Many of your cars engines critical components are driven by belts. Belts operate in tough conditions, such as high heat, high speed, and are under considerable tension. Since rubber is an unpredictable material, even under ideal conditions, belt failure is one of the most common causes of auto breakdowns on the road. Vehicle belts are easy to check, like serpentine, drive, and multi rib belts, and to replace them at home is relatively easy and inexpensive. This is the best way to take care of...

This is a short video describing where to place a capo on a standard tuned guitar to make it playable in the same positions and notes as a ukulele.

Your vehicle's power steering pump is integral to your car functioning at all. That's because the power steering pump is what provides the hydraulic power for steering. Without it, your car would pretty much go nowhere. Inside the pump, retractable vanes spin, pulling hydraulic fluid in with low pressure and spitting it out at high pressure. Every pump has a pressure relief valve to make sure the pressure is never too high, but still your steering pump may wear out over time.
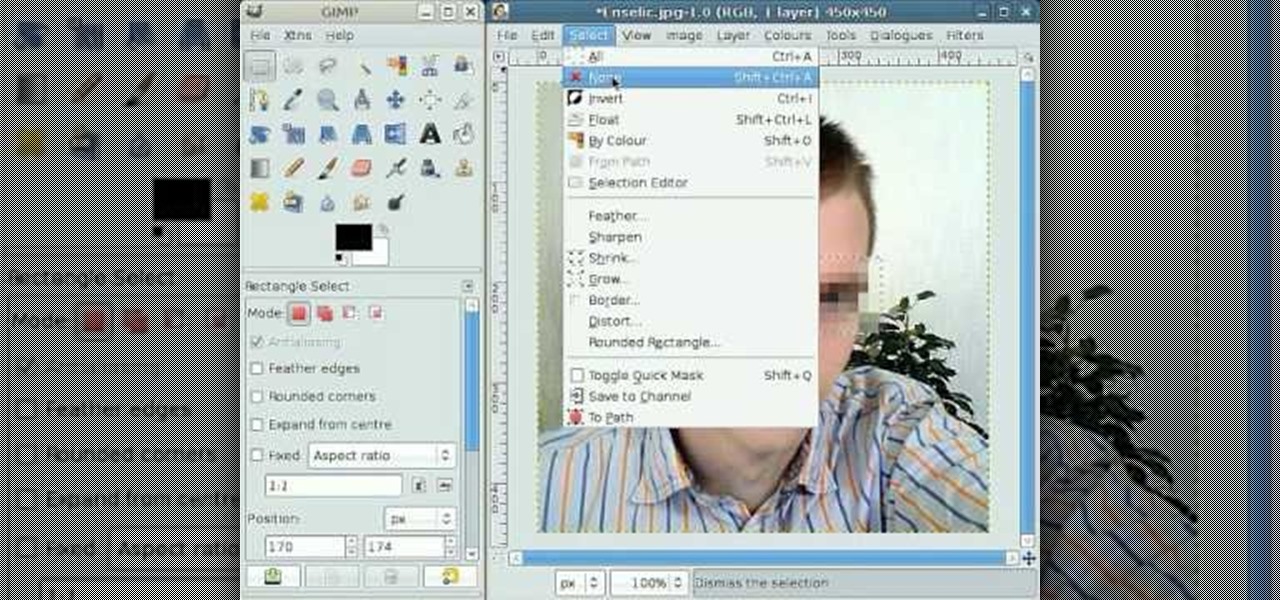
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".
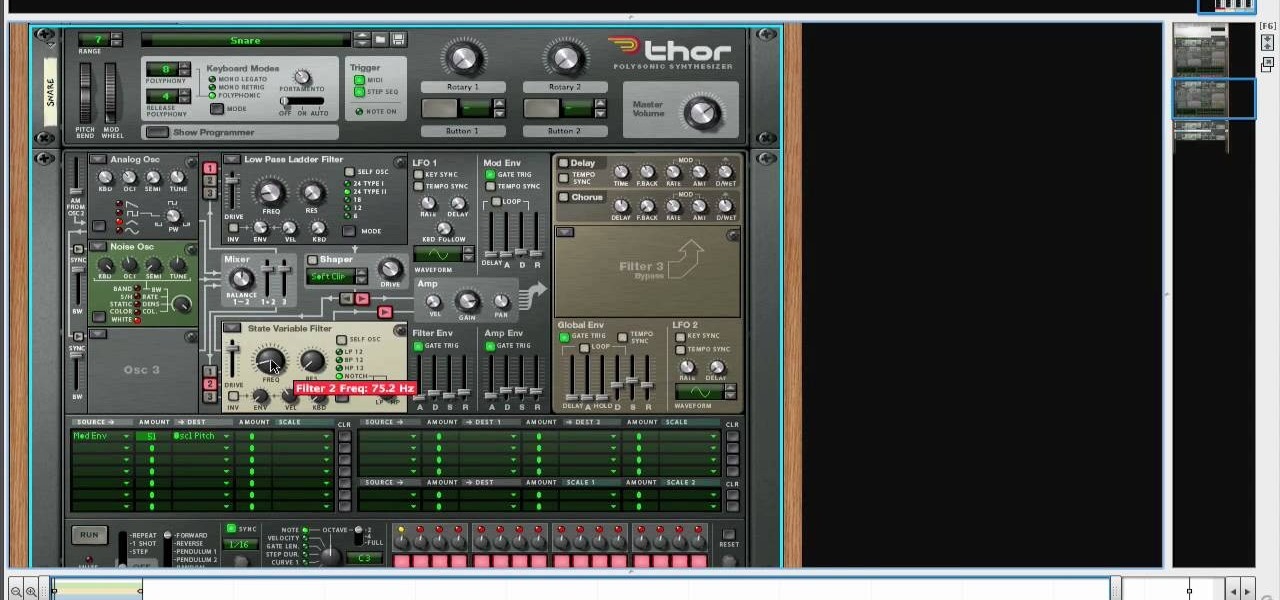
Create drums sounds using Reason's Thor synthesizerYou can use the Thor synthesizer to make a kick, snare, hat and clap sound.Kick:Use the analog oscillator with triple wave form octave3. Set the source to mod envelope 45 destination oscillator 1.Use a very short attack to K and release time. You get the short effect of pitch. Try different oscillator types to get different textures.Snare: Use the same basic patch that we created for the kick. We will keep it as the basis for most patches for...
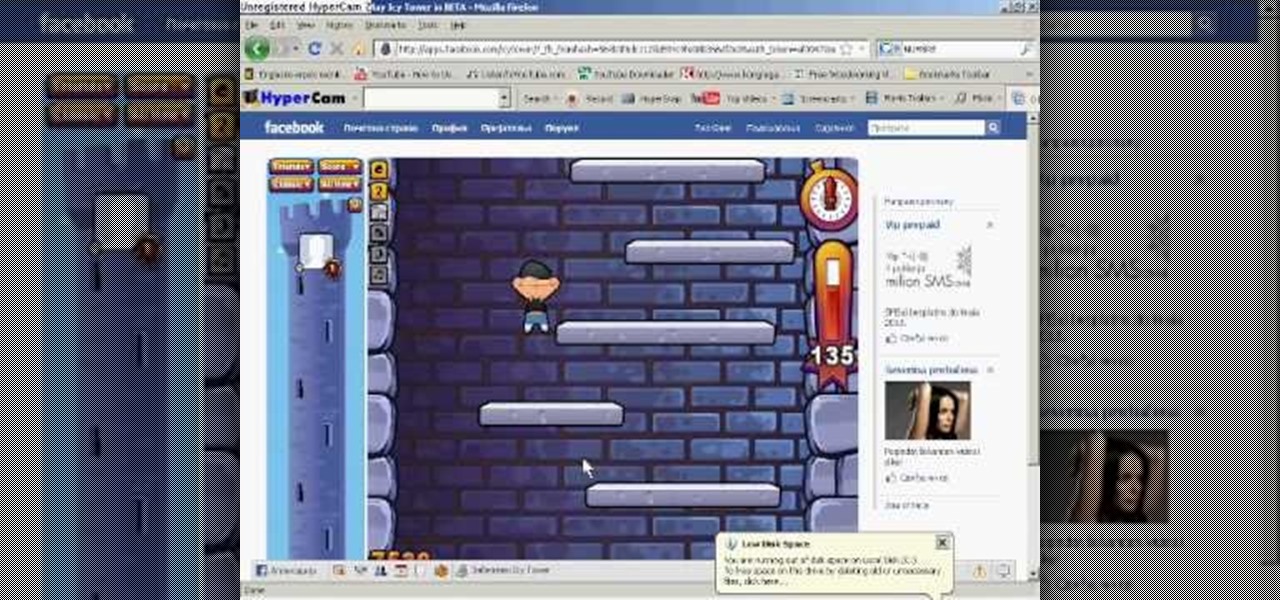
Make your Icy Tower score the highest ever. Break records. Impress friends. Rule the game! How? Cheat Engine, a simple hacking program.

These 2 videos demonstrates how to tie your Converse high tops in fun, stylish ways. For the first video, take a pair of shoes and take out the strings. Thread one string through first whole going INSIDE.

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with cheat codes (07/21/09).

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

Learn how to do power hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do triceps single-arm kickbacks. Presented by Real Jock Gay Fitness Health & Life. Benefits

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

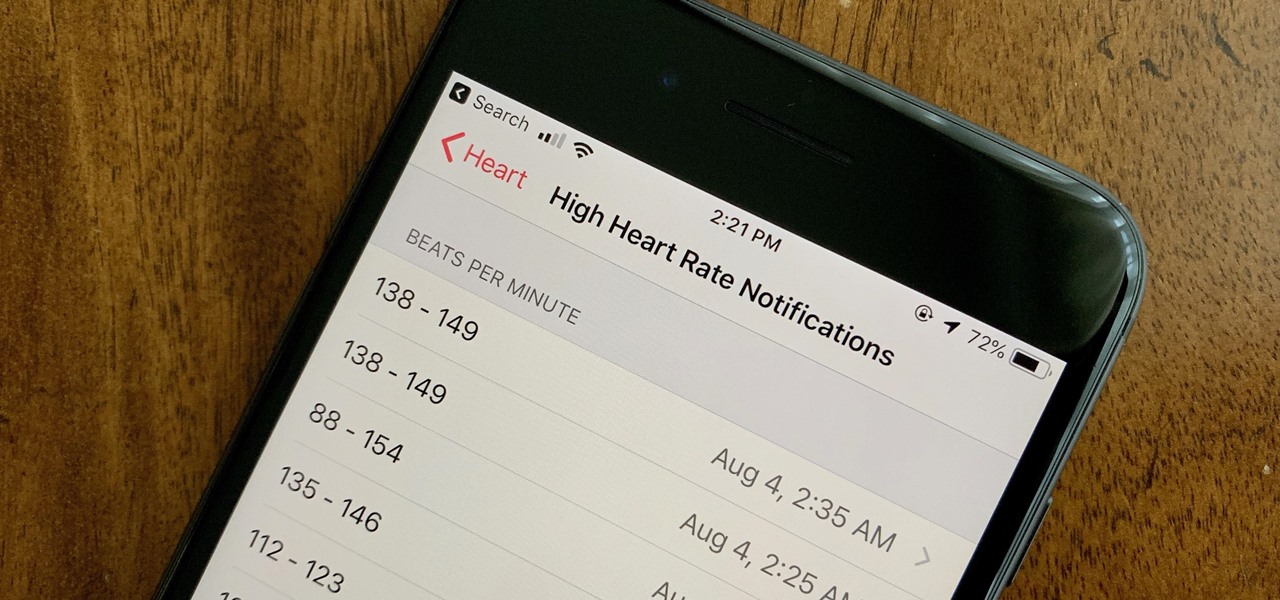
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

One of the best aspects of the Magic Leap One is the spatial audio, a feature that enhances the overall sense of immersion when interacting with virtual objects and content through the device. Now the company is aiming to boost the quality of that component by partnering with one of the leading names in high-quality audio.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

The Centers for Disease Control and Prevention (CDC) just reported some upsettingly high numbers of human papillomavirus (HPV) in adults. In data retrieved from 2013–2014, 22.7% of US adults in the 18–59 range were found to have the types of high-risk genital HPV that cause certain cancers.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Whether you love or hate wearing high heels, a pair of stilettos can be incredibly painful. You can feel blisters, searing pain, pressure, and stabbing aches long after you kick off those heels, but a really simple trick could help alleviate some of the issues caused by tight-fitting, wobbly shoes. According to Kat Collings of Who What Wear, taping your third and fourth toes (if counting away from the big toe) together with tape will reduce the amount of pain you feel in the ball of your foot...

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Depending on who you ask, the OnePlus One smartphone has so far been either a bit of a letdown or a rousing success.

When you were younger, you probably had your parents bugging you not to have your cassette player headphones up too loud. For all you younger readers out there, it was probably a CD player. The even younger readers likely had an iPod or other MP3 player. Either way, your parents didn't want you to mess up your hearing, blasting that Limp Bizkit in your ears (wow, I'm showing my age here).

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Enjoy this high energy fat burning reggaeton workout

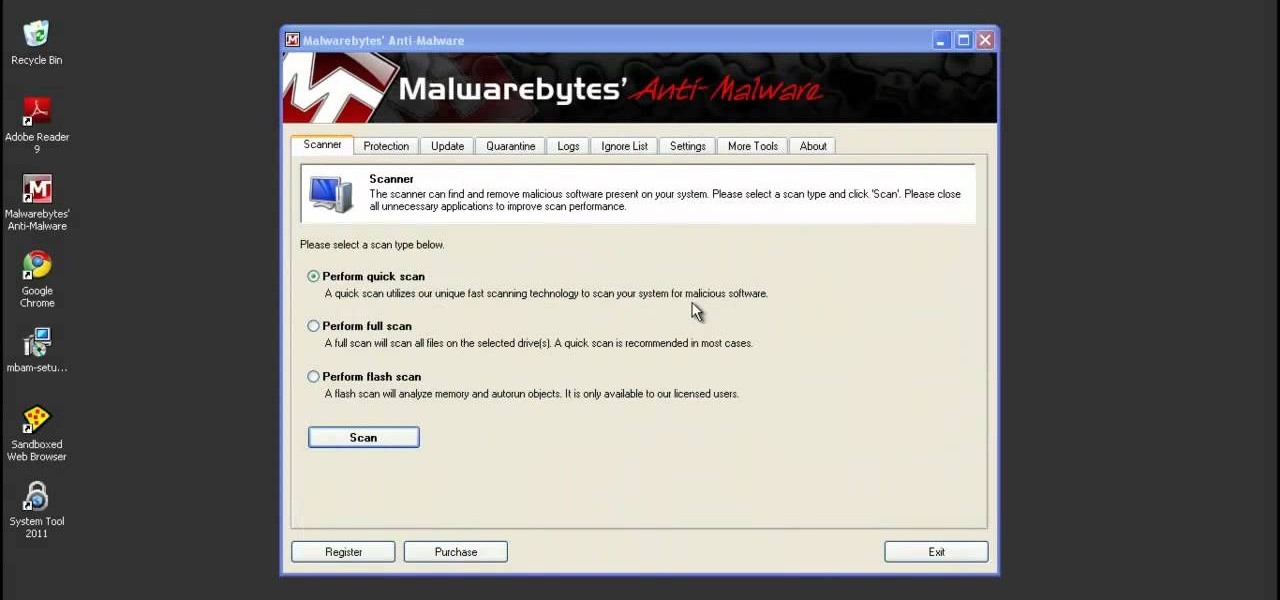
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.