too. Bluetooth works on a 2.4GHz short wavelength radio frequency, but it's only effective over short distances. Well, Kipkay's going to show you how to increase the range by swapping out the antenna in the bluetooth adapter with a HyperGain 2.4GHz high performance antenna.

When it comes to earning high scores in a web game like Crazy Taxi or Crazy Cabbie, sure, you could, like, actually play it — but where's the fun in that? Cheat your way to the top with this hacker's how-to.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to make high quality audio/video cables.

Learn how to do a slim-chance with Flysurfer teamrider Mathias Wichmann. This trick is extremely hard and looks awesome. It's technically advanced.

You know YouTube is able to host high-defintion video content online now, right? Well, how do you watch it, or make it, or embed it? Well, this video tutorial will show you how to upload, embed and watch 720p HD video on YouTube. This YouTube hack will let you watch and embed videos in true 1280x720 high definition.

High waists and poofy balloon skirts are both two of the hottest fashion trends this season, seen on stars like Lauren Conrad and Jessica Simpson (yes, of the famous "Mom jean" snafu).

Here's a great summertime treat that won't have you cheatng on your diet. This healthy alternative ice cream is low in fat, high in protien, low in carbs, and is still pretty good. This video will demonstrate exactly how to make high protien low fat, ice-cream.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

There are two ways to properly lock your seat belt. You can use the childlock auto adhjustment. Or you can recline the seat, but then push forward to make your seat belt very tight. You don't want to be flopping around in the car. The bottom of your wrist is on top of the steering wheel and your shoulder is in the seat. It will loosen up when you get on the track.

Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

In this tutorial, we learn how to use AV mode & High Speed Sync (flash). First, go to AV mode and change the settings to 2.8. When you do this, your shutter speed will blink at 250. To fix this, hit the lightning bolt with the "h" and change it to the high speed setting. Now, your camera will be able to use the high speed shutter with the flash as well. Now, take some shots of your subject in the sun and you should be able to see a huge difference. The background should come in crystal clear ...

Cory teaches us how to do a high pitched scream in this video tutorial. This is the same as a low scream, just higher in pitch. The first this to do is to let out a lot of air when you are using a high pitched scream. This is the opposite of what you would do for a low pitch yell. The next thing to do is to position your tongue in your mouth. The tongue should be up to the front of your mouth touching your bottom teeth. The last thing to remember is to use a different spot in your throat, fin...

Watch this video to learn how to burn fat doing cardio. A step by step video tutorial that will guide you through some basic instructions to help you burn fat doing high intensity interval training. Yuri Elkaim from MyTreadmillTrainer presents a very informative lesson on how high intensity training burns fat. He explains the difference between high intensity training and long cardio. Long cardio encourages you to take your time and, for example, go on a 1 to 2 hour slow bike ride. High inten...

Personal fitness coach Yuri Elkaim demonstrates how to do high intensity interval training for beginners on treadmills. Start out with a light walk on a treadmill for about three to five minutes. From a walk, do a low grade jog for 30 seconds. Then, switch to a minute and a half of walking. Use a three to one ratio of low intensity to high intensity workout. As the workout progresses, it will get more challenging. Repeat the workout interval repetitions for 10 to 15 minutes. The interval work...

Fashion Demonstrator offers a short tutorial on how to prepare your self for a night out in high heels. First you start by wearing a pair of heels all day around the house, higher then ones you intend to wear later. This is to get your feet used to the feel and your self used to the balance. Then when you are ready, you switch to the pair of heels, with a still high but slightly lower heel then before, that you intent to wear out. The idea is that since you have spent the day in very high and...