Ramen has always been a go-to meal for frugal foodies, college students, and anyone else who loves a soothing, cheap, and easy meal. And while instant ramen is delicious (and can easily be improved), making a simple homemade ramen is even better, and nearly as easy.

It happens to even the most avid cereal eaters: sooner or later you open a box, unfurl the crinkled plastic bag, and find that the cereal inside is stale. Maybe you forgot about it, maybe you ate it too slowly, or maybe you just found a new, better cereal and left it behind like Andy left Woody. Either way, the crunchy goodness is now stale, and you grab the box and walk to the trash can. Stop!

At first glance, mandolines seem like such a good idea. After all, who wouldn't want a tool that can create picture-perfect and paper-thin slices of fruits and vegetables that would put even the sharpest chef's knife to shame? Your French fry game would never be the same. Salads would become works of art. Your casseroles would cook perfectly evenly, since the ingredients would be cut uniformly.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Tater tots have a bad rap as a soggy cafeteria staple, but bake them at home and they crisp up nicely in the oven. Drain any unwanted oil from them on paper towels and they become perfectly crunchy on the outside and fluffy on the inside.
Macs, like pretty much all Apple products, are notorious for not having a highly customizable UI. They do this to keep a consistent look and feel across all of their devices, but I've grown bored of it over the years.

Freekeh is the next great supergrain that you might not have heard of yet. According to nutritionists, it comes out on top compared all to other grains, with more protein, fiber, vitamins, minerals, and a lower glycemic index.

Planning a Super Bowl party, or any football-themed party for that matter, can be fun for even the most craft-adverse host, as almost anything brown can turn into a football with just a little decoration. With a little planning, you won't be serving up any Pinterest fails this Sunday night.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

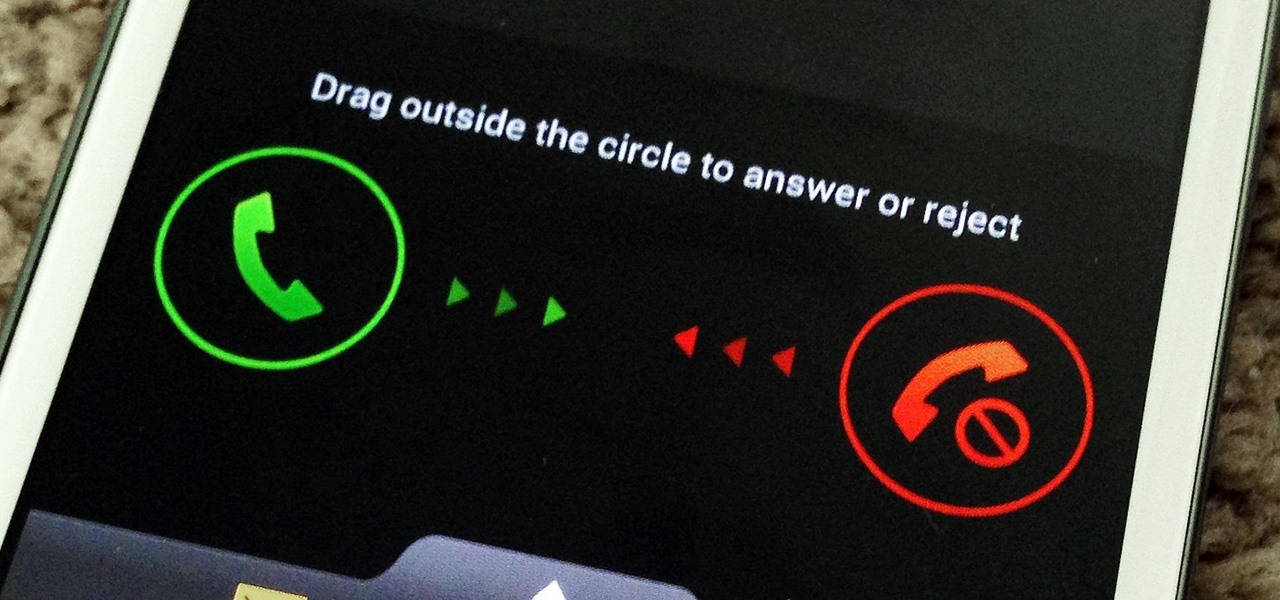
Due to their large size and added screen real estate, Apple included a new feature for the iPhone 6 and 6 Plus known as "Reachability." Essentially, this function makes reaching the top part of the display easier by double-tapping the home key to shift the screen down closer to your thumb.

BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices yet. While there are ways to port BlinkFeed over to other devices, it's reliability is dependent on the ROM, sometimes causing bugs and crashes.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

Long-exposure photography gives us the ability the capture some pretty amazing shots by delicately capturing moving elements in an image while keeping the shutter open at a slow speed. While that's great for things like traffic, scenery, and carnival rides, it can come in especially handy for 4th of July fireworks.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Google's new camera app has a highly innovative and unique feature dubbed Lens Blur, and the most interesting thing about it is not necessarily what it does, so much as how it does it.

You don't always plan on getting drunk, it usually just sort of happens, right? You finish one beer, move on to the next, and all of a sudden you're a six-pack in and feelin' it. And when you're drinking in places you're not supposed to, it can get ugly.

The all new HTC One M8 is the latest Android flagship making the rounds through major carriers hoping to beckon your purchase. Coming in at about $200 for most carriers with a contract, it makes a good case for itself with its advanced features and solid price point—but, there's another way to buy the One, and it's not from your carrier.

You've probably seen someone in your family truss the turkey on Thanksgiving before roasting it, even if you don't recognize the word. To truss a bird or roast just means to wrap it up as compactly as possible before placing it in the oven, and it's usually done by tying it with string. Trussing a bird is a tradition that's been around for a long time, and a lot of home cooks do it religiously even if they don't know why. It's a highly debated topic with fierce supporters on both sides, but f...

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

Point-and-shoot cameras are practically extinct these days now that every new phone on the planet has a camera built right in. This makes the smartphone market highly competitive, because the camera specs and features are a big selling point.

You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

Lag has been a serious issue on Android devices since the very beginning. Even the Nexus 7's quad-core processor can't stop it from happening. That's because the pauses and long responses are coming straight from the Android OS itself, not the hardware.

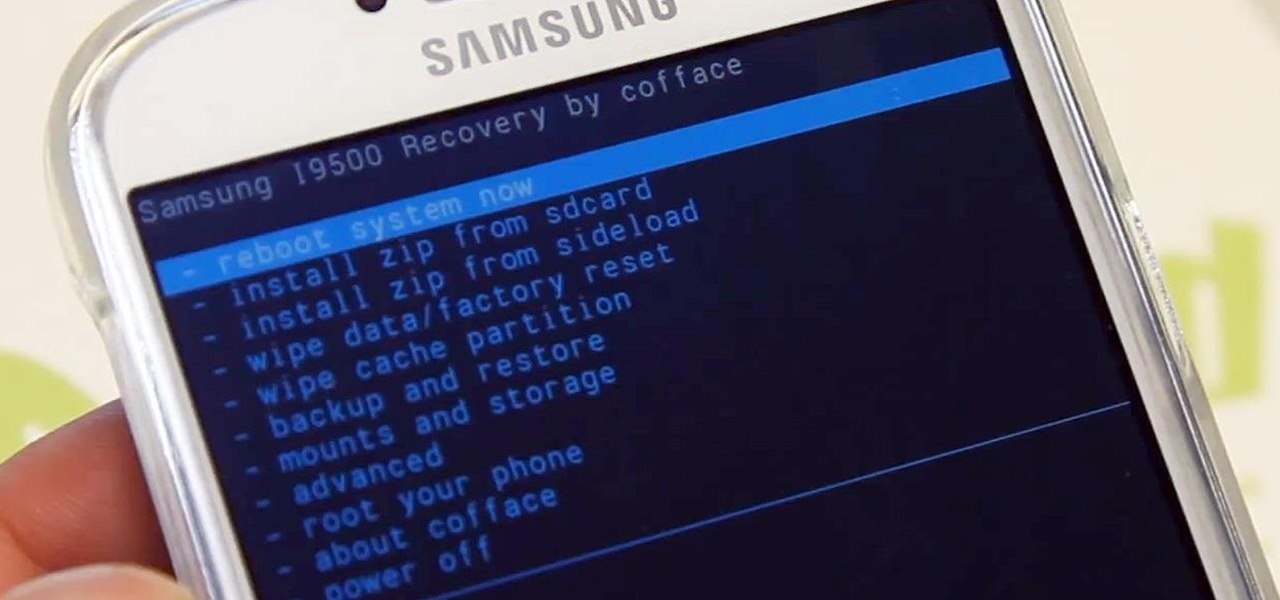
Ready to start rooting your Samsung Galaxy S4? For those of you with the GT-i9500 model GS4, this quick video will walk you through the entire rooting process using Odin and CWM.

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

Walking the streets at night can be uncomfortably dangerous. In 2010, there were 32,885 motor vehicle deaths in the United States. Of those, roughly 13%, or 4,280, were pedestrians. Two-thirds of those pedestrian deaths occurred at nighttime. Along with darkness, drivers also have to deal with rain and other harsh weather conditions. Combined, all of these factors can be very dangerous for anyone taking a walk at night. As it happens, pedestrian deaths are on the rise since 2009.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

The final chapter of Christopher Nolan's Batman trilogy is here, The Dark Knight Rises, and if you're anything like me, it made you want to immediately don a cowl of your own and run around punching criminals. Don't forget though, one of the most awesome aspects of Batman is his never-ending supply of crazy gadgets. Unfortunately for most of us, we don't have a billion dollars, nor Morgan Freeman, so we'll just have to make do with some good old-fashioned DIY tricks. Read on for a rundown of ...

The 2010 Ford Lincoln MKX can do plenty of things, and a lot of those features are geared toward comfort. Like your seats. You can position your seats exactly how you want them. And you can save that position so you can always come back to it later, just in case someone messes with your comfort zone. Watch and see how to set your memory seats on a 2010 Lincoln MKX. This will also work on a few other cars as well.

Thanks to the PlayStation 3 and Xbox 360, video games are constantly evolving to higher degrees of sophistication, with complex graphics, lifelike resemblances and storylines that create exciting experiences that relieve the tediousness of our everyday lives.

There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline your security process and make browsing the web so much easier, and right now, it's on sale for just $79.99.

With Shortcuts, Apple has designed a way to create your own tools and automations right on your iPhone. And to top it off, your creations can be accessed in a variety of ways, including Siri phrases, widgets, and the Shortcuts app itself. Perhaps even more useful is adding them as custom actions to your Share Sheet and making them available to you system-wide.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

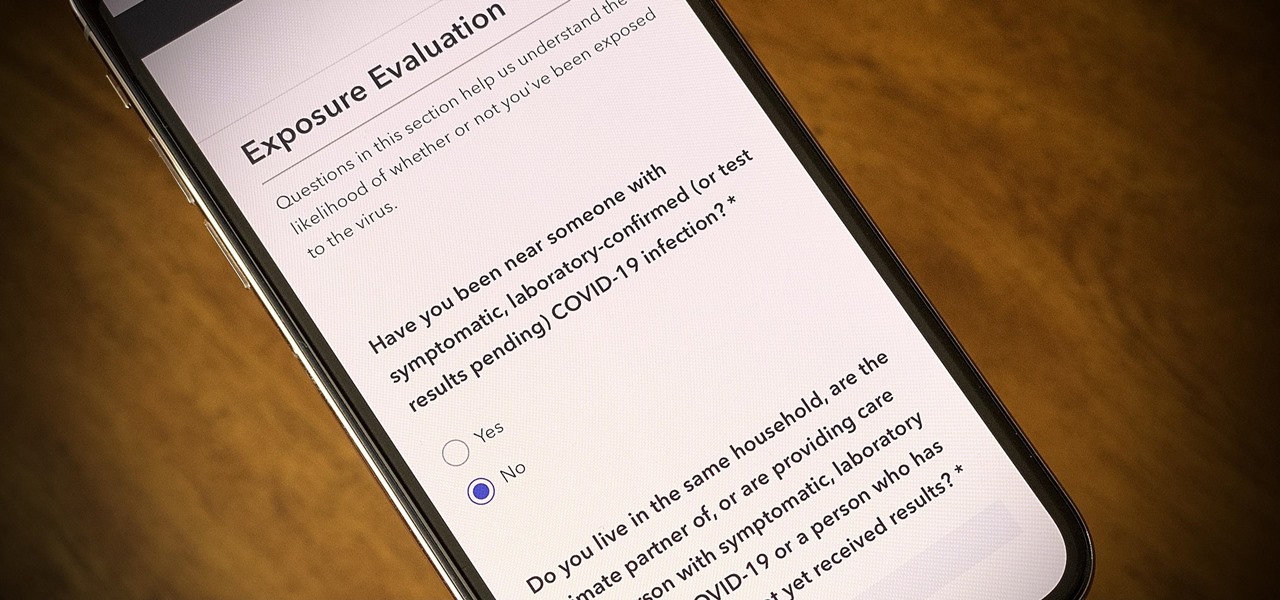
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.