For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Even as we look forward to returning to work in person, the last year has changed how work can be done. That means there will always be a demand for good programmers and coders who can support the digital infrastructure of the online working world. The Backend Developer Bootcamp Bundle can give you the expertise you need to become a highly qualified programmer for only $29.99.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

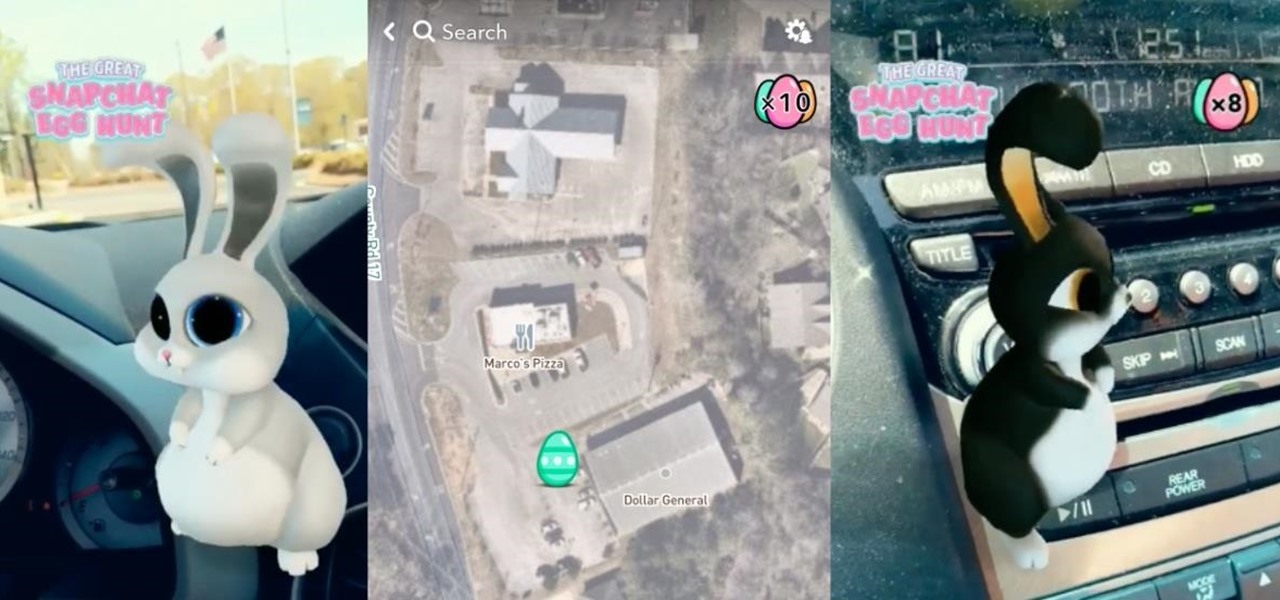
While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

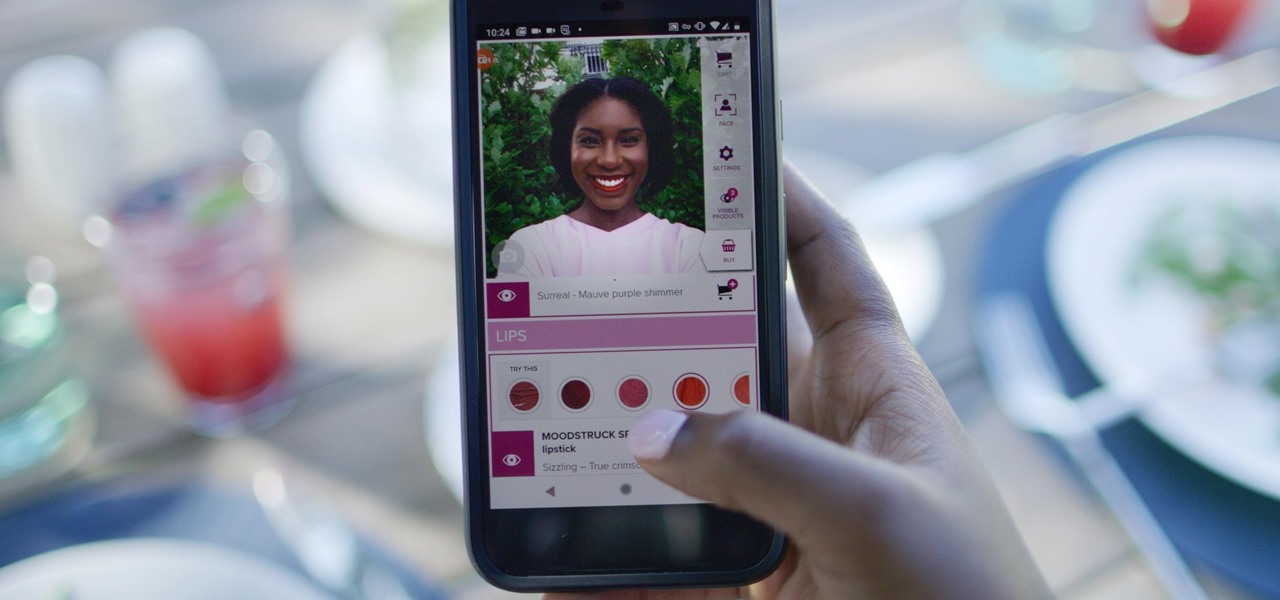
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

In the midst of fending off legal challenges from Magic Leap and Epic Games, startup Nreal isn't retreating. Instead, the company is digging in its heels and pushing forward with its launch plan for its Nreal Light smartglasses.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Almost half a year after we broke the story about the demise of Meta Company, there's good news for fans of the augmented reality startup — a rebirth is at hand.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

The camera punch hole on the S10 has gotten our creative juices flowing more than any notch ever could. First, we saw wallpapers that served to camouflage the cutout or even accentuate it. Now, if you want to go the opposite direction and highlight your S10's camera hole, there's an app that turns it into a circular battery meter.

Although all signs points to Microsoft releasing a new HoloLens in the coming days, the company is nevertheless looking to distribute its augmented reality apps to other operating systems.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

The app that Lego demoed at this year's iPhone launch event is now available in the App Store, and it showcases several new capabilities available in ARKit 2.0.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

While the three new iPhones won't even be announced until Sept. 12 during Apple's fall event, case makers are already primed for the launch of the devices. Some case designs are already live on manufacturer websites, and you can even buy or preorder cases for the iPhone XR, iPhone XS, and iPhone XS Plus to have right now or on launch day.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Magic Leap has earned a reputation for overt secrecy, but as it nears the highly-anticipated launch of the Magic Leap One, the company is spilling some of the beans. This week, we get a heaping helping of information on the Lumin OS, as well as a couple of great demos.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

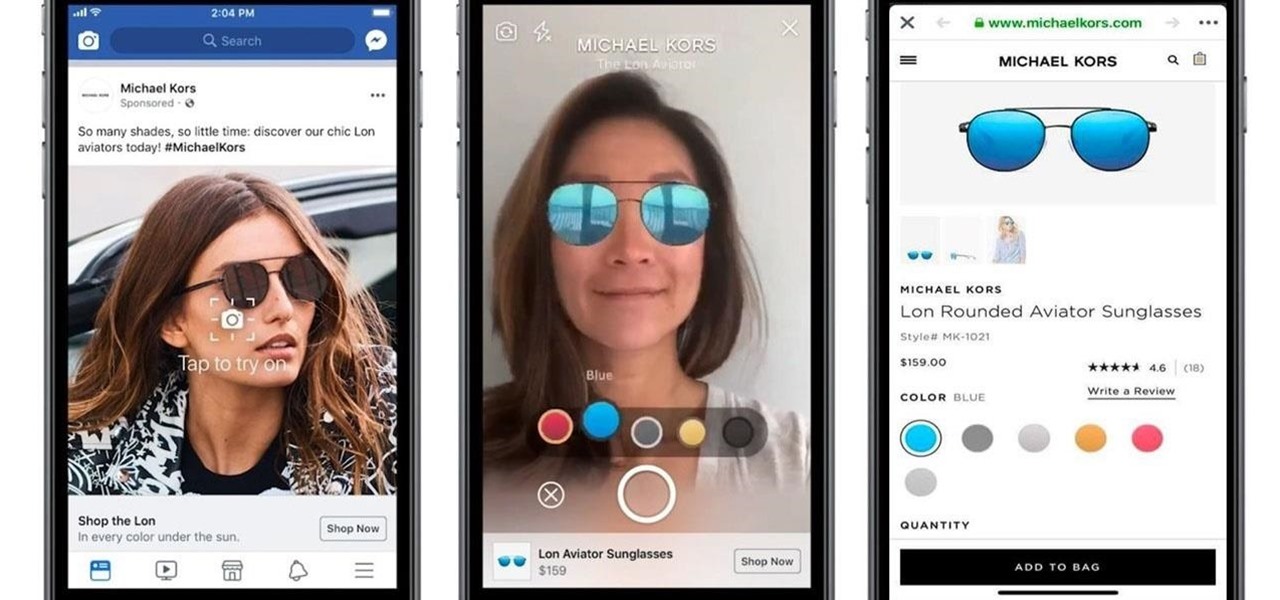
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed.

Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

I don't need to remind you that Netflix is a holy bastion of both outsourced and original content. I probably also don't need to remind you that Netflix's rating system sucks. It suggests content based on how much you'd like it, as opposed to how highly it's rated. After all, Netflix wouldn't admit that some of their own material isn't good.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

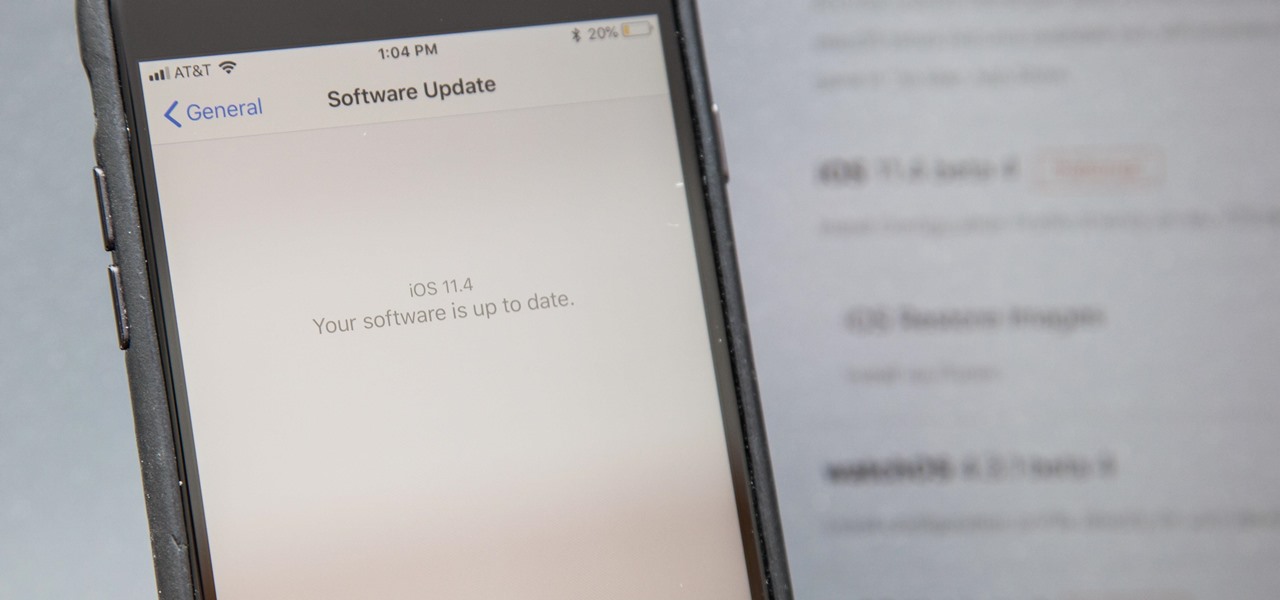
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

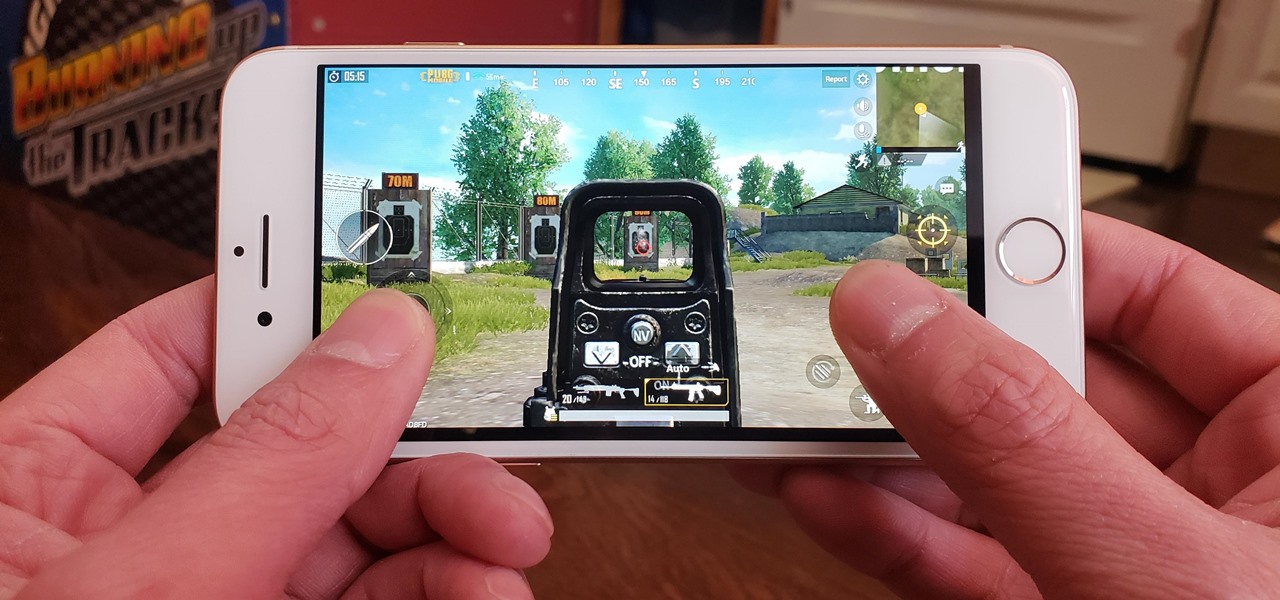
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

Alongside the usual collection of holiday-themed Lenses, Snapchatters received an extra-special treat from Snapchat over the weekend—a world-spanning Easter egg hunt.

The Galaxy S9 is an audio powerhouse. It has the first set of stereo speakers on a Samsung flagship, and it even comes standard with a set of AKG-tuned earbuds that would normally cost $99. But if you want to further enhance your audio experience, there's a feature that will customize audio output to your own specific hearing.

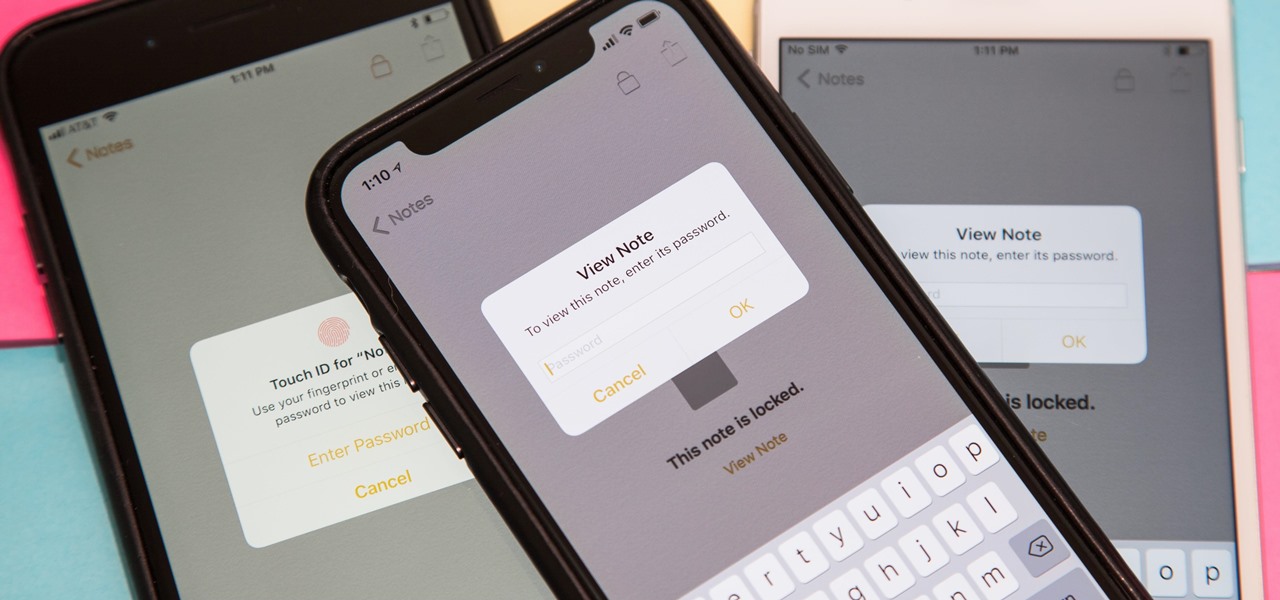
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

We regret to inform you the former king of third-party keyboards, Swype, has officially retired on both Android and iOS. A few weeks ago, we noticed Swype's mysterious disappearance from the iOS App Store but had hoped it was just pulled temporarily, not gone forever. Unfortunately, Swype is no more, but there's something that's ready to take its place for you on your phone.

Now that it's been officially released for Android, Monument Valley 2 shot to the top of our best paid puzzle games list, and rightly so. This was no easy feat, as the games we covered ran the gamut of puzzles and all had stellar reviews. But there's just something about Monument Valley 2 that made it stand out from the rest.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.