My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

Despite all the tragic stories you hear on the news, you'll probably never be involved in a shooting. But you never know. Nobody thinks it’s going to happen to them – until it does. Be prepared to survive a shooting rampage, just in case.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Apple has implemented a new sensor on the rear camera of its fourth-generation iPad Pro, and it's pretty exciting. It's called the LiDAR Scanner, a scanning "light-detection and ranging" sensor, and you may very well be acquainted with it if you follow any driverless car news. Will we also get it on the upcoming iPhone 12 Pro?

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

Already among the first game makers to add augmented reality content to an existing game upon the launch of ARKit, Zynga is breaking new ground with mobile AR once again.

Right now, Apple is testing two versions of iOS. On the one hand, you have iOS 13, buggy but feature-filled. On the other, iOS 12.4. The latter just got an update to the fifth developer and public beta versions, 13 days after the release of iOS 12.4 developer beta 4.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

OnePlus unveiled its latest device — the OnePlus 7 Pro — Tuesday, May 14. Usually, the company touts a device with impressive specs, build quality, and price, all without sacrificing too much. This time around, however, OnePlus decided to include a Pro device without compromise, while retaining those core values, making the 7 Pro highly competitive against the "low end" phones of their competitors (the iPhone XR and Samsung S10e).

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

Now that the NCAA Basketball Tournament is underway, 7-Eleven has decided to launch an augmented reality experience to remind basketball fans where they can quench their thirst throughout March Madness.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

In MyFitnessPal, you can search through a food database to add your meal into the app's diary and track your calories. Unfortunately, the sheer size of the database can make it hard to find exactly what you have just consumed, which is why MFP includes a barcode feature to make the process of adding food much smoother.

In a world where augmented reality is becoming the hero of the movie marketing, Universal Studios has decided to use the technology to reinvent the traditional movie trailer, a time-tested tactic of film promotion, in support of the forthcoming Robert Zemeckis film, Welcome to Marwen.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

While there are many awesome features in iOS 12, there's one that has got the best of me and my patience. Sending photos and videos in a text or iMessage. Yes, there are a few ways the process remains the same, but if you select pics and vids right from within the Message app, be prepared to be annoyed ... highly annoyed.

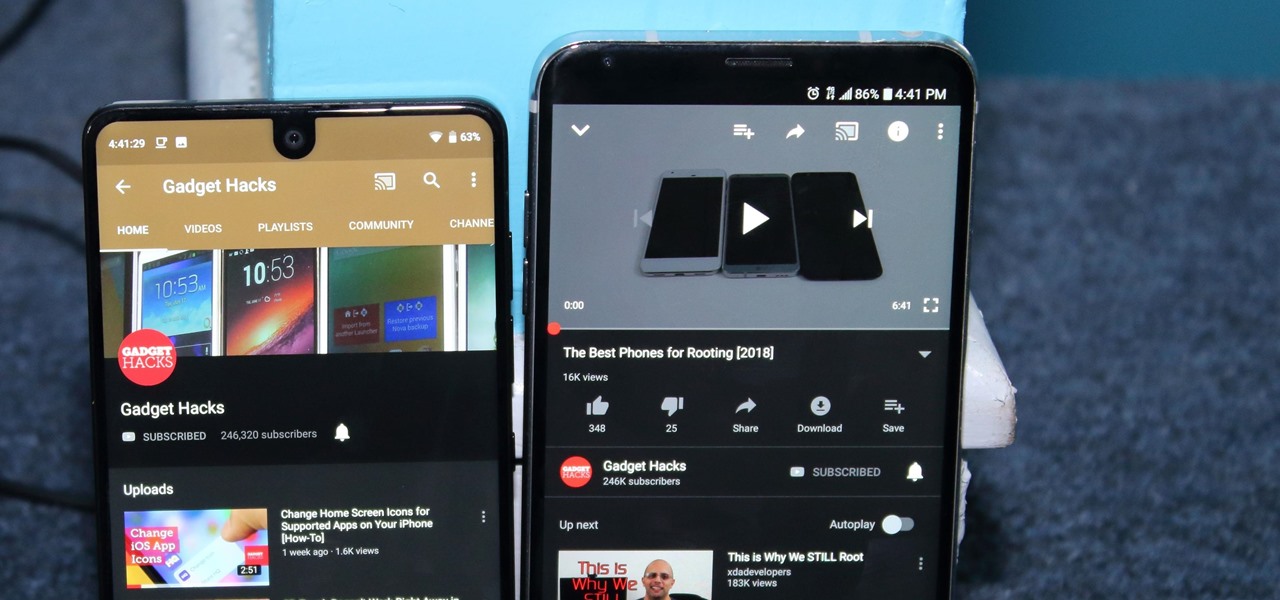
After months passed since Google first announced the feature, YouTube's dark mode has finally reached the Android masses. Sure, it just changes some colors, but it has been a highly sought-after feature since iPhone users got it months ago.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Another entrant into the do-it-yourself AR content creation market has emerged, as Zappar has updated its ZapWorks Studio software to include features for development newbies.

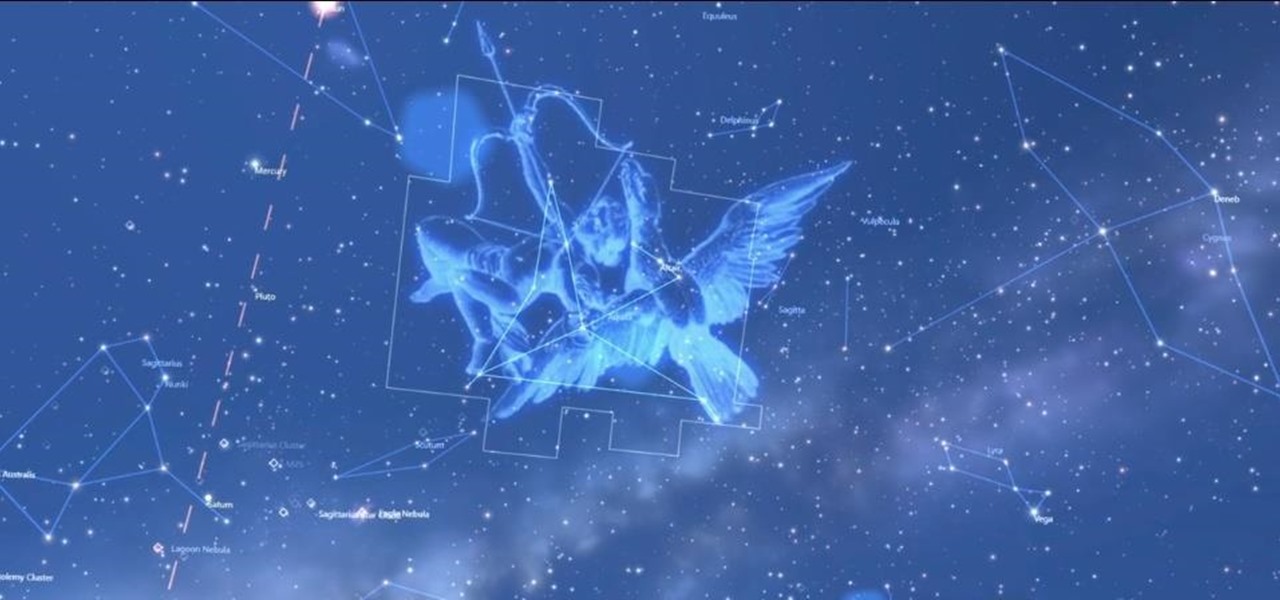
On June 23, National Geographic will begin welcoming visitors to the world's first outdoor planetarium in Quebec, Canada, where an augmented reality experience overlaid on the night sky will replace the projection systems of traditional facilities.

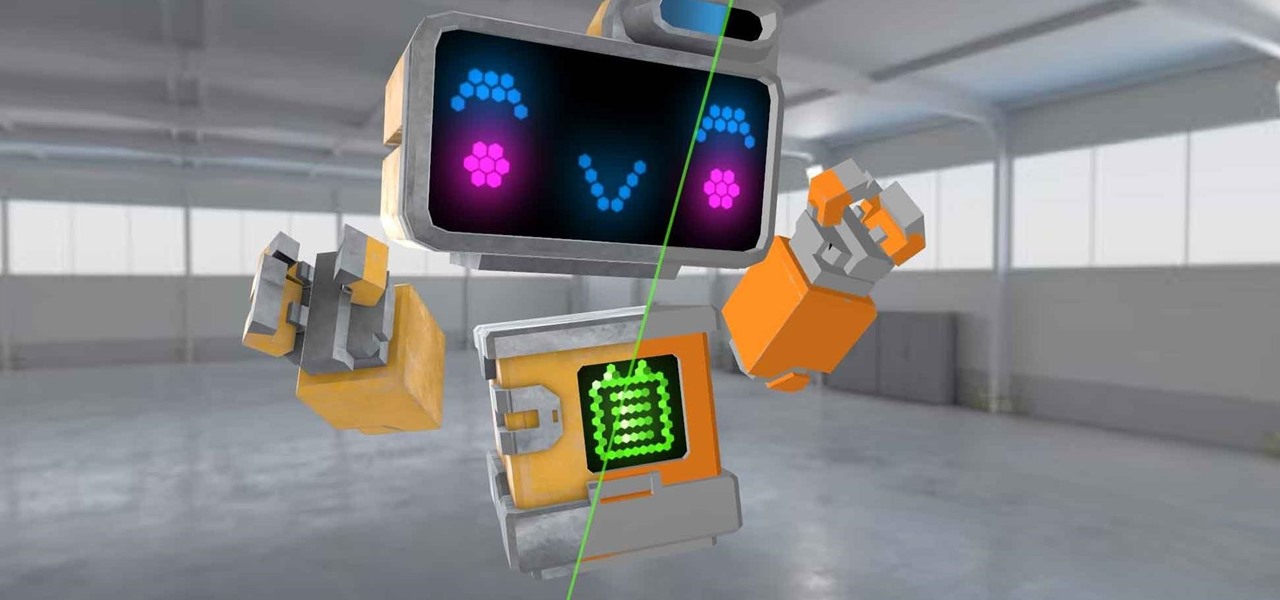
Hand tracking technology company Leap Motion has built a stunningly fluid augmented reality ping-pong game that not only showcases the capabilities of its open source Project North Star augmented reality headset, but also demonstrates how artificial intelligence can elevate immersive experiences.

Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

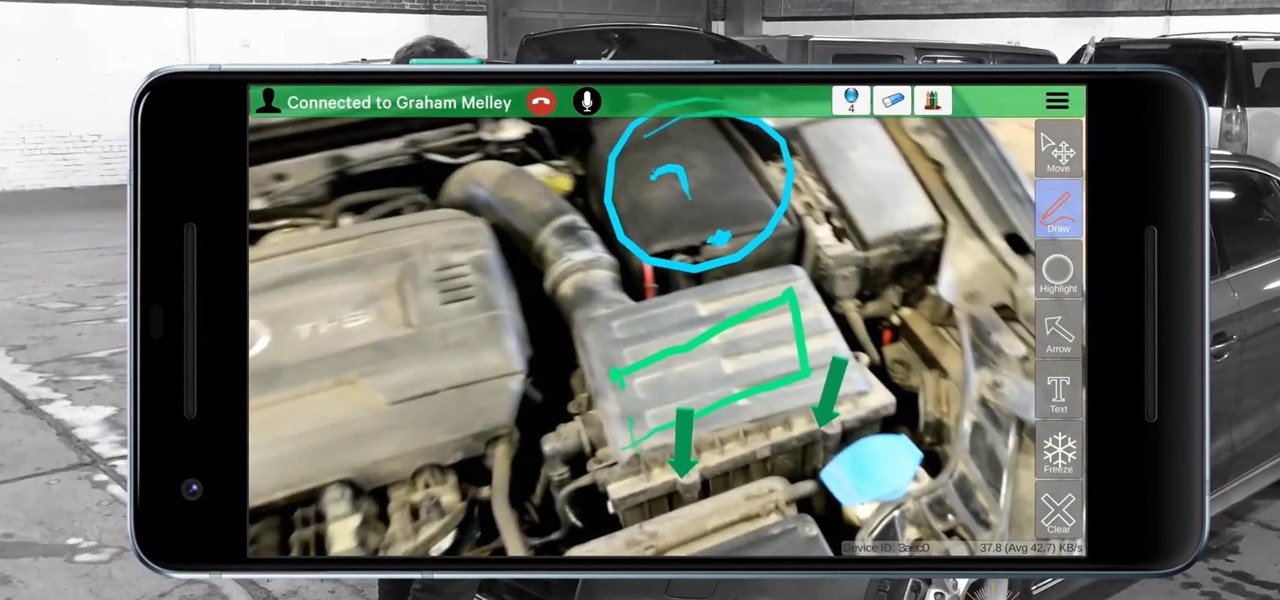
Scope AR has decided to take its live remote assistance enterprise application, Remote AR, further into the mobile augmented reality realm by harnessing the powers of Google's recently released ARCore.

Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.

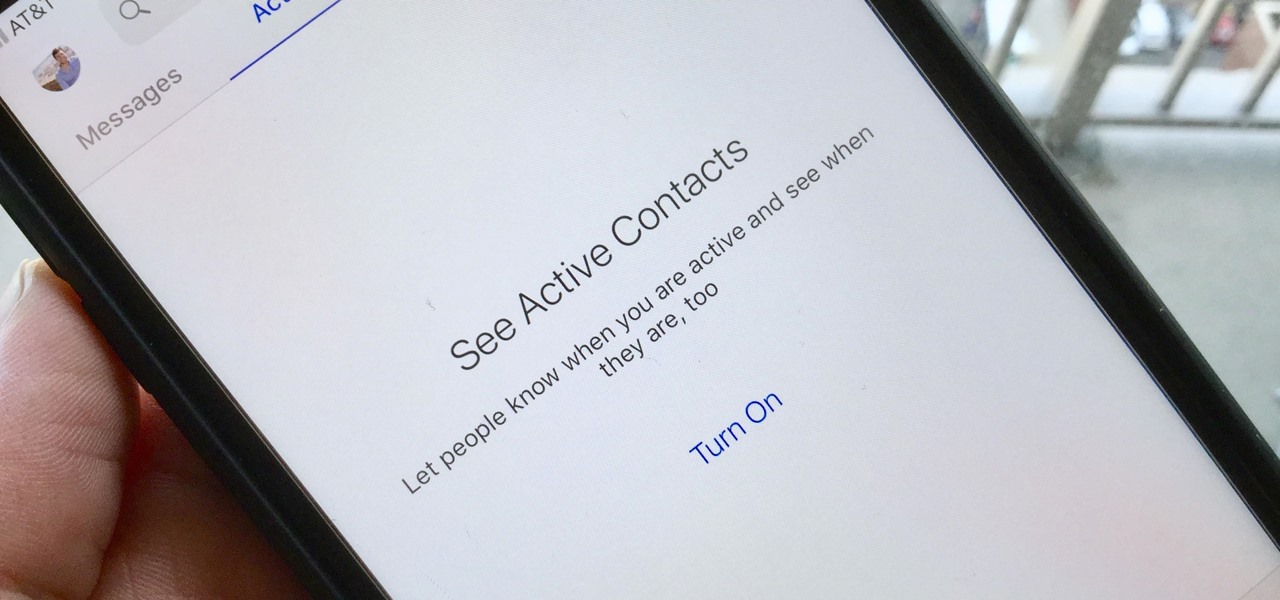
For all of its advantages, Facebook Messenger isn't the best for people who like their privacy. The popular app lets all your Facebook friends know when you're online by default, as well as how long you've been idle, making it impossible to check up with one person without leaving yourself vulnerable to your entire friends list. Luckily, this feature is one you can turn off.

Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.

As part of its ARCore release announcement, Google also revealed a forthcoming app that's sure to excite those who celebrate '80s pop culture.

After closing its 2017 financial books on a high note, Snap, Inc. is planning to ride the momentum of its augmented reality products into the new year. That's the main takeaway following the company's 2017 earnings conference call, which was held on Tuesday.

If you're an Android user, you're very likely jealous of your iPhone friends who have access to the wide, wonderful world of augmented reality thanks to ARKit.

Longtime Next Reality readers may remember my Wish List for Microsoft early last year. It was a post in which I put my head together with a number of other community developers to create a list of features that would make Windows Mixed Reality and HoloLens better for developers. It would seem that one of the most sought-after features is finally here ... well, sort of.