Android is a highly customizable operating system. Sometimes, we use these capabilities to add core functionality or streamline the user experience, but there are other times when customization is just about having fun and making your smartphone's interface more enjoyable.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.
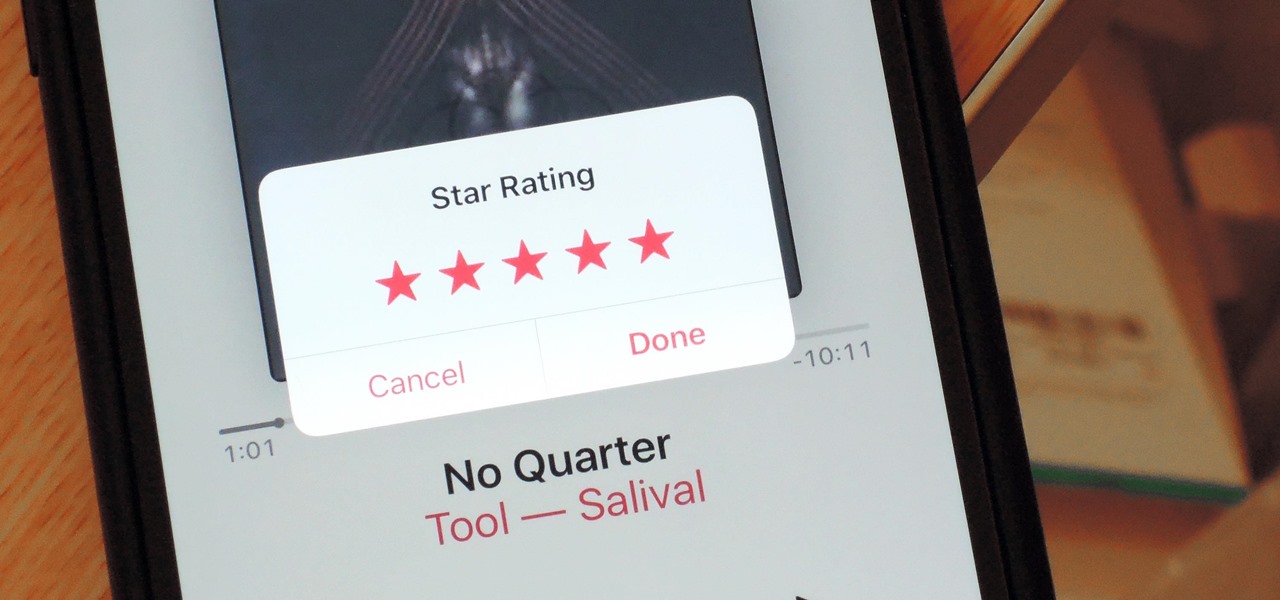
When Apple released the iOS 10.2 update to the public on December 12, 2016, iPhone users got a slew of new features, including new emojis, a brand new TV app, the ability to save camera settings, and more. But out of all of these new features, the one that interests me the most is something they didn't even include in the release notes—star ratings are back in the Music app!

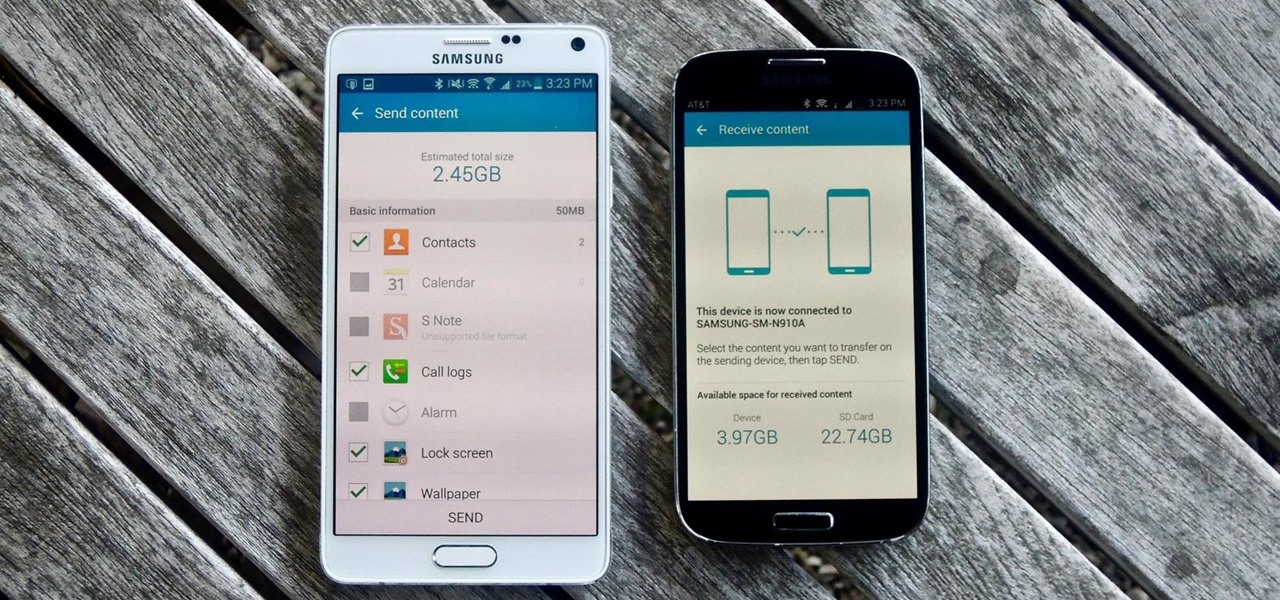
Google Drive has a very simple way to switch from iOS to Android. iPhone users who want to take the plunge into the wonderful world of Android, but were hesitant to do so in the past because of the laborious process of backing up their data, can back up their contacts, photos, videos, and calendars with the tap of a button.

In recent years, wave after wave of technological advancement has led us down roads that are beginning to look more and more like science fiction stories. In their efforts to bring us from science fiction to science fact, Microsoft Research showed us a new communication medium called Holoportation earlier this year—and now they have found a way to make this highly complex holographic system far more mobile.

Google and Microsoft have both established platforms and hardware for emerging digital realities, but Apple, true to form, hasn't had much to say on the subject. They've shown interest in augmented reality, and we've seen patent filings that indicate research and development, but a recent rumor points to that research ending up in your car instead of a rose gold headset.

It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected his movements using a Kinect into a holographic zombie.

Video game emulation has saved arcade and console classics from obsolescence, and that wonderful hobby has found its way onto the Microsoft HoloLens—with some three dimensional upgrades, of course.

The official release of Apple's iOS 10 mobile operating system is still a few months away, but starting today, June 7, the public beta version is available to download if you'd like to get a head start on checking out all the cool new features included in Apple's latest mobile OS.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

While there are tools online that let you turn photos into interesting emoji art, and mobile apps that let you create emoji mosaics, none do it better than an iPhone app by second verse, which makes it a super easy, highly customizable process.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Listen up, children, pregnant women, and lightweights: this particular KitKat variety is not for you. Well, with 0.8% alcoholic content per 2 KitKat bars, it's highly unlikely anyone will actually get drunk on these things. Still...

If you consider yourself a regular coffee, tea, or hot chocolate drinker, you probably have a kitchen cabinet full of stained mugs that refuse to scrub clean. Thankfully, there is a better solution that doesn't involve continuing to fight those stains with a sponge, bleach, and elbow grease. The answer to your coffee or tea stain problems is Cafiza: an awesome espresso machine cleaning product that is popular amongst professional baristas... but also doubles as an extremely effective ceramic ...

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

I loved the original Star Wars trilogy when I was a kid, but loathe all of the current DVD, Blu-ray, and streaming versions available today. Ever since 1997, every version of A New Hope, The Empire Strikes Back, and Return of the Jedi has had horrendous CGI effects added in that George Lucas deemed necessary to bring his "ideal" version to life.

Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

There are countless beauty tools, from expensive brushes that perfect your application of powder to carefully shaped smoothing pads that help you to blend your makeup. Yet hiding in your silverware drawer is a free and highly useful beauty tool that can help you create an even more sophisticated look: a spoon.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).

With only a month left until Samsung's highly-anticipated Galaxy S6 and Galaxy S6 Edge are released to the general public, it's only natural that some of the devices' features slowly trickle out, like Edge notifications, the new Smart Remote app, and, of course, wallpapers.

My college days are long behind me, and while I don't necessary miss them, I am jealous of all the countless resources available to students these days. Apps like PhotoMath are something I wish I had access to in my student days, making assignments less strenuous and easier to complete.

Early last year, Google purchased Quest Visual, acquiring the immensely popular augmented reality translator app Word Lens in the process. While Google did put the feature on the Google Glass, they spoke more about implementing Word Lens into their Translate app sometime in the future.

An app with overabundant features can make it more customizable, but too many options can also be overwhelming, even on a mobile web browser. If you're tired of Safari or Chrome on your iPhone, try out Frameless from developer Jay Stakelon, a simpler web experience using just the essentials.

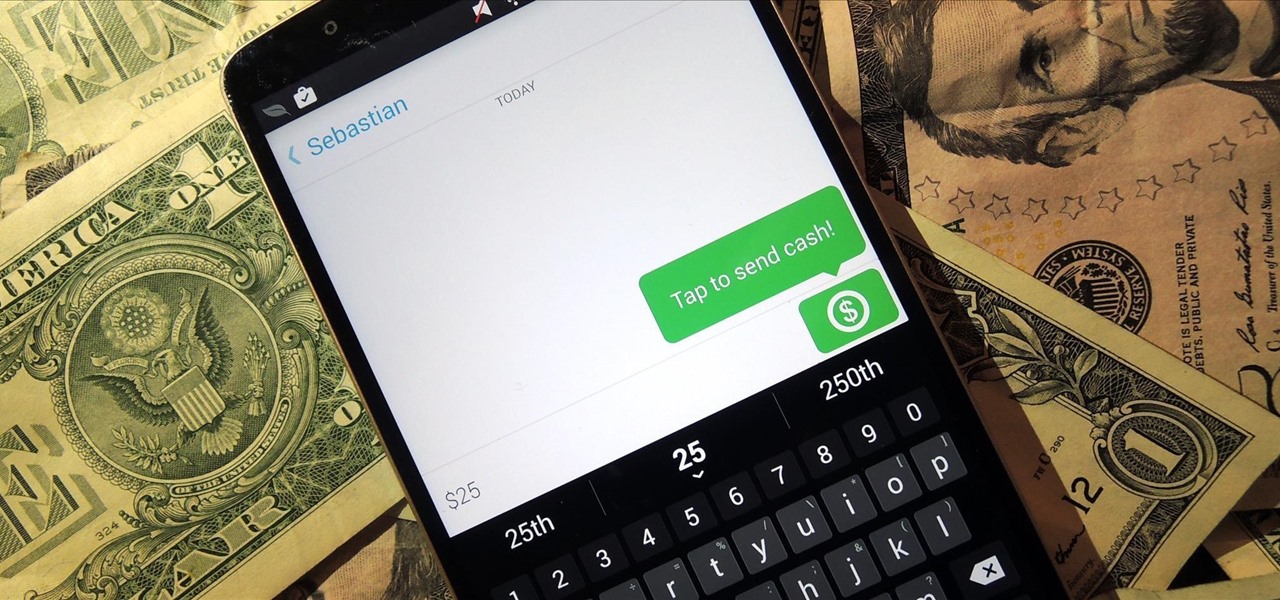
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

The official release of iOS 8 was highly anticipated, but the truth is it may have been a little premature on Apple's part. Since its debut only a week ago, plenty of bugs and issues have been reported across the various compatible iPhone models.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

The Samsung Galaxy S5 display can be replaced by most do-it-yourselfers with some basic mechanical skills and a few inexpensive tools. The good news is that once you replace your display assembly your screen will be good as new with no bubbles or dust on the inside. The replacement part is a bit pricey but that is a good percentage of the cost involved with manufacturing this device. Below is a video showing the entire process from start to finish. It's best to turn on your volume for the nar...