Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Are you a great singer, or do you want to be an excellent singer? This 2 part video tutorial will walk you through the basics of singing high notes. The best part? You won't be gasping for air at the end of it. This is all about singing the high notes without struggling.

If you're fond of remote-controlled vehicles, you might appreciate this video tutorial on how to assemble a Traxxas high-current connector. To add a high-current connector to your Traxxas R/C model vehicle, you're going to need some pliers, wire strippers, flathead screwdriver, solder and a soldering iron. Replacing the old connector is easy, and will help give your hobby RTR (ready to run) nitro and electric model car or monster truck some life in needs.

It's not as easy to walk in high heels as you think, girls! Shoetube.tv host Stephanie Simons shows you how to own the cat walk and turn heads. Learn how to walk in high heels like a supermodel by watching this video tutorial.

How to use the Transfer Case manual lever on a 2010 Toyota 4Runner with a few easy steps: The manual transfer case offers three drive modes: two wheel drive high range, four wheel drive high range, and four wheel drive low range. Shift the transfer case from the two wheel drive high to four wheel drive high while in motion. To shift from four wheel drive high to four wheel drive low, come to a complete stop, shift the transmission into neutral and move the transfer case lever to the four whee...

This is a song from HSM3 or High School Musical 3 starring Zac Efron, Vanessa Hudgens and other Disney stars. This is an original dance to 'Now or Never' but the song is wholly Disney from HSM.

This is a demonstration of High End exercises on the saxophone. This exercise involves the last five notes on the top, starting from B up to a high F and back down. There are also different combinations. This tutorial video is great for beginners and advanced sax players. Check out this instructional sax video that shows you how to practice these high end exercises and improve your saxophone playing skills!

This fitness how-to video demonstrates proper form and technique doing a sumo dead lift high pull with a kettlebell. Sumo dead lift high pulls with kettlebells are an effective way of strength training. Follow along with this video workout to learn how to do kettlebell sumo dead lifts with high pulls.

High heels to dance in? While a high heel might seem awkward to dance in, a good rule of thumb is to go by what sort of heel you're used to using anyway. Watch this video dance tutorial and learn how to pick out a pair of high heels for Latin dance class.

In this video you will learn how to make a high voltage, high frequency power supply in just five minutes, and for less than twenty bucks. All you'll need is a compact fluorescent light (CFL) and a flyback transformer to make that alternative energy source of yours.

Check out this video to learn how to play high major chords on the fret board of a ukulele! Part 1 of 2 - How to Play high major chords on the ukelele.

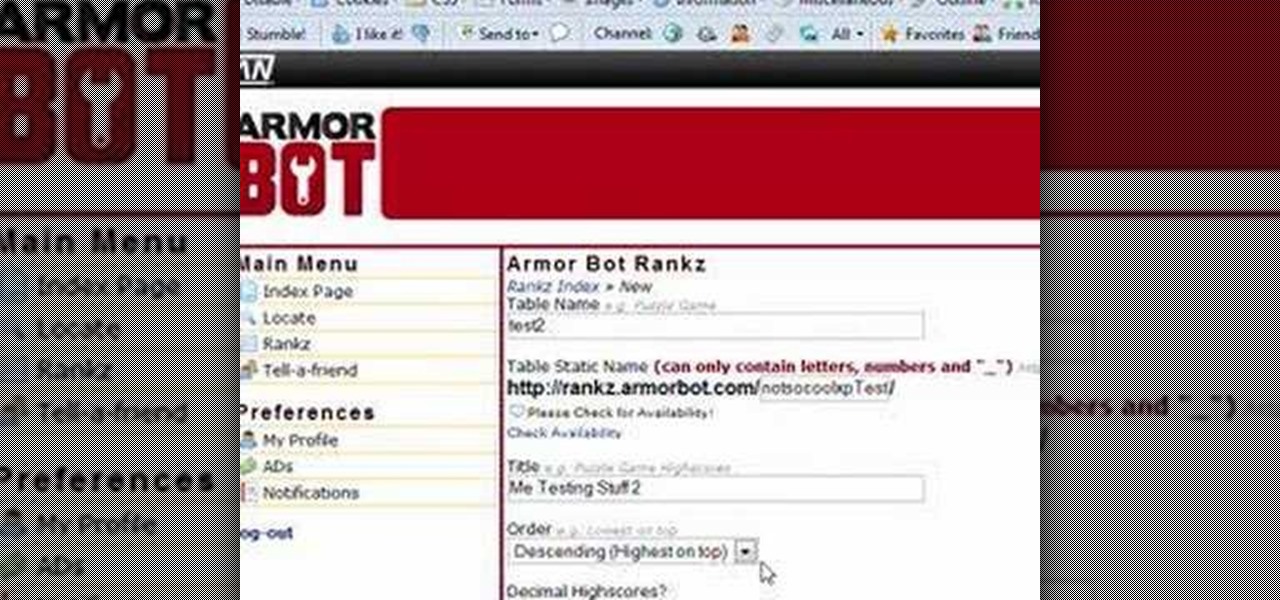
Learn how to create a high score table for Flash games using Armorbot.com Part 1 of 2 - How to Create a high score table for Flash games.

Take your desktop security to a whole new level by making your folders invisible! This video shows how you can make a folder icon disappear, so that the folder will hide in plain sight on your desktop. Use invisible folders to trick your friends!

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.

Microsoft's Kinect is gaining popularity with Xbox 360 owners, but what's really more fun? Playing games with this revolutionary hands-free gaming device or gutting the sucker to see what it's all about? We'll take the latter choice.

In this clip, you'll learn how to get started using SkyRecon's Stormshield. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to use the VSN plug-in to encrypt email in Microsoft Outlook. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

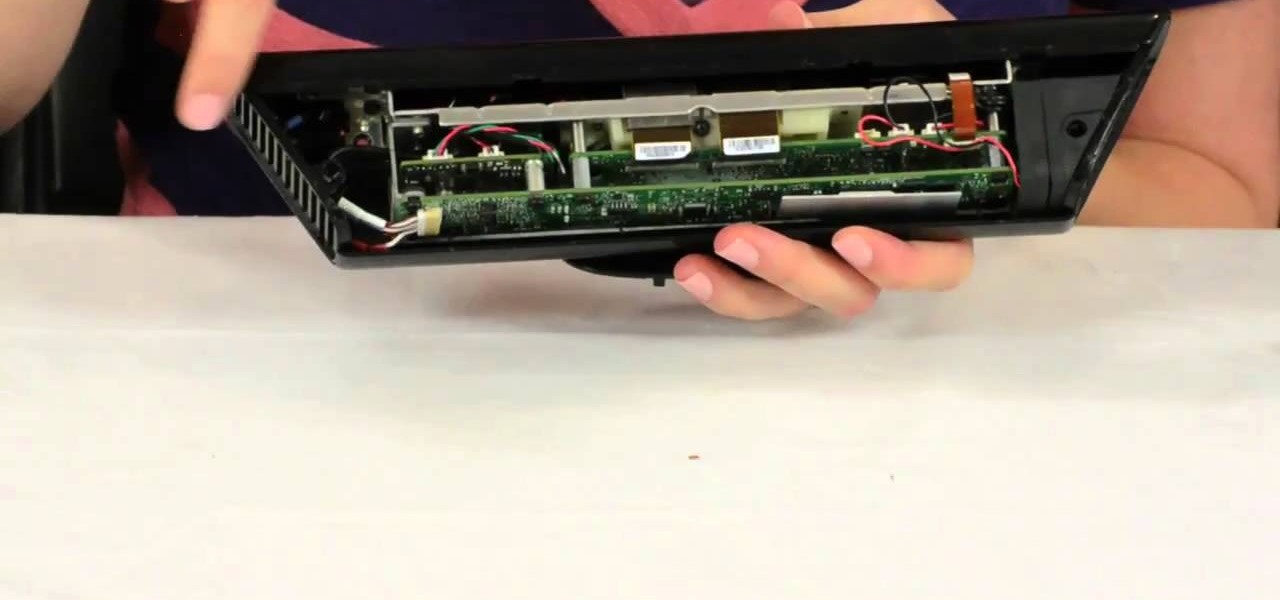
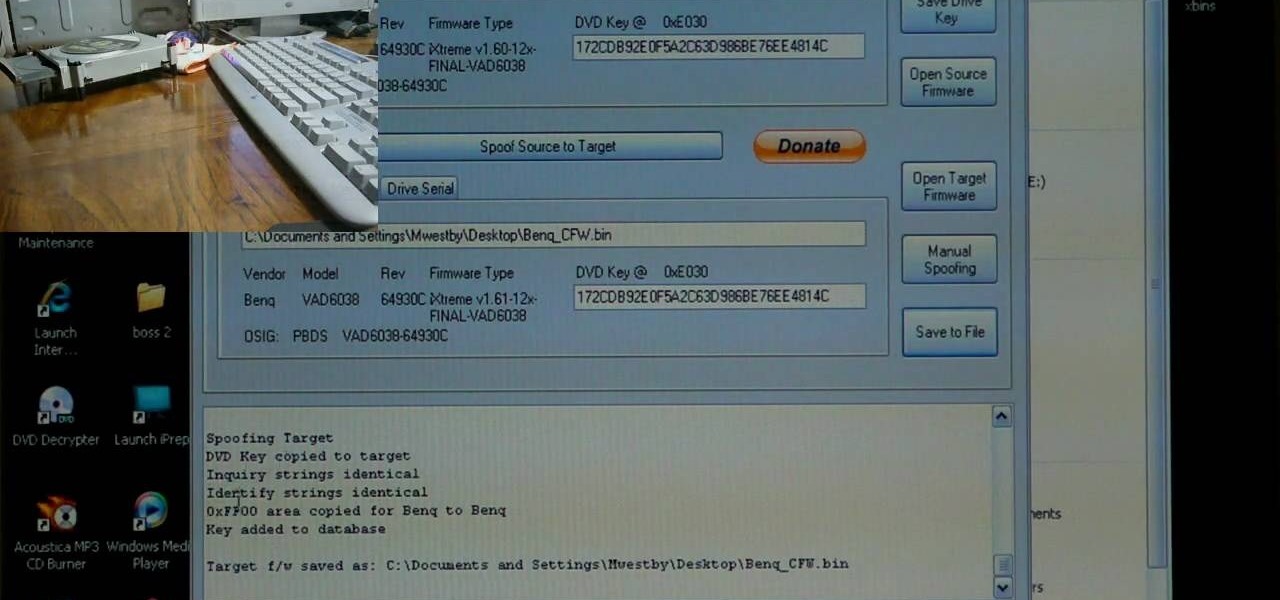
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

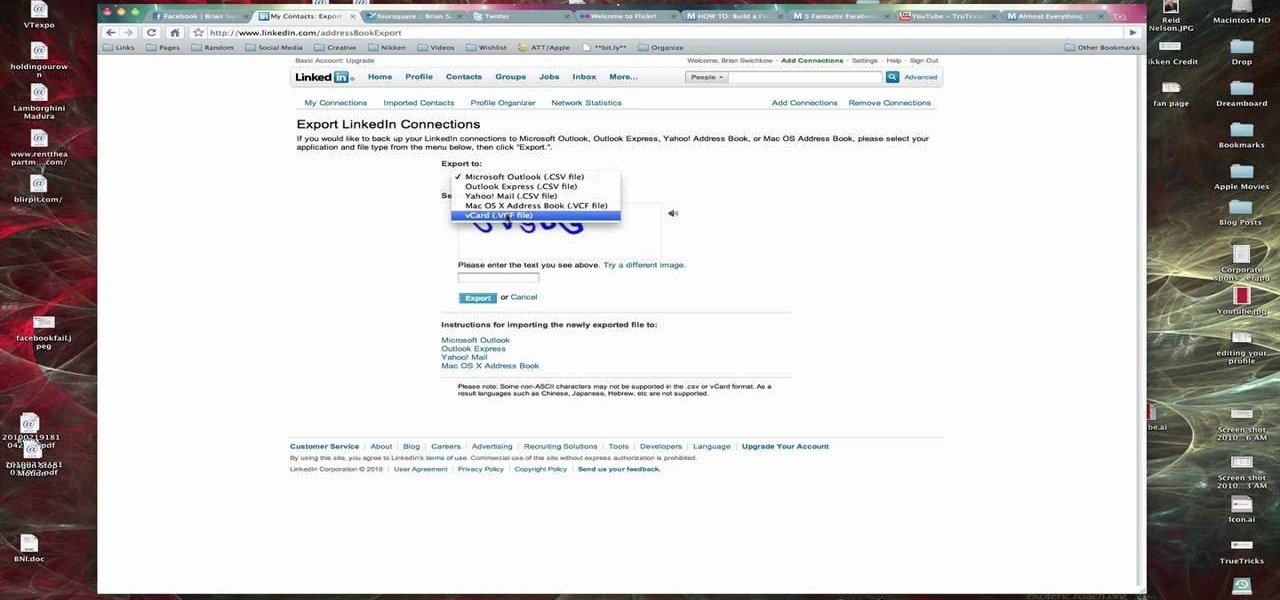
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

Installing a peephole in your home's front door can give you and your family a sense of security knowing who comes to your door before they enter. In this video Barbara K will show us exactly how to install a peephole on your door.

When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

The spy camera shown in this how-to video has a 60 foot cable, and is full color and has audio. This spy cam can be used as a security device, or to feed paranoid delusions or stalking urges. Watch this video tutorial and learn how to set up an X10 spy camera.

Installing a home security system can be expensive, but it doesn't have to be. This how to video shows you some easy practices that keep your home well protected. All you need is a few inexpensive items such as flood lights, signs, and light timers.

Your home security systems may not work for you if you don't turn it on. To top it off some of your bad habits can invite thieves in to your home. This how to video reviews some common sense steps to protect your home from burglars.