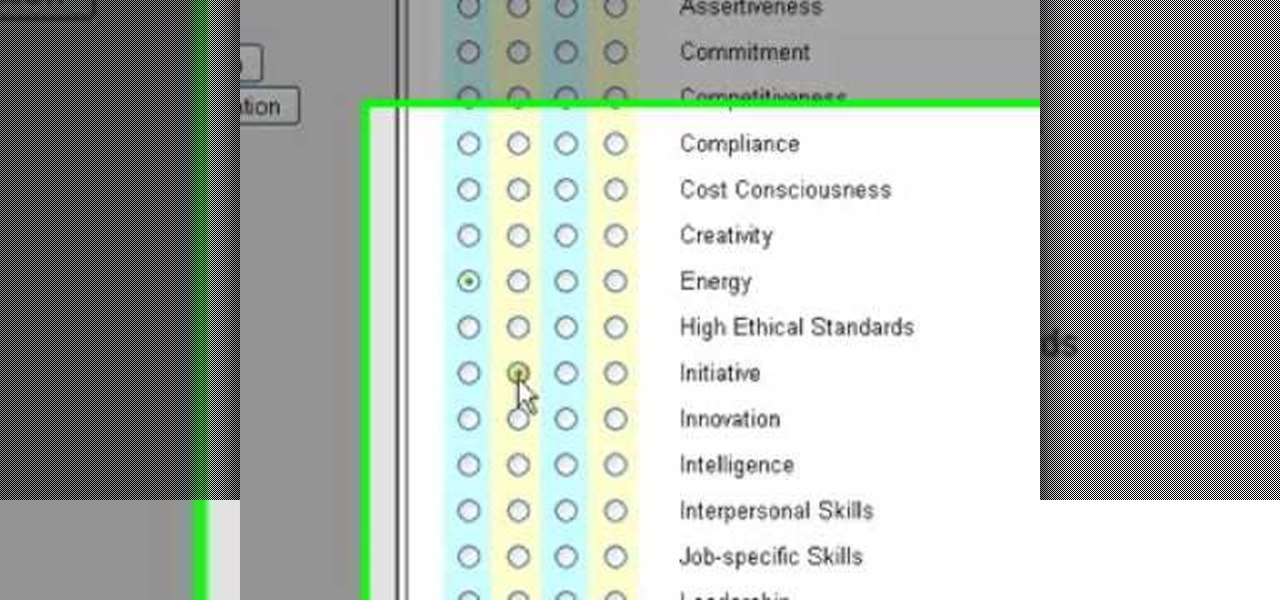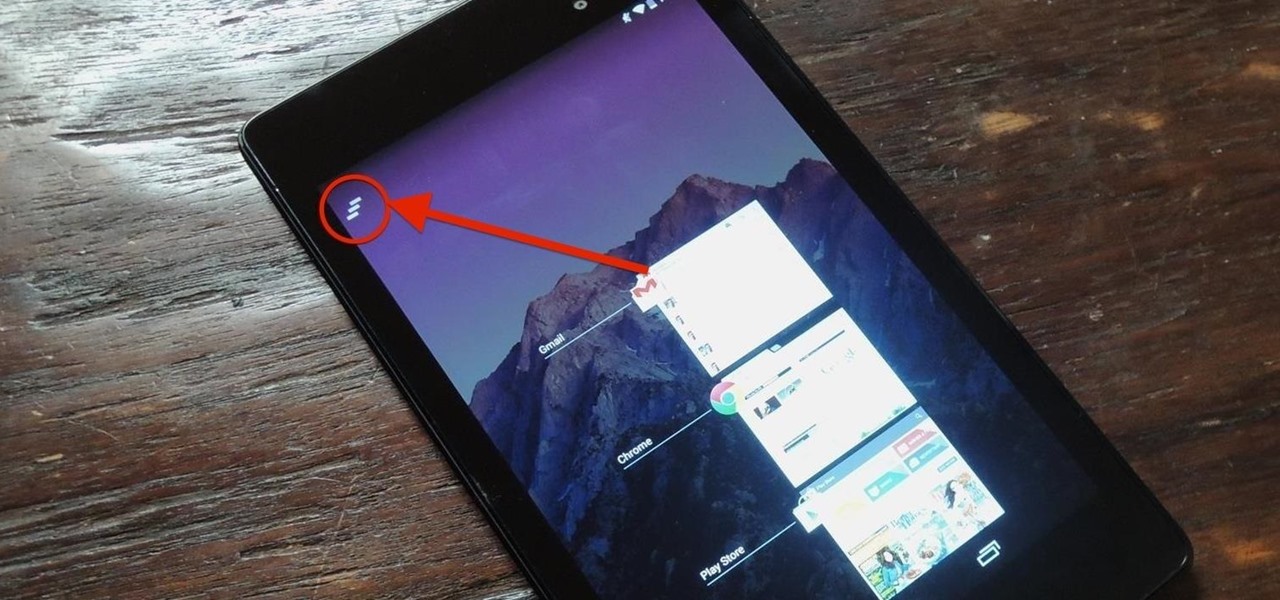
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

There wasn't really anything too special about the S Pen on the Samsung Galaxy Note 2, with its limited capabilities and finicky sensitivity. Luckily, the S Pen was greatly improved on the Note 3, the biggest enhancement being Air Command, a floating menu that appears when the S Pen is removed that gives quick access to all the new features.

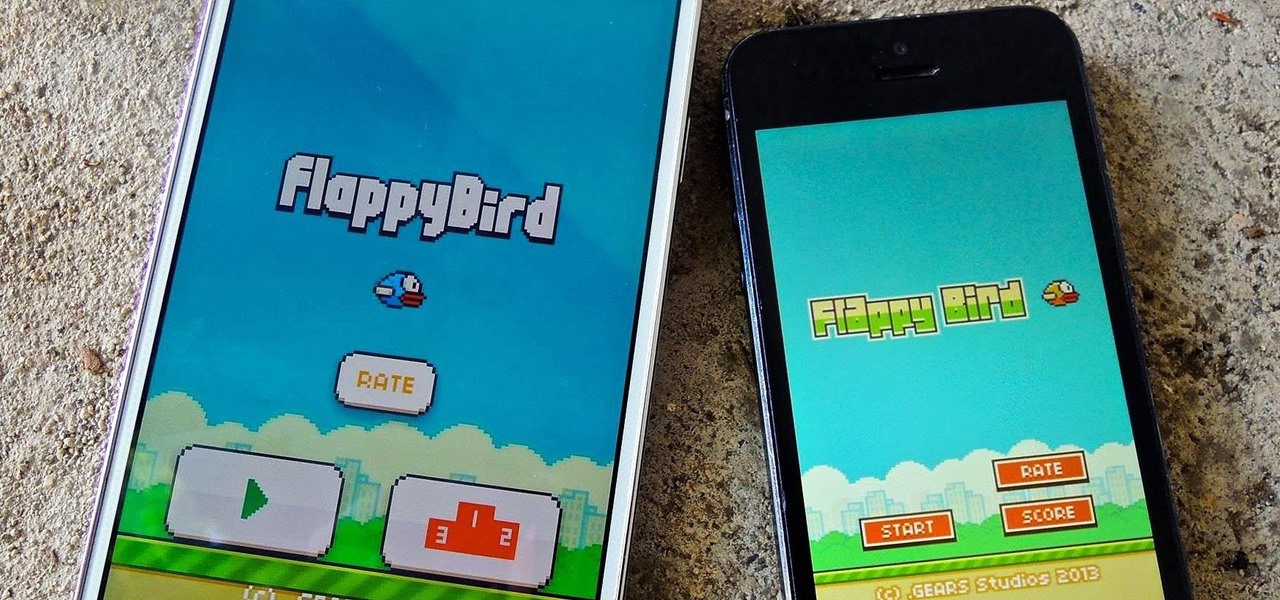
Flappy Bird is the extremely difficult, overly frustrating, strangely similar, yet highly addictive smartphone game from .GEARS STUDIOS that has catapulted its way to the top of the charts on both Google Play and the iOS App Store—seemingly out of nowhere.

This year's NFL playoffs have been nothing short of spectacular. With Super Bowl XLVIII coming up on Sunday, February 2nd, people are already gearing up for another classic showdown between the NFC and AFC, and this time it's the Seattle Seahawks versus the Denver Broncos.

There are a lot of great music apps available on Google Play for your Android device, each usually specializing in one feature or another, and we’ve shown a bunch of them. There's everything from floating controls to equalizers to deeply integrated streaming, but what if you want all of those features jam-packed into a single app?

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

Learning to make giant bubbles for this video has been the most fun I've had with a project in a long time. It's addicting to try to get them to grow bigger and bigger than the ones before. Since filming this video, my skill has improved tremendously and the bubbles you're about to see, though spectacularly big, are dwarfed by what I've made since. Everyone loves to watch. This is definitely one project that will draw a crowd!

With CyanogenMod 10.2 recently released and the Samsung Galaxy S4 still waiting on Android 4.3, it only makes sense that the coveted features from both firmwares are highly desired by Android owners all over. We've already brought you a feature from each firmware—the cLock home/lock screen widget from CyanogenMod and the Google Play Edition Camera and Gallery from Android 4.3. Now we're bringing you another in the form of an updated text messaging application, ported from both Android 4.3 and...

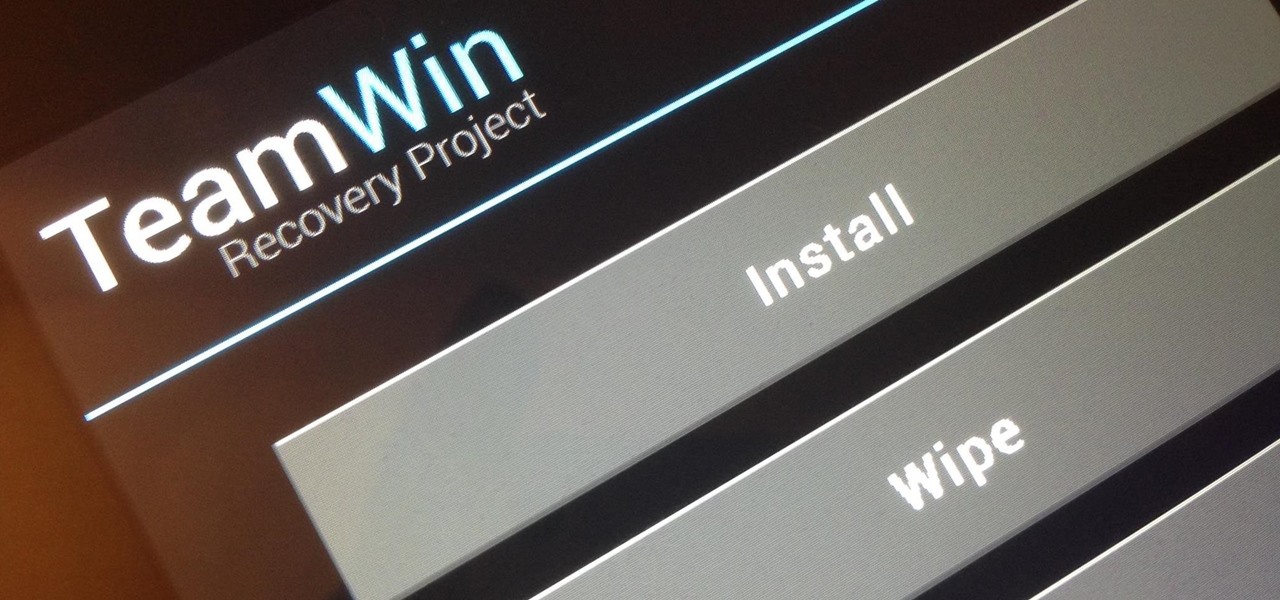
If MacGyver had a Nexus 7, he'd most definitely have TWRP installed. It's the softModder's Swiss Army knife for all things modding. You can flash custom ROMs, install add-ons, recover from a disaster, and much more.

The Jelly Bean update brought a lot of cool features to the Samsung Galaxy S3, but one nasty bug remained. Something was causing "Android System" usage to be consistently high. Of course, the percentage of this process that is used is dependent on what you're doing at any given time, but it shouldn't be anywhere near this level with "standard" use (calls, texts, emails, light browsing, etc.).

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Glitches can be extremely annoying when playing some of your favorite games, but sometimes, only sometimes, there are glitches in the game that give you an unprecedented advantage against the computer or other players online.

Maybe not water per-se, but with this simple technique you can turn one of the most abundant materials on earth into a highly explosive gas.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Do you have what it takes to join the elite and become a sniper? Maybe not in real life, but in a video game, you surely have the guts to become a military sniper. In Sniper: Ghost Warrior, you control a highly trained sniper, amongst a team of US Special Forces, as you try to control a military coup d'état (or just "coup") in the island of Isla Truena, which is a small fictional Latin Amercian country. Can you and your sniper team save the country from ruin?

Letters of recommendation are important in the business world. If you have been asked to write about a coworker, student or friend, check out this tutorial. Takes you through a step-by-step process you can use to produce a professional-looking and highly effective letter of recommendation. Includes how to structure your letter, how to personalize it for your candidate, and how to make it convincing to the recipient.

This glitch is a simple one on Killzone 2 for PS3. To do this glitch, you'll need to perform the medic technique Just watch the whole video walkthrough to find out how to find the Radec Academy Glitch.

On this map, you can do this great glitch on Killzone 2 for PS3. There's a lot to do on this map, so there's sure to be many more glitches, but you'll have to figure that out yourself. Just watch the whole video walkthrough to find out how to find the Outside Pyrrhus Rise Glitch.

Want to play lead guitar in a rock band? Well first you have to learn techniques from the masters. This guitar lesson teaches you how to play "Save it for Later" by the English Beat. The original song uses a highly unusual guitar tuning (D-A-D-A-A-D). Here's how to play the song using standard guitar tuning (E-A-D-G-B-E). Once you get a hang of these popular guitar chords and tunes, you can start incorporating them into your own songs. With this lesson and a bit of practice you will be able t...

Dark Angels are a highly sought after army figurine for Warhammer 40k. This hobby how to video shows how to quickly paint the Dark Angels miniatures so they're ready for table top war play. Watch, follow along, and get your Warhammer going.

This video teaches you how to use NLP to anchor others to you. Create the impression that you are sexy, motivated, confident, etc. with this simple, yet highly effective, NLP (Neuro Linguistic Programming) technique taught by Steve G. Jones, Clinical Hypnotherapist and expert in hypnosis.

There are few things more relaxing than a hot shower after a long hard day of toil, and there are few times when people are so vulnerable or oblivious to the possibility of a little practical joke. A splash of almost freezing water will feel even colder within the warm security of a good shower. Watch this video pranking tutorial and learn how to ruin someone's hot shower with a hit of ice water. Use this as inspiration for one of your April Fools Day pranks!

Once again, the Frugal Chef shows her viewers how to make a delicious, nutritious, and cost effective meal. Today, the meal of choice is Vegetarian Lentil Stew. This hearty lentil stew is chock full of wholesome and easily available ingredients such as lentils, carrots, and olive oil. Even though this stew does not contain meat, the lentils are sure to be very filling. The Frugal Chef highly recommends that while you are preparing the recipe, you thoroughly stir together all the included vege...

ICELED UFO is a complete automotive underbody lighting kit consisting of four ICELED tubes, an advanced Electronic Control Unit and a wireless Infrared handset that allows the entire system to be remote controlled from inside or outside the car. The ECU can independently address all the pixels in the tubes allowing them to project patterns ranging from complex all the way down to a single color on the ground. The ECU also provides ICELED data for synchronous control of additional ICELED light...

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Most people are familiar with the decline of honeybee colonies around the world. Among other threats, Colony Collapse Disorder (CCD) is eroding the capability of honeybees to maintain their hives and provide their services to human farmers.