How To: Secure the WRT54G and a default password list
This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.


This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.
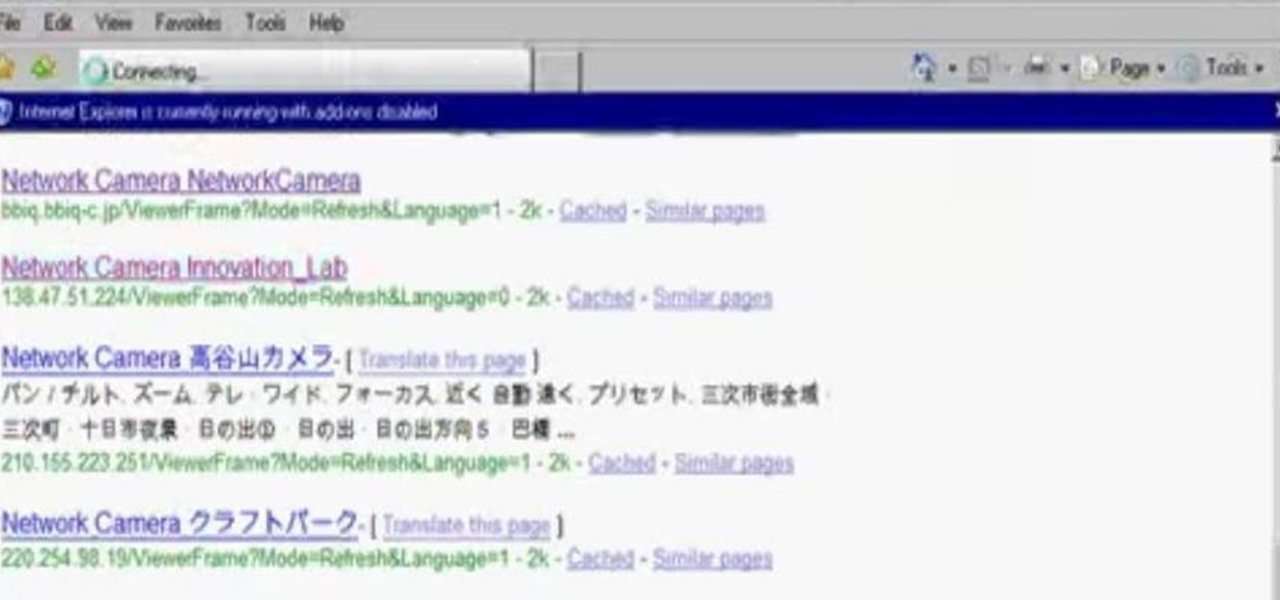
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Welcome back, my rookie hackers!
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.
This video will guide you how to blur faces in YouTube video. Many times it’s needed to blur the faces of people in videos. In many sensitive cases faces are blur due to security or confidentiality reasons.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

A high waisted skirt is one of the most flattering skirts you can wear. Because it's cinched in directly at the smallest part of your midsection - your waist - you automatically get an hourglass figure silhouette.
Need some high quality images to work on? High resolution images are those that are at least 300 dpi (dots per inch)... In layman's terms, high quality. When an image is less than 300 dpi, you will notice a loss in quality and an add-in of pixelation when printed.

Explanation of the "540 kick", a 360° spinning kick landed on the kicking leg. This high jumping, high kicking move will surely impress.

Learn how to do high speed photography with Bre Pettis. To do high speed photography correctly, you need to link a strobe to your camera as shown by Mr. Pettis of Make Magazine. Then you can create cool pictures just like him.

A dowager bun may not sound familiar to you, but you've probably seen more than a handful at fancy holiday parties and soirees. Dowagers are the widows of deceased landholder husbands. But while this is the grim origin of dowagers and "uptight" and high dowager buns, today the dowager bun is more an elegant statement than anything else.

You can take high resolution photos with just about any digital SLR, but whether these high resolution photos turn out impressive depends on setting, lighting, and the compliance of your subjects to pose. While photographing your friends and family in everyday life has these aforementioned conditions already set for you, if you take photos in the studio many factors can be adjusted to your liking.

Professional quality, high definition video cameras are now getting within the grasp of independent film makers, and this tutorial shows you how you can use the Flip camera, or other small HD cameras, to shoot your own high quality projects.

Knee high socks are totally school girl chic and help warm up your legs on a cool fall day when you want to stay toasty while looking fashionable. But if you've ever walked around a shopping center for more than half an hour with your knee highs on, you know that they've now quickly turned into mid-calf socks.

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

Most rear derailleurs (read: not Shimano) are high-normal, which means that they shift into the highest gear on the bike by default. This video features a professional bike mechanic walking you through the process of adjusting the rear derailleur and its cables into a high-normal setting, ensuring crisp shifting and a more successful ride.

Not sure how to enable javascript on your computer? Follow these steps to enable all the functionality javascript provides.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

High heels can be tricky to walk in, but they make you legs look great. It's the price you pay for looking hot. Here's how to put your sexiest foot forward—without toppling over. Watch this video fashion tutorial and learn how to walk in high heels.

This how-to video shows the basics of the high jump. The high jump is a hard sport to master, and takes perfect form. Keep practicing and have fun.

So how does a card counter keep track of the cards in blackjack? While there are many different systems and variations, counting cards is usually as simple as adding and subtracting the number 1. Subtract one when a high card is dealt and add one when a low card is dealt. The greater the count, the more high cards in the shoe, and the more high cards in the deck, the greater the counting edge for the player.

This is a great video clip series that will follow every aspect of how to punt better in football. Our expert will walk you through everything from catching the deep snap to how to properly drop the ball and how to get more distance on your kicks.
Apple just released iOS 14.4.1 for iPhone today, Monday, Mar. 8. The event marks 41 days since Apple released a public update for iPhones, with iOS 14.4 back on Jan. 26.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.
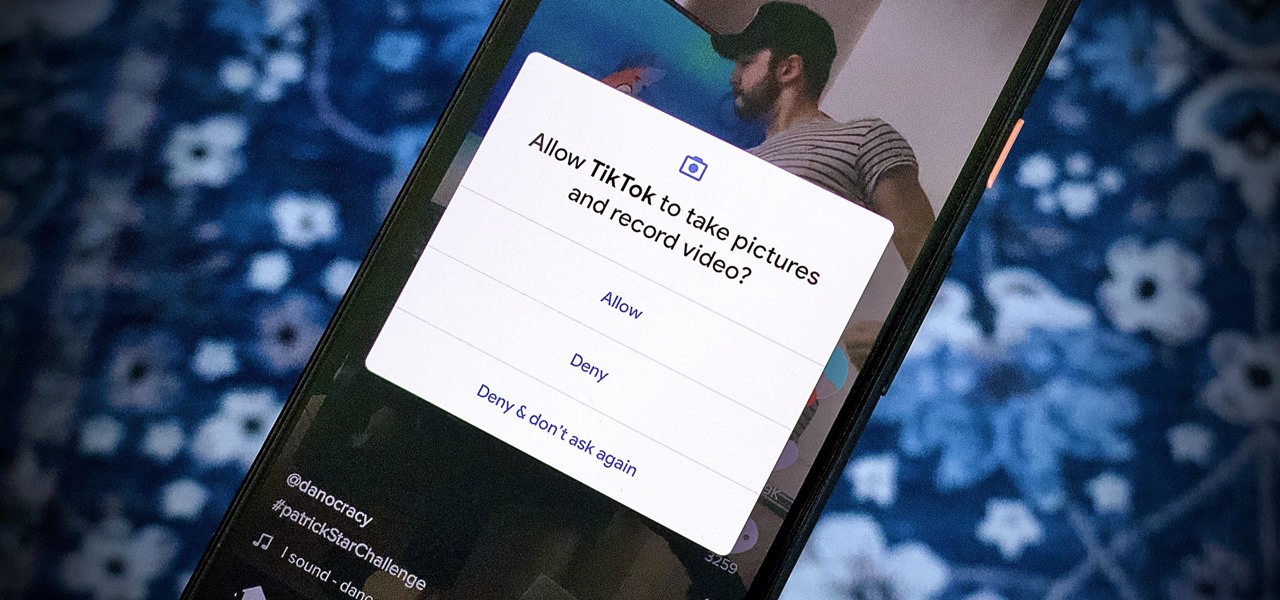
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.
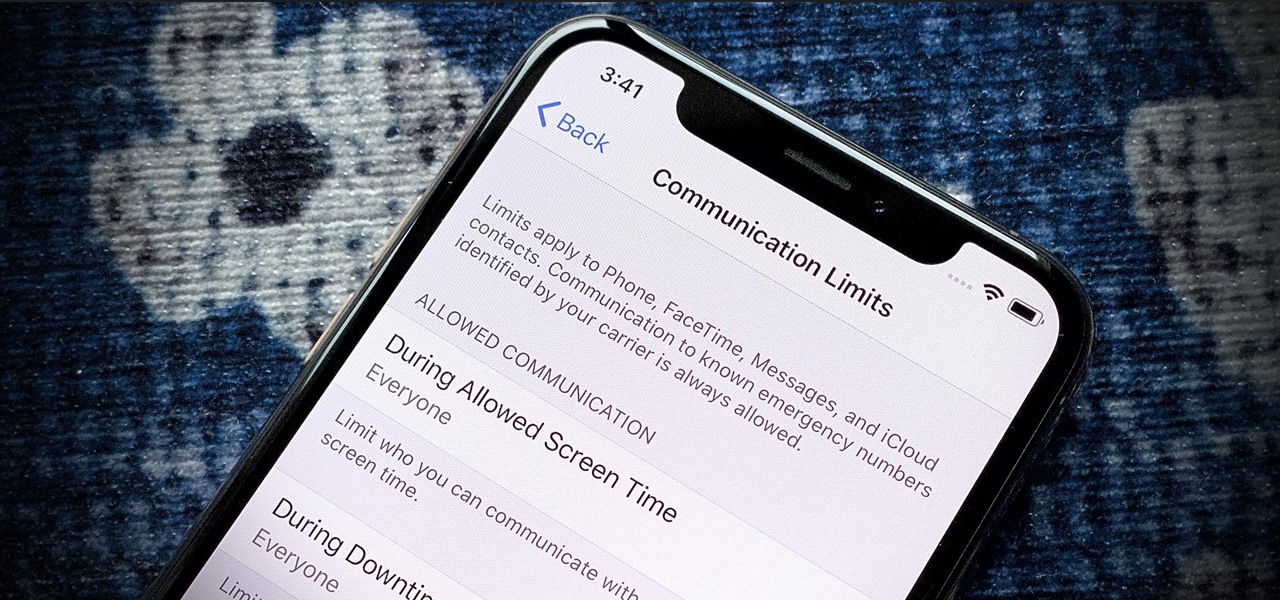
Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.
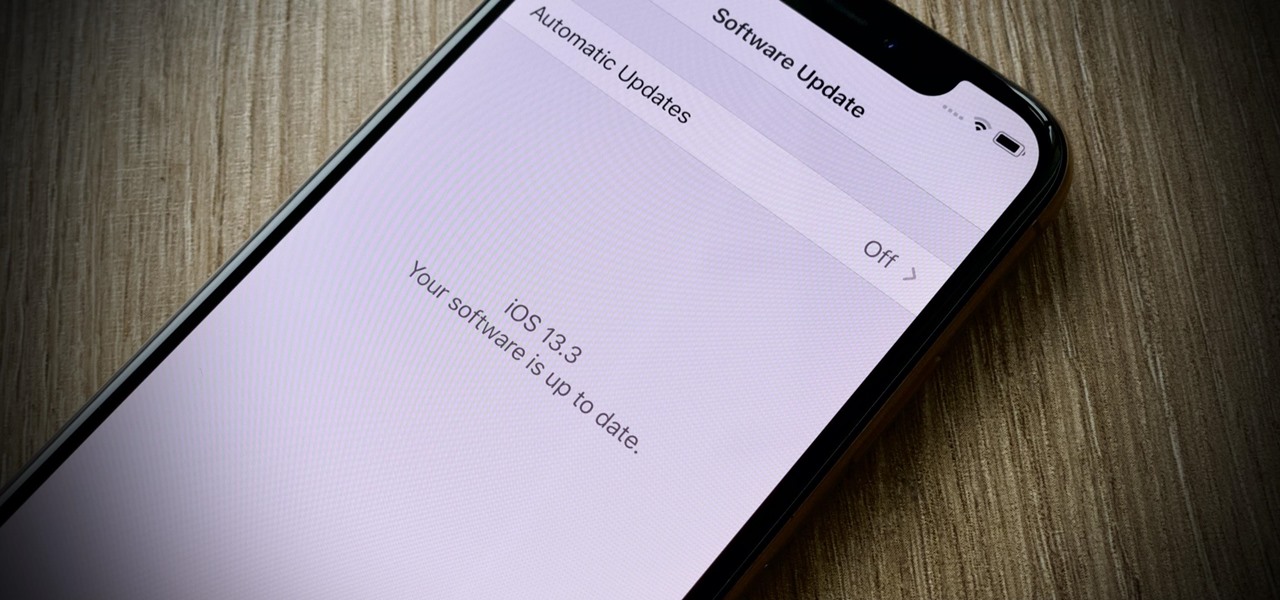
Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.